
Tell-A-Vision = Why Not Try Love Again?
Links +++ February 2013 Archive

P-r-i-m-e-t-i-m-e p-r-e-s-e-n-t-s:
Peace Keeper by Michael Stickrod
135 Huntington St., Brooklyn, New York ~ March 1, 2013, 6-10pm
An Eastern & Western Band 2/27/13 ~ Chant -> Ripple -> Country Roads
http://www.youtube.com/embed/Brx0vrfGUVA?rel=0 ~ Video ChannelPublished on Feb 28, 2013 ~ Okay, here's step two in an effort to establish a new musical genre known as Eastern & Western. Our players are (from left to right at the beginning of this video) Nate, James, Pondo, Cedar and Linnea--and our dancer is Hitomi. Emma Goldman: It's not the revolution if you can't dance to it. Yeah, and it's not the revolution if we don't have effective ways to sustain relatively elated moods. Please let us know how you feel about our music. If you like it, please share it with your friends. ~ Very best, Pondo
Sometimes people don't want to hear the truth because they don't want their illusions destroyed. ~ Friedrich Nietzsche
The Melodians ~ Rivers of Babylon
US Supreme Court leans towards
striking part of Voting Rights Act
You Remember the Supreme Court, which was mostly appointed by the War Criminal Bush family, and the ones who told U.S. American Voters to Drop Dead ?
Yeah Yeah Yeahs~- Sacrilege ~ http://www.youtube.com/embed/6_dw3TZNIGE?rel=0
John 13:34-35
Man Dies In Custody After Being Handcuffed To Back Of Police Van and Dragged Down Street By Police
http://www.youtube.com/embed/glV9zcmHbFc?rel=034 A new command I give you: Love one another. As I have loved you, so you must love one another.
35 By this everyone will know that you are my disciples, if you love one another.
Steve Bell on the 10th anniversary of the Iraq war
Tony Blair says, "I've long since given up trying to persuade people that it was the right decision to invade IraqChina claims most cyber-attacks on its
military websites have US originBeijing says defence ministry and another site subjected to 1.7m attacks last year, two-thirds of which came from within America
Reuters in Beijing, guardian.co.uk, Thursday 28 February 2013 05.15 EST, Article Source
China denies allegations made earlier this month that a Chinese military unit was probably
behind a series of hacking attacks mostly targeting the US. Photograph: Andy Wong/APTwo Chinese military websites were subject to about 144,000 hacking attacks a month last year, almost two-thirds of which came from the US, China's defence ministry has said.
Earlier this month a US computer security company said a Chinese military unit was probably behind a series of hacking attacks mostly targeting America, triggering a war of words between Washington and Beijing. China denied the allegations and said it was the victim.
Beijing has now provided some details for the first time of the alleged attacks from the US. "The defence ministry and China military online websites have faced a serious threat from hacking attacks since they were established, and the number of hacks has risen steadily in recent years," said a ministry spokesman, Geng Yansheng, on Thursday.
"According to the IP addresses, the websites were, in 2012, hacked on average from overseas 144,000 times a month, of which attacks from the US accounted for 62.9%."
The comments were made at a monthly news conference, which foreign reporters are not allowed to attend, and posted on the ministry's website.
Geng said he had noted reports that the US planned to expand its cyberwarfare capability but that they were unhelpful to increasing international co-operation towards fighting hacking.
"We hope that the US side can explain and clarify this," he added.
The Unit 61398 building. Photograph: Peter Parks/AFP/Getty ImagesThe US security company, Mandiant, identified the Shanghai-based Unit 61398 of the Chinese army as the most likely culprits behind the hacking targeting America. Mandiant said it believed the unit had carried out "sustained" attacks on a wide range of industries.
The hacking dispute adds to diplomatic tension between China and the US, already strained by Chinese suspicion about Washington's motives in Asia and arguments over issues from trade to human rights.
Politicians Have Sex With Their Mothers ???
Republicans Stole 2.3 Trillion Dollars
... or More ... From U.S. Tax Payers?and Democrats Don't Shive A GiT
Local Report ~ Yahoo Links ~ Bing Links
How convenient, ... the day before 9/11 Neocon, Republican, War Criminal Donald Rumsfeld admitted 2.3 Trillion U.S. Tax Dollars was missing and to the best of recollections over 9 Billion U.S. tax payer dollars spent on an illegal Iraq war are also missing, while
Republicans Hold U.S. Tax Payers Hostage
Over Budget sequestrationIs War Criminal Condoleezza Rice
A Pedophile Pervert?Condoleezza Rice was the First to Authorize Torture
Local Report ~ Yahoo Links ~ Bing Links
Seymour Hersh says the US government has videotapes of boys being sodomized at Abu Ghraib prison in Iraq.
"The worst is the soundtrack of the boys shrieking," the reporter told an ACLU convention last week. Hersh says there was "a massive amount of criminal wrongdoing that was covered up at the highest command out there, and higher."
Children sodomized at Abu Ghraib
By Geraldine Sealey, Salon, Article Source
After Donald Rumsfeld testified on the Hill about Abu Ghraib in May, there was talk of more photos and video in the Pentagon’s custody more horrific than anything made public so far. "If these are released to the public, obviously it’s going to make matters worse," Rumsfeld said. Since then, the Washington Post has disclosed some new details and images of abuse at the prison. But if Seymour Hersh is right, it all gets much worse.
Hersh gave a speech last week to the ACLU making the charge that children were sodomized in front of women in the prison, and the Pentagon has tape of it. The speech was first reported in a New York Sun story last week, which was in turn posted on Jim Romenesko’s media blog, and now EdCone.com and other blogs are linking to the video. We transcribed the critical section here (it starts at about 1:31:00 into the ACLU video.) At the start of the transcript here, you can see how Hersh was struggling over what he should say:
"Debating about it, ummm … Some of the worst things that happened you don’t know about, okay? Videos, um, there are women there. Some of you may have read that they were passing letters out, communications out to their men. This is at Abu Ghraib … The women were passing messages out saying ‘Please come and kill me, because of what’s happened’ and basically what happened is that those women who were arrested with young boys, children in cases that have been recorded. The boys were sodomized with the cameras rolling. And the worst above all of that is the soundtrack of the boys shrieking that your government has. They are in total terror. It’s going to come out."
"It’s impossible to say to yourself how did we get there? Who are we? Who are these people that sent us there? When I did My Lai I was very troubled like anybody in his right mind would be about what happened. I ended up in something I wrote saying in the end I said that the people who did the killing were as much victims as the people they killed because of the scars they had, I can tell you some of the personal stories by some of the people who were in these units witnessed this. I can also tell you written complaints were made to the highest officers and so we’re dealing with a enormous massive amount of criminal wrongdoing that was covered up at the highest command out there and higher, and we have to get to it and we will. We will. You know there’s enough out there, they can’t (Applause). …. So it’s going to be an interesting election year."
Notes from a similar speech Hersh gave in Chicago in June were posted on Brad DeLong’s blog. Rick Pearlstein, who watched the speech, wrote: "[Hersh] said that after he broke Abu Ghraib people are coming out of the woodwork to tell him this stuff. He said he had seen all the Abu Ghraib pictures. He said, ‘You haven’t begun to see evil…’ then trailed off. He said, ‘horrible things done to children of women prisoners, as the cameras run.’ He looked frightened."
So, there are several questions here: Has Hersh actually seen the video he described to the ACLU, and why hasn’t he written about it yet? Will he be forced to elaborate in more public venues now that these two speeches are getting so much attention, at least in the blogosphere? And who else has seen the video, if it exists — will journalists see and report on it? did senators see these images when they had their closed-door sessions with the Abu Ghraib evidence? — and what is being done about it?
(Update: A reader brought to our attention that the rape of boys at Abu Ghraib has been mentioned in some news accounts of the prisoner abuse evidence. The Telegraph and other news organizations described "a videotape, apparently made by US personnel, is said to show Iraqi guards raping young boys." The Guardian reported "formal statements by inmates published yesterday describe horrific treatment at the hands of guards, including the rape of a teenage Iraqi boy by an army translator.")
Martin Rowson
Sweet Condi & the Asspirate Neocon BandAccording to a Senate Intelligence Committee Memo, George Bush's National Security Adviser, Condoleezza Rice, was the first person to verbally approve torture during July 2002 ... and then there was this:
BEN-VENISTE: Isn't it a fact, Dr. Rice, that the August 6 [2001] PDB warned against possible attacks in this country? And I ask you whether you recall the title of that PDB?
RICE: I believe the title was, "Bin Laden Determined to Attack Inside the United States [using planes]."
Is Neocon Republican War Criminal
John Bolton In Prison, Yet?Arrest of Pentagon Official May Help Unravel Neo-Conservative Cabal
This article appears in the May 13, 2005 issue of Executive Intelligence Review.
by Jeffrey Steinberg, Executive Intelligence Review, Article Source
Pentagon Iran desk officer and neo-con patsy Larry Franklin was arrested on May 4, on charges that he passed classified information based upon secret Pentagon documents to two American Israel Public Affairs Committee (AIPAC) officials in June 2003, at a restaurant in Arlington, Va. The two AIPAC officials, who were not named in the complaint, were Steve Rosen and Keith Weissman, who were both fired by AIPAC in recent weeks.
A number of senior intelligence sources, reached for comment on the Franklin charges, all had the same essential reading: The FBI has a prima facie case against Franklin. In FBI raids on his home, Federal agents confiscated 83 classified documents, which he was not authorized to have there. The case is cut and dried, and a charge of mishandling classified documents carries a ten-year Federal jail sentence. Franklin is being squeezed to provide prosecutors with a complete picture on the AIPAC/Israel espionage operation, including Pentagon officials who were part of the effort. These include, but are not limited to: Doug Feith, William Luti, Harold Rhode, and Abram Shulsky.
In addition, one source emphasized the importance of Franklin's December 2001 trip to Rome, accompanied by Rhode and Michael Ledeen. The trip centered around a meeting with former Iran-Contra swindler Manucher Ghorbanifar, whom Ledeen sought to reactivate as a Pentagon channel to the Iranian government, and as a source on activities inside Iraq and Afghanistan. The Rome trip coincided with the surfacing of the forged Niger government documents, falsely charging that Saddam Hussein was seeking large quantities of yellow cake uranium from the African nation.
Franklin was arrested on a criminal complaint, even as a grand jury continues to consider his case. He is widely considered to be providing information to prosecutors. A closer look at his associations with the neo-con crowd shows that by targetting him, FBI officials might be able to unravel a whole skein of wrongdoing, which could help bring down the inner circle linked to Vice President Dick Cheney.
Preparing To Hit Iran?
The investigation of Franklin, and his dealings with the AIPAC officials, first was made public in August 2004, in the immediate wake of a major propaganda barrage promoting pre-emptive military action against Iran. As head of the Iran desk at the Pentagon, Franklin had access to classified documents related to that area; according to the criminal complaint, he allegedly disclosed Top Secret information related to potential attacks upon U.S. forces in Iraq, to the two individuals, neither of whom had the security clearance to receive that information. At the time, Lyndon LaRouche estimated that patriotic sections of the U.S. intelligence community were acting to defuse a potential Israeli "breakaway ally" hit against Iran.
It was not only AIPAC officials with whom Franklin was in touch. He is reported to have also had meetings with Naor Gilan, until recently an Iran specialist at the Israeli Embassy in Washington. And, according to both the New York Times and Associated Press on May 5, FBI officials recently questioned a former senior Mossad official about his ties to Franklin. The official was Uzi Arad, a former senior official with the Israeli intelligence agency. Arad is reported to have told the FBI that he had met Franklin twice, and received an academic paper from him.
Arad is no garden variety Mossad agent. He held senior posts from 1975 to 1999, and served as the Foreign Policy Advisor to Prime Minister Benjamin Netanyahu. After the FBI probe of Franklin was announced Aug. 29, 2004, Azad was one of the Israelis who jumped to defend Israel against the allegations that Franklin had passed them classified documents, saying that at worst the analyst (Franklin) "crossed the line" by inappropriately disseminating sensitive material. "That is not espionage," he said.
Azad is also notable for the fact that, in a speech at the Jerusalem Institute for Contemporary Affairs on March 26, 2003 (five days into the Iraq War), he called on the United States and Israel to take military action against Iran as well. The luncheon meeting which Franklin had with the AIPAC officials, at which he allegedly passed them classified information, occurred on June 26, 2003.
Who Is Larry Franklin?
Sources in the military and intelligence community have provided this news service with a profile of the suspected Israeli mole: Larry Franklin is a Defense Intelligence Agency (DIA) analyst, who shifted from Cold War Soviet studies, to a specialty in Iran-Iraq. A protégé of DIA Sovietologist Winnifred Joshua, Franklin also studied at Johns Hopkins University's School of Advanced International Studies (SAIS), where he was reportedly picked up by Paul Wolfowitz, then-Deputy Secretary of Defense, and an individual who has been probed for passing U.S. secrets to Israel since 1978, according to a February 2004 study by Stephen Green, which catalogued long-standing espionage allegations against, and investigations into Wolfowitz, Feith, Michael Ledeen, Stephen Bryen, and Richard Perle.
In the Summer of 2001, Franklin was transferred from DIA to the Pentagon's policy office under Feith, where he took charge of the Iran desk in the Near East South Asia (NESA) section, and later worked for the Office of Special Plans (OSP), the Iraq war-planning unit under Feith and NESA head William Luti. Luti had been a military aide to former Speaker of the House Newt Gingrich, and had been in the Office of Vice President Cheney at the start of the "Bush 43" Administration. According to Lt. Col. Karen Kwiatkowski (USAF, ret.), who served in NESA from June 2002 to March 2003, Luti bragged at staff meetings, that he was reporting directly to "Scooter," which, she learned, was a reference to Cheney's chief of staff, I. Lewis "Scooter" Libby.
As an Air Force Reserve officer, Franklin had served several tours of duty at the U.S. Embassy in Tel Aviv, where, according to one military source, he had gotten in trouble for unauthorized contacts with Israeli intelligence officials. According to one news account, the current FBI probe into Franklin's activities was triggered by a June 2002 leak in the New York Times, which detailed American war plans against Iraq. While on the NESA Iran desk, Franklin was also reportedly the subject of a probe into his mishandling of classified documents; however, a serious probe into that incident was blocked by the intervention of Luti and Feith, according to a confidential Pentagon source.
Franklin, according to an eyewitness, was part of a neo-con inner circle that met frequently, behind closed doors, in the office of Doug Feith. The group included Feith, Luti, OSP official Abram Shulsky, Office of Net Assessment Mideast specialist Harold Rhode, former Defense Policy Board Chairman Richard Perle, David Wurmser, and Michael Maloof. As a group, they worked closely with Wolfowitz and with Libby, whose own ties to the Israeli Mafiya and Israeli intelligence run deep: Libby was the former attorney for Israeli "Mafia" boss Marc Rich.
Franklin, Rhode, and Ledeen
In the Summer of 2003, it was revealed that Larry Franklin had been part of a Pentagon team, composed also of Rhode and self-professed "universal fascist" Michael Ledeen, which had travelled to Rome, in December 2001, to open unauthorized channels to the Iranian government, through a widely discredited Iran-Contra figure, Manucher Ghorbanifar. According to one news account of the trip, the troika sabotaged talks then under way between the State Department and the Iranian government, involving the turning over to the United States of five top al-Qaeda figures, who were in custody in Iran.
Virtually every member of the neo-con grouping has been under investigation for espionage, fabrication of intelligence, and other treachery against the United States. Sources, for example, have identified Rhode, a longtime protégé of British intelligence's Dr. Bernard Lewis, and a close collaborator of Ledeen, as the target of a separate espionage probe, involving his passing of U.S. national security secrets to Israel, while he was in Baghdad as part of the Coalition Provisional Authority (CPA). While in Baghdad, Rhode practically lived out of the home and office of Iraqi National Congress (INC) head Ahmed Chalabi.
Ledeen is also, according to law enforcement sources, a target of inquiry, concerning his suspected role in passing forged Niger government documents to the Italian intelligence service, SISMI. The forged documents purported to "prove" that Iraq was seeking uranium from Niger, to build a nuclear bomb. Vice President Cheney and other Bush Administration officials used the threat of Iraq's alleged imminent possession of a nuclear bomb, as a bludgeon to force Congressional approval of the Iraq War. When President Bush cited alleged Iraqi efforts to obtain uranium "yellow cake" from an African state in his Jan. 28, 2003 State of the Union address, the whole issue blew up, leading to the ongoing Federal criminal probe.
Although both the State Department and CIA had cautioned that the Niger yellow cake story was dubious, Bush and Cheney went ahead with their shrill allegations. Then-International Atomic Energy Agency (IAEA) director Dr. Mohammed ElBaradei revealed in early March 2003, that the Niger documents were shoddy forgeries. According to several former U.S. intelligence officials, one prime suspect in the document forgeries scam was Chalabi's INC. Ledeen, a longtime Chalabi booster, has also long been a paid "consultant" to SISMI. A September 2004 Washington Monthly article reports that when Ledeen, Franklin, and Rhode met in December 2001 with Iranian government officials in Rome, the head of SISMI and Italy's Minister of Defense also attended the meetings.
A Bolton Angle?
While the issue of Pentagon illegal activity with Israel, in order to provoke a war against Iran, or Syria, is still a live one, so is the matter of the Niger "yellow cake" concoction, a story which has never been solved, and which is intimately connected with the still live investigation of what is known as the Plame leak.
It was December 2001, after the Ledeen, Franklin, Rhode trip to Rome, that fraudulent documents surfaced, alleging that Iraq was negotiating for yellow cake from Niger. In the Spring of 2002, reportedly on the recommendation of Vice President Cheney, former U.S. Ambassador Joe Wilson was sent to investigate the charges, and returned a report saying that the claim was false. In the Summer of 2003, Wilson was subjected to an attempt to discredit him in the media, including through the disclosure of the identity of his wife, covert CIA operative Valerie Plame. The disclosure of Plame's identity was a violation of Federal law, but, as yet, the Administration has not "solved" the case. A Federal Special Prosecutor is still pursuing the case of the leak, which many sources report to have originated from the vicinity of Cheney's office.
On the strength of Wilson's report, and other analysis, the CIA and the State Department removed the Niger report from their intelligence estimates of Iraq's pursuit of weapons of mass destruction. Yet, in December 2002, Under-Secretary of State for Arms Control and International Security Affairs John Bolton played a key role in putting this false information in a widely circulated State Department Fact Sheet on "Omissions From the Iraqi Declaration of the United Nations Security Council."
In a March 1, 2005 letter to the chairman of the National Security Subcommittee of the House Government Reform Committee, Rep. Henry Waxman (D-Calif.) asked for a committee investigation into State Department efforts to conceal the role of Bolton in the creation of the Fact Sheet, and in insisting that the Niger reference be kept in the Fact Sheet, despite objections from both State Department intelligence and CIA officials.
This inquiry has relevance not only to Bolton's potential connection to an espionage network, but to his persistent role in "fixing" intelligence which he and his neo-con friends did not like. It was this cooking of intelligence which provided the justification for pushing the United States into war against Iraq, in pursuit of WMD which were not there, and which the neo-con circles around Dick Cheney continue to carry out in pursuit of the new wars they have on their agenda.
+++ More on John Bolton Here and Here.
Why does Stanford University Continue to Protect Rice and Rumsfeld?
Why Supreme Court
Will Not Stand By U.S. Citizens?List of United States Supreme Court Justices appointed by War Criminal Ronald Reagan
Antonin Scalia & Anthony Kennedy
List of United States Supreme Court Justices appointed by War Criminal George H. W. Bush
David Souter & Clarence Thomas
List of United States Supreme Court Justices appointed by War Criminal George W. Bush
John G. Roberts & Samuel Alito
Supreme Court to democracy: Drop dead
With a single rash, partisan act, the high court has tainted the Bush presidency, besmirched its own reputation and soiled our nation's proudest legacy.
By Gary Kamiya, Salon's executive editor
Dec. 14, 2000 | Tuesday, Dec. 12, is a day that will live in American infamy long after the tainted election of George W. Bush has faded from memory.With their rash, divisive decision to dispense with the risky and inconvenient workings of democracy and simply award the presidency to their fellow Republican, five right-wing justices dragged the Supreme Court down to perhaps its most ignominious point since the Dred Scott decision.
The court was the last American civic institution to have preserved an aura of impartiality, to be regarded as above the gutter of partisanship and self-interest. The reality, of course, is that no court, no judge, no human being, is completely free of those entanglements. Yet the court has generally acted wisely in avoiding judgments that would inevitably and utterly besmirch it. With one reckless and partisan ruling, it squandered its most precious possession: its reputation. It may take years, even decades, to repair the damage done by the Scalia-Rehnquist court's decision to cancel the election and crown the winner.
It's hard not to conclude, now that this whole sorry saga is over, that the fix was in from the beginning. Not the crude, "vast right-wing conspiracy" fix of Hillary Clinton's imagination, but a de facto fix. Why shouldn't one think the game was rigged, when five Republican-appointed justices -- one of whose son works for the law firm of the lawyer representing Bush, another of whose wife is recruiting staff for the Bush admininstration and two of whom have made clear their desire to retire under a Republican administration -- trashed their entire judicial philosophy to ram through, with only the most cramped of legal justifications, a last-second victory for a Republican who lost the national popular vote and, when the votes in Florida are actually counted, is likely to have lost the Florida one as well?
Perfect justice does not exist. But this was judicial folly, politically explosive and judicially threadbare. This was the court stepping in and awarding victory to one side before the game was over. Even those of us who don't often agree with the court's conservative majority expected better.
As Justice Stevens wrote in his savage dissent, "The position by the majority of this court can only lend credence to the most cynical appraisal of the work of judges throughout the land ... Although we may never know with complete certainty the identity of the winner of this year's election, the identity of the loser is perfectly clear. It is the nation's confidence in the judge as an impartial guardian of the rule of law." [Continue Reading]
Call for: CONSTITUTIONAL CONVENTION
To Remove TRAITOR Politicians
Who Would Abolish United States Liberty and FreedomsDear Citizens of the World,
We have a Pandora's box of mischief with which to snare you. We can have you in court so long, you will never get out. We can easily drain away all your assets over one pretext or another. We have an inexhaustible fund with which to draw from to pay our lawyers.
These lawyers are paid by you in the form of taxes. You do not have this vast supply of wealth. We know how to divide and conquer. Have we not brought down rulers of countries through our devices?
Do you think your tiny self will be any match for us? [Continue Reading]
Have You Been Scroogled?
Think Google respects your privacy? Think again. Article Source
Google goes through every Gmail that's sent or received, looking for keywords so they can target Gmail users with paid ads. And there's no way to opt out of this invasion of your privacy. Outlook.com is different—we don't go through your email to sell ads.
Watch the video to see how you get Scroogled:
http://www.youtube.com/embed/anFSX2WltPc?rel=0Tell Google To Stop!
Let them know they shouldn't go through your email to sell ads. Warn Your Friends!
Target: Eric Schmidt, Executive Chairman of Google
Sponsored by: Outlook.comGoogle earns money by violating your privacy. They go through every word of your personal Gmail so they can target you with ads.
Every word of every email. Even the most private ones, like messages about relationships, health care, finances, and more. Do you feel violated yet?
Even if you don't use Gmail, Google will still go through emails you send to Gmail addresses in order to sell ads -- despite you never having agreed to their terms of service. There is absolutely no way to opt out, whether you use Gmail or not.
It's time to take back your privacy. Sign this Petition and tell Google to stop going through your emails to sell ads.
[Note: ~@~ will no longer respond to email using AT&T, Cablevision, Comcast, Time Warner Cable, Google, or Verizon domains.]
~Six Strikes~ Anti-Piracy Scheme,
Instituted By Corporate Criminals, Starts Monday
The much-discussed U.S. six strikes anti-piracy scheme is expected to go live on Monday. The start date hasn't been announced officially by the CCI but a source close to the scheme confirmed the plans. During the coming months millions of BitTorrent users will be actively monitored by copyright holders. After repeated warnings, Internet subscribers risk a heavy reduction in download speeds and temporary browsing restrictions.
During the summer of 2011 the MPAA and RIAA teamed up with five major Internet providers in the United States, announcing their a plan to warn and "punish" BitTorrent pirates.
The parties launched the Center for Copyright Information (CCI) and agreed on a system through which Internet account holders will be warned if their connections are used to commit copyright infringement. After five or six warnings ISPs may then take a variety of repressive measures.
Initially the first ISPs were expected to send out the first "copyright alerts" by the end of 2011, but for reasons unknown this deadline silently passed, as did the revised July 2012 and the December 2012 start dates.
But it appears that the wait is over now.
TorrentFreak learned from a source close to CCI that the system is currently scheduled to launch early next week, and we're not the only ones. Another sign of the start of the program is that a few days ago the CCI launched their new website. This is where recipients of the copyright alerts will be directed to.
The website explains how the copyright alert system works and lists places where people can download and stream music and movies legally. It also lists details about the appeals process for people who want to dispute one of the warnings.
Unfortunately the new website does not give an overview of the punishments or mitigation measures that Internet subscribers will be subjected to.
We previously learned that AT&T will block users' access to some of the most frequently visited websites on the Internet, until they complete a copyright course. Verizon will slow down the connection speeds of repeated pirates, and Time Warner Cable will temporarily interrupt people's ability to browse the Internet.
It's expected that the two remaining providers, Cablevison and Comcast, will take similar measures. None of the ISPs will permanently disconnect repeat infringers as part of the plan.
Of course, there are plenty of ways for people to prevent being monitored by copyright holders. BitTorrent proxies and VPN services are the most likely option here. These services replace a user's home IP-address with one provided by the proxy service, making it impossible for tracking companies to identify who is doing the file-sharing.
Also, those who download through Usenet, cyberlockers or other non-P2P services can not be monitored by the copyright alert system at all.
These circumvention options are not news to the copyright holders and the ISPs. CCI Executive Director Jill Lesser previously said that the main purpose of the alerts is to educate the public, and that hardcore pirates are not the target of the system.
TorrentFreak asked the CCI if it had any idea how many alerts would be sent out in the first few months of the scheme, but the organization didn't want to make any predictions. We will find out more in the weeks to come. The same is true for the backdoor lawsuit option that was baked into the plan. ~ Article Source
Telecom Crimes & Punishment
Nobody was charged with a crime, during the Republican, war criminal Bush Administration, when corporate criminals 'knowingly' broke laws and illegally spied on U.S. citizens, with Democrat Help:
Violation of the Fourth Amendment to the Constitution
Violation of the First Amendment to the Constitution
Unlawful electronic surveillance or disclosure or use of information obtained by electronic surveillance in violation of 50 U.S.C. §1809.
Unlawful interception, use or disclosure of Class communications in violation of 18 U.S.C. § 2511
Unlawful solicitation and obtained disclosure of the contents of communications in violation of 18 U.S.C. § 2702(a)(1) or (a)(2)
Unlawful solicitation and obtained disclosure of non-content records or other information in violation of 18 U.S.C. § 2702(a)(3)
Violation of the Administrative Procedures Act
Violation of the constitutional principle of separation of powers
[Continue Reading Crimes and Punishment]
On Monday, February 25, 2013, these Criminals will employ a new Copyright Alert System:
and a lot of Innocent People will get hurt.
For Example:
The 14 Most Ridiculous Lawsuits
Filed by the RIAA and the MPAA
Nine years ago the RIAA won a groundbreaking suit against Napster.com in what would become the beginning of a nearly decade-long flood of litigation. The incident seemed to be a tipping point for the Entertainment Industry, as both the RIAA and MPAA up until then had enjoyed little success in stemming the piracy movement which was growing at exponential rates across the world. Peer-sharing, while still relatively new at the time, looked like it would be snuffed out in the legal battles to come; the populace that had taken to services like Napster were too afraid to continue for fear of being sued.
The RIAA alone had managed to sue upwards of 35,000 people after their win against Napster, and when they had finally announced in late 2008 that they would stop filing lawsuits on a grand scale, they still reserved the right to sue particular offenders whom they deem to be the worst. In the meantime, the duo turned their attention to the Internet Service Providers, in an attempt to exert a measure of force on those companies to handle offenders by disallowing them internet access, a move which the European Union has declared something of a human rights violation. Showing colors strangely unlike any expected, American ISP's have actually resisted this pressure, disliking the implication that one industry can control another on little more than a whim.
The behavior of the RIAA/MPAA during the last decade has been nothing short of a schoolyard bully who has the teacher in his pocket. It's not just the consumers who've had enough of the Industry's nonsense, the ISP's and even the actors and musicians who just ten years ago claimed they were being robbed are now standing up to call out the associations for their wonton disregard for their own customer-base. It's important that it be stressed that it was not only the outlandish number of people that had been sued that brought this about, but several cases in which the RIAA, chiefly, managed to cross the line in such a way that the public could not help but demand action. Here we take a look at some of those most ridiculous suits they filed that they immediately regretted, as well as some associated lunacy that could affect you.
The Late Larry Scantlebury
Seven different recording labels banded together to bring the fight against a man named Larry Scantlebury. Larry was a vietnam veteran who loved reading books in his spare time, along with spending time with his wife and spoiling his three grandchildren. The RIAA was suing Larry for allegedly stealing their content, as usual, when during the long drawn-out process, he died. Where normally this kind of incident would lead to candle-light vigils, and scandal about a man dying while being sued by the RIAA, this only got more vile. Immediately upon hearing that the accused had passed away, Warner's lawyers told his surviving family members that they had 60 days to grieve before their depositions were expected, and at that time the RIAA would consider amending the charges before moving on with the case, against them.
Fred Lawrence and His Grandson
The MPAA sued a Wisconsin Grandfather named Fred Lawrence for illegally downloading four movies via peer-to-peer sharing. True to form, they contacted him demanding $4,000 with the threat that if they didn't get paid, he'd be facing a lawsuit; when Mr. Lawrence flatly refused to pay them he found himself facing a potential $600,000 in damages. As it turns out, his 12-year-old grandson had downloaded the movies for no particular reason, since they already owned three of the four offending titles. This entire episode was especially stressful to Mr. Lawrence, as legal experts explained to him that even if he fight and won against the MPAA, the association would be fully within their rights to sue his grandson afterwards.
Sarah Ward: Mega-Pirate
Mrs. Ward was a 66-year-old retired schoolteacher who sculpted in her spare time, and suffered from mild dyslexia. She rarely used the computer for anything more than checking her e-mail, or the weather, and enjoyed listening to celtic or folk music. The RIAA sent her notice in late 2003 that she was being sued for illegally downloading and trafficking several million dollars worth of music using the peer-to-peer file-sharing program and network KaZaA. Specifically cited in the charges was her extreme pirating of artist Snoop Dogg. Also interesting to note is that KaZaA was strictly a Microsoft Windows application at the time, and Mrs. Ward's old Apple machine would not have been running it.
Tanya Anderson
42-year-old single mother Tanya Anderson was informed by the RIAA in 2004 that she could either settle out of court or face legal action for her early morning piracy antics. She learned that she had apparently been downloading the rap song "Shake that Ass, Bitch" at 4:24 in the morning under the username "gotenkito." This was news to her, and she promptly counter-sued the RIAA under state Racketeering laws. At the time, she worked for the Department of Justice, but was forced to leave for health reasons shortly after her legal woes began. She was severely disabled, and with the loss of her job added to the already soaring legal fees she was in for hard times. To put a nice cap on it all, the RIAA not only called her 10-year-old daughter's school impersonating the girl's grandmother in an attempt to get information from her, but they also threatened to "interrogate and confront her little girl at the offices of the RIAA lawyers" if Ms. Anderson did not drop her counter-claim, which she disclosed in her deposition against them.
Lola Scruse
In 2006 a grandmother of three, Lola Scruse, who was also 66 years old, and on dialysis. She lived off of Social Security checks, and she didn't know much of anything about computers or the internet other than the fact that she owned one and paid for the other. Her grandchildren would use her computer when they were over to visit. Lola was informed by the Court that she owed $6,000 for 872 songs that she had downloaded illegally, and that she had already lost the case due to default judgement since she never responded to the initial lawsuit. She was already handling monstrous medical bills for the dialysis, and now with this figure added, she was quite upset. Lola's since been more mindful of what her grandchildren are doing on her computer, and the RIAA has since targeted more grandmothers who don't respond to strange court documents about things they don't understand.
Berry the Hobo
Chaz Berry fell on hard times, and became one of New York City's thousands of homeless people. He was going about his business in early 2007, presumably just being homeless, when he found out that he was being sued by the RIAA for copyright infringement. Apparently, the Industry lawyers had found that they couldn't locate Mr. Berry, and were aware that he was in fact homeless. That didn't stop the process server from adhering the summons to the door of his former apartment. They reported to the Court that they had "made every effort" to locate Mr. Berry, and requested default judgement in the case. After much legal ado, the case was dropped against Mr. Berry, and the RIAA barely escaped the courtroom without sanctions on their legal team.
Jammie Thomas: First in Court
In 2007 the RIAA took a case all the way to a jury in Federal Court, suing Jammie Thomas on 24 counts of illegal file-sharing. This was the first case to go all the way to court, as every other had either been settled or was tied up in litigation and negotiating settlement. Being the first, it was extremely important to both sides of the issue, which at the time was red-hot in all media venues. At the time of the trial, well over 20,000 other suits were active, and the RIAA had a point to prove. In the end, the jury found Thomas guilty on all 24 counts, and set an award to the plaintiff of $222,000, despite the testimony of expert witnesses that proved a degree of reasonable doubt.
The Displaced Granny: Rhonda Crain
In 2006 Ms. Crain, a grandmother who had been displaced by Hurricane Katrina to East Texas, was told by the RIAA that she had the option to pay them the pittance of $4,500 or see them in court. They explained to her that they knew all about her KaZaA account name "kcrain" and that her sharing of tracks by the likes of Usher and 50 Cent, totalling 572 songs, were well documented. Ms. Crain ended up settling in court with the RIAA under stipulations that she delete the offending files, and she did not have to pay them any damages. The judge in this case had decided that simply paying for internet access that someone else uses to download files does not make a person entirely liable for those downloads. It's too bad Mrs. Scruse didn't have that judge.
Brianna LaHara
At just 12 years old, Brianna LaHara was forced into settlement with the RIAA and had to pay $2,000 in damages for illegally sharing music. The breakdown was roughly two dollars per song. Out of 261 defendants in the first round of mass-suits, Brianna was the first to settle. At the time, the association had stated that it was only going after offenders who had been shown to have shared more than 1,000 songs illegally, and that anyone who stepped forward before a suit was filed against them would be given amnesty, though only for tracks officially represented by the RIAA. Not many people actually took the chance, since it would have only opened them up to secondary suits from interest groups working in tandem with the RIAA. This also came at the same time that the association was targeting universities and the students who used their networks to acquire music through them.
The Ghost of Gertrude
83-year-old Gertrude Walton was sued for illegally sharing over 700 songs on peer-to-peer file-sharing networks in early 2005, under the username "smittenedkitten." The problem with the case, was that Gertrude Walton not only did not own a computer, or know how to use one, but had in fact died in December of 2004. The RIAA quickly dismissed the case, after the entire known world laughed them out of court.
Tenenbaum Fights Back
In 2007 a man named Joel Tenenbaum decided not to settle and took his case all the way to court when he was sued by the RIAA. He began the adventure defending himself, but as time wore on, the RIAA lawyers delayed as much as possible, stalling whenever the opportunity presented itself. When the delays and court actions got too thick for him to handle without help, a Harvard Law professor named Charles Nesson stepped in to carry the mantle. The team then proceeded to not only stand their ground, but to attack the RIAA in both open court and open media. Not stopping their, Tenenbaum and Nesson called on the Court itself, declaring that allowing the RIAA to sue for such large amounts was unconstitutional, and violates Due Process. To truly make their point sink in, and gain massive attention Nesson brought to the foreground the fact that the RIAA itself used the very same argument in its own defense in a previous round of suits in which it was accused of the unauthorized use of music samples.
The Pirate Bay
Of all the sites on the internet dealing with peer-to-peer sharing, The Pirate Bay is widely known as the largest and most established. Based in Sweden, TPB has operated with near-impunity to American copyright laws, at least until recently. The MPAA tried repeatedly, at one point on a weekly basis, along with its sister association the RIAA, as well as several other special-interest groups and even Microsoft itself, to frighten the operators of the site to shut down by threatening legal action. In 2006 the MPAA released a public memorandum exalting in their success and stating that TPB had been shut down, and commending the U.S. and Swedish authorities for doing such a wonderful job in "the raid". There was a raid, and there were technically arrests, and seizures, but TPB was only shut down for 3 days and largely unaffected by the loss of equipment. The MPAA's press-release actually backfired, and became a more effective marketing tool for the Swedish Pirate Bay here in the U.S. than anything they could have done themselves. It read like an advertisement, showcasing what is available, for free, if one were to visit TPB. The full release can be read here [Note: The MPAA has removed this file which was originally located at: http://www.mpaa.org/press_releases/2006_05_31.pdf ???]. When the site came back online, it had an even larger following than it had before the raid. In 2009, after amendments to Swedish laws, the Pirate Bay founders were put on trial for breaking Swedish copyright laws; this was the first time they could be prosecuted by anyone. In the end, all four founders of the site were convicted on less than half the original charges, and sentenced to one year in prison and required to pay large award sums to the groups behind the suit. Under Swedish laws, however, no sentence is legal until all appeals are carried out in full, meaning The Pirate Bay's founders are unaffected by the outcome and will remain so for several more years to come.
Sue and Sue Alike: Real Networks vs. MPAA
IN 2008, during the feverish litigation-fest the U.S. Government was hosting for the MPAA lawyers, Hollywood reacted violently to a new piece of software released by Real Networks, called RealDVD. The software was simple, it basically broke the Industry's DRM (Digital Rights Management) on DVD's so that consumers could copy the DVD or save it to their computer for posterity. The MPAA began using the Digital Millenium Copyright Act, or the DMCA as it's more commonly known, to sue every entity that has come in contact with this DRM-bypassing software. The drama became even more spectacular when Real Networks turned the tables and counter-sued the MPAA, and demanded the court rule that their software be legitimized under a previously-established set of laws governing software and technology for the consumer. Technically, at that point, both sides had laws to substantiate their own claims, and the entire ordeal became a media fiasco dubbed "Dumb and Dumber" in the headlines. Recently, the MPAA has accused Real Networks of destroying evidence that showed the source of their code, which they claim to be "hackers."
Shawn Hogan
When the MPAA attempted to get a piece of the action by suing Shawn Hogan for illegally sharing Meet the Fockers in 2006, the case received a lot of media attention. This was partially because of the fact that Shawn never shared the movie, nor did he download it to begin with. He also owned the movie on DVD, but this wasn't what had made headlines; Shawn's ire for justice at being slandered in such a way drove him to hire a legal team to prove that the MPAA was wrong, and in their research they discovered that the Industry never actually owned the copyright to the movie in the first place due to clerical errors at the time of the filing. The case was quickly dismissed.
These ridiculous cases aside, the RIAA and MPAA continue to wander around the internet harassing innocent bystanders as they see fit. The RIAA raised eyebrows again in late 2007 with the sudden declaration that ripping your own CD's to your computer is illegal, which surprised many owners of mp3-players who had read the manuals to their devices. As strange as this was, it didn't really surprise people, as RIAA had also just sued XM Satellite Radio only a year beforehand, for selling a receiver that could record songs. The MPAA recently made headlines by finally winning a case against the Pirate Bay in a landmark decision made by Swedish courts. The case will spend years in further litigation in Stockholm, but it was the verdict that nobody ever expected, given the amount of times the MPAA has targeted the Internet's most notorious peer-to-peer sharing hub. This is clearly an issue that has no clear end in sight, and in the meantime, the best anybody can do is cover their own end, whether they actually participate in piracy or not. ~ Article Source
Politicians Are the Real Criminals
None of They/Them End Up In Jail and
They Consistantly Tell U.S. To: Drop Dead
Six ways pirates can get around the coming 'Six Strikes'
By Darlene Storm, February 22, 2013 11:39 AM EST, Article Source
Last August, Google changed its search algorithms so sites would rank lower based on "the number of valid copyright removal notices" that Google received. But "demoting pirate sites" was not enough, according to Recording Industry Association of America (RIAA) report [PDF]. The RIAA said it has "found no evidence" that Google's plan is working since "these sites consistently appear at the top of Google's search results for popular songs or artists."
Despite the fact that the European Copyright Society (ECS) found that hyperlinking is not copyright infringement, the Hollywood-funded anti-piracy organization BREIN will not be happy until there is no daily limit on reporting "pirate links" to Google, and "wants to increase the daily DMCA cap from 10,000 to 40,000 and eventually remove the restrictions altogether." However, ECS wrote, "As Tim-Berners Lee, who is regularly accredited as being an inventor of the World Wide Web, has explained, a standard hyperlink is nothing more than a reference or footnote, and that the ability to refer to a document is a fundamental right of free speech."
The RIAA disagrees and if it had its way, even Google's auto-complete feature would be wiped clean of "piracy-inducing keywords." The RIAA report card concluded, "The search rankings for sites for which Google has received large numbers of instances of infringement do not appear to have been demoted by Google's demotion signal in any meaningful way, at least with respect to searches for downloads or mp3s of specific tracks or artists." Yet as Techdirt pointed out, most folks unhappy about their Google ranking would stop to learn about search engine optimization. Furthermore, the RIAA doesn't seem to understand that if logged into Google, then different people see different Google search results. The bottom line: "The RIAA will never, ever be satisfied until Google wipes out all infringement with the magic 'piracyBgone' button."
Speaking of piracy and the RIAA, the Six Strikes escalated warning system is about to kick in and the idea of Hollywood--an unelected body of industry-connected officials who get to police the Internet--being given that power is such a horribly flawed plan that it is nearly inconceivable the Copyright Alert System (CAS) will soon launch. AT&T, Cablevision, Comcast, Time Warner Cable, and Verizon have struck Six Strikes deals with the Center for Copyright Information devil (RIAA and MPAA members). Some of the ISPs' Six Strikes plans, like that of Verizon, have leaked out onto the net.
While not advocating piracy and I'm certainly not an expert on pirating, there seem to be many ways around Six Strikes--other than don't pirate.
1. Since Six Strikes targets BitTorrent users, they should use a VPN or anonymizing proxy service--only 16% of file-sharers hide their IP now. Apparently even some FBI pirates don't bother with hiding IPs, even though the FBI warns that pirating is a serious, not victimless, crime.
2. Switch over to Usenet or a similiar site.
3. Download from a free file-hosting service such as one listed in Google results that the RIAA is so vehemently opposed to.
4. Switch over to a streaming site without downloading movies. ICE may take it down, but you won't be targeted by the Copyright Alert System. Torrent Freak reported, "The copyright alerts only target a subgroup of online pirates, namely BitTorrent users. The millions of users of file-hosting services, Usenet and streaming sites are not going to be affected."
5. Switch to a higher priced business-class account with your ISP so your public Wi-Fi is considered "legitimate." Jill Lesser, Executive Director of the CCI, claimed that "legitimate" businesses like Starbucks with free Wi-Fi would be immune to "Copyright Alerts." Instead, "residential Internet accounts are the focus of our program." If "very small businesses like a home-office or a local real estate office" use a residential account instead of paying big bucks for a business account, then "if an employee of the small business, or someone using an open Wi-Fi connection at the business, engages in infringing activity the primary account owner would receive Alerts."
On The Media's Brooke Gladstone interviewed Lesser about the coming Six Strikes in general. To ensure it doesn't happen again when given an alert, aka a strike, one of the punishments is a tutorial for "ensuring their wireless connection is password protected." If and when the fifth and sixth alerts are issued, then after a "copyright tutorial," a residential-classed account will get cut down to slower-than-molasses speeds of 256kbps for two or three days. Although Lesser previously said Six Strikes was not "punitive," good luck trying to get anything done at those 1990s speeds.
6. Diehard 'casual' pirates could ride out the Six Strikes storm, since nothing more happens after the sixth warning. At the start of WYNC's OntheMedia interview, it was said that Six Strikes is supposed to "stop serial illegal downloaders." Later during the interview, when asked what happens if you get Strike 7, 8 or 9, Lesser said, "Once they've been mitigated, they've received several alerts, we're just not going to send them any more alerts. Because they are not the kind of customer that we're going to reach with this program." Nothing more "under this program" will happen. "For us it is reaching the casual infringer which is a large percentage of peer-to-peer piracy," Lesser stated.
The third-party tool MarkMonitor will be used to identify users who engage in copyright-infringing activities. It was approved as an accurate tracking methodology by an independent and impartial technical expert that is none other than Stroz Friedberg--a group that "was also the RIAA's lobbying firm for half a decade."
If you feel "wrongly accused" then there is a $35 'review fee' to see precisely what you are accused of. It's refunded if you win, but if the Copyright Alert System is so sure of itself then why charge at all? Why not let individuals know what they are accused of without this stipulation that the fee is to stop "frivolous appeals?"
Below is the Copyright Alert System and Six Strikes OnTheMedia interview of the Center for Copyright Information director Jill Lesser
Again, I'm not advocating that copyright infringement is right and people should pirate. People work hard to create music, movies, content and they should be paid for it. But just as I was opposed to SOPA, it seems wrong to give Hollywood this much power into our private lives and over the Internet.
Notes from ~@~ Listed Below:
Make Health Last. What will your last 10 years look like?
http://www.youtube.com/embed/Qo6QNU8kHxI?rel=0
Half of Michigan blacks disenfranchised by GOP war on Democracy
http://www.youtube.com/embed/tkU7N_ljLQM?rel=0
Thwart assault on voting rights
or risk return to 'old poison', NAACP warns
Debo Adegbile to go before supreme court to defend Voting Rights Act and argue key provision should not be struck down
Ed Pilkington, guardian.co.uk, Friday 22 February 2013 17.34 EST, Article Source
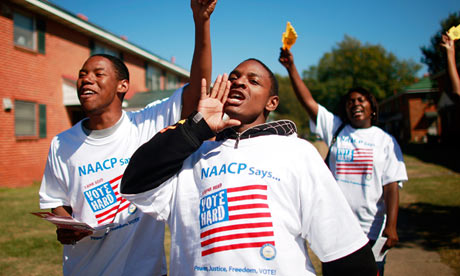
Wednesday's hearing is being seen as the greatest threat to the Voting Rights Act since
it was enacted in 1965. Photograph: Mario Tama/Getty Images
The lawyer who will next week go before the US supreme court to defend the Voting Rights Act has warned that if a key provision of the law that prevents discrimination at the polling booth largely in southern states is struck down, it would "set the hands of the clock winding backwards" for millions of minority voters.
Debo Adegbile, special counsel for the NAACP, the country's largest civil rights organisation, will have the momentous task on Wednesday of defending one of the mainstays of America's prolonged struggle against racial discrimination.
Lined up against him will be an array of conservative lawyers and legislators, many based in the south, where the sting of the legislation is felt most keenly.
Wednesday's hearing, in which the nine supreme court justices will hear oral argument before delivering a ruling expected in June, is being seen as the greatest threat to the Voting Rights Act since it was enacted in 1965. The focus of the debate will be Section 5, a provision under which 16 states – mainly though not exclusively in the south – are subject to stringent federal monitoring designed to prevent them discriminating against African American and other minority voters.
In Shelby County v Holder, representatives of one of the proscribed areas - Shelby County in Alabama – are calling on the justices to throw out Section 5 on the grounds that racial segregation and discrimination are in the past, and therefore such exceptional measures are no longer necessary. Under the terms of Section 5, any of the identified jurisdictions must seek "pre-clearance" from the Department of Justice or a federal court in Washington before they can make any substantial changes to their voting arrangements.
But Adegbile will go before the judges to argue that the blatant attacks on the voting rights of black and other minority citizens which the Act addressed were still very much a live problem. In comments to reporters, he said that there was an "unbroken chain of more than 100 years of intense and persistent discrimination against minority voters across large parts of the country."
The 1965 Voting Rights Act was one of the towering achievements of the civil rights movement and the presidency of Lyndon Johnson. It was passed at a time when hundreds of thousands of black voters were still effectively disenfranchised through a range of dirty tricks, some as crude as imposing a poll tax on voting that weeded out poorer, disproportionately minority, citizens.
The NAACP brief submitted to the supreme court ahead of the hearing points out that the jurisdictions covered by Section 5 have shown a consistent pattern of discriminatory behaviour. Between 1982 and 2006, the jurisdictions collectively tried to introduce 1,300 discriminatory voting measures, all of which were blocked under the Act.
Drawing on a phrase used in supreme court deliberations in the past, Adegbile said that the method of discrimination might have changed over time, but "old poison was being poured into new bottles". Alabama, the state from which next week's challenge originates, has had almost 240 discriminatory voting laws blocked over that period.
The NAACP brief notes that "purposeful discrimination by Alabama lawmakers persists to the present day". Though the population of the state is a quarter African American, there are still no black statewide elected officials.
In 2011, a federal court hearing a gambling case found that there was "compelling evidence that political exclusion through racism remains a real and enduring problem in Alabama" and that the desire to disenfranchise blacks remained "entrenched in the high echelons of state government". Several white legislators involved in the case were recorded on tape comparing black voters to "illiterates" and "Aborigines".
Paradoxically, Shelby County, the specific district that has brought the supreme court challenge, itself has dirty hands in terms of a persistent pattern of discriminatory offending. The county has a decades-old history of holding "at-large" elections – votes staged across the entire district to make sure that the majority white population always prevails.
It also has a history of "diluting" black representation by redrawing boundary lines to destroy majority-black districts. As recently as 2008, the small town of Calera in Shelby County introduced a redistricting plan that resulted in the defeat of the only black member of the city council – a move that was later overturned under the same section 5 of the Voting Rights Act that the leaders of Shelby County now want to strike down.
"This is not a theoretical concern," said Adegbile. "The Voting Rights Act is strong medicine, for a strong problem."
The enduring problem of electoral skullduggery in the US was on ample display during last year's presidential election. Mainly Republican-controlled legislatures introduced an unprecedented number of reforms that erected barriers to voting that disproportionately affected minority communities.
President Obama on Friday lent his voice to the defence of the Voting Rights Act. He said that if the safeguards were removed, "it would be hard for us to catch those things up front to make sure that elections are done in an equitable way".
Earlier this month Obama ordered the creation of a non-partisan commission to look into how the voting experience in the US could be improved, following evidence of considerable impediments, including long lines at the polls, last November.
Section 5 currently applies to nine states in their entirety: Alabama, Alaska, Arizona, Georgia, Louisiana, Mississippi, South Carolina, Texas and Virginia. It also applies to identified parts of a further seven states: California, Florida, Michigan, New Hampshire, New York, North Carolina and South Dakota.
New Hampshire is in the process of "bailing out" of Section 5, which means it has had a clean record under the terms of the Act for the past 10 years and is now being freed from its provisions. The NAACP argues that the process of the "bail out" rebuts Alabama's claim that the legislation is too rigid and incapable of change.
Why Congress protected its own pay in the sequester deal
By NCC Staff | National Constitution Center, Article Source
Congressional staffers face layoffs and furloughs in two weeks, but Congress members made sure their own paychecks were safe when passing the "sequester law" in 2011.
Technically, the mandatory cuts to military and domestic federal spending are part of the Budget Control Act of 2011. The act contained a "poison pill"–the threat of stark budget cuts by January 2013 in the form of what's known as the sequester.
That threat was pushed back to March 1, 2013, as part of a compromise made in January. But now, barring a last-second deal, it looks like the sequester will happen.
The sequestration of funds requires that most government agencies cut their budgets by the same percentage across the board. Currently, the cuts add up to $1.2 trillion over a decade.
Right now, non-military government agencies need to cut their costs by 8.2 percent starting on March 1, 2013. Defense branches will have to cut costs by 9.4 percent. (Those percentages could be lower for the first year of cuts.)
Last fall, President Barack Obama's administration gave a detailed report, via the Office of Management and Budget, about which agencies had to cut costs–and which government folks were exempt.
"The number of Federal Bureau of Investigation agents, Customs and Border Patrol agents, correctional officers, and federal prosecutors would be slashed. The Federal Aviation Administration's ability to oversee and manage the Nation's airspace and air traffic control would be reduced," said the OMB.
Included in the mandatory cuts are expenses the members of Congress use to hire and maintain their staffs. In all, the operational expenses for Congress add up to $133 million annually.
Staffers face 22 days of furloughs, which add up to about a 20 percent pay cut for them, and layoffs lurk as a possibility.
Unless, of course, you are an actual member of Congress. Your pay can't be cut as part of the 2011 Budget Control Act.
So why are the "bosses" in Congress not suffering with the staff, at least not until later this spring?
The 27th Amendment to the Constitution forbids Congress from changing its own pay during a current term of Congress. The sequester "poison pill" in the 2011 Budget Control Act was scheduled to go into effect on January 2, 2013, the last day of the prior Congress.
The actual rules for who gets sequestered, and who doesn't, are set by the Gramm-Rudman-Hollings Act of 1985, as amended. The Statutory Pay-As-You-Go Act of 2010 can also be a factor when a sequester goes into effect.
Congressional pay is just one of many programs that will be exempt from cuts. According to the Congressional Research Service, "Most exempt programs are mandatory, and include Social Security and Medicaid; refundable tax credits to individuals; and low-income programs such as the Children's Health Insurance Program, Supplemental Nutrition Assistance Program, Temporary Assistance for Needy Families, and Supplemental Security Income."
Somehow, Congress found a way to delay its own pay, possibly until January 2015, by agreeing to put its pay in escrow on April 16, 2013, as part of the fiscal cliff deal. Even that act has been subject to a vigorous debate as a possible violation of the 27th Amendment, and it could be challenged if the budget deadlock drags out.
Radio Control Models ~ Aviation
Quadrocopter Pole Acrobatics ~ http://www.youtube.com/watch?v=pp89tTDxXuI&feature=youtu.be
Gomma TV ~ Punk TV Italy
Salvatore Iaconesi's: My Open Source [Cancer] Cure
Rome, February 4th 2012: Everything is fine. I have had my surgery a few days ago, and everithing went perfectly. I will soon write all the details of the surgery, and of the enormous benefits which i was able to gather through La Cura, my open source cure. And now it is the time to move on, and to work even harder together to make this experience useful for everyone. Expect news. Really soon. :) Salvatore
Robin Hood Rooster ~ http://www.youtube.com/watch?v=kGq53ArYFSw
Holland's Song ~ http://www.youtube.com/embed/kiERkyuWpE8?rel=0 ~ Keyboardist Lanier Greig dies
No Fear in the Now ~ https://www.youtube.com/watch?v=ZUdHX1Bent0
Goa Hippy Tribe documentary series – Introduction ~ http://vimeo.com/17325384
2 out of every 3 Americans lost
Fourth Amendment protections to DHS
By Darlene Storm, February 19, 2013 3:21 PM EST, Article Source
Two out of every three people reading this could have your electronic devices searched, without there being any reasonable suspicion, because the Department of Homeland Security has decided that such search and seizures do not violate your Fourth Amendment protection against unreasonable search and seizure. Border agents don't need probable cause and they don't need a stinking warrant since they don't need to prove any reasonable suspicion first. Nor, sadly, do two out of three people have First Amendment protection; it is as if DHS has voided those Constitutional amendments and protections they provide to nearly 200 million Americans.
Those numbers come from the ACLU's estimates of how many people live within 100 miles of the United States border, since Homeland Security's Office for Civil Rights and Civil Liberties (CLCR) concluded that border searches of electronic devices do not violate the Fourth Amendment. Previously, the ACLU called this area the Constitution-Free Zone and provided a map showing how many people within states along the all our borders are affected without constitutional rights. The estimate is that nearly two out of three Americans live in the Constitution-Free Zone.
Don't be silly by thinking this means only if you are physically trying to cross the international border. As we saw when discussing the DEA using license plate readers and data-mining to track Americans movements, the U.S. "border" stretches out 100 miles beyond the true border. Godfather Politics added:
But wait, it gets even better! If you live anywhere in Connecticut, Delaware, Florida, Hawaii, Maine, Massachusetts, Michigan, New Hampshire, New Jersey or Rhode Island, DHS says the search zones encompass the entire state.
Immigrations and Customs Enforcement (ICE) and Customs and Border Protection (CBP) have a "longstanding constitutional and statutory authority permitting suspicionless and warrantless searches of merchandise at the border and its functional equivalent." This applies to electronic devices, according to the recent CLCR "Border Searches of Electronic Devices" executive summary [PDF]:
Fourth Amendment
The overall authority to conduct border searches without suspicion or warrant is clear and longstanding, and courts have not treated searches of electronic devices any differently than searches of other objects. We conclude that CBP's and ICE's current border search policies comply with the Fourth Amendment. We also conclude that imposing a requirement that officers have reasonable suspicion in order to conduct a border search of an electronic device would be operationally harmful without concomitant civil rights/civil liberties benefits. However, we do think that recording more information about why searches are performed would help managers and leadership supervise the use of border search authority, and this is what we recommended; CBP has agreed and has implemented this change beginning in FY2012.
First Amendment
Some critics argue that a heightened level of suspicion should be required before officers search laptop computers in order to avoid chilling First Amendment rights. However, we conclude that the laptop border searches allowed under the ICE and CBP Directives do not violate travelers' First Amendment rights.
The ACLU said, Wait one darn minute! Hello, what happened to the Constitution? Where is the rest of CLCR report on the "policy of combing through and sometimes confiscating travelers' laptops, cell phones, and other electronic devices--even when there is no suspicion of wrongdoing?" DHS maintains it is not violating our constitutional rights, so the ACLU said:
If it's true that our rights are safe and that DHS is doing all the things it needs to do to safeguard them, then why won't it show us the results of its assessment? And why would it be legitimate to keep a report about the impact of a policy on the public's rights hidden from the very public being affected?
 The Fourth Amendment states: The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.
The Fourth Amendment states: The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.
Just the same, as ChristainPost wrote, "Your constitutional rights have been repealed in ten states. No, this isn't a joke. It is not exaggeration or hyperbole. If you are in ten states in the United States, your some of your rights guaranteed by the Bill of Rights have been made null and void."
The ACLU filed a Freedom of Information Act request for the entire DHS report about suspicionless and warrantless "border" searches of electronic devices. ACLU attorney Catherine Crump said "We hope to establish that the Department of Homeland Security can't simply assert that its practices are legitimate without showing us the evidence, and to make it clear that the government's own analyses of how our fundamental rights apply to new technologies should be openly accessible to the public for review and debate."
Meanwhile, the EFF has tips to protect yourself and your devices against border searches. If you think you know all about it, then you might try testing your knowledge with a defending privacy at the U.S. border quiz.
Notes from ~@~ Listed Below:
Rolling in the beats
24 Video APC40 Mashup created by Chris from Ithaca Audio
Suggestion: Use Full Screen (button located lower right corner of video) ~ http://vimeo.com/29926452100 Riffs
Alex Chadwick plays 100 Riffs: A Brief History of Rock'n'Roll ~ http://vimeo.com/43426940
CISPA is Back
Dangerous Cybersecurity Legislation Threatens Online Privacy
The Cyber Intelligence Sharing and Protection Act (CISPA) is back.
Last year, Representatives Rogers and Ruppersberger introduced CISPA, which would create a gaping new exemption to existing privacy law. CISPA would grant companies more power to obtain "threat" information (such as from private communications of users) and to disclose that data to the government without a warrant -- including sending data to the National Security Agency.
This week, CISPA was reintroduced in the House of Representatives. EFF is joining groups like ACLU and Fight for the Future in combating this legislation.
Last year, tens of thousands of concerned individuals used the EFF action center to speak out against overbroad and ineffective cybersecurity proposals. Together, we substantially changed the debate around cybersecurity in the U.S., moving forward a range of privacy-protective amendments and ultimately helping to defeat the Senate bill.
Now we need your help again. Can you send a message to your Representatives asking them to oppose this bill? Take Action Now!
Iceland's On-going Revolution
[Ed. Note: Where No Bank Bailout Provided Faster Economic Recovery]
by Deena Stryker, Mon Aug 01, 2011 at 08:47 AM PDT, Article Source
An Italian radio program's story about Iceland's on-going revolution is a stunning example of how little our media tells us about the rest of the world. Americans may remember that at the start of the 2008 financial crisis, Iceland literally went bankrupt. The reasons were mentioned only in passing, and since then, this little-known member of the European Union fell back into oblivion.
As one European country after another fails or risks failing, imperiling the Euro, with repercussions for the entire world, the last thing the powers that be want is for Iceland to become an example. Here's why:
Five years of a pure neo-liberal regime had made Iceland, (population 320 thousand, no army), one of the richest countries in the world. In 2003 all the country's banks were privatized, and in an effort to attract foreign investors, they offered on-line banking whose minimal costs allowed them to offer relatively high rates of return. The accounts, called IceSave, attracted many English and Dutch small investors. But as investments grew, so did the banks' foreign debt. In 2003 Iceland's debt was equal to 200 times its GNP, but in 2007, it was 900 percent. The 2008 world financial crisis was the coup de grace. The three main Icelandic banks, Landbanki, Kapthing and Glitnir, went belly up and were nationalized, while the Kroner lost 85% of its value with respect to the Euro. At the end of the year Iceland declared bankruptcy.
Contrary to what could be expected, the crisis resulted in Icelanders recovering their sovereign rights, through a process of direct participatory democracy that eventually led to a new Constitution. But only after much pain.
Geir Haarde, the Prime Minister of a Social Democratic coalition government, negotiated a two million one hundred thousand dollar loan, to which the Nordic countries added another two and a half million. But the foreign financial community pressured Iceland to impose drastic measures. The FMI and the European Union wanted to take over its debt, claiming this was the only way for the country to pay back Holland and Great Britain, who had promised to reimburse their citizens.
Protests and riots continued, eventually forcing the government to resign. Elections were brought forward to April 2009, resulting in a left-wing coalition which condemned the neoliberal economic system, but immediately gave in to its demands that Iceland pay off a total of three and a half million Euros. This required each Icelandic citizen to pay 100 Euros a month (or about $130) for fifteen years, at 5.5% interest, to pay off a debt incurred by private parties vis a vis other private parties. It was the straw that broke the reindeer's back.
What happened next was extraordinary. The belief that citizens had to pay for the mistakes of a financial monopoly, that an entire nation must be taxed to pay off private debts was shattered, transforming the relationship between citizens and their political institutions and eventually driving Iceland's leaders to the side of their constituents. The Head of State, Olafur Ragnar Grimsson, refused to ratify the law that would have made Iceland's citizens responsible for its bankers' debts, and accepted calls for a referendum.
Of course the international community only increased the pressure on Iceland. Great Britain and Holland threatened dire reprisals that would isolate the country. As Icelanders went to vote, foreign bankers threatened to block any aid from the IMF. The British government threatened to freeze Icelander savings and checking accounts. As Grimsson said: "We were told that if we refused the international community's conditions, we would become the Cuba of the North. But if we had accepted, we would have become the Haiti of the North." (How many times have I written that when Cubans see the dire state of their neighbor, Haiti, they count themselves lucky.)
In the March 2010 referendum, 93% voted against repayment of the debt. The IMF immediately froze its loan. But the revolution (though not televised in the United States), would not be intimidated. With the support of a furious citizenry, the government launched civil and penal investigations into those responsible for the financial crisis. Interpol put out an international arrest warrant for the ex-president of Kaupthing, Sigurdur Einarsson, as the other bankers implicated in the crash fled the country.
But Icelanders didn't stop there: they decided to draft a new constitution that would free the country from the exaggerated power of international finance and virtual money. (The one in use had been written when Iceland gained its independence from Denmark, in 1918, the only difference with the Danish constitution being that the word ‘president' replaced the word ‘king'.)
To write the new constitution, the people of Iceland elected twenty-five citizens from among 522 adults not belonging to any political party but recommended by at least thirty citizens. This document was not the work of a handful of politicians, but was written on the internet. The constituent's meetings are streamed on-line, and citizens can send their comments and suggestions, witnessing the document as it takes shape. The constitution that eventually emerges from this participatory democratic process will be submitted to parliament for approval after the next elections.
Some readers will remember that Iceland's ninth century agrarian collapse was featured in Jared Diamond's book by the same name. Today, that country is recovering from its financial collapse in ways just the opposite of those generally considered unavoidable, as confirmed yesterday by the new head of the IMF, Christine Lagarde to Fareed Zakaria. The people of Greece have been told that the privatization of their public sector is the only solution. And those of Italy, Spain and Portugal are facing the same threat.
They should look to Iceland. Refusing to bow to foreign interests, that small country stated loud and clear that the people are sovereign.
That's why it is not in the news anymore.
Study Confirms Tea Party Was Created by
Big Tobacco and Billionaire Koch Brothers
Brendan DeMelle, Executive Director, DeSmogBlog.com, Article Source
A new academic study confirms that front groups with longstanding ties to the tobacco industry and the billionaire Koch brothers planned the formation of the Tea Party movement more than a decade before it exploded onto the U.S. political scene.
Far from a genuine grassroots uprising, this astroturf effort was curated by wealthy industrialists years in advance. Many of the anti-science operatives who defended cigarettes are currently deploying their tobacco-inspired playbook internationally to evade accountability for the fossil fuel industry's role in driving climate disruption.
The study, funded by the National Cancer Institute of the National Institute of Health, traces the roots of the Tea Party's anti-tax movement back to the early 1980s when tobacco companies began to invest in third party groups to fight excise taxes on cigarettes, as well as health studies finding a link between cancer and secondhand cigarette smoke.
Published in the peer-reviewed academic journal, Tobacco Control, the study titled, 'To quarterback behind the scenes, third party efforts': the tobacco industry and the Tea Party, is not just an historical account of activities in a bygone era. As senior author, Stanton Glantz, a University of California, San Francisco (UCSF) professor of medicine, writes:
"Nonprofit organizations associated with the Tea Party have longstanding ties to tobacco companies, and continue to advocate on behalf of the tobacco industry's anti-tax, anti-regulation agenda."
The two main organizations identified in the UCSF Quarterback study are Americans for Prosperity and Freedomworks. Both groups are now "supporting the tobacco companies' political agenda by mobilizing local Tea Party opposition to tobacco taxes and smoke-free laws." Freedomworks and Americans for Prosperity were once a single organization called Citizens for a Sound Economy (CSE). CSE was founded in 1984 by the infamous Koch Brothers, David and Charles Koch, and received over $5.3 million from tobacco companies, mainly Philip Morris, between 1991 and 2004.
In 1990, Tim Hyde, RJR Tobacco's head of national field operations, in an eerily similar description of the Tea Party today, explained why groups like CSE were important to the tobacco industry's fight against government regulation. Hyde wrote:
"... coalition building should proceed along two tracks: a) a grassroots organizational and largely local track,; b) and a national, intellectual track within the DC-New York corridor. Ultimately, we are talking about a "movement," a national effort to change the way people think about government's (and big business) role in our lives. Any such effort requires an intellectual foundation - a set of theoretical and ideological arguments on its behalf."
The common public understanding of the origins of the Tea Party is that it is a popular grassroots uprising that began with anti-tax protests in 2009.
However, the Quarterback study reveals that in 2002, the Kochs and tobacco-backed CSE designed and made public the first Tea Party Movement website under the web address www.usteaparty.com. Here's a screenshot of the archived U.S. Tea Party site, as it appeared online on Sept. 13, 2002:

WELCOME to the U.S. TEA PARTY
CSE describes the U.S. Tea Party site, "In 2002, our U.S. Tea Party is a national event, hosted continuously online, and open to all Americans who feel our taxes are too high and the tax code is too complicated." The site features a "Patriot Guest book" where supporters can write a message of support for CSE and the U.S. Tea Party movement.
Sometime around September 2011, the U.S. Tea Party site was taken offline. According to the DNS registry, the web address www.usteaparty.com is currently owned by Freedomworks.
The implications of the UCSF Quarterback report are widespread. The main concern expressed by the authors lies in what they see happening overseas as the Tea Party movement expands internationally, training activists in 30 countries including Israel, Georgia, Japan and Serbia.
As the authors explain:
"This international expansion makes it likely that Tea Party organizations will be mounting opposition to tobacco control (and other health) policies as they have done in the USA."
Freedomworks and Americans for Prosperity are both multi-issue organizations that have expanded their battles to include other policies they see as threats to the free market principles they claim to defend, namely fighting health care reform and regulations on global warming pollution. The report's warning about overseas expansion efforts by Freedomworks should therefore also be heeded by groups in the health and environment arenas.
Finally, this report might serve as a wake-up call to some people in the Tea Party itself, who would find it a little disturbing that the "grassroots" movement they are so emotionally attached to, is in fact a pawn created by billionaires and large corporations with little interest in fighting for the rights of the common person, but instead using the common person to fight for their own unfettered profits.
Gabrielle Giffords Confronts Her Shooter
Congresswoman Gabrielle Giffords Talks Palin Cross Hairs
http://www.youtube.com/watch?feature=player_embedded&v=R7046bo92a4
According to George W Bush the Tea Party Would Be A Terrorist Cell

Charles Manson was convicted of murder through the joint-responsibility rule, where each member of a conspiracy is guilty of crimes fellow conspirators commit in furtherance of the conspiracy's object.

The View' Condemns Palin's Political Target Map; Behar Cracks: 'Looks Like Al-Qaida Christmas Card'
http://www.youtube.com/watch?feature=player_embedded&v=5mlYHiJCqBI
Does Joint-Responsibility Rule of Conspiracy apply to:
Sarah Palin, Big Tobacco, and Billionaire Koch Brothers ?
You Betcha!
http://www.youtube.com/watch?feature=player_embedded&v=Y9ozFfITZ14
Donald Byrd obituary
Virtuoso trumpeter who honed his craft with Art Blakey's Jazz Messengers
Donald Byrd ~ Cristo Redentor ~ http://vimeo.com/826468
Change Happens

I Love You, Spoken From the Heart, Does Not Require A Corporatist Holiday
Plant Art, Photograph, and Words by C. Spangler
(imo)
Articles worth a read
Icelandic MP who released WikiLeaks video plans US visit despite legal threat
Birgitta Jónsdóttir says she has held back from visiting long enough and plans tour to express support for Bradley Manning
Israel's 'Prisoner X' was Australian Mossad agent, documentary claims
Israel has never acknowledged prisoner's existence and has gone to extraordinary lengths to stifle media coverage of case
Gas company targets protected Manú park in Peruvian Amazon
Leaked document reveals Pluspetrol is eyeing a region where biodiversity 'exceeds that of any other place on Earth'
Punk fashion celebrated at New York's Metropolitan Museum of Art
Organisers hope exhibition of punk fashion at the Costume Institute has the power to shock – and draw the crowds
Medical marijuana brings in $10m for Michigan
The economic argument for legalization is appealing to more and more statehouses
By Natasha Lennard, Salon.com, Article Source
(Credit: Peter Kim via Shutterstock)As marijuana legalization supporters have long noted, measures to permit the sale of either medical or recreational marijuana promise to bring substantial windfalls to whatever state enacts them. Michigan's legalization of medical marijuana proves as much.
According to the Detroit Free Press, "a report says nearly $10 million in revenue was collected from applicants — more than double the cost of running the program. The report covers the state's last budget year, which ended Sept. 30."
To register as a marijuana user in the state, individuals must pay $100, while those who grow medical marijuana must also pay a fee to the state.
In this time of state budget shortfalls, it's little wonder that lawmakers are embracing the financial impetus of legalizing marijuana. Indeed, if arguments based on the ruinous effects of racially disparate marijuana arrests weren't enough, maybe news of Michigan's windfall will have some influence. Pennsylvania state Sen. Daylin Leach (D-17) noted as much in advance of introducing a legalization bill into the Pennsylvania statehouse. "The economic argument, at the end of the day, will probably be the most effective in changing this terrible policy we've had in place for too long."
Jeffrey Miron, visiting professor of economics at Harvard University, has estimated that on a national level, replacing marijuana prohibition with a system of taxation and regulation similar to that used for alcohol would produce combined savings and tax revenues of between $10 billion and $14 billion per year.
Natasha Lennard is an assistant news editor at Salon, covering non-electoral politics, general news and rabble-rousing.
Closing Arguments ~ Please Watch the Below Video
Please Click to View Video ~ Video transcript below:
Boston Legal
Stick It
Season 2, Episode 19
Written by David E. Kelley
Broadcast: March 14, 2006Alan Shore: When the weapons of mass destruction thing turned out not to be true, I expected the American people to rise up. Ha! They didn't.
Then, when the Abu Ghraib torture thing surfaced and it was revealed that our government participated in rendition, a practice where we kidnap people and turn them over to regimes who specialize in torture, I was sure then the American people would be heard from. We stood mute.
Then came the news that we jailed thousands of so-called terrorist suspects, locked them up without the right to a trial or even the right to confront their accusers. Certainly, we would never stand for that. We did.
And now, it's been discovered the executive branch has been conducting massive, illegal, domestic surveillance on its own citizens. You and me. And I at least consoled myself that finally, finally the American people will have had enough. Evidentially, we haven't.
In fact, if the people of this country have spoken, the message is we're okay with it all. Torture, warrantless search and seizure, illegal wiretappings, prison without a fair trial or any trial, war on false pretenses. We, as a citizenry, are apparently not offended.
There are no demonstrations on college campuses. In fact, there's no clear indication that young people even seem to notice.
Well, Melissa Hughes noticed. Now, you might think, instead of withholding her taxes, she could have protested the old fashioned way. Made a placard and demonstrated at a Presidential or Vice-Presidential appearance, but we've lost the right to that as well. The Secret Service can now declare free speech zones to contain, control and, in effect, criminalize protest.
Stop for a second and try to fathom that.
At a presidential rally, parade or appearance, if you have on a supportive t-shirt, you can be there. If you're wearing or carrying something in protest, you can be removed.
This! In the United States of America. This!In the United States of America. Is Melissa Hughes the only one embarrassed? He sits down abruptly in the witness chair next to the judge.
Judge Robert Sanders: Mr. Shore. That's a chair for witnesses only.
Alan Shore: Really long speeches make me so tired sometimes.
Judge Robert Sanders: Please get out of the chair.
Alan Shore: Actually, I'm sick and tired.
Judge Robert Sanders: Get out of the chair!
Alan Shore: And what I'm most sick and tired of... He get's up and out of the chair. ...is how every time somebody disagrees with how the government is running things, he or she is labeled un-American.
D.A. Jonathan Shapiro: Evidentially, it's speech time.
Alan Shore: And speech in this country is free, you hack! Free for me, free for you. Free for Melissa Hughes to stand up to her government and say, "Stick it"!
D.A. Jonathan Shapiro: Objection!
Alan Shore: I object to government abusing its power to squash the constitutional freedoms of its citizenry. And, God forbid, anybody challenge it, they're smeared as being a heretic. Melissa Hughes is an American. Melissa Hughes is an American. Melissa Hughes is an American!
Judge Robert Sanders: Mr. Shore. Unless you have anything new and fresh to say, please sit down. You've breached the decorum of my courtroom with all this hooting.
Alan Shore: Last night, I went to bed with a book. Not as much fun as a 29-year-old, but the book contained a speech by Adlai Stevenson. The year was 1952.
He said, "The tragedy of our day is the climate of fear in which we live and fear breeds repression. Too often, sinister threats to the Bill of Rights, to freedom of the mind are concealed under the patriotic cloak of anti-Communism."
Today, it's the cloak of anti-terrorism. Stevenson also remarked, "It's far easier to fight for principles than to live up to them."
I know we are all afraid. But the Bill of Rights - we have to live up to that. We simply must. That's all Melissa Hughes was trying to say. She was speaking for you. I would ask you now to go back to that room and speak for her.
Boston Legal
Beauty and the Beast
Season 4, Episode 01
Written By David E. Kelley
Broadcast September 25, 2007Alan Shore: Let's look at what's happened in Washington. These huge corporations that poison our drinking water, foul our air, lay waste to our lands have discovered that instead of trying to influence government, better to simply become government. And with a little help from a friend in a very high place they've done just that.
Over one hundred top environmental posts have been passed out to representatives of polluting industries. Can you fathom that, Judge?
As Alan happens to look back at Lorraine, she shifts her lapel to expose her brassier.
Judge Robert Sanders: Don't you be asking me to fathom. I am not a, uh, fathomer!
Alan Shore: Almost every agency responsible for protecting America from pollution is now being headed up by somebody from the pollution industry. The fix is in.
Judge Robert Sanders: How does this involve Stanford University?
Alan Shore: It involves a need in this country for independent, unbiased, uncorrupted environmental research. And since it's obviously not coming from Washington, academia is our best, if not our only, hope. And now it, too, is being co-opted by big pollution. The facts are that the oil industry has systematically campaigned to create doubt as to the very existence of global warming. Pumping millions of dollars into think tanks, consumer groups, media outlets, religious and civic organizations. Every penny aimed at defusing the concern over climate change. Now, they're privatizing university research. Berkeley. Princeton. Now, Stanford. Do we truly want our universities, the breeding grounds for tomorrow's leaders, innovators, visionaries, do we truly want them climbing into bed with the oil companies?
Attorney Lorraine Weller: Strange bedfellows?
Alan Shore: Lorraine! Stop it. He's not letting her get to him. Your Honor, at some point a little common sense has to prevail in this country. We've started a war, in part, for oil. One we may never get out of in our lifetime. Of all the industrialized nations in the world, we're the biggest contributor to greenhouse gas emissions and we do the least about it. We thumb our nose at the Kyoto Treaty. Our government actually censors scientific reports from the EPA and others to edit out little findings they don't like. Even the Democratic presidential hopefuls don't talk about this because they don't want to jeopardize their campaign contributions from big oil. Big oil. Big politics. Do we really all intend to sit quietly as they infiltrate vital academic research? Is that what we want? Is that who we are?
Boston Legal
The Chicken and The Leg
Season 4, Episode 3
Written by: Lawrence Broch & David E. Kelley
Airdate: October 9, 2007Adam Jovanka: [snip] sexually active. And many start doing so because they feel all their friends are. Sure, we can pass out condoms. But it is simply more responsible, more moral and yes, more safe to practice abstinence. That's what we should be telling them. And this school is.
Alan Shore: This case isn't about teenage pregnancy. She didn't get pregnant. She got H.I.V. I can see why you would want to make it about teenage pregnancy, since, well, actually I can't. The United States had the worst teen pregnancy rate of any industrialized nation. And contrary to what Mr. Jovanka would like us to believe, there is no evidence whatsoever that suggests using condoms or teaching students about condoms makes them any more inclined to have sex. None. They're already inclined to have sex and have been since early puberty. They're simply going to do it, we all do it. Birds do it, bees do it. Educated fleas do it. One day, Your Honor even you... Slamming of gavel.. Yes, the fact is this case has nothing to do with the efficacy of abstinence only programs. This case is about religion, politics and federal funding. Our present administration, in blind service to the religious right, has transcended the separation of Church and State and consistently implemented a faith-based political and moral mandate. And now that same policy has been passed on to our educational system. If schools teach abstinence only, they get federal funding. If they teach any other type of sex education, they don't. And as a result, the students in these abstinence only programs aren't being taught the truth about that magnificent technological marvel, the condom. That's not a dirty word, Your Honor. Condoms. Judge slams gavel again. They first came on the scene some 3,000 years ago in Egypt. For centuries they wert merrily along in modified forms warding off syphilis, gonorrhea, preventing unplanned pregnancies, until science and medicine eventually caught up and the pill became a much more effective, less intrusive contraceptive. Penicillin and other antibiotics were miracle cures for gonorrhea and syphilis. The poor humble condom languished. And then came AIDS... this terrifying new disease that panicked the world. For many years, it has been fatal, gruesomely so in every case. There was no vaccine, no cure, no treatment. But there were condoms, and they worked. They were safe, time-tested, easy to use, and they protected both partners. The condom is arguably the single most important invention of the past 2,000 years. In fact, it has been said without exaggeration that the health of the world depends on them. Now one would think that the obvious choice would be for schools to tell their students as much. But Abby's school... indeed all schools, that teach abstinence only, have chosen to lie. They teach that condoms are ineffective at preventing pregnancies, which is a lie. They teach that condoms are ineffective at prevent disease, which is a lie. Some of the literature actually compares using a condom to playing Russian Roulette, which is a frightening, despicable, unforgivable lie. Alan turns and smiles at Abigail. Abby Hold has H.I.V., which in all likelihood will develop into AIDS. We've sort of forgotten about AIDs in this country. Treatments have improved dramatically. Drugs are keeping people alive for many years after they become infected. But the Grim Butcher's bill for this pandemic still keeps growing and growing. 65 million people worldwide have become infected. One time unprotected sex can kill you. A condom can save you. It is inconceivable, that every child in the world isn't taught that. We should be in criminal court this very moment, trying this obscenely duplicitous school for conspiracy to commit murder. Ah. But frankly, I have no stomach for that. I think of the horror that has been inflicted on this fifteen year old girl, and I'm just so profoundly sad. I can point out the evils of this corrupt system. I can tell you have effective condoms are, the lives they save and on and on and on and... but words seem to be these hollow, useless things rattling around in this courtroom. Because ultimately the lies this school told Abby Holt may... will probably kill her. They have certainly altered her life forever. And in the face of that, all I can think of is ... why?
Boston Legal
Smoke Signals
Season 5, Episode 01
Written By: David E. Kelley
Broadcast: September 22, 2008Alan Shore: Michael Rhodes smoked cigarettes for fifty years, got lung cancer and died. We all know what happened here. We also all know this death. Everybody in this room knows somebody who has fought the same battle and died this agonizing, brutal, excruci... A beat. Alan smiles derisively. But, emotion has no play here. Michael Rhodes was eleven years old when he started smoking. It was 1948, at that time there was no known risk. And even if there were, at eleven, he certainly lacked the capacity to assume it. And after that he was addicted. They manufacture them to be addictive. In just the last few years they've increased the amount of nicotine in the average cigarette by 11.6% to make them even more addictive. Recently we learned that tobacco companies have been adding an ammonia-based compound to cigarettes for years to increase absorption of nicotine. It's basically the same principle used in crack cocaine. And let's look at the obscene strategy they've employed here. "Smoking may cause cancer but it didn't cause this particular cancer." "It wasn't our cigarettes!" Or, "It was genetic." Or, "Asbestos". Or, "A paper mill." Never do they take responsibility. Ever! And, God forbid, if you sue them they'll bury you. And your lawyer. They might even depose your doctor to death for good measure. All their insidious methods and cunning corporate tactics aren't just history. It's what they continue to do now! Today! Because the tobacco industry is like a nest of cockroaches, they will always find a way to survive.
Attorney Phoebe Prentice: Objection! The Judge raises his hand to shush her.
Alan Shore: They still go after kids with one strategy after another. They put up brightly colored ads at kids' eye level in convenience stores. They hire gorgeous twenty-somethings to frequent popular venues and seduce young adults into attending lavish corporate-sponsored parties. Cockroaches will always find a way. They can't advertise on TV but they've hired PR agencies to hook them up with the film industry. And it's working! Researchers estimate that smoking in movies delivers nearly four hundred thousand new adolescent smokers every year. Every time you try to kill the cockroach it finds another way. It has to! Because when you make a product that kills off your consumers you have to find a way to recruit new customers. They've now got a new feminized version of the macho Camel brand using slogans like Lite & Luscious with hot pink packaging. Virginia Slims advertise their thin cigarette. Velour magazine did a whole spread on the cigarette diet. They use social, psychological profiling targeting potential smokers by gender, ethnicity, sexual preferences, socio-economic groups. Cockroaches don't discriminate! Their CEO comes into this courtroom gloating over their anti-smoking campaign which is designed to get kids to smoke! In 2005 they spent fifteen billion on advertising and promotion. That's a 225% increase from 1998 and they have the audacity to declare they're trying to discourage smoking. This is not how corporations with a conscience behave! How in God's name are cigarettes even legal? Can anybody tell me that? They are a deadly concoction of carcinogens that damage every single organ in your body. Why do we not ban them? Because it's a free country, because freedom of choice is an American ideal worth somebody dying every six seconds? How can any company, especially one with such a conscience, no less, knowingly manufacture a product that poisons its users! And make that product look cool and hip and sexy and fun so they can get children. How can any attorney defend a company that would do such a thing? How can any society tolerate it? But we do! There is no conscience at Big Tobacco. There is no conscience in Washington which has been bought and paid for by this industry. Conscience has to come from you, the jury. If real regulation is to happen, it has to come from you! People are smoking day after day after day. And dying and dying and dying and the tobacco companies keep getting richer and richer. Last year alone they made twelve billion dollars in profits. How can that be? How can that be?
Google Moves to Destroy Online Anonymity ...
Unintentionally Helping Authoritarian Governments
Governments Move to Destroy Online Anonymity
Posted on February 10, 2013 by WashingtonsBlog, Article Source, via Keith Lampe
Some of the world's leading social critics and political critics have used pen names.
As Tyler Durden of Zero Hedge points out (edited slightly for readability):
Though often maligned (typically by those frustrated by an inability to engage in ad hominem attacks), anonymous speech has a long and storied history in the United States. Used by the likes of Mark Twain (aka Samuel Langhorne Clemens) to criticize common ignorance, and perhaps most famously by Alexander Hamilton, James Madison and John Jay (aka publius) to write the Federalist Papers, we think ourselves in good company in using one or another nom de plume.
Particularly in light of an emerging trend against vocalizing public dissent in the United States, we believe in the critical importance of anonymity and its role in dissident speech.
Like the Economist magazine, we also believe that keeping authorship anonymous moves the focus of discussion to the content of speech and away from the speaker -- as it should be. We believe not only that you should be comfortable with anonymous speech in such an environment, but that you should be suspicious of any speech that isn't.
But governments -- especially authoritarian governments -- hate anonymity.
A soon-to-be-released book by Google executive Eric Schmidt - called "The New Digital Age" -- describes the desire of authoritarian governments to destroy anonymity. The Wall Street Journal provides an excerpt:
Some governments will consider it too risky to have thousands of anonymous, untraceable and unverified citizens — "hidden people"; they'll want to know who is associated with each online account, and will require verification at a state level, in order to exert control over the virtual world.
Last December, China started requiring all web users to register using their real names.
But the U.S. is quickly moving in the same direction. As Gene Howington reported last year:
Do you have a right to anonymous political free speech?
According to the Supreme Court, you do. According to the Department of Homeland Security, you don't. They've hired General Dynamics to track U.S. citizens exercising this critical civil right.
The history of anonymous political free speech in America dates back to our founding. The seminal essays found in "The Federalist Papers" were written by Alexander Hamilton, James Madison and John Jay under the nom de plume of "Publius" although this was not confirmed until a list of authorship complied by Hamilton was posthumously released to the public. As previously discussed on this blog, the right to anonymous political free speech has been addressed by the Supreme Court. Most notably in the cases of Talley v. California, 362 U.S. 60 (1960) and McIntyre v. Ohio Elections Commission, 514 U.S. 334 (1995). In Talley, Justice Hugo Black writing for the majority said that, "Anonymous pamphlets, leaflets, brochures and even books have played an important role in the progress of mankind. Persecuted groups and sects from time to time throughout history have been able to criticize oppressive practices and laws either anonymously or not at all." In McIntyre, Justice John Paul Stevens writing for the majority said that, "Anonymity is a shield from the tyranny of the majority. [... ] an author's decision to remain anonymous, like other decisions concerning omissions or additions to the content of a publication, is an aspect of the freedom of speech protected by the First Amendment." That seems clear enough in defining that citizens do have a Constitutionally protected right to anonymous political free speech.
The full DHS policy statement regarding its activities can be viewed in the DHS Privacy Compliance Review of the NOC Media Monitoring Initiative (November 15, 2011), but rt.com's summary spells out the basics:
"Under the National Operations Center (NOC)'s Media Monitoring Initiative that came out of DHS headquarters in November, Washington has the written permission to retain data on users of social media and online networking platforms.
Specifically, the DHS announced the NCO and its Office of Operations Coordination and Planning (OPS) can collect personal information from news anchors, journalists, reporters or anyone who may use "traditional and/or social media in real time to keep their audience situationally aware and informed."
According to the Department of Homeland Security's own definition of personal identifiable information, or PII, such data could consist of any intellect "that permits the identity of an individual to be directly or indirectly inferred, including any information which is linked or linkable to that individual." Previously established guidelines within the administration say that data could only be collected under authorization set forth by written code, but the new provisions in the NOC's write-up means that any reporter, whether someone along the lines of Walter Cronkite or a budding blogger, can be victimized by the agency.
Also included in the roster of those subjected to the spying are government officials, domestic or not, who make public statements, private sector employees that do the same and "persons known to have been involved in major crimes of Homeland Security interest," which to itself opens up the possibilities even wider.
The department says that they will only scour publically-made info available while retaining data, but it doesn't help but raise suspicion as to why the government is going out of their way to spend time, money and resources on watching over those that helped bring news to the masses." -- rt.com
This question about the right to anonymous political free speech is also asked over the background of the Electronic Privacy Information Center filing a FOIA request against the DHS to find out the details of the agency's social network monitoring program.
***
As part of recent disclosures related to the EPIC suit, it is revealed that the DHS has hired and instructed General Dynamics to monitor political dissent and the dissenters. The range of websites listed as being monitored is quite impressive. Notably, jonathanturley.org is not on this list [Howington's essay is a guest blog on constitutional law professor Jonathan Turley's website], but equally of note is that this list is by the DHS' own admission "representative" and not "comprehensive".
***
Some of the more high profile and highly trafficked sites being monitored include the comments sections of The New York Times, The Los Angeles Times, Newsweek, the Huffington Post, the Drudge Report, Wired, and ABC News. In addition, social networking sites Facebook, MySpace and Twitter are being monitored. For the first time, the public not only has an idea who the DHS is pursuing with their surveillance and where, but what they are looking for as well. General Dynamics contract requires them to "[identify] media reports that reflect adversely on the U.S. Government, DHS, or prevent, protect, respond government activities." The DHS also instructed General Dynamics to generate "reports on DHS, Components, and other Federal Agencies: positive and negative reports on FEMA, CIA, CBP, ICE, etc. as well as organizations outside the DHS." In other words, the DHS wants to know who you are if you say anything critical about the government.
Anybody thinking of the name "Goebbels" at this point is not out of line.
Indeed, valuing online privacy could even get you labeled as a potential terrorist.
Google Moving to Help Destroy Anonymity
Google's motto is "Do No Evil". And Google notes in a patent application:
When users reveal their identities on the internet, it leaves them more vulnerable to stalking, identity theft and harassment.
So you might assume that Google is fighting to protect anonymity on the web.
But Schmidt's new book reveals that Google will support the destruction of anonymity (via Wall Street Journal):
Within search results, information tied to verified online profiles will be ranked higher than content without such verification, which will result in most users naturally clicking on the top (verified) results. The true cost of remaining anonymous, then, might be irrelevance.
Search Engine Journal explains:
[Passages from Schmidt's book] confirm what many industry writers have been passionately clattering away about for months now. Google+ is an identity verification network. As the network continues to grow, content associated with a verified identity will rise to the top of Google search rankings.
(Google+ is now the world's second most popular social network.)
In other words, Schmidt acknowledges (in the first quote above) that authoritarians want to destroy anonymity ... and Google will help them do so.
We are not saying that Google likes authoritarians. (Potential ties between Google and the government are beyond the scope of this essay.) However, Google will do business with anyone ... and will cowtow to authoritarians they happen to do business with.
Google is doing this to make money. Remember, Google gathers information across all of its platforms, and personalizes search engine results based upon what you've looked for in past searches.
After all, Google is primary an advertising company ... not a search company. See this, this, this and this.
As the Daily Mail reported last year:
A former Google executive has lambasted his ex-employer ... claiming that the search company has been turned into an 'ad company' obsessed with harvesting people's private information.
James Whittaker, a current Partner Development Manager at Microsoft and ex-Engineering Director at Google, posted the 1328-word attack on Google on his Microsoft blog this week.
'Perhaps Google is right,' writes Whittaker, 'Perhaps the future lies in learning as much about people's personal lives as possible.
'The Google I was passionate about was a technology company. The Google I left was an advertising company.'
***
The move comes in the wake of Google's controversial new 'privacy policy', which allowed the search giant to 'pool' information from 60 separate services including Gmail, Google Search and Android phones, to create 'personalised' advertising.
The bottom line is that anonymity reduces Google's ability to monetize personal information and sell it to its advertisers. So Google is on a campaign to destroy anonymity ... and unintentionally helping tyrants in the process.
As INeedHits laments:
We knew a day would come when privacy was a thing of the past, but Schmidt clearly spells out that day is sooner than we had expected.
ARPSN Seismic Heliplots ~ Seismic Activity and Cobb [Mountain] Weather
Autumn Fenders ~ 1969 Photography Album by Ralph Davis
Speedway Meadows, Golden Gate Park, San Francisco ~ 1969 Photo Album by Ralph Davis
Marliese's Corner ~ San Francisco Events
CHASING ICE captures largest glacier calving ever filmed
http://www.youtube.com/embed/hC3VTgIPoGU?rel=0
Notes from ~@~ Listed Below:
Cheaper Than Brandy and No Hang-Over
FEB. 10, 1799 ~ Napoleon marched out of Cairo at the head of his French expeditionary Army. He headed north towards Jerusalem, but was stopped at the city of Jaffa.
Around this time French soldiers discovered marijuana in Egyptian bazaars. The tough old soldiers thought it cheaper than brandy and didn't leave you hung-over the next morning. via Karl
SANDY HOOK FATHER OWNS CONGRESS via Bruce
http://www.youtube.com/watch?v=dhXPlCjr0Vw
Amestizo ~ BLOG
The Reality Matrix - Matter, Energy, Perception, Nature Of Reality
http://www.youtube.com/embed/Swkpyt4weiw
Radio Control Models ~ Aviation
Raffaello D'Andrea ~ Feedback Control and the Coming Machine Revolution
http://www.youtube.com/embed/C4IJXAVXgIo?rel=0
Karl Cohen ~ Association International du Film d'Animation-SF Newsletter
ASIFA-SF NEWSLETTER
Association International du Film d'Animation
(International Animated Film Association)
February 2013IN THIS ISSUE YOU WILL FIND A SERIOUS ARTICLE ABOUT UNPAID STUDENT INTERNSHIPS -- WHEN ARE THEY AN ASSET AND WHEN ARE THEY A RIPOFF? By KC It includes the 6 rules the US govt. uses to determine if the person is getting the training that fits into the legal definition of an unpaid intern or if the unpaid person is being exploited.
Plus there is a link to an IMPRESSIVE TECHNIQUE USING SEQUENCES OF THICK PAPER CUTOUTS, plenty of awards news, local news. national news, an article about a festival in France, news of our members only event and much more.
You, at least, Want Honest Government, Don't You?
There Had To Be More Than One Born Every Day? ~ Dahbud on P.T. Barnum
MASS GRAVES
Between 1983 and 1992 -- the Reagan/Bush and Bush/Quayle era -- the U.S. gave Iraq innumerable weapons, and issued about $2 billion in loans, most of which were used to buy even more weapons; the U.S. never expected full repayment. In addition, U.S. corporations provided Iraq with the means to manufacture chemical and biological weapons. The "point man" the Reagan administration sent to solidify U.S.-Iraqi relations -- and who had personal knowledge that Iraq was using chemical weapons against Iran, and who helped remove the "terrorist" label against Iraq -- was . . . Donald Rumsfeld. [liberalslant.com / wb042903.htm - missing link.]
Neocon War Criminal Donald Rumsfeld shaking hands with his good friend Saddam HusseinARTICLE COPY:
The Shock and Awe of American Ignorance
Playing Spin the Battle
by Walt Brasch, April 25, 2003More than half of all Americans believe that Saddam Hussein was personally involved in the 9/11 terrorist attacks. According to an Associated Press poll conducted shortly after the conclusion of the successful invasion of Iraq, 53 percent of the nation pin the 9/11 murders on Saddam, something the CIA and most of the world intelligence gathering organizations have consistently discounted.
The fact that so many Americans believe this reveals the successful drum beating of the Bush administration along with a failure of both Congress and the media to adequately question the President's motives or to challenge the statements coming from the White House and Pentagon. President Bush and his horde of advisors have constantly said they never--ever--said that Saddam was the person behind the attacks. But, if the President could say "subliminal," that's what he, the vice-president, and their administration did to the Americans, with the complicity of the media who abrogated their responsibilities and made it seem that challenging anything the President said would be treason.
In message after message, the President referred to 9/11 and the war on terrorism. Then, as in the movies, he jump-cut to the evils of Saddam, letting the people think there was a smooth transition, while implanting those "hidden" meanings.
A month after 9/11, Americans believed Osama bin Laden and al-Qaeda were responsible. Upon that basis, the President ordered an invasion of Afghanistan, one of several countries that harbored bin Laden and his terrorists, and overthrew the Taliban regime. At the time, finding anyone who thought Saddam was personally involved in 9/11 was as rare as finding a corporate executive who believed in unions.
Americans quickly learned that 15 of the 19 suicide/killers of 9/11 were Saudi. With a little more digging into buried news accounts, they might have also learned that 26 of al-Qaeda's top leadership at the time of 9/11, including bin Laden, were Egyptian, Saudi, or Yemini. Only one, a third level administrator, was an Iraqi. They might also have learned that eight of the top 10 financial contributors to al-Qaeda are Saudi. They might also have learned that Saddam and al-Qaeda had never been close, that as ruthless as Saddam was, he was relatively moderate in the world of terrorism except, of course, against his own people.
A year of Presidential drum beating and brow-bashing led to about a third of Americans becoming believers. A month before the invasion of Iraq, about 45 percent of Americans, according to the AP, believed the Iraqi dictator was personally involved.
The eight percent increase in the month after the invasion could be attributed not only to war-mongering rhetoric, but to the nation trying to justify why it sent more than 200,000 of its sons and daughters, mothers and fathers, brothers, sisters, aunts, uncles, and cousins to war.
By the time war had begun, the message wasn't that Iraq was behind 9/11, but that it was a potential enemy because it had weapons of mass destruction.
In the most recent State of the Union, President Bush had forcefully declared that Iraq had a weapons program that included at least 500 tons of chemical weapons, 38,000 liters of botulism, 25,000 liters of anthrax, as well as uncountable numbers of SCUDs. But, as in the telephone rumor game when a simple fact spread person to person eventually becomes a bloated urban myth, America's people and their news media escalated even those unproven numbers until the average working person may have been led to believe that Iraq actually posed a greater danger to America than did North Korea and Iran, both of which had nuclear capability to hit American targets, something Iraq did not have.
However, Iraq once had weapons of mass destruction, although none were nuclear. Between 1983 and 1992--the Reagan/Bush and Bush/Quayle era--the U.S. gave Iraq innumerable weapons, and issued about $2 billion in loans, most of which were used to buy even more weapons; the U.S. never expected full repayment. In addition, U.S. corporations provided Iraq with the means to manufacture chemical and biological weapons. The "point man" the Reagan administration sent to solidify U.S.-Iraqi relations-and who had personal knowledge that Iraq was using chemical weapons against Iran, and who helped remove the "terrorist" label against Iraq--was . . . Donald Rumsfeld.
But, slowly and reluctantly under a U.N. mandate, Iraq began to destroy its weapons. So far, 300,000 American and British combat forces, aided by numerous infiltrators and the best spy satellite system ever known to mankind, have been unable to locate any weapons of mass destruction--other than ones used by the Coalition forces. Maybe the Bush administration should send in Monk and Colombo.
The fact that the two-nation "coalition" of 300,000 overwhelmed and destroyed a country of 24 million quickly, and that Iraq's armies used only bullets, light artillery, and short-range, but legal, missiles in its defense, suggests that the defeated nation probably didn't have the weapons the U.S. claimed.
President Bush and his supporters kept saying the war wasn't about oil. But, the first thing the Coalition troops protected once they entered Baghdad weren't the hospitals or museums but the Oil Ministry. Maybe the Ministry was in an "historical district."
At the time President Bush was telling the U.N. and the American people that he had no plans to go to war with Iraq, his administration officials were meeting in secret with several industry giants with financial and political ties to the Administration to develop a plan for a post-war Iraq.
One of those giants was Bechtel, a multi-nation conglomerate with close financial ties to the White House. Another was a subsidiary of Haliburton, the multi-billion dollar oil company that once had Dick Cheney as its CEO.
In a few months, Americans may be shocked that Iraq didn't help al-Qaeda and the 9/11 attacks, that it didn't have weapons of mass destruction, and that there may have been collusion between the Administration and major corporations to reap financial rewards for rebuilding a country that the U.S. destroyed. We should be shocked--but we should also be in awe of how well the President and his administration spun their messages of war, and how dizzy the major media must have been to have accepted the words unchallenged.
Walt Brasch, a national award-winning reporter and editor, is professor of journalism at Bloomsburg University. He is the author of 13 books, including The Press and the State, and the current book, The Joy of Sax: America During the Bill Clinton Era. You may contact him through his web-site http://www.walterbrasch.com
Real Story of MASS GRAVES
[http://www.sfbg.com/News/32/21/Features/iraq.html -> missing link - see Made In America (below)]In the early 1980s the Reagan administration chose to support Iraq over Iran in their bloody war. Neither country was exactly an ally, but the White House considered Iran the worse of the two nations, and cold war politics (along with a U.S. desire to maintain control of oil supplies in the Middle East) put us on the side of Iraq.
According to a 1990 report, "The Poison Gas Connection," issued by the L.A.-based Simon Wiesenthal Center (See sidebar), more than 207 companies from 21 western countries, including at least 18 from the United States, contributed to the buildup of Saddam Hussein's arsenal. Subsequent investigations turned up more than 100 more companies participating in the Iraqi weapons buildup.
The frontline cheerleader for America's corporate contributors to Saddam, the man who paved the way for Iraq to purchase millions of dollars worth of weapons and dangerous dual-use technology from U.S. corporations, was none other than the architect of Gulf War I, former president George Bush.
In a stunning July 27, 1992, speech on the floor of the House of Representatives, House Banking Committee chair Henry Gonzalez drove the Bush connection home in no uncertain terms:
"The Bush administration deliberately, not inadvertently, helped to arm Iraq by allowing U.S. technology to be shipped to Iraqi military and to Iraqi defense factories," Gonzalez said. "Throughout the course of the Bush administration, U.S. and foreign firms were granted export licenses to ship U.S. technology directly to Iraqi weapons facilities despite ample evidence showing that these factories were producing weapons."
Gonzalez, who was accused by administration officials of jeopardizing national security for going public with his gritty revelations, also stated: "The president misled Congress and the public about the role U.S. firms played in arming Iraq."
Documents gathered by Gonzalez and other independent investigators show that despite U.S. intelligence reports dating back to 1983 documenting Saddam's mass gassing of the Kurds and Iranians in the ongoing Iran-Iraq war, Bush pressed for support of the Iraqis. In a damning Oct. 21, 1989, cable from Secretary of State James Baker to then Iraqi foreign minister Tariq Aziz, only a year after the mass gassing of the Kurds, Baker assured the Iraqis that the United States was very eager for a close working relationship with Saddam Hussein.
"As I said in our meeting," Baker wrote, "the U.S. seeks a broadened and deepened relationship with Iraq on the basis of mutual respect. That is the policy of our president."
ARTICLE COPY:
Made In America
It's no accident that Iraq has weapons of mass destruction. U.S. corporations helped supply them.
By Dennis Bernstein, February 25, 1998
IN JANUARY 1991 Iraqi president Saddam Hussein launched a barrage of long-range Scud missiles against Israel and Saudi Arabia. Dozens of people were wounded or killed -- including 28 U.S. soldiers who were asleep in their bunks when the Scuds hit. According to declassified secret nuclear, chemical, and biological logs kept by the Pentagon, Israeli police "confirmed nerve gas" at the site where the missile landed in downtown Tel Aviv.
While the incident was widely reported in the press, it was rarely mentioned that the technology used to increase the range of the missile that hit Israel, and to create the nerve gas that was apparently carried inside, was supplied to Iraq by U.S. and western corporations. Likewise, when U.S.-led allied forces bombed more than 30 chemical and biological weapons facilities during the 1991 war with Iraq, much of the deadly toxins that were released into the upper atmosphere, only to fall back down on the heads of U.S. forces, were created with the generous support of U.S. firms and America's leading politicians.
At one point, just a year before Iraq invaded Kuwait, Pentagon officials invited key Iraqi military technicians to a special conference in Portland, Ore., that amounted to a crash course in how to detonate a nuclear bomb.
Even today, the chemical, biological, and possibly even nuclear weapons U.S. troops could face in Gulf War II might as well be stamped "Made in the USA."
As the United States threatens to bomb Iraq for the third time this decade, the irony is brutal: Many of the same politicians, news media outlets, and interest groups that are promoting Gulf War II either supported or ignored the policies of the Reagan and Bush administrations that gave Iraq its deadly arsenal.
In fact, the problem goes far beyond the Middle East: If Saddam Hussein is capable of launching chemical, biological, or nuclear attacks, it will be the result of a long-standing U.S. policy of allowing defense contractors and other powerful corporations to sell the technology of death to almost anyone in the world who is willing to pay for it.
The Iraqi situation, former CIA military analyst Patrick Eddington told the Bay Guardian, "goes to the heart of the concept of nonproliferation and whether something like the international Chemical Weapons Convention is going to have any credibility."
"It has no chance of working if the countries who are the primary signatories, and for that matter the primary suppliers of dual-use technology," Eddington said, referring to technology that can be used for both civilian and military purposes, "are still cranking this stuff out and supplying it. It's a two-faced policy -- and that definitely includes the United States."
Our friend Saddam
Documents obtained by the Bay Guardian -- many of which have been available for years, released during Congressional investigations -- shed disturbing light on the U.S. policy of arming Saddam Hussein, a policy that may again result in the exposure of hundreds of thousands of U.S. soldiers -- and millions of civilians -- to dangerous chemical and biological weapons.
"If tomorrow the Iraqis fired a missile with biological warheads on it," Gary Milholland of the Wisconsin Project for Nuclear Arms Control told the Bay Guardian, "the missile itself would have been purchased from Russia, upgraded with help from Germany, and the bacteria would be based on a strain imported from the United States...
In the early 1980s the Reagan administration chose to support Iraq over Iran in their bloody war. Neither country was exactly an ally, but the White House considered Iran the worse of the two nations, and cold war politics (along with a U.S. desire to maintain control of oil supplies in the Middle East) put us on the side of Iraq.
In accordance with a long and continuing tradition and policy, that meant the U.S. would arm Iraq to the teeth -- without much concern for the long-term consequences.
According to a 1990 report, "The Poison Gas Connection," issued by the L.A.-based Simon Wiesenthal Center (See sidebar), more than 207 companies from 21 western countries, including at least 18 from the United States, contributed to the buildup of Saddam Hussein's arsenal. Subsequent investigations turned up more than 100 more companies participating in the Iraqi weapons buildup.
The frontline cheerleader for America's corporate contributors to Saddam, the man who paved the way for Iraq to purchase millions of dollars worth of weapons and dangerous dual-use technology from U.S. corporations, was none other than the architect of Gulf War I, former president George Bush.
In a stunning July 27, 1992, speech on the floor of the House of Representatives, House Banking Committee chair Henry Gonzalez drove the Bush connection home in no uncertain terms:
"The Bush administration deliberately, not inadvertently, helped to arm Iraq by allowing U.S. technology to be shipped to Iraqi military and to Iraqi defense factories," Gonzalez said. "Throughout the course of the Bush administration, U.S. and foreign firms were granted export licenses to ship U.S. technology directly to Iraqi weapons facilities despite ample evidence showing that these factories were producing weapons." (See sidebar)
Gonzalez, who was accused by administration officials of jeopardizing national security for going public with his gritty revelations, also stated: "The president misled Congress and the public about the role U.S. firms played in arming Iraq."
Documents gathered by Gonzalez and other independent investigators show that despite U.S. intelligence reports dating back to 1983 documenting Saddam's mass gassing of the Kurds and Iranians in the ongoing Iran-Iraq war, Bush pressed for support of the Iraqis. In a damning Oct. 21, 1989, cable from Secretary of State James Baker to then Iraqi foreign minister Tariq Aziz, only a year after the mass gassing of the Kurds, Baker assured the Iraqis that the United States was very eager for a close working relationship with Saddam Hussein. "As I said in our meeting," Baker wrote, "the U.S. seeks a broadened and deepened relationship with Iraq on the basis of mutual respect. That is the policy of our president."
According to Gonzalez, senior Bush aides successfully lobbied against the concerns of other government officials to allow Iraq to purchase the technology -- technology that could be adapted for both civilian and military purposes. These high-level Bush officials, including Baker, forced this policy through despite substantial available evidence that the Iraqis were furiously working on developing nuclear weapons and other devices of mass destruction.
The CIA reported at a top-secret intelligence briefing in November 1989 that Iraq "is interested in acquiring a nuclear explosive capability" and to this end "is ordering substantial quantities of dual-use equipment." Nevertheless, Bush and other top U.S. officials continually pressured the Agriculture Department's Commodity Credit Corporation (CCC) and the U.S. Export-Import Bank to give Iraq credit for farm products and manufactured goods. From 1983 to 1990 the CCC provided Iraq with $5 billion in credits and loans to purchase U.S. exports. Between 1984 and 1990 the Eximbank insured $297 million of additional exports. As recently as seven months before the 1990 Iraqi invasion of Kuwait, Bush issued an order allowing the bank to provide even more credit to Iraq.
Nuclear know-how
State Department documents drafted after Bush became president in 1989 warned that Iraq would rise out of the ruins of its eight-year war with Iran as a "great military and political power, and [Iraq] is aiming higher." They also indicated that Iraq was planning to use "a big-stick approach" to the border conflict with Kuwait.
According to Gonzalez's July 27, 1992, floor speech, as late as the fall of 1989, only months before Iraq invaded Kuwait, George Bush signed a top secret National Security Decision directive, known as NSD 26, ordering closer ties with Saddam Hussein and Iraq: "Normal relations between the United States and Iraq would serve our long-term interests and support stability both in the Gulf and the Middle East," stated the top secret directive. "The United States remains committed to support the individual and collective self-defense of friendly countries in the area."
The Bush directive also encouraged U.S. firms to participate in the reconstruction of the Iraqi economy, "particularly in the energy area, where they do not conflict with our nonproliferation and other significant objectives."
And participate they did. According to House and Senate Banking Committee investigations, in the five years preceding the Gulf War, the U.S. Department of Commerce licensed more than $1.5 billion of strategically sensitive American exports to Iraq. Many were directly delivered to nuclear and chemical weapon plants as well as to Iraqi missile sites. More than 700 licenses were issued to U.S. corporations doing business in Iraq; many of these licenses were for the shipment of this dual-use technology to Iraq.
In April 1990, U.S. intelligence reported to the Bush administration that Hussein "has strengthened his ties to terrorist groups and may use terrorism to intimidate his Arab and western opponents." But Bush administration back-channel and international diplomatic and financial support continued unabated.
The cooperation between U.S. suppliers and Iraqi weapons planners continued up to the beginning of the war. U.S. technicians and officials moved back and forth easily between the two countries.
In one of the more stunning incidents, in September 1989, just one year before the Iraqi military stormed over the Kuwaiti border, U.S. military officials invited several Iraqi technicians to attend a "detonation conference" at the Red Lion Inn in Portland, Ore.
The conference -- the Ninth Symposium (International) on Detonation, was a crash course from the world's experts on how to detonate a nuclear weapon. Among the named sponsors of the conference were the Office of Naval Research, the Air Force Armament Laboratory, the Army Armament Research, Development and Engineering Center, the Army Ballistic Research Laboratory, Lawrence Livermore National Laboratory, Los Alamos National Laboratory, the Naval Sea Systems Command, Naval Surface Warfare Center, Office of Naval Technology and Sandia National Laboratories, according to the conference proceedings.
The three Iraqis attending, M. Ahadd, S. Ibrhim, and H. Mahd, were all representing Al Qaqaa State Establishment in Iraq. Al Qaqaa, according to an Oct. 27, 1992, report by the Senate Committee on Banking, Housing, and Urban Affairs, "was Iraq's major explosives and rocket fuel factory." It was also a "filling station for ballistic missiles" and home for Iraq's nuclear weapons program.
Joining the Iraqis in this quaint setting on the Columbia River, learning all about nuclear bomb detonation, were 445 participants from 20 countries, including Israelis and technicians from South Korea.
The list of U.S. corporations that teamed up with Saddam reads like a who's who of America's favorite defense contractors. According to the Wiesenthal report and the Senate Banking Committee they include Hewlett-Packard, Honeywell, and Sperry/Unisys among others.
Bush's secret weapons
In a letter dated July 9, 1992, twenty Democratic members of the House Judiciary Committee petitioned the attorney general to appoint a special prosecutor to investigate "serious allegations of possible violations of federal criminal statutes by high-ranking officials of the Executive Branch."
Among the potential criminal violations cited in the petition were making false statements, obstruction of justice, concealment or falsification of records, perjury, mail and wire fraud, conspiracy to defraud the United States or to commit an offense against the United States, and financial conflict of interest by high executive branch officials.
The 1992 letter further cited the Bush administration's "willful and repeated failure" to comply with requests by the House Judiciary and other committees for both documents and witnesses.
According to the 27-month Gonzalez Investigation, the Bush administration set up an "interagency" group after the Gulf War to prevent Congress from finding out about U.S. aid to Iraq before the Kuwait invasion.
Gonzalez's concerns centered on the handling by the Justice Department of the investigation into Banka Nazionale del Lavoro (BNL) in Atlanta. Most of Iraq's purchases of sensitive technology were handled by BNL. According to Gonzalez, Iraq had set up a secret network to buy equipment for missiles and for nuclear, chemical, and germ weapons. More than $5 billion in soft loans were funneled through the bank to the Iraqis in the five years leading up to the war. According to Gonzalez's compelling investigation, almost half of the $5 billion was funneled directly into Iraq's ambitious weapons program.
The Bush administration's task was to limit the investigation to one low-level bank official in Atlanta, resisting any attempt to connect the Iraqi loans to high administration officials or to BNL's mother bank in Italy and other shady institutions, such as the Bank of Credit and Commerce International (BCCI), the CIA's bank of choice.
To this end, at least five federal agencies apparently misled, lied to, and blatantly stonewalled prosecutors in charge of the BNL investigation. According to a strongly worded October 1992 statement by the then chair of the Senate Intelligence Committee, David Boren, in support of the appointment of a special prosecutor, the CIA "with strong advice" from the Justice Department "authored a misleading letter to the acting U.S. attorney in Atlanta" regarding the BNL investigation. "In light of this new information," Boren stated, "I call on the attorney general to meet his obligations ... and appoint a special prosecutor."
To make his case, Boren cited the concerns of the federal judge in the stymied BNL case. In a sharp rebuke of the government's behavior, Judge Marvin Shoob accused Bush officials of stonewalling and deception in the BNL case and joined the call for a special prosecutor.
"High-level officials in the Justice Department and the State Department met with the Italian ambassador," stated the frustrated federal judge, and "...decisions were made at the top levels of the United States government and within the intelligence community to shape this case." Shoob also noted that "the local prosecutor in this matter received ... highly unusual and inappropriate telephone calls from the White House Office of Legal Counsel."
Despite the strong words from Boren, Gonzalez, and Shoob, a special prosecutor was never appointed, and no administration officials were ever indicted or even forced to testify. Low-level bank officials ultimately took the rap for a multibillion-dollar, illegal, secret government scheme, spearheaded by the president of the United States, to arm Iraq.
And the coverup, thanks to Clinton officials, continues to this day. During the 1992 presidential campaign, Gore called the coverup of the secret Bush policy to arm Iraq "bigger than Watergate ever was," but in a Jan. 16, 1995, report, the Clinton Justice Department absolved the Bush administration and stated that it had found no evidence "that U.S. agencies or officials illegally armed Iraq."
War criminals
London Independent reporter Robert Fisk has written movingly about riding back to Tehran in a train with young Iranian soldiers returning from the front during the bloody war with Iraq -- a war fueled by western politicians and western arms dealers. "All of them were coughing up Saddam Hussein's poisons from their lungs into blood-red swabs and bandages," writes the veteran Middle East reporter. "And the mustard gas that was slowly killing them permeated the whole great 20-carriage train as it thundered up from the desert battlefields of the first Gulf War." Fisk points out it was not only technology that the United States and the Europeans provided Saddam with to create nuclear, chemical, and biological weapons, but the means to efficiently deploy them.
"The Americans had sold him helicopters to spray the crops with pesticide," Fisk said, "the 'crops,' of course, being human beings." And in an astounding revelation Fisk stated, "I later met the [German] arms dealer who flew from the Pentagon to Baghdad with U.S. satellite photos of the Iranian front lines to help Saddam kill more Iranians."
Iranians weren't the only victims. Tens of thousands of U.S. soldiers and military personnel were doused with chemical and biological warfare agents in the first Gulf War. In fact, Gulf veterans have filed a billion-dollar class action lawsuit in federal court in Galveston, Texas, against companies that supplied Iraq with the dual-use technology to create its weapons of mass destruction. Among the companies named are Bechtel, M.W. Kellog, Dresser Industries, and Interchem Inc...
The Iran-Contra Affair: The Making of a Scandal, 1983-1988
The Iran-Contra Scandal in Perspective [missing link - new link below]http://www.gwu.edu/~nsarchiv/nsa/publications/irancontra/irancon.html
http://www.gwu.edu/~nsarchiv/NSAEBB/NSAEBB210/index.htm
and how the Republican Party & their Corporate Buddies
hid the information: [missing link - new link below]http://www.gwu.edu/%7Ensarchiv/nsa/publications/DOC_readers/icread/icread.html
Which raises the question why the Pentagon,
in this Village Voice article, wanted to do this:According to a Denver Post report on January 24, the Pentagon has been considering an option to bulldoze the bodies of U.S. soldiers killed by chemical or biological weapons into mass graves and then burn them to save the lives of surviving troops.
In conclusion,
When contemplating war,
beware of babies in incubatorsThe babies in the incubator story is a classic example of how easy it is for the public and legislators to be mislead during moments of high tension. It's also a vivid example of how the media can be manipulated if we do not keep our guards up. - Permalink
Van Morrison: Astral Weeks
http://www.youtube.com/watch?v=CVxEO97iWdA&feature=player_embedded
Astral Weeks ~ Joe Creighton live at Blue Beat, Double Bay ~ http://vimeo.com/57040369
War Criminal Quotes
February 5, 2003
We know that Saddam Hussein is determined to keep his weapons of mass destruction, is determined to make more. = Colin Powell
Iraq both poses a continuing threat to the national security of the United States and international peace and security in the Persian Gulf region and remains in material and unacceptable breach of its international obligations by, among other things, continuing to possess and develop a significant chemical and biological weapons capability, actively seeking a nuclear weapons capability, and supporting and harboring terrorist organizations. = Sen. Hillary Clinton, D-NY
February 8, 2003
We have sources that tell us that Saddam Hussein recently authorized Iraqi field commanders to use chemical weapons -- the very weapons the dictator tells us he does not have. = George W. Bush
David Normal ~ Artist
CRAZYOLOGY EXHIBITION
by David Normal
CRAZYOLOGY RECEPTION FEBRUARY 8THHello
I'm having an exhibition of my artworks called "CRAZYOLOGY" in San Francisco at 1000 Van Ness. through Feb. 14th.
This article published today in Cartwheel Arts, blog and magazine based in LA, explains it well:
http://www.cartwheelart.com/news/let-there-be-light-david-normal-illuminates-san-francisco
If you are in the Bay Area please come to the reception on Friday Feb. 8th.
The following advertising bombast will tell you everything you need to know.
"CRAZYOLOGY"FRIDAY FEB. 8th - 7PM till Late . . .
A Gallery Reception Party for David Normal's Installation of the Illuminations at 1000 Van Ness, San Francisco, CA
*
Featuring: Los Angeles's Scintillating Sci-Fi-Delic Flying Saucer Love Cult, THE FANCY SPACE PEOPLE
*
Light, Sound and Dimensional Mystery Theater with SPUKKIN' FACESHIP and the SEMI-PERMANENT AUTONOMOUS ZONE
*
A Whirlwind of Unusual Spectacles for the Connoisseur of Eccentricities MOLOTOV MALCONTENT and DIXIE DELISH
*
The Fine Far Eastern Art of SHIBARI by TIED OUT WEST with Electronic Noise Accompaniment by BARNEY THE THEREMIN WIZARD
*
Auditory Incunabula and Instrumental Curiosa THE CRANK ENSEMBLE
*
hyper-extended clownicles of the TEMPLETON VARIETY SHOW pioneering the high frontiers of madcap mummery
*
A Seriously Rollicking Dramatized Recital of Tennyson's Classic Poem THE LADY OF SHALLOT by LADY CHIMMERLY, LADY STARRYHORN, SIR BALLSALOT
*
A Scholarly Dissertation on Demonically Possessed Cats by DR. PAUL KOUDOUNARIS, PhD with Interpretive Antics by TIFFANY ROJAS, KAOS KITTY, and Members of the SF SPCA
*
Esoteric Revelations and Poetic Illuminations "Dr. Hal" Robins, Church of the SubGenius
*
Vinyl Interludes by DJ NEIL MARTINSON
*
bodypainting by ACE BODYPAINT
*
DAVID NORMAL'S wardrobe by DAS-OWL
*
Raffle and give-away of David Normal artworks hosted by Dr. Hal
*
Panoramic Delirium of Ocular Delectation by K-ROB and SPAZSearch FlyingSnail for Art by David Normal:
Refuses To Investigate Murders of Women, Children, Civilians, Or Torture During Bush's Illegal Iraq War?
"JUSTIFIES ASSASSINATIONS OF US CITIZENS"
Bringing New Definition To: YES WE CAN?
Does Justification Also Include John Ashcroft & a Criminal Bush Administration?
Chilling legal memo from Obama DOJ
justifies assassination of US citizensThe president's partisan lawyers purport to vest him with the most extreme power a political leader can seize
Glenn Greenwald, guardian.co.uk, Tuesday 5 February 2013 10.56 EST, Article Source
Barack Obama Photograph: ReutersThe most extremist power any political leader can assert is the power to target his own citizens for execution without any charges or due process, far from any battlefield. The Obama administration has not only asserted exactly that power in theory, but has exercised it in practice. In September 2011, it killed US citizen Anwar Awlaki in a drone strike in Yemen, along with US citizen Samir Khan, and then, in circumstances that are still unexplained, two weeks later killed Awlaki's 16-year-old American son Abdulrahman with a separate drone strike in Yemen.
Since then, senior Obama officials including Attorney General Eric Holder and John Brennan, Obama's top terrorism adviser and his current nominee to lead the CIA, have explicitly argued that the president is and should be vested with this power. Meanwhile, a Washington Post article from October reported that the administration is formally institutionalizing this president's power to decide who dies under the Orwellian title "disposition matrix".
When the New York Times back in April, 2010 first confirmed the existence of Obama's hit list, it made clear just what an extremist power this is, noting: "It is extremely rare, if not unprecedented, for an American to be approved for targeted killing." The NYT quoted a Bush intelligence official as saying "he did not know of any American who was approved for targeted killing under the former president". When the existence of Obama's hit list was first reported several months earlier by the Washington Post's Dana Priest, she wrote that the "list includes three Americans".
What has made these actions all the more radical is the absolute secrecy with which Obama has draped all of this. Not only is the entire process carried out solely within the Executive branch - with no checks or oversight of any kind - but there is zero transparency and zero accountability. The president's underlings compile their proposed lists of who should be executed, and the president - at a charming weekly event dubbed by White House aides as "Terror Tuesday" - then chooses from "baseball cards" and decrees in total secrecy who should die. The power of accuser, prosecutor, judge, jury, and executioner are all consolidated in this one man, and those powers are exercised in the dark.
In fact, The Most Transparent Administration Ever™ has been so fixated on secrecy that they have refused even to disclose the legal memoranda prepared by Obama lawyers setting forth their legal rationale for why the president has this power. During the Bush years, when Bush refused to disclose the memoranda from his Office of Legal Counsel (OLC) that legally authorized torture, rendition, warrantless eavesdropping and the like, leading Democratic lawyers such as Dawn Johnsen (Obama's first choice to lead the OLC) vehemently denounced this practice as a grave threat, warning that "the Bush Administration's excessive reliance on 'secret law' threatens the effective functioning of American democracy" and "the withholding from Congress and the public of legal interpretations by the [OLC] upsets the system of checks and balances between the executive and legislative branches of government."
But when it comes to Obama's assassination power, this is exactly what his administration has done. It has repeatedly refused to disclose the principal legal memoranda prepared by Obama OLC lawyers that justified his kill list. It is, right now, vigorously resisting lawsuits from the New York Times and the ACLU to obtain that OLC memorandum. In sum, Obama not only claims he has the power to order US citizens killed with no transparency, but that even the documents explaining the legal rationale for this power are to be concealed. He's maintaining secret law on the most extremist power he can assert.
Last night, NBC News' Michael Isikoff released a 16-page "white paper" prepared by the Obama DOJ that purports to justify Obama's power to target even Americans for assassination without due process (the memo is embedded in full below). This is not the primary OLC memo justifying Obama's kill list - that is still concealed - but it appears to track the reasoning of that memo as anonymously described to the New York Times in October 2011.
This new memo is entitled: "Lawfulness of a Lethal Operation Directed Against a US Citizen Who is a Senior Operational Leader of Al-Qa'ida or An Associated Force". It claims its conclusion is "reached with recognition of the extraordinary seriousness of a lethal operation by the United States against a US citizen". Yet it is every bit as chilling as the Bush OLC torture memos in how its clinical, legalistic tone completely sanitizes the radical and dangerous power it purports to authorize.
I've written many times at length about why the Obama assassination program is such an extreme and radical threat - see here for one of the most comprehensive discussions, with documentation of how completely all of this violates Obama and Holder's statements before obtaining power - and won't repeat those arguments here. Instead, there are numerous points that should be emphasized about the fundamentally misleading nature of this new memo:
1. Equating government accusations with guilt
The core distortion of the War on Terror under both Bush and Obama is the Orwellian practice of equating government accusations of terrorism with proof of guilt. One constantly hears US government defenders referring to "terrorists" when what they actually mean is: those accused by the government of terrorism. This entire memo is grounded in this deceit.
Time and again, it emphasizes that the authorized assassinations are carried out "against a senior operational leader of al-Qaida or its associated forces who poses an imminent threat of violent attack against the United States." Undoubtedly fearing that this document would one day be public, Obama lawyers made certain to incorporate this deceit into the title itself: "Lawfulness of a Lethal Operation Directed Against a US Citizen Who is a Senior Operational Leader of al-Qaida or An Associated Force."
This ensures that huge numbers of citizens - those who spend little time thinking about such things and/or authoritarians who assume all government claims are true - will instinctively justify what is being done here on the ground that we must kill the Terrorists or joining al-Qaida means you should be killed. That's the "reasoning" process that has driven the War on Terror since it commenced: if the US government simply asserts without evidence or trial that someone is a terrorist, then they are assumed to be, and they can then be punished as such - with indefinite imprisonment or death.
But of course, when this memo refers to "a Senior Operational Leader of al-Qaida", what it actually means is this: someone whom the President - in total secrecy and with no due process - has accused of being that. Indeed, the memo itself makes this clear, as it baldly states that presidential assassinations are justified when "an informed, high-level official of the US government has determined that the targeted individual poses an imminent threat of violent attack against the US".
This is the crucial point: the memo isn't justifying the due-process-free execution of senior al-Qaida leaders who pose an imminent threat to the US. It is justifying the due-process-free execution of people secretly accused by the president and his underlings, with no due process, of being that. The distinction between (a) government accusations and (b) proof of guilt is central to every free society, by definition, yet this memo - and those who defend Obama's assassination power - willfully ignore it.
Those who justify all of this by arguing that Obama can and should kill al-Qaida leaders who are trying to kill Americans are engaged in supreme question-begging. Without any due process, transparency or oversight, there is no way to know who is a "senior al-Qaida leader" and who is posing an "imminent threat" to Americans. All that can be known is who Obama, in total secrecy, accuses of this.
(Indeed, membership in al-Qaida is not even required to be assassinated, as one can be a member of a group deemed to be an "associated force" of al-Qaida, whatever that might mean: a formulation so broad and ill-defined that, as Law Professor Kevin Jon Heller argues, it means the memo "authorizes the use of lethal force against individuals whose targeting is, without more, prohibited by international law".)
The definition of an extreme authoritarian is one who is willing blindly to assume that government accusations are true without any evidence presented or opportunity to contest those accusations. This memo - and the entire theory justifying Obama's kill list - centrally relies on this authoritarian conflation of government accusations and valid proof of guilt.
They are not the same and never have been. Political leaders who decree guilt in secret and with no oversight inevitably succumb to error and/or abuse of power. Such unchecked accusatory decrees are inherently untrustworthy (indeed, Yemen experts have vehemently contested the claim that Awlaki himself was a senior al-Qaida leader posing an imminent threat to the US). That's why due process is guaranteed in the Constitution and why judicial review of government accusations has been a staple of western justice since the Magna Carta: because leaders can't be trusted to decree guilt and punish citizens without evidence and an adversarial process. That is the age-old basic right on which this memo, and the Obama presidency, is waging war.
2. Creating a ceiling, not a floor
The most vital fact to note about this memorandum is that it is not purporting to impose requirements on the president's power to assassinate US citizens. When it concludes that the president has the authority to assassinate "a Senior Operational Leader of al-Qaida" who "poses an imminent threat of violent attack against the US" where capture is "infeasible", it is not concluding that assassinations are permissible only in those circumstances.
To the contrary, the memo expressly makes clear that presidential assassinations may be permitted even when none of those circumstances prevail: "This paper does not attempt to determine the minimum requirements necessary to render such an operation lawful." Instead, as the last line of the memo states: "it concludes only that the stated conditions would be sufficient to make lawful a lethal operation" - not that such conditions are necessary to find these assassinations legal. The memo explicitly leaves open the possibility that presidential assassinations of US citizens may be permissible even when the target is not a senior al-Qaida leader posing an imminent threat and/or when capture is feasible.Critically, the rationale of the memo - that the US is engaged in a global war against al-Qaida and "associated forces" - can be easily used to justify presidential assassinations of US citizens in circumstances far beyond the ones described in this memo. If you believe the president has the power to execute US citizens based on the accusation that the citizen has joined al-Qaida, what possible limiting principle can you cite as to why that shouldn't apply to a low-level al-Qaida member, including ones found in places where capture may be feasible (including US soil)? The purported limitations on this power set forth in this memo, aside from being incredibly vague, can be easily discarded once the central theory of presidential power is embraced.
3. Relies on the core [War Criminals] Bush/Cheney theory of a global battlefield
The primary theory embraced by the Bush administration to justify its War on Terror policies was that the "battlefield" is no longer confined to identifiable geographical areas, but instead, the entire globe is now one big, unlimited "battlefield". That theory is both radical and dangerous because a president's powers are basically omnipotent on a "battlefield". There, state power is shielded from law, from courts, from constitutional guarantees, from all forms of accountability: anyone on a battlefield can be killed or imprisoned without charges. Thus, to posit the world as a battlefield is, by definition, to create an imperial, omnipotent presidency. That is the radical theory that unleashed all the rest of the controversial and lawless Bush/Cheney policies.
This "world-is-a-battlefield" theory was once highly controversial among Democrats. John Kerry famously denounced it when running for president, arguing instead that the effort against terrorism is "primarily an intelligence and law enforcement operation that requires cooperation around the world".
But this global-war theory is exactly what lies at heart of the Obama approach to Terrorism generally and this memo specifically. It is impossible to defend Obama's assassination powers without embracing it (which is why key Obama officials have consistently done so). That's because these assassinations are taking place in countries far from any war zone, such as Yemen and Somalia. You can't defend the application of "war powers" in these countries without embracing the once-very-controversial Bush/Cheney view that the whole is now a "battlefield" and the president's war powers thus exist without geographic limits.
This new memo makes clear that this Bush/Cheney worldview is at the heart of the Obama presidency. The president, it claims, "retains authority to use force against al-Qaida and associated forces outside the area of active hostilities". In other words: there are, subject to the entirely optional "feasibility of capture" element, no geographic limits to the president's authority to kill anyone he wants. This power applies not only to war zones, but everywhere in the world that he claims a member of al-Qaida is found. This memo embraces and institutionalizes the core Bush/Cheney theory that justified the entire panoply of policies Democrats back then pretended to find so objectionable.
4. Expanding the concept of "imminence" beyond recognition
The memo claims that the president's assassination power applies to a senior al-Qaida member who "poses an imminent threat of violent attack against the United States". That is designed to convince citizens to accept this power by leading them to believe it's similar to common and familiar domestic uses of lethal force on US soil: if, for instance, an armed criminal is in the process of robbing a bank or is about to shoot hostages, then the "imminence" of the threat he poses justifies the use of lethal force against him by the police.
But this rhetorical tactic is totally misleading. The memo is authorizing assassinations against citizens in circumstances far beyond this understanding of "imminence". Indeed, the memo expressly states that it is inventing "a broader concept of imminence" than is typically used in domestic law. Specifically, the president's assassination power "does not require that the US have clear evidence that a specific attack . . . will take place in the immediate future". The US routinely assassinates its targets not when they are engaged in or plotting attacks but when they are at home, with family members, riding in a car, at work, at funerals, rescuing other drone victims, etc.
Many of the early objections to this new memo have focused on this warped and incredibly broad definition of "imminence". The ACLU's Jameel Jaffer told Isikoff that the memo "redefines the word imminence in a way that deprives the word of its ordinary meaning". Law Professor Kevin Jon Heller called Jaffer's objection "an understatement", noting that the memo's understanding of "imminence" is "wildly overbroad" under international law.
Crucially, Heller points out what I noted above: once you accept the memo's reasoning - that the US is engaged in a global war, that the world is a battlefield, and the president has the power to assassinate any member of al-Qaida or associated forces - then there is no way coherent way to limit this power to places where capture is infeasible or to persons posing an "imminent" threat. The legal framework adopted by the memo means the president can kill anyone he claims is a member of al-Qaida regardless of where they are found or what they are doing.
The only reason to add these limitations of "imminence" and "feasibility of capture" is, as Heller said, purely political: to make the theories more politically palatable. But the definitions for these terms are so vague and broad that they provide no real limits on the president's assassination power. As the ACLU's Jaffer says: "This is a chilling document" because "it argues that the government has the right to carry out the extrajudicial killing of an American citizen" and the purported limits "are elastic and vaguely defined, and it's easy to see how they could be manipulated."
5. Converting Obama underlings into objective courts
This memo is not a judicial opinion. It was not written by anyone independent of the president. To the contrary, it was written by life-long partisan lackeys: lawyers whose careerist interests depend upon staying in the good graces of Obama and the Democrats, almost certainly Marty Lederman and David Barron. Treating this document as though it confers any authority on Obama is like treating the statements of one's lawyer as a judicial finding or jury verdict.
Indeed, recall the primary excuse used to shield Bush officials from prosecution for their crimes of torture and illegal eavesdropping: namely, they got Bush-appointed lawyers in the DOJ to say that their conduct was legal, and therefore, it should be treated as such. This tactic - getting partisan lawyers and underlings of the president to say that the president's conduct is legal - was appropriately treated with scorn when invoked by Bush officials to justify their radical programs. As Digby wrote about Bush officials who pointed to the OLC memos it got its lawyers to issue about torture and eavesdropping, such a practice amounts to:
"validating the idea that obscure Justice Department officials can be granted the authority to essentially immunize officials at all levels of the government, from the president down to the lowest field officer, by issuing a secret memo. This is a very important new development in western jurisprudence and one that surely requires more study and consideration. If Richard Nixon and Ronald Reagan had known about this, they could have saved themselves a lot of trouble."
Life-long Democratic Party lawyers are not going to oppose the terrorism policies of the president who appointed them. A president can always find underlings and political appointees to endorse whatever he wants to do. That's all this memo is: the by-product of obsequious lawyers telling their Party's leader that he is (of course) free to do exactly that which he wants to do, in exactly the same way that Bush got John Yoo to tell him that torture was not torture, and that even it if were, it was legal.
That's why courts, not the president's partisan lawyers, should be making these determinations. But when the ACLU tried to obtain a judicial determination as to whether Obama is actually authorized to assassinate US citizens, the Obama DOJ went to extreme lengths to block the court from ruling on that question. They didn't want independent judges to determine the law. They wanted their own lawyers to do so.
That's all this memo is: Obama-loyal appointees telling their leader that he has the authority to do what he wants. But in the warped world of US politics, this - secret memos from partisan lackeys - has replaced judicial review as the means to determine the legality of the president's conduct.
6. Making a mockery of "due process"
The core freedom most under attack by the War on Terror is the Fifth Amendment's guarantee of due process. It provides that "no person shall be . . . deprived of life . . . without due process of law". Like putting people in cages for life on island prisons with no trial, claiming that the president has the right to assassinate US citizens far from any battlefield without any charges or trial is the supreme evisceration of this right.
The memo pays lip service to the right it is destroying: "Under the traditional due process balancing analysis . . . . we recognize that there is no private interest more weighty than a person's interest in his life." But it nonetheless argues that a "balancing test" is necessary to determine the extent of the process that is due before the president can deprive someone of their life, and further argues that, as the New York Times put it when this theory was first unveiled: "while the Fifth Amendment's guarantee of due process applied, it could be satisfied by internal deliberations in the executive branch."
Stephen Colbert perfectly mocked this theory when Eric Holder first unveiled it to defend the president's assassination program. At the time, Holder actually said: "due process and judicial process are not one and the same." Colbert interpreted that claim as follows:
"Trial by jury, trial by fire, rock, paper scissors, who cares? Due process just means that there is a process that you do. The current process is apparently, first the president meets with his advisers and decides who he can kill. Then he kills them."
It is fitting indeed that the memo expressly embraces two core Bush/Cheney theories to justify this view of what "due process" requires. First, it cites the Bush DOJ's core view, as enunciated by John Yoo, that courts have no role to play in what the president does in the War on Terror because judicial review constitutes "judicial encroachment" on the "judgments by the President and his national security advisers as to when and how to use force". And then it cites the Bush DOJ's mostly successful arguments in the 2004 Hamdi case that the president has the authority even to imprison US citizens without trial provided that he accuses them of being a terrorist.
The reason this is so fitting is because, as I've detailed many times, it was these same early Bush/Cheney theories that made me want to begin writing about politics, all driven by my perception that the US government was becoming extremist and dangerous. During the early Bush years, the very idea that the US government asserted the power to imprison US citizens without charges and due process (or to eavesdrop on them) was so radical that, at the time, I could hardly believe they were being asserted out in the open.
Yet here we are almost a full decade later. And we have the current president asserting the power not merely to imprison or eavesdrop on US citizens without charges or trial, but to order them executed - and to do so in total secrecy, with no checks or oversight. If you believe the president has the power to order US citizens executed far from any battlefield with no charges or trial, then it's truly hard to conceive of any asserted power you would find objectionable.
DOJ white paper PDF
(The Coup's) Ride the Fence by Haik Hoisington ~ BlackMustache.com ~ NOT WORK WORD SAFE
Notes from ~@~ Listed Below:
Nature Was My Teacher
The Vision of Viktor Schauberger
from Thomas Joseph Brown, Source
In 1958, what was to be the last year of his life, a little known man of great vision received an invitation from America he simply couldn't refuse: complete and ample financial support to carry on the work of Project Implosion -- a project which promised to give humanity free, clean energy while allowing for the return of balance in nature. And so, despite his deteriorating health, an elderly Austrian Forestmaster, Viktor Schauberger, gathered all the materials of his life's work and made the trip to America -- at last Schauberger was to receive the long-overdue recognition for his awesome discoveries!
Unbeknown to Viktor however, there was no money, only a well planned set-up that kept him in virtual imprisonment until every bit of his incredible data was signed over to these mysterious Americans. Completely crushed and dismayed, Viktor returned home to Austria where he died five days later.
Who was this man Viktor Schauberger, and what sort of evolved discoveries had he made which prompted the methodical invalidation of his ideas and the diabolical destruction of his intense will to life?
This video reseals all the shocking details of his life commitment -- the proposals, the inventions, and the predictions that so upset the establishment.
This video celebrates Viktor's dedication to the salvation and glorification of water -- the lifeblood of the earth. Witness for yourself the astounding contributions one remarkable man attempted to bring to a planet already showing signs of the desperate times ahead during the 1920s and 1930s. This is one video you will want to show to everyone around to help spread its vital message.
This video has been posted on several other sites for years and is now legendary. I am posting it here with my other surviving videos to have them all in one place. Do more searching on Schauberger and implosion energy, there has been a lot of good work put out since I did this video in the early 1990s.
The Dirty Fu*king Hippies WERE RIGHT! via Amestizo
http://www.youtube.com/embed/eCyoLabWii8?rel=0
Missing BBS Files ~ Some of the first Bulletin Board Systems in the United States
8BBS
8BBS started in 1980 in my spare bedroom in Santa Clara, CA. It was inspired by and loosely modeled on CBBS. Dick Murphy wrote much of the custom PAL8 assember code and special features. I wrote the 'easy' parts in BASIC.
8BBS hardware consisted of a DEC PDP-8/e, 32K 12-bit words using core memory (no need for a UPS). The 12-bit words allowed two characters to be stored (6-bits each), or three 8-bit characters could be stored in two 12-bit words.
Initially, 8BBS used a Penywhistle 300-baud dial-up modem. A user in Pennsylvania eventually offered to donate a Bell 1200-baud modem. The mass storage device consisted of DEC RK05J removeable hard drives (1.2 MB ea). Backups were done on a DEC TU56 magnetic tape drive using a TD8-E controller. The TD8-E controller used a lot of CPU cycles, so backups were done late at night. The console was a DEC VT52 video terminal and a LA180 DECprinter for hardcopy printouts.
My policy was 'no censorship'. The reasons for this were to differentiate 8BBS from most other BBS's that had heavy moderation and reflected only the opinions of its operator and that fact that my work often required me to be away (often out of the country) for days or weeks at a time so it wasn't practical for me to moderate, approve, censor, edit, delete users posts.
Some of the more noteable 8BBS users that I recall were, Paul Traina, Kevin Mitnick, 'Roscoe' and 'Susan Thunder'.
A small sample of 8BBS messages is available at: http://www.flyingsnail.com/missingbbs/8BBS.html
During the summer of 1982, the FBI and Santa Clara police raided my apartment while I was out of the country and seized the RK05 disk packs that 8BBS used. I was never charged with any offense, but did have to hire an attorney to request the return of my property that was taken by the police.
The 8BBS RK05 disk packs were returned about a year later, but the forensic exam damaged the data structure so it was no longer possible to run 8BBS. The backups were of the user posts only, not the 8BBS source code and executables. I suspect the forensic examiners tried to work with it on a PDP-11 system which uses a slightly different variation of RK05 disk pack.
I understand that some students from Drexel University were charged with theft of goods - that's where the donated Bell 1200 baud modem alledgedly came from. I believe 8BBS was the first BBS to be raided and shutdown by the FBI for content posted by its users.
Even though my employer fired me because of the police raid, the 8BBS project was fun to create and provided opportunities to interact with many interesting people. I learned that most people (law-enforcement especially) have a rather tenous concept of what the 1st Amendment means.
January/February 1981: Thirty-Two Years Ago
A Lesson In Consistency
http://www.flyingsnail.com/missingbbs/8BBS.html
8BBS Printout of January 30, 1981: Msg 5808 ~ http://www.flyingsnail.com/missingbbs/5808.htmlFunction: A,B,C,D,E,F,G,H,K,L,N,'O,P,Q,R,S,
T,U,V,W,X,Y,Z',# (Or "?" if not known)? ,S,R
Message: What message to retrieve, 1/5962? 5808Message number 5808 is 16 lines from Susan Thunder
To Curtis Spangler and SYSOP at 15:47:52 on 30-Jan-81.
Subject: DIAL-UP DISCONNECTIONDear Bernard,
I'm sorry that your line was disconnected for about a half hour right around 3:15 today, but this impatient asshole known as Curtis Spangler decided to dump me off and use the system... needless to say, I had the line "removed" from service for a few minutes so that Curtis would KNOW that not all the users on this system just let getting dumped off go right past them...Eric Moyer was lucky ... he slipped in there just as I re-established service to this line ... If anyone reading this happens to know Curtis's phone number or address, I will tell you how to NO AMA calls all over the country via the TSPS in exchange for the information ... (free calls ... ) ... And maybe those of you who like to "dump" into this BBS will think twice about doing it ... Curtis is certainly going to remember it for awhile!!!
THUNDR@ MIT-DM, AI
C. Spangler - Photograph: FlyingSnailCurtis Spangler - The CommuniTree's First Fairwitness
Let's look at some of the earliest electronic virtual communities. This kinship chart shows the origins of the first computer bulletin boards (BBSs) that supported social interaction. Prior to this moment, BBSs messages were organized by alphabetical order, or by date. BBSs were metaphors for physical bulletin boards... objects for the exchange of simple messages, not conversations. Now, in 1978 a group of people in Northern California designed a BBS that used message attachment protocols that facilitated conversations. As a metaphor for this structure they used a tree, firstly because it was based on a principle of computer science called binary tree protocol, and secondly because Northern California near Silicon Valley was a land of hot tubs, Eastern mysticism, and computer hackers, and the organicity that the word "tree" suggested was important to those hackers' worldview.
The story of the life and death of the first CommuniTree tells us how and why the later virtual community systems were designed. The original CommuniTree was designed with the idea that the community it facilitated would be completely free. Anyone could enter any sort of message. In fact, censorship was completely prohibited at the level of the code, of the Tree's program. It worked this way: First, the system operator was prevented from reading messages as they arrived. Second, messages were hard to remove once they were entered. Third, anything could be entered into the system, including so-called control characters, which are not part of the standard alphanumeric set and which can be used to control the operation of the host computer. Lastly, to make sure that no system operator could tamper with the system, the code was written in language called Forth, and not documented. Now Forth is a religion unto itself, and if you know anything about Forth you recognize that this makes the system a total black box -- it's impossible to know anything about how the code works.
CommuniTree went online in 1978. The kinds of conversations they had in there were of a high intellectual and spiritual character. They talked about new philosophies and new religions for post-Enlightenment humanity, the first time such conversations had taken place online.
Now, at the same moment Apple Computer had reached an agreement with the U. S. Government that in return for a tax break, Apple put computers into primary and secondary schools in the U.S., and some of those computers had modems. This meant that quite suddenly a lot of kids could get online. At first both boys and girls had access, but the boys quickly elbowed the girls out of the way -- high tech was men's work. The boys quickly found out CommuniTree's phone number and logged on. They were clearly unimpressed with the high intellectual level of the discourse on CommuniTree, and they expressed their dissatisfaction in ways that were appropriate to their age and linguistic abilities. Now, the hardware of the Tree was the best that Apple had to offer in 1978, it had two floppy disk drives with a combined total of 300 kilobytes of storage. At the time, the folks who designed the Tree said "300K -- we can go on forever. We'll never fill this up." A common BBS today would have at least 100 megabytes of storage, many orders of magnitude greater than the Tree. So it didn't take long for the kids to fill every byte of disk space with every word they could think of that meant shitting or fucking, and then they'd add control characters on top of that, characters that could mess with the program or stop the floppy drives. The sysops couldn't see the messages arriving and couldn't remove them afterward. The Tree was doomed.
One of the participants in the Tree discourse said "Well, the barbarian hordes mowed us down." And the people who were on the Tree ran away, just like the population of a village during a sack. It was a kind of scattering of the tribes. Some of those people went off and designed BBSs of their own that had built into them the elements of control and surveillance that appeared to be necessary to ensure the BBS's survival in a real world that included roaming barbarians. That kind of surveillance and control continues to the present day, built right into the software; we don't think about it much any more.
And that's how, back at the beginning of virtual time, the first virtual community left the Magic Garden and entered the "real" virtual world in which good had to find ways to coexist with evil.
Source: http://www.flyingsnail.com/missingbbs/CommuniTree.html
The Stanford Packet Radio Network
Michael J. Flynn, Curtis Spangler, and Andrew ZimmermanComputer Systems Laboratory, Electrical Engineering Department
Stanford University, Stanford CA 94305-2192Abstract The Stanford Packet Radio Network is designed to provide from 9600 to about 56,000 baud access to "line of sight" users (within about 30 miles) of SUN-the Stanford University Network. The cost objective is $'~,000 per user for the marginal cost of modem, transceiver, etc. Basic testing has been completed, and a preliminary network will begin operations in early 1986. [Continue Reading]
Boptime with Even Steven + The Legends of Wilmington Jazz
BOPTIME: Saturday, 6 AM Eastern time, 3 AM Pacific time:
MP3 Stream ~ Low 24K ~ High 128K ~ Real Audio ~ Low 24K ~ High 128K ~ Windows ~ Low 24K ~ High 128K
Mike Wilhelm ~ Charlatans, Flamin' Groovies, Loose Gravel, and more
Strawberry Roan by Mike Wilhelm - Complete 1915 lyrics by Curley Fletcher located at source
http://www.youtube.com/watch?v=15o4FcRFZDI&feature=player_embedded
Autumn Fenders ~ Ralph Davis
Keith Lampe ~ Co-Founder of YIPPIE and Progressive Activist Groups + Video Channel
Pondo Mantra, Keith Lampe
http://www.youtube.com/watch?list=UUn23s8Fks1Bry-Pn1KJeWdg&v=yxXEBlc5slI&feature=player_embedded
Paul Krassner ~ The Realist/Writer/Comic/Investigative Satirist
Paul Krassner's Contributions to the Counterculture
http://www.youtube.com/watch?v=5D1pSDTMTqA&feature=player_embedded
Notes from ~@~ Listed Below:
Nobody Knows the Truth About Chemtrails
What in The World Are They Spraying? ~ http://vimeo.com/16219493#at=0
Archives ~ The past: Nothing Has Changed
2013: 2013.02 ~ 2013.01
2012: 2012.12 ~ 2012.11 ~ 2012.10 ~ 2012.09 ~ 2012.08 ~ 2012.07 ~ 2012.06 ~ 2012.05 ~ 2012.04 ~ 2012.03 ~ 2012.02 ~ 2012.01
2011: 2011.12 ~ 2011.11 ~ 2011.10 ~ 2011.09 ~ 2011.08 ~ 2011.07 ~ 2011.06 ~ 2011.05 ~ 2011.04 ~ 2011.03 ~ 2011.02 ~ 2011.01
2010: 2010.12 ~ 2010.11 ~ 2010.10 ~ 2010.09 ~ 2010.08 ~ 2010.07 ~ 2010.06 ~ 2010.05 ~ 2010.04 ~ 2010.03 ~ 2010.02 ~ 2010.01
2009: 2009.12 ~ 2009.11 ~ 2009.10 ~ 2009.09 ~ 2009.08 ~ 2009.07 ~ 2009.06 ~ 2009.05 ~ 2009.04 ~ 2009.03 ~ 2009.02 ~ 2009.01
2008: 2008.12 ~ 2008.11 ~ 2008.10 ~ 2008.09 ~ 2008.08 ~ 2008.07 ~ 2008.06 ~ 2008.05 ~ 2008.04 ~ 2008.03 ~ 2008.02 ~ 2008.01
2007: 2007.12 ~ 2007.11 ~ 2007.10 ~ 2007.09 ~ 2007.08 ~ 2007.07 ~ 2007.06 ~ 2007.05 ~ 2007.04 ~ 2007.03 ~ 2007.02 ~ 2007.01
Marliese's Corner ~ San Francisco Events
Michelle Aldrich: Cancer Free!
http://www.youtube.com/watch?v=9AZU-brG7i4&feature=player_embeddedMichelle is a member of the San Francisco Medical Cannabis Task Force. She is on the Advisory Board for Patients Out of Time and, along with her husband Michael, are recipients of the High Times Lifetime Achievement Award. They have been prominent activists in the San Francisco area for close to half a century. This interview was conducted in April of 2012 at the Seventh National Clinical Conference on Cannabis Therapeutics in Tucson, Arizona. The video of this interview can be viewed in its entirety on the Cannabis Therapeutics YouTube Channel, hosted by Patients out of Time.
My Oral Cancer Adventure ~ Surviving Oral Cancer ~ [Page in progress]
The Flower
http://www.youtube.com/watch?v=hMM_T_PJ0Rs&feature=player_embedded
Medical Marijuana helps Curtis undergoing oral cancer treatment.
Amestizo ~ BLOG + NEW: http://amestizo.bigcartel.com/
Shocking! The real purpose of your life! by Alan Watts
http://www.youtube.com/watch?feature=player_embedded&v=LwmbUzMViiU
Gomma TV ~ Punk TV Italy
Salvatore Iaconesi's: My Open Source [Cancer] Cure
Rome, December 2nd 2012: Everything goes really fine. I just had my latest Magnetic Resonance and the tumor seems to have completely stopped. I still have some time to fine-tune my strategy, and to continue it with energy and strength, preparing myself for surgery. ~ Salvatore
I have a brain cancer.
I converted my digital medical records into open, accessible formats, turning them into a very personal form of Open Data.
This data is available at http://www.artisopensource.net/cure
Artists, scientists, doctors, designers, hackers are all invited to send me their cure.
In different cultures the word CURE means different things, referring to the body, the soul or to society.
Send me your cure at: info@artisopensource.net and it will be published on the website, so that anyone (maybe someone with my same disease) will be able to benefit from it.
Nobody for President = NONE OF THE ABOVE should be on voter ballots
Wavy Gravy's 'Hippy Icon, Flower Geezer'
by Robert Hurwitt, January 17, 2013, Article Source
Wavy Gravy at Flying Snail Ranch, photograph by C. SpanglerWavy Gravy doesn't remember much about his walk around the block with Albert Einstein. Small wonder. He was only a 5-year-old named Hugh Romney at the time. But he says he can remember "a shock of white hair" and "twinkling eyes." And Einstein's particular smell.
"I haven't smelled anything like that ever since," Gravy told the audience at the Marsh Berkeley at the opening of his new show last Friday.
Then, his eyes twinkling within his own unruly shock of white hair and whiskers, he added that, 71 years later, he's still waiting for the moment a stray familiar whiff will make him blurt out to some startled stranger, "You smell just like Albert Einstein."
The great physicist is only the first of many celebrated names casually dropped or comically evoked in the course of Gravy's self-descriptively titled "Hippy Icon, Flower Geezer & Temple of Accumulated Error."
Dylan, Dietrich
Bob Dylan, Lenny Bruce, Bill Graham, Marlene Dietrich, Alice Cooper and Paul Krassner crop up, among others, sometimes in odd combinations - as in a memory of Tiny Tim and beatnik icon Neal Cassady crooning a Bing Crosby tune together.
Not that any of those people, or the anecdotes that touched on everything from Woodstock to San Francisco's seminal 1960s improv group the Committee, will necessarily grace future performances. "Hippy Icon," like "the activist clown and former frozen dessert" (a reference to his onetime celebrity as a Ben & Jerry's ice cream flavor) himself, is far from set in its ways.
As Marsh founder Stephanie Weisman explained, Gravy had such a good time performing a spur-of-the-moment holiday show, "Wavy Gravy and His Guided Mistletoes," at the Berkeley venue that he decided to return for several weeks of unstructured, seat-of-the pants reminiscences drawn from his eventful, wide-ranging life. Surprise guests may drop in at some shows, or, as on last Friday, not.
"Every night the show is a lot different," Weisman said. "A lot."
Each is a benefit
Each one is also a benefit for two of the humanitarian activist's longtime causes, his circus arts-based Camp Winnarainbow, and the Seva Foundation, co-founded by Gravy, Ram Dass and public health expert Larry Brilliant in 1978, which has done extensive work fighting diabetes and restoring eyesight from Tibet and Nepal to sub-Saharan Africa as well as working with American Indian health initiatives.
Gravy's Himalayan journey with Brilliant, which led to the founding of Seva - and, accidentally, the introduction of soap bubbles to Tibetan Buddhist services - was covered in one of the rambling tales. Winnarainbow was barely mentioned in passing.
Gravy began with some random anecdotes from childhood and his time as an acting student in New York, rooming with a coati, a raccoon-like Central American critter "with a long, erotic nose that goes around corners."
He faltered a bit, then warmed up by reading an odd tale about a "drool-encrusted" basset hound from his book "Something Good for a Change," which he seemed to find so infectiously funny that he soon had the audience laughing with him.
Lots of stories
The stories that followed ranged from his "teenage beatnik" coffeehouse-poet days in Boston, rooming with Dylan in Greenwich Village, decades of Hog Farm adventures from feeding the legions at Woodstock to a volcanic vat of cherry Jell-O on the Medicine Ball Caravan.
Chronology vanished in hazy shards of tales of Nepal, gigs with Tiny Tim and Manhattan street-poet icon Moondog, Nobody for President campaigns and comical protest arrests (as Santa Claus or the Easter Bunny) - and songs, accompanying his strangely soothing raspy voice on a one-stringed instrument he called an "iktar" ("Sanskrit," he later explained, "for one string").
"This was a good night," a tired Gravy said, after talking with well-wishers and selling copies of "Something Good," DVDs of "Saint Misbehavin' " (Michelle Estrick's Gravy documentary), clown noses and Winnarainbow posters after the show. "There was no thinking about it. It just flowed."
Hippy Icon, Flower Geezer & Temple of Accumulated Error: Stories by Wavy Gravy. Through Feb. 10. The Marsh Berkeley, 2120 Allston Way, Berkeley. $15-$50. (415) 282-3055. www.themarsh.org.
Robert Hurwitt is The San Francisco Chronicle's theater critic and All Links Located at Source, listed above.
Rainbow Puddle ~ Stellar Light Shows + Video Channel
Experimental Psychology In Layers
http://www.youtube.com/watch?feature=player_embedded&v=2MmkIMQrmwo
Freedom of expression and freedom of speech aren't really important unless they're heard...It's hard for me to stay silent when I keep hearing that peace is only attainable through war. And there's nothing more scary than watching ignorance in action. So I dedicated this Emmy to all the people who feel compelled to speak out and not afraid to speak to power and won't shut up and refuse to be silenced. ~ Tommy Smothers
Closing Argument
Drop Dead ~ Telecom Crimes ~ Patriot Act ~ Denialist ~ He Said It ~ Rethinking 9/11 ~ Are you better off?
Boston Legal Speech on America ~ http://www.youtube.com/embed/TwDAbVqQqv0?rel=0
Another Version ~ Please Click to View Video ~ http://vimeo.com/47165357One Can Lead A Horse To Water, But...
Until there is a solution for this, where one solution has been provided, Nobody will bring Peace to Our Times, feed the hungry, care for the sick, and bake apple pie better than Mom. (otoh) If None of the Above was on voter ballots, it would be a huge step towards recovering U.S. political control, and Nobody gets it.
George Carlin, The American Dream ~ http://vimeo.com/20452708
Oh, I hope that I see you again I never even caught your name As you looked through my window pane ~~ So I'm writing this message today I'm thinking that you'll have a way Of hearing the notes in my tune ~~ Where are you going? Where have you been? I can imagine other worlds you have seen ~~ Beautiful faces and music so serene ~~ So I do hope I see you again My universal citizen You went as quickly as you came ~~ You know the power Your love is right You have good reason To stay out of sight ~~ But break our illusions and help us Be the light ~ Listen ~ Message by Michael Pinder
Without love in the dream, it will never come true. ~ Jerry Garcia/Robert Hunter
The man whispered, "God, speak to me" and a meadowlark sang. But the man did not hear.
So the man yelled "God, speak to me" and the thunder rolled across the sky. But the man did not listen.
The man looked around and said, "God let me see you" and a star shined brightly. But the man did not notice.
And the man shouted, "God show me a miracle" and a life was born. But the man did not know.
So the man cried out in despair, "Touch me God, and let me know you are there"
Whereupon God reached down and touched the man. But the man brushed the butterfly away and walked on.

Don't miss out on a blessing because it isn't packaged the way you expect.



















