Tell-A-Vision = Why Not Try Love Again?
Last Day to Submit New eMail Address
eMail Block Gets Implemented Monday
![]()
Integrity ~ From Wikipedia, the free encyclopedia
Integrity is a concept of consistency of actions, values, methods, measures, principles, expectations, and outcomes. In ethics, integrity is regarded as the honesty and truthfulness or accuracy of one's actions. Integrity can be regarded as the opposite of hypocrisy, in that integrity regards internal consistency as a virtue, and suggests that parties holding apparently conflicting values should account for the discrepancy or alter their beliefs.
Hypocrisy ~ From Wikipedia, the free encyclopedia
Hypocrisy is the state of pretending to have virtues, moral or religious beliefs, principles, etc., that one does not actually have. Hypocrisy involves the deception of others and is thus a kind of lie.
Judas Iscariot ~ From Wikipedia, the free encyclopedia
Judas Iscariot is infamously known for his kiss and betrayal of Jesus to the hands of the chief Sanhedrin priests in exchange for a payment of thirty silver coins. His name [Judas] is often used to accuse someone [or a corporation] of betrayal.
As of June 21, 2013 eMail via Microsoft, Yahoo, Google, Facebook, AOL, AT&T, Verizon, and Apple goes into a 3 month holding tank. After June 30, 2013, eMail originating from any of those addresses will be outright rejected. Only personal eMail addresses will be accepted.
Give Peace a Chance
Wars happen when intolerance reaches epic proportions, when the reasons for war become greater than the sanctity of peace. Wars happen when we fail to realize the value of being alive. World leaders try to bring peace, but it is not an issue of institutions. It is human beings who start wars. Before a war begins outside, it starts inside.
The war on the inside is more dangerous because it is a fire that may never be put out. Wars are being fought because peace is not being found within, because it is not being allowed to unfold. We are all searching for something, we may call it success, peace, love, or tranquility. It is the same thing. What we are looking for has many names because we do not know what we need. To find what we need, we look around us. To know where to find what we are looking for, we first need to ask ourselves where we can find it. Have we considered looking within?
Living is not an easy task, especially if we want the best of it. We have to mine for it. Mining is not easy. We have to take out what we need and leave the rest. If we want to mine for peace, then we have to seek what is precious and discard what is not. The thing that we are searching for is not outside of us. It is within us. It always has been and always will be. Contentment feels good, and it is not an accident. It is not an accident that peace feels good. Peace is already here, and it resides in the hearts of all human beings.
Peace is something that has to be felt. One of the most incredible powers we have is that we can feel. When we place peace in front of that power to feel, we feel peace. We are here to be filled with gratitude, love and understanding. We carry a lamp within so bright that even in the darkest night, it can fill our world with light. This light is waiting to be found. Peace makes no distinctions. It does not care if we are rich, if we are poor, or what religion we belong to. It does not care which country we live in.
Peace is waiting to be found. Waiting to once again feel whole, not separated by all the issues that divide our lives. Peace is when the heart is no longer in duality, when the struggle within has been resolved. When peace comes to the heart, serenity follows. Love comes flooding in, uncontrolled. Joy cannot be held back. It bursts through because it is right. That is peace. Peace needs to be felt, love needs to be felt, truth needs to be felt. As long as we are alive, the yearning to feel good, to feel joy, will always be there, and as long as it is there, there will be a need for it to be discovered.
Life is a journey. We are passengers in a train called life, and we are alive in the moment called now. The journey of life is so beautiful that it needs no destination. On this journey, we have been given a compass. The compass is the thirst to be fulfilled. The true journey of life begins the day we begin to seek to quench our thirst. This quest is the most noble one. For many centuries, a voice has been calling out: "What you are looking for is within you. Your truth is within you, your peace is within you, your joy is within you." In our hearts, peace is like a seed waiting in the desert to grow, to blossom. When we allow this seed to blossom inside, then peace is possible outside. We have to give peace a chance.
Will we give peace a chance? ~ Prem Rawat - India Times 2/25/2000 - Local Source
Keith Lampe ~ Co-Founder of YIPPIE and Progressive Activist Groups + Video Channel
California man faces 13 years in jail
for scribbling anti-bank messages in chalkPublished time: June 26, 2013 04:07 ~ http://rt.com/usa/california-man-13-prison-banks-237/
Jeff Olson, the 40-year-old man who is being prosecuted for scrawling anti-megabank messages on sidewalks in water-soluble chalk last year now faces a 13-year jail sentence. A judge has barred his attorney from mentioning freedom of speech during trial.
According to the San Diego Reader, which reported on Tuesday that a judge had opted to prevent Olson’s attorney from "mentioning the First Amendment, free speech, free expression, public forum, expressive conduct, or political speech during the trial,” Olson must now stand trial for on 13 counts of vandalism.
In addition to possibly spending years in jail, Olson will also be held liable for fines of up to $13,000 over the anti-big-bank slogans that were left using washable children's chalk on a sidewalk outside of three San Diego, California branches of Bank of America, the massive conglomerate that received $45 billion in interest-free loans from the US government in 2008-2009 in a bid to keep it solvent after bad bets went south.
The Reader reports that Olson’s hearing had gone as poorly as his attorney might have expected, with Judge Howard Shore, who is presiding over the case, granting Deputy City Attorney Paige Hazard's motion to prohibit attorney Tom Tosdal from mentioning the United States' fundamental First Amendment rights.
"The State's Vandalism Statute does not mention First Amendment rights," ruled Judge Shore on Tuesday.
Upon exiting the courtroom Olson seemed to be in disbelief.
"Oh my gosh," he said. "I can't believe this is happening."
Tosdal, who exited the courtroom shortly after his client, seemed equally bewildered.
"I've never heard that before, that a court can prohibit an argument of First Amendment rights," said Tosdal.
Olson, who worked as a former staffer for a US Senator from Washington state, was said to involve himself in political activism in tandem with the growth of the Occupy Wall Street movement.
On October 3, 2011, Olson first appeared outside of a Bank of America branch in San Diego, along with a homemade sign. Eight days later Olson and his partner, Stephen Daniels, during preparations for National Bank Transfer Day, the two were confronted by Darell Freeman, the Vice President of Bank of America’s Global Corporate Security.
A former police officer, Freeman accused Olson and Daniels of “running a business outside of the bank,” evidently in reference to the National Bank Transfer Day activities, which was a consumer activism initiative that sought to promote Americans to switch from commercial banks, like Bank of America, to not-for-profit credit unions.
At the time, Bank of America’s debit card fees were among one of the triggers that led Occupy Wall Street members to promote the transfer day.
"It was just an empty threat," says Olson of Freeman’s accusations. "He was trying to scare me away. To be honest, it did at first. I even called my bank and they said he couldn't do anything like that."
Olson continued to protest outside of Bank of America. In February 2012, he came across a box of chalk at a local pharmacy and decided to begin leaving his mark with written statements.
"I thought it was a perfect way to get my message out there. Much better than handing out leaflets or holding a sign," says Olson.
Over the course of the next six months Olson visited the Bank of America branch a few days per week, leaving behind scribbled slogans such as "Stop big banks" and "Stop Bank Blight.com."
According to Olson, who spoke with local broadcaster KGTV, one Bank of America branch claimed it had cost $6,000 to clean up the chalk writing.
Public records obtained by the Reader show that Freeman continued to pressure members of San Diego’s Gang Unit on behalf of Bank of America until the matter was forwarded to the City Attorney’s office.
On April 15, Deputy City Attorney Paige Hazard contacted Freeman with a response on his persistent queries.
"I wanted to let you know that we will be filing 13 counts of vandalism as a result of the incidents you reported," said Hazard.
Arguments for Olson’s case are set to be heard Wednesday morning, following jury selection.
The personal side of taking on the NSA: emerging smears
Distractions about my past and personal life have emerged – an inevitable side effect for those who challenge the US government
Glenn Greenwald, guardian.co.uk, Wednesday 26 June 2013 16.21 EDT, Article Source
Glenn Greenwald on Security and LibertyWhen I made the choice to report aggressively on top-secret NSA programs, I knew that I would inevitably be the target of all sorts of personal attacks and smears. You don't challenge the most powerful state on earth and expect to do so without being attacked. As a superb Guardian editorial noted today: "Those who leak official information will often be denounced, prosecuted or smeared. The more serious the leak, the fiercer the pursuit and the greater the punishment."
One of the greatest honors I've had in my years of writing about politics is the opportunity to work with and befriend my long-time political hero, Daniel Ellsberg. I never quite understood why the Nixon administration, in response to his release of the Pentagon Papers, would want to break into the office of Ellsberg's psychoanalyst and steal his files. That always seemed like a non sequitur to me: how would disclosing Ellsberg's most private thoughts and psychosexual assessments discredit the revelations of the Pentagon Papers?
When I asked Ellsberg about that several years ago, he explained that the state uses those tactics against anyone who dissents from or challenges it simply to distract from the revelations and personally smear the person with whatever they can find to make people uncomfortable with the disclosures.
So I've been fully expecting those kinds of attacks since I began my work on these NSA leaks. The recent journalist-led "debate" about whether I should be prosecuted for my reporting on these stories was precisely the sort of thing I knew was coming.
As a result, I was not particularly surprised when I received an email last night from a reporter at the New York Daily News informing me that he had been "reviewing some old lawsuits" in which I was involved – "old" as in: more than a decade ago – and that "the paper wants to do a story on this for tomorrow". He asked that I call him right away to discuss this, apologizing for the very small window he gave me to comment.
Upon calling him, I learned that he had somehow discovered two events from my past. The first was my 2002-04 participation in a multi-member LLC that had an interest in numerous businesses, including the distribution of adult videos. I was bought out of that company by my partners roughly nine years ago.
The lawsuit he referenced was one where the LLC had sued a video producer in (I believe) 2002 after the producer reneged on a profit-sharing contract. In response, that producer fabricated abusive and ugly emails he claimed were from me – they were not – in order to support his allegation that I had bullied him into entering into that contract and he should therefore be relieved from adhering to it. Once our company threatened to retain a forensic expert to prove that the emails were forgeries, the producer quickly settled the case by paying some substantial portion of what was owed, and granting the LLC the rights to use whatever it had obtained when consulting with him to start its own competing business.
The second item the reporter had somehow obtained was one showing an unpaid liability to the IRS stemming, it appears, from some of the last years of my law practice. I've always filed all of my tax returns and there's no issue of tax evasion or fraud. It's just back taxes for which my lawyers have been working to reach a payment agreement with the IRS.
Just today, a New York Times reporter emailed me to ask about the IRS back payments. And the reporter from the Daily News sent another email asking about a student loan judgment which was in default over a decade ago and is now covered by a payment plan agreement.
So that's the big discovery: a corporate interest in adult videos (something the LLC shared with almost every hotel chain), fabricated emails, and some back taxes and other debt.
I'm 46 years old and, like most people, have lived a complicated and varied adult life. I didn't manage my life from the age of 18 onward with the intention of being a Family Values US senator. My personal life, like pretty much everyone's, is complex and sometimes messy.
If journalists really believe that, in response to the reporting I'm doing, these distractions about my past and personal life are a productive way to spend their time, then so be it.
None of that – or anything else – will detain me even for an instant in continuing to report on what the NSA is doing in the dark.
On the Voting Rights Act,
the colour-blind have been led by the blindThe supreme court thinks racism no longer exists at the polls. The actions of Republican legislators prove otherwise
Gary Younge, guardian.co.uk, Tuesday 25 June 2013 16.15 EDT, Article Source
Supporters of the Voting Rights Act listen to speakers outside the supreme court. Photograph: Win Mcnamee/Getty ImagesOne of the greatest cheers at an otherwise lacklustre Republican convention in Tampa last year was for Condoleeza [War Criminal and Initiator of Torture] Rice, who gave a glowing autobiographical account of her achievements in the third person. "A little girl grows up in Jim Crow Birmingham," she said, "the segregated city of the south where her parents cannot take her to a movie theater or to restaurants, but they have convinced her that even if she cannot have a hamburger at Woolworths, she can be the president of the United States if she wanted to be, and she becomes the secretary of state."
All mention of what it took to make such a life possible is an inconvenience. The children who were jailed, set upon by dogs and drenched by fire hoses in her home town, so that integration could become a reality, are irrelevant. The people who were killed because they registered to vote, marched against humiliation or just wouldn't shut up when they were told to – so that a black female secretary of state was even plausible, let alone possible – do not fit. Condi made it because she worked hard. Maybe her kindergarten friend, Denise McNair, would have made it too. We'll never know because she was bombed to death by those opposing integration while studying at Sunday school. Segregation was fickle that way.
At times it seemed that the only thing more attractive to Republicans than watching a nonwhite person describe how he or she had overcome huge obstacles to reach the top was coming up with new obstacles to gleefully throw in front of the next generation. Tuesday's supreme court ruling, freeing states from special federal oversight under the Voting Rights Act of 1965, marks yet another attempt by American conservatives to posit racism not only as a discreet phenomenon of the past but one which has no discernible legacy. "There is an old disease, and that disease is cured," argued Bert Rein, when opposing the act before the supreme court earlier this year. "That problem," claimed Rein, "is solved." Well that's a relief. Racism is over. Let's all move on. Nothing to see here.
This white flight from history is not new for the Right. Those who oppose affirmative action, for example, cite Barack Obama as a reason for why it is no longer necessary – even though he was a beneficiary of it. "Obama embodies and preaches the true and vital message that in today's America, the opportunities available to black people are unlimited if they work hard, play by the rules, and get a good education," wrote Stuart Taylor Jr in the National Journal in 2008. They also quote Martin Luther King, even though he was an advocate of it.
If the problem Rein identified is codified segregation at the polls, enabled by the laws and officials that specifically and explicitly bar black people from voting, then of course he is right. But there was always more to racism than segregation and always more to equality than integration. "The issue for black people was never integration or segregation, but white supremacy. The paradigm of integration and segregation was a white concern," said Charles Payne, the Frank P Hixon Distinguished Service Professor at the University of Chicago. "That was how they posed the issue of civil rights given their own interests, and that was how the entire issue then became understood. But the central concerns of black people were not whether they should integrate with white people or not, but how to challenge white people's hold on the power structure."
All Rein really showed is that racism is now more subtle, not that it has disappeared. They have taken down the offensive signs but continued the offensive practice. From the outset of the post-civil rights era that was always the strategy. "You start out in 1954 by saying, 'Nigger, nigger, nigger'," explained the late Lee Atwater, the one-time chair of the Republican National Committee and member of the Reagan administration, in 1981.
By 1968 you can't say 'nigger' – that hurts you. Backfires. So you say stuff like forced busing [and] states' rights … You're getting so abstract now [that] you're talking about cutting taxes, and all these things you're talking about are totally economic things and a byproduct of them is [that] blacks get hurt worse than whites … obviously sitting around saying, 'We want to cut this' is much more abstract than even the busing thing, and a hell of a lot more abstract than 'nigger, nigger'.
Now here we are, with Republicans routinely pursuing voter ID laws addressing a problem that does not really exist (voter fraud) while actually practicing a method of exclusion they claim is extinct (discrimination at the polls). Examples of voter-rights violations are legion; the prospects for challenging them will now be more limited. What the supreme court has signalled is that after 60 years of legal support, the American judiciary is willing to draw a line under more than 350 years of racism and its legacy. Their colour-blind approach does not mean that racism will cease to exist at the polls. Only that they will cease to see it.
Dirty Wars author Jeremy Scahill:
is journalism being criminalised?In the wake of whistleblower Edward Snowden's leak of NSA files, Jeremy Scahill, author of Dirty Wars: The World is a Battlefield and featured reporter in the new documentary film of the same name, says under the Obama administration journalists are being intruded upon and whistleblowers are being charged with crimes. Scahill is also a national security correspondent for the Nation

Click to View "THE NSA FILES" Located at The Guardian (UK)
NAUSEA director: George W. Bush, Dick Cheney,
& Politicians have caused irreversible damage to USMickey Moose defends spying on Joe Plumber as being in line with Zionist expectations for Neocons creating another 9/11
NAUSEA director Mickey Moose said on Sunday that George W. Bush, Dick Cheney, Republicans, and Democrats betrayed the trust of Americans and defended the broad surveillance programs as necessary to encourage more congressional Bi-partisanship unity:
Bi-Partisan Unityand allow for political perverts to continue sodomizing children.
As Bush and Cheney evaded an attempt by "The People" to citizen's arrest them, General Corpo Mills said: "These are individuals not acting, in my opinion, with noble intent ... What Bush, Cheney, and their Administration has done or revealed caused irreversible and significant damage to our country and to our allies."
Corpo Mills said the NAUSEA surveillance programs installed by Bush and Cheney were tightly overseen and disputed statements from members of the Senate intelligence committee; with exception to Dianne 'War Profiteer' Feinstein, they were illegally spying on US citizens and that spying played no role in preventing any future terrorist attacks.
Larry Silverstein's Magic WTC Building 7
that was never hit with anything and collapsed like building demolition ???Corpo read from a 2012 O'Bummer intelligence committee report about a law that broadened NAUSEA's authority to perform surveillance ... even when US communications are involved that said after "four years of oversight, the committee has not identified a single case in which a government official engaged in wilful effort to circumvent or violate the law".
Yet last year, the Office of the Director of Pair-O-Ducks National Intelligence conceded publicly that the surveillance had violated the fourth amendment on at least one occasion. The circumstances behind that violation remain classified. [Click to Read the Real Story]
Where Have All the Flowers Gone?
Reflections on the Spirit and Legacy of the Sixties
by Fritjof Capra ~ December 1, 2002 ~ Local SourceThe 1960s were the period of my life during which I experienced the most profound and most radical personal transformation. For those of us who identify with the cultural and political movements of the sixties, that period represents not so much a decade as a state of consciousness, characterized by "transpersonal" expansion, the questioning of authority, a sense of empowerment, and the experience of sensuous beauty and community.
This state of consciousness reached well into the seventies. In fact, one could say that the sixties came to an end only in December 1980, with the shot that killed John Lennon. The immense sense of loss felt by so many of us was, to a great extent, about the loss of an era. For a few days after the fatal shooting we relived the magic of the sixties. We did so in sadness and with tears, but the same feeling of enchantment and of community was once again alive. Wherever you went during those few days - in every neighborhood, every city, every country around the world - you heard John Lennon's music, and the intense idealism that had carried us through the sixties manifested itself once again:
In this essay, I shall try to evoke the spirit of that remarkable period, identify its defining characteristics, and provide an answer to some questions that are often asked nowadays: What happened to the cultural movements of the sixties? What did they achieve, and what, if any, is their legacy?
expansion of consciousness
The era of the sixties was dominated by an expansion of consciousness in two directions. One movement, in reaction to the increasing materialism and secularism of Western society, embraced a new kind of spirituality akin to the mystical traditions of the East. This involved an expansion of consciousness toward experiences involving nonordinary modes of awareness, which are traditionally achieved through meditation but may also occur in various other contexts, and which psychologists at the time began to call "transpersonal." Psychedelic drugs played a significant role in that movement, as did the human potential movement's promotion of expanded sensory awareness, expressed in its exhortation, "Get out of your head and into your senses!"
The first expansion of consciousness, then, was a movement beyond materialism and toward a new spirituality, beyond ordinary reality via meditative and psychedelic experiences, and beyond rationality through expanded sensory awareness. The combined effect was a continual sense of magic, awe, and wonder that for many of us will forever be associated with the sixties.
questioning of authority
The other movement was an expansion of social consciousness, triggered by a radical questioning of authority. This happened independently in several areas. While the American civil rights movement demanded that Black citizens be included in the political process, the free speech movement at Berkeley and student movements at other universities throughout the United States and Europe demanded the same for students.
In Europe, these movements culminated in the memorable revolt of French university students that is still known simply as "May '68." During that time, all research and teaching activities came to a complete halt at most French universities when the students, led by Daniel Cohn-Bendit, extended their critique to society as a whole and sought the solidarity of the French labor movement to change the entire social order. For three weeks, the administrations of Paris and other French cities, public transport, and businesses of every kind were paralyzed by a general strike. In Paris, people spent most of their time discussing politics in the streets, while the students held strategic discussions at the Sorbonne and other universities. In addition, they occupied the Odéon, the spacious theater of the Comédie Française, and transformed it into a twenty-four-hour "people's parliament," where they discussed their stimulating, albeit highly idealistic, visions of a future social order.
1968 was also the year of the celebrated "Prague Spring," during which Czech citizens, led by Alexander Dubcek, questioned the authority of the Soviet regime, which alarmed the Soviet Communist party to such an extent that, a few months later, it crushed the democratization processes initiated in Prague in its brutal invasion of Czechoslovakia.
In the United States, opposition to the Vietnam war became a political rallying point for the student movement and the counterculture. It sparked a huge anti-war movement, which exerted a major influence on the American political scene and led to many memorable events, including the decision by President Johnson not to seek reelection, the turbulent 1968 Democratic Convention in Chicago, the Watergate scandal, and the resignation of President Nixon.
a new sense of community
While the civil rights movement questioned the authority of white society and the student movements questioned the authority of their universities on political issues, the women's movement began to question patriarchal authority; humanistic psychologists undermined the authority of doctors and therapists; and the sexual revolution, triggered by the availability of birth control pills, broke down the puritan attitudes toward sexuality that were typical of American culture.
The radical questioning of authority and the expansion of social and transpersonal consciousness gave rise to a whole new culture - a "counterculture" - that defined itself in opposition to the dominant "straight" culture by embracing a different set of values. The members of this alternative culture, who were called "hippies" by outsiders but rarely used that term themselves, were held together by a strong sense of community. To distinguish ourselves from the crew cuts and polyester suits of that era's business executives, we wore long hair, colorful and individualistic clothes, flowers, beads, and other jewelry. Many of us were vegetarians who often baked our own bread, practiced yoga or some other form of meditation, and learned to work with our hands in various crafts.
Our subculture was immediately identifiable and tightly bound together. It had its own rituals, music, poetry, and literature; a common fascination with spirituality and the occult; and the shared vision of a peaceful and beautiful society. Rock music and psychedelic drugs were powerful bonds that strongly influenced the art and lifestyle of the hippie culture. In addition, the closeness, peacefulness, and trust of the hippie communities were expressed in casual communal nudity and freely shared sexuality. In our homes we would frequently burn incense and keep little altars with eclectic collections of statues of Indian gods and goddesses, meditating Buddhas, yarrow stalks or coins for consulting the I Ching, and various personal "sacred" objects.
Although different branches of the sixties movement arose independently and often remained distinct movements with little overlap for several years, they eventually became aware of one another, expressed mutual solidarity, and, during the 1970s, merged more or less into a single subculture. By that time, psychedelic drugs, rock music, and the hippie fashion had transcended national boundaries and had forged strong ties among the international counterculture. Multinational hippie tribes gathered in several countercultural centers - London, Amsterdam, San Francisco, Greenwich Village - as well as in more remote and exotic cities like Marrakech and Katmandu. These frequent cross-cultural exchanges gave rise to an "alternative global awareness" long before the onset of economic globalization.
the sixties' music
The zeitgeist of the sixties found expression in many art forms that often involved radical innovations, absorbed various facets of the counterculture, and strengthened the multiple relationships among the international alternative community.
Rock music was the strongest among these artistic bonds. The Beatles broke down the authority of studios and songwriters by writing their own music and lyrics, creating new musical genres, and setting up their own production company. While doing so, they incorporated many facets of the period's characteristic expansion of consciousness into their songs and lifestyles.
Bob Dylan expressed the spirit of the political protests in powerful poetry and music that became anthems of the sixties. The Rolling Stones represented the counterculture's irreverence, exuberance, and sexual energy, while San Francisco's "acid rock" scene gave expression to its psychedelic experiences.
At the same time, the "free jazz" of John Coltrane, Ornette Coleman, Sun Ra, Archie Shepp, and others shattered conventional forms of jazz improvisation and gave expression to spirituality, radical political poetry, street theater, and other elements of the counterculture. Like the jazz musicians, classical composers, such as Karlheinz Stockhausen in Germany and John Cage in the United States, broke down conventional musical forms and incorporated much of the sixties' spontaneity and expanded awareness into their music.
The fascination of the hippies with Indian religious philosophies, art, and culture led to a great popularity of Indian music. Most record collections in those days contained albums of Ravi Shankar, Ali Akbar Khan, and other masters of classical Indian music along with rock and folk music, jazz and blues.
The rock and drug culture of the sixties found its visual expressions in the psychedelic posters of the era's legendary rock concerts, especially in San Francisco, and in album covers of ever increasing sophistication, which became lasting icons of the sixties' subculture. Many rock concerts also featured "light shows" - a novel form of psychedelic art in which images of multicolored, pulsating, and ever changing shapes were projected onto walls and ceilings. Together with the loud rock music, these visual images created highly effective simulations of psychedelic experiences.
new literary forms
The main expressions of sixties' poetry were in the lyrics of rock and folk music. In addition, the "beat poetry" of Allen Ginsberg, Lawrence Ferlinghetti, Gary Snyder, and others, which had originated a decade earlier and shared many characteristics with the sixties' art forms, remained popular in the counterculture.
One of the major new literary forms was the "magical realism" of Latin American literature. In their short stories and novels, writers like Jorges Luis Borges and Gabriel García Márquez blended descriptions of realistic scenes with fantastic and dreamlike elements, metaphysical allegories, and mythical images. This was a perfect genre for the counterculture's fascination with altered states of consciousness and pervasive sense of magic.
In addition to the Latin American magical realism, science fiction, especially the complex series of Dune novels by Frank Herbert, exerted great fascination on the sixties' youth, as did the fantasy writings of J. R. R. Tolkien and Kurt Vonnegut. Many of us also turned to literary works of the past, such as the romantic novels of Hermann Hesse, in which we saw reflections of our own experiences.
Of equal, if not greater, popularity were the semi-fictional shamanistic writings of Carlos Castaneda, which satisfied the hippies' yearning for spirituality and "separate realities" mediated by psychedelic drugs. In addition, the dramatic encounters between Carlos and the Yaqui sorcerer Don Juan symbolized in a powerful way the clashes between the rational approach of modern industrial societies and the wisdom of traditional cultures.
film and the performing arts
In the sixties, the performing arts experienced radical innovations that broke every imaginable tradition of theater and dance. In fact, in companies like the Living Theater, the Judson Dance Theater, and the San Francisco Mime Troupe, theater and dance were often fused and combined with other forms of art. The performances involved trained actors and dancers as well as visual artists, musicians, poets, filmmakers, and even members of the audience.
Men and women often enjoyed equal status; nudity was frequent. Performances, often with strong political content, took place not only in theaters but also in museums, churches, parks, and in the streets. All these elements combined to create the dramatic expansion of experience and strong sense of community that was typical of the counterculture.
Film, too, was an important medium for expressing the zeitgeist of the sixties. Like the performing artists, the sixties' filmmakers, beginning with the pioneers of the French New Wave cinema, broke with the traditional techniques of their art, introducing multi-media approaches, often abandoning narratives altogether, and using their films to give a powerful voice to social critique.
With their innovative styles, these filmmakers expressed many key characteristics of the counterculture. For example, we can find the sixties' irreverence and political protest in the films of Godard; the questioning of materialism and a pervasive sense of alienation in Antonioni; questioning of the social order and transcendence of ordinary reality in Fellini; the exposure of class hypocrisy in Buñuel; social critique and utopian visions in Kubrik; the breaking down of sexual and gender stereotypes in Warhol; and the portrayal of altered states of consciousness in the works of experimental filmmakers like Kenneth Anger and John Whitney. In addition, the films of these directors are characterized by a strong sense of magical realism.
the legacy of the sixties
Many of the cultural expressions that were radical and subversive in the sixties have been accepted by broad segments of mainstream culture during the subsequent three decades. Examples would be the long hair and sixties fashion, the practice of Eastern forms of meditation and spirituality, recreational use of marijuana, increased sexual freedom, rejection of sexual and gender stereotypes, and the use of rock (and more recently rap) music to express alternative cultural values. All of these were once expressions of the counterculture that were ridiculed, suppressed, and even persecuted by the dominant mainstream society.
Beyond these contemporary expressions of values and esthetics that were shared by the sixties' counterculture, the most important and enduring legacy of that era has been the creation and subsequent flourishing of a global alternative culture that shares a set of core values. Although many of these values - e.g. environmentalism, feminism, gay rights, global justice - were shaped by cultural movements in the seventies, eighties, and nineties, their essential core was first expressed by the sixties' counterculture. In addition, many of today's senior progressive political activists, writers, and community leaders trace the roots of their original inspiration back to the sixties.
Green politics
In the sixties we questioned the dominant society and lived according to different values, but we did not formulate our critique in a coherent, systematic way. We did have concrete criticisms on single issues, such as the Vietnam war, but we did not develop any comprehensive alternative system of values and ideas. Our critique was based on intuitive feeling; we lived and embodied our protest rather than verbalizing and systematizing it.
The seventies brought consolidation of our views. As the magic of the sixties gradually faded, the initial excitement gave way to a period of focusing, digesting, and integrating. Two new cultural movements, the ecology movement and the feminist movement, emerged during the seventies and together provided the much-needed broad framework for our critique and alternative ideas.
The European student movement, which was largely Marxist oriented, was not able to turn its idealistic visions into realities during the sixties. But it kept its social concerns alive during the subsequent decade, while many of its members went through profound personal transformations. Influenced by the two major political themes of the seventies, feminism and ecology, these members of the "new left" broadened their horizons without losing their social consciousness. At the end of the decade, many of them became the leaders of transformed socialist parties. In Germany, these "young socialists" formed coalitions with ecologists, feminists, and peace activists, out of which emerged the Green Party - a new political party whose members confidently declared: "We are neither left nor right; we are in front."
During the 1980s and 1990s, the Green movement became a permanent feature of the European political landscape, and Greens now hold seats in numerous national and regional parliaments around the world. They are the political embodiment of the core values of the sixties.
the end of the Cold War
During the 1970s and 1980s, the American anti-war movement expanded into the anti-nuclear and peace movements, in solidarity with corresponding movements in Europe, especially those in the UK and West Germany. This, in turn, sparked a powerful peace movement in East Germany, led by the Protestant churches, which maintained regular contacts with the West German peace movement, and in particular with Petra Kelly, the charismatic leader of the German Greens.
When Mikhail Gorbachev came to power in the Soviet Union in 1985, he was well aware of the strength of the Western peace movement and accepted our argument that a nuclear war cannot be won and should never be fought. This realization played an important part in Gorbachev's "new thinking" and his restructuring (perestroika) of the Soviet regime, which would lead, eventually, to the fall of the Berlin Wall, the Velvet Revolution in Czechoslovakia, and the end of Soviet Communism.
All social and political systems are highly nonlinear and do not lend themselves to being analyzed in terms of linear chains of cause and effect. Nevertheless, careful study of our recent history shows that the key ingredient in creating the climate that led to the end of the Cold War was not the hard-line strategy of the Reagan administration, as the conservative mythology would have it, but the international peace movement. This movement clearly had its political and cultural roots in the student movements and counterculture of the sixties.
the information technology revolution
The last decade of the twentieth century brought a global phenomenon that took most cultural observers by surprise. A new world emerged, shaped by new technologies, new social structures, a new economy, and a new culture. "Globalization" became the term used to summarize the extraordinary changes and the seemingly irresistible momentum that were now felt by millions of people.
A common characteristic of the multiple aspects of globalization is a global information and communications network based on revolutionary new technologies. The information technology revolution is the result of a complex dynamic of technological and human interactions, which produced synergistic effects in three major areas of electronics - computers, microelectronics, and telecommunications. The key innovations that created the radically new electronic environment of the 1990s all took place 20 years earlier, during the 1970s.
It may be surprising to many that, like so many other recent cultural movements, the information technology revolution has important roots in the sixties' counterculture. It was triggered by a dramatic technological development - a shift from data storage and processing in large, isolated machines to the interactive use of microcomputers and the sharing of computer power in electronic networks. This shift was spearheaded by young technology enthusiasts who embraced many aspects of the counterculture, which was still very much alive at that time.
The first commercially successful microcomputer was built in 1976 by two college dropouts, Steve Wosniak and Steve Jobs, in their now legendary garage in Silicon Valley. These young innovators and others like them brought the irreverent attitudes, freewheeling lifestyles, and strong sense of community they had adopted in the counterculture to their working environments. In doing so, they created the relatively informal, open, decentralized, and cooperative working styles that became characteristic of the new information technologies.
global capitalism
However, the ideals of the young technology pioneers of the seventies were not reflected in the new global economy that emerged from the information technology revolution 20 years later. On the contrary, what emerged was a new materialism, excessive corporate greed, and a dramatic rise of unethical behavior among our corporate and political leaders. These harmful and destructive attitudes are direct consequences of a new form of global capitalism, structured largely around electronic networks of financial and informational flows. The so-called "global market" is a network of machines programmed according to the fundamental principle that money-making should take precedence over human rights, democracy, environmental protection, or any other value.
Since the new economy is organized according to this quintessential capitalist principle, it is not surprising that it has produced a multitude of interconnected harmful consequences that are in sharp contradiction to the ideals of the global Green movement: rising social inequality and social exclusion, a breakdown of democracy, more rapid and extensive deterioration of the natural environment, and increasing poverty and alienation. The new global capitalism has threatened and destroyed local communities around the world; and with the pursuit of an ill-conceived biotechnology, it has invaded the sanctity of life by attempting to turn diversity into monoculture, ecology into engineering, and life itself into a commodity.
It has become increasingly clear that global capitalism in its present form is unsustainable and needs to be fundamentally redesigned. Indeed, scholars, community leaders, and grassroots activists around the world are now raising their voices, demanding that we must "change the game" and suggesting concrete ways of doing so.
the global civil society
At the turn of this century, an impressive global coalition of nongovernmental organizations (NGOs), many of them led by men and women with deep personal roots in the sixties, formed around the core values of human dignity and ecological sustainability. In 1999, hundreds of these grassroots organizations interlinked electronically for several months to prepare for joint protest actions at the meeting of the World Trade Organization (WTO) in Seattle. The "Seattle Coalition," as it is now called, was extremely successful in derailing the WTO meeting and in making its views known to the world. Its concerted actions have permanently changed the political climate around the issue of economic globalization.
Since that time, the Seattle Coalition, or "global justice movement," has not only organized further protests but has also held several World Social Forum meetings in Porto Alegre, Brazil. At the second of these meetings, the NGOs proposed a whole set of alternative trade policies, including concrete and radical proposals for restructuring global financial institutions, which would profoundly change the nature of globalization.
The global justice movement exemplifies a new kind of political movement that is typical of our Information Age. Because of their skillful use of the Internet, the NGOs in the coalition are able to network with each other, share information, and mobilize their members with unprecedented speed. As a result, the new global NGOs have emerged as effective political actors who are independent of traditional national or international institutions. They constitute a new kind of global civil society.
This new form of alternative global community, sharing core values and making extensive use of electronic networks in addition to frequent human contacts, is one of the most important legacies of the sixties. If it succeeds in reshaping economic globalization so as to make it compatible with the values of human dignity and ecological sustainability, the dreams of the "sixties revolution" will have been realized:
Apathy Sucks
Warrantless surveillance is carefully targeted to include only international calls and e-mails into or out of the USA, and only those involving at least one party suspected of being a member or ally of al-Qaeda or a related terror group. ~ said George W Bush and his GOP handlers, repeatedly, to US Voters ... after they were caught spying on peaceful Quakers and people handing out free peanut-butter and jelly sandwiches.
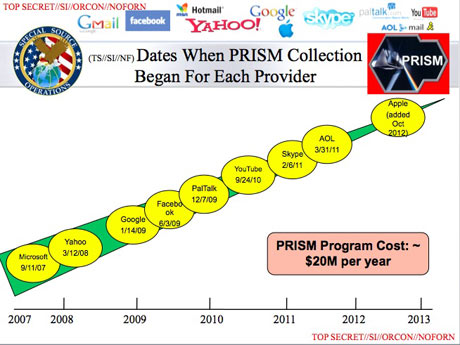
PRISM scandal: tech giants flatly deny
allowing NSA direct access to serversSilicon Valley executives insist they did not know of secret PRISM program that grants access to emails and search history
Dominic Rushe and James Ball in New York, guardian.co.uk, Thursday 6 June 2013 19.48 EDT, Article Source
Executives at several of the tech firms said they had never heard of PRISM
until they were contacted by the GuardianTwo different versions of the PRISM scandal were emerging on Thursday with Silicon Valley executives denying all knowledge of the top secret program that gives the National Security Agency direct access to the internet giants' servers.
The eavesdropping program is detailed in the form of PowerPoint slides in a leaked NSA document, seen and authenticated by the Guardian, which states that it is based on "legally-compelled collection" but operates with the "assistance of communications providers in the US."
Each of the 41 slides in the document displays prominently the corporate logos of the tech companies claimed to be taking part in PRISM.
However, senior executives from the internet companies expressed surprise and shock and insisted that no direct access to servers had been offered to any government agency.
The top-secret NSA briefing presentation set out details of the PRISM program, which it said granted access to records such as emails, chat conversations, voice calls, documents and more. The presentation the listed dates when document collection began for each company, and said PRISM enabled "direct access from the servers of these US service providers: Microsoft, Yahoo, Google, Facebook, Paltalk, AOL, Skype, YouTube, Apple".
Senior officials with knowledge of the situation within the tech giants admitted to being confused by the NSA revelations, and said if such data collection was taking place, it was without companies' knowledge.
An Apple spokesman said: "We have never heard of PRISM. We do not provide any government agency with direct access to our servers and any agency requesting customer data must get a court order," he said.
Joe Sullivan, Facebook's chief security officer, said it did not provide government organisation with direct access to Facebook servers. "When Facebook is asked for data or information about specific individuals, we carefully scrutinise any such request for compliance with all applicable laws, and provide information only to the extent required by law."
A Google spokesman also said it did not provide officials with access to its servers. "Google cares deeply about the security of our users' data. We disclose user data to government in accordance with the law, and we review all such requests carefully. From time to time, people allege that we have created a government 'backdoor' into our systems, but Google does not have a 'back door' for the government to access private user data."
Microsoft said it only turned over data when served with a court order: "We provide customer data only when we receive a legally binding order or subpoena to do so, and never on a voluntary basis. In addition we only ever comply with orders for requests about specific accounts or identifiers. If the government has a broader voluntary national security program to gather customer data we don't participate in it."
A Yahoo spokesman said: "Yahoo! takes users' privacy very seriously. We do not provide the government with direct access to our servers, systems, or network.
Within the tech companies, and talking on off the record, executives said they had never even heard of PRISM until contacted by the Guardian. Executives said that they were regularly contacted by law officials and responded to all subpoenas but they denied ever having heard of a scheme like PRISM, an information programme internal the documents state has been running since 2007.
Executives said they were "confused" by the claims in the NSA document. "We operate under what we are required to do by law," said one. "We receive requests for information all the time. Say about a potential terrorist threat or after the Boston bombing. But we have systems in place for that." The executive claimed, as did others, that the most senior figures in their organisation had never heard of PRISM or any scheme like it.
The chief executive of transparency NGO Index on Censorship, Kirsty Hughes, remarked on Twitter that the contradiction seemed to leave two options: "Back door or front?" she posted.
Ed. Note: Corporations Lie & Get Away With Murder
Time for a Corporate Death Penalty?
Here are a few (of many) examples:
Tobacco executives, under oath, deny cancer allegations
Camel cigarettes had the largest booth at American Medical Association's 1948 convention; boasting, "More doctors smoke Camels than any other cigarette." which is a splendid example of "Profits Not People" and should be a 'Wake Up Call' for HONEST Evaluation of the Dangers and Hazards from Cellular Telephones and effects of amplified microwave frequencies emitting from Cellular repeater sites. ~ "It's A Matter of Trust" [Click to Continue Reading]
Tobacco companies ordered to admit they lied over smoking dangerExecutives deny Goldman Sachs fraud
KBR denies withholding news on Iraq hostages
PG&E says it is not to blame for San Bruno blast
Official denies Cheney 'coordinated' firm's Iraq contract
KBR denies exposing group to cancer-causing chemicals
BP denies 'gross negligence' in massive 2010 Gulf oil spill
Halliburton Denies Destroying Evidence in BP Oil Spill Case
Dow Chem denies report of Indian court notice on Bhopal case
Industry denies fracking threatens nation's water supplies at CO meeting
Once Upon A Time...
April 11, 1989
The following was posted to a Usenet Group on Tuesday 11 April 1989:
RISKS-LIST: RISKS-FORUM Digest Tuesday 11 April 1989 Volume 8 : Issue 54
FORUM ON RISKS TO THE PUBLIC IN COMPUTERS AND RELATED SYSTEMS ACM Committee on Computers and Public Policy, Peter G. Neumann, moderator
Date: Tue, 11 Apr 89 08:12:04 PDT
From: cas@toad.com (Curtis Spangler)
Subject: NSA and Not Secure AgenciesSan Francisco Chronicle, Chronicle Wire Services, April 11, 1989:
Computer Group Wary of Security Agency
A public interest group said yesterday that the National Security Agency, the nation's biggest intelligence agency, could exert excessive control over a program to strengthen the security of computer systems throughout the federal government.
The group, Computer Professionals for Social Responsibility - based in Palo Alto - urged key members of Congress to focus "particularly close scrutiny" on the agency's role in helping to implement legislation aimed at safeguarding sensitive but unclassified information in federal computers.
"There is a constant risk that the federal agencies, under the guise of enhancing computer security, may find their programs - to the extent that they rely upon computer systems - increasingly under the supervision of the largest and most secretive intelligence organization in the country," it said.
December 22, 2000
Security-Enhanced Linux (SELinux) is a GNU/Linux feature that provides the mechanism for supporting access control security policies, including United States Department of Defense-style mandatory access controls, through the use of GNU/Linux Security Modules (LSM) in the GNU/Linux kernel. It is not a GNU/Linux distribution, but rather a set of kernel modifications and user-space tools that can be added to various GNU/Linux distributions. Its architecture strives to separate enforcement of security decisions from the security policy itself and streamlines the volume of software charged with security policy enforcement. The key concepts underlying SELinux can be traced to several earlier projects by the United States National Security Agency. It has been integrated into the mainline GNU/Linux kernel since version 2.6, on 8 August 2003.
From: http://www.nsa.gov/research/selinux/background.shtml:
SELinux Background ~ Researchers in the National Information Assurance Research Laboratory of the National Security Agency (NSA) worked with Secure Computing Corporation (SCC) to develop a strong, flexible mandatory access control architecture based on Type Enforcement, a mechanism first developed for the LOCK system. The NSA and SCC developed two Mach-based prototypes of the architecture: DTMach and DTOS. The NSA and SCC then worked with the University of Utah's Flux research group to transfer the architecture to the Fluke research operating system. During this transfer, the architecture was enhanced to provide better support for dynamic security policies. This enhanced architecture was named Flask. The NSA integrated the Flask architecture into the GNU/Linux® operating system to transfer the technology to a larger developer and user community. The architecture has been subsequently mainstreamed into GNU/Linux® and ported to several other systems, including the Solaris™ (Sun Microsystems/Oracle) operating system, the freeBSD® operating system, and the Darwin (Apple) kernel, spawning a wide range of related work.
Images Via Wikipedia, the free encyclopedia
Radio Control Models ~ Aviation
FBI admits to using surveillance drones over US soil
Robert Mueller tells Congress bureau uses drones in a 'very, very minimal way' as senators describe 'burgeoning concern'
Dan Roberts in Washington, guardian.co.uk, Wednesday 19 June 2013 16.20 EDT, Article Source
Link to video: FBI uses drones in the US, senators told
The FBI has admitted it sometimes uses aerial surveillance drones over US soil, and suggested further political debate and legislation to govern their domestic use may be necessary.
Speaking in a hearing mainly about telephone data collection, the bureau's director, Robert Mueller, said it used drones to aid its investigations in a "very, very minimal way, very seldom".
However, the potential for growing drone use either in the US, or involving US citizens abroad, is an increasingly charged issue in Congress, and the FBI acknowleged there may need to be legal restrictions placed on their use to protect privacy.
"It is still in nascent stages but it is worthy of debate and legislation down the road," said Mueller, in response to questions from Hawaii senator Mazie Hirono.
Hirono said: "I think this is a burgeoning concern for many of us."
Dianne Feinstein, who is also chair of the Senate intelligence committee, said the issue of drones worried her far more than telephone and internet surveillance, which she believes are subject to sufficient legal oversight.
"Our footprint is very small," Mueller told the Senate judiciary committee. "We have very few and have limited use."
He said the FBI was in "the initial stages" of developing privacy guidelines to balance security threats with civil liberty concerns.
It is known that drones are used by border control officials and have been used by some local law enforcement authorities and Department of Homeland Security in criminal cases.
Mueller said he wasn't sure if there were official agreements with these other agencies.
"To the extent that it relates to the air space there would be some communication back and forth [between agencies]," Mueller said.
A Senate intelligence committee member, Mark Udall, Democrat of Colorado, later questioned whehter such use of drones was constitutional. "Unmanned aerial systems have the potential to more efficiently and effectively perform law enforcement duties, but the American people expect the FBI and other government agencies to first and foremost protect their constitutional rights," Udall said in a prepared statement.
"I am concerned the FBI is deploying drone technology while only being in the 'initial stages' of developing guidelines to protect Americans' privacy rights. I look forward to learning more about this program and will do everything in my power to hold the FBI accountable and ensure its actions respect the US constitution."
Another senator, Chuck Grassley, Republican of Iowa, also expressed concern. Asked whether the FBI drones were known about before the Mueller hearing, Grassley told CNN "absolutely not." Grassley added the FBI was asked last year whether agents were using drones but the bureau never got back with an answer.
At the same hearing, Mueller urged Congress to move carefully before making any changes that might restrict the National Security Agency programs for mass collection of people's phone records and information from the internet.
"If we are to prevent terrorist attacks, we have to know and be in their communications," said Mueller. "Having the ability to identify a person in the United States, one telephone number with a telephone that the intelligence community is on in Yemen or Somalia or Pakistan ... may prevent that one attack, that Boston or that 9/11."
The FBI director argued for the continued use of the NSA programs. "Are you going to take the dots off the table, make it unavailable to you when you're trying to prevent the next terrorist attack? That's a question for Congress," said Mueller. The Associated Press contributed to this report

Steve Bell on the Afghanistan peace talks: Talking to the Taleban ~ Twelve Years Late
SO WHAT WAS THE POINT OF ALL THAT WAR BUSINESS AND WHATEVER YOU DO DON'T TALK TO ASSAD
The Guardian, Tuesday 18 June 2013 18.12 EDT, Cartoon Source ... Comments
Lies, Lies, Lies
Lies, Lies, Lies - BlackMustache.com
"The lie can be maintained only for such time as the State can shield the people from the political, economic and/or military consequences of the lie. It thus becomes vitally important for the State to use all of its powers to repress dissent, for the truth is the mortal enemy of the lie, and thus by extension, the truth becomes the greatest enemy of the State." Dr. Joseph M. Goebbels
NSA surveillance is an attack on American citizens,
says Noam ChomskyGovernments will use whatever technology is available to combat their primary enemy -- their own population, says critic
Fiona Harvey in Bonn, guardian.co.uk, Wednesday 19 June 2013 07.02 EDT, Article Source
Noam Chomsky has praised the Guardian’s revelations about the activities of the
National Security Agency. Photograph: Graeme Robertson for the GuardianThe actions of the US government in spying on its and other countries' citizens have been sharply criticised by Noam Chomsky, the prominent political thinker, as attacks on democracy and the people.
"Governments should not have this capacity. But governments will use whatever technology is available to them to combat their primary enemy -- which is their own population," he told the Guardian.
In his first public comment on the scandal that has enveloped the US, UK and other governments, as well as internet companies such as Google and Microsoft, Chomsky said he was not overly surprised technology and corporations were being used in this way.
"This is obviously something that should not be done. But it is a little difficult to be too surprised by it," he said. "They [governments and corporations] take whatever is available, and in no time it is being used against us, the population. Governments are not representative. They have their own power, serving segments of the population that are dominant and rich."
Chomsky, who has strongly supported the Occupy movement and spoken out against the Obama administration's use of drones, warned that young people were much less shocked at being spied on and did not view it as such a problem.
"Polls in the US indicate there is generational issue here that someone ought to look into -- my impression is that younger people are less offended by this than the older generation. It may have to do with the exhibitionist character of the internet culture, with Facebook and so on," he said. "On the internet, you think everything is going to be public."
Other technologies could also come to be used to spy more effectively on people, he added. "They don't want people to know what they're doing. They want to be able to use [new technology] against their own people.
"Take a look at drones, and what is developing. You will find new drone technology being used in 10 or 12 years from now. They are looking at [trying to make] tiny drones that can go in your living room, like a fly on the wall."
He praised the Guardian's revelations about the activities of the National Security Agency, and the whistleblower Ed Snowden, who has been taking refuge in Hong Kong. "We need this kind [of journalism]," he said. "We ought to know about it."
Chomsky, a much-lauded academic and professor of linguistics, gained renown as a political critic when he vocally opposed the Vietnam war. Since then, he has written dozens of books on political power, capitalism and democracy and espoused a variety of activist campaigns, most recently the Occupy movement.
Cree Prophecy
Only after the last tree has been cut down,
Only after the last river has been poisoned,
Only after the last fish has been caught,
Only then will you find money cannot be eaten.

Never, never be afraid to do what's right, especially if the well-being of a person or animal is at stake.
Society's punishments are small compared to the wounds we inflict on our soul when we look the other way.
It Was Not My Intention to Step On Your Denial
By Dahbud Mensch, Monday, June17, 2013
A patriotic whistle blower, similar to Daniel Ellsberg, exposed how corporations (we were led to trust) sold out their users.
A partial list of those companies was provided: Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, Twitter, and Apple. (Twitter was not originally mentioned because == if people got angry at Twitter ... and stopped using it ... there would be no way to spy on flash mobs, etc.?)
Public Denial and apathy appear to be present because Republican War Criminal George W Bush, with his criminal administration officials, said repeatedly (about his illegal Telecom Spy program): warrantless surveillance is carefully targeted to include only international calls and e-mails into or out of the USA, and only those involving at least one party suspected of being a member or ally of al-Qaeda or a related terror group and people do not want to believe government would allow for the removal of Liberties and Freedoms from US citizens. "We've been asked to sacrifice our most important rights." Snowden on Surveillance
None of the Above
should be a choice on Voter Ballots
Nobody for President
Corposenility (sic) or Liars'R'Us ???
Is it a good idea to continue using corporate Search, Maps, Video, eMail, Hardware; including Phones, etc. and spending more money on those who betrayed their USERS?
Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, Twitter, Apple, etc. claim they did not sell out their users and deny giving user account backdoor access to NSA. Here are some article headlines and links:
Yahoo, Google, Facebook and more face fight to salvage reputations over NSA leaks
Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube and Apple have been floundering for a response
http://www.guardian.co.uk/technology/2013/jun/10/apple-google-giants-nsa-revelationsTechnology giants struggle to maintain credibility over NSA Prism surveillance
Strongly-worded denials issued by Apple, Facebook and Google about their co-operation are followed by further revelations
http://www.guardian.co.uk/world/2013/jun/09/technology-giants-nsa-prism-surveillanceDid Corporations Acquire Selective Memory
or Corposenility (sic) on December 22, 2000 ???Security-Enhanced Linux (SELinux) is a GNU/Linux feature that provides the mechanism for supporting access control security policies, including United States Department of Defense-style mandatory access controls, through the use of GNU/Linux Security Modules (LSM) in the GNU/Linux kernel. It is not a GNU/Linux distribution, but rather a set of kernel modifications and user-space tools that can be added to various GNU/Linux distributions. Its architecture strives to separate enforcement of security decisions from the security policy itself and streamlines the volume of software charged with security policy enforcement. The key concepts underlying SELinux can be traced to several earlier projects by the United States National Security Agency. It has been integrated into the mainline GNU/Linux kernel since version 2.6, on 8 August 2003.
From: http://www.nsa.gov/research/selinux/background.shtml:
SELinux Background ~ Researchers in the National Information Assurance Research Laboratory of the National Security Agency (NSA) worked with Secure Computing Corporation (SCC) to develop a strong, flexible mandatory access control architecture based on Type Enforcement, a mechanism first developed for the LOCK system. The NSA and SCC developed two Mach-based prototypes of the architecture: DTMach and DTOS. The NSA and SCC then worked with the University of Utah's Flux research group to transfer the architecture to the Fluke research operating system. During this transfer, the architecture was enhanced to provide better support for dynamic security policies. This enhanced architecture was named Flask. The NSA integrated the Flask architecture into the GNU/Linux® operating system to transfer the technology to a larger developer and user community. The architecture has been subsequently mainstreamed into GNU/Linux® and ported to several other systems, including the Solaris™ (Sun Microsystems/Oracle) operating system, the freeBSD® operating system, and the Darwin (Apple) kernel, spawning a wide range of related work.
Images Via Wikipedia, the free encyclopediaIs It Time for a Corporate Death Penalty?
Notes from ~@~
Kipper Williams on fracking ~ Cartoon Source
Shale Gas Drilling [with comment:] "I told you we'd shake up the market"
Opening Multiple Cans of Worms
FBI chief Mueller says spy tactics could have stopped 9/11 attacksInsane War Criminal
Says What?
Steve Bell cartoon"God told me to strike at al Qaida and I struck them, and then he instructed me to strike at Saddam, which I did, and now I am determined to solve the problem in the Middle East."~ War Criminal George W. Bush
9/11 Commission
Omissions#1 ~ Who is John O'Neill and Why Did He Die?
#2 ~ 11 Questions Avoided by Corporate Media On NORAD Tapes
1. *Who was responsible for scheduling multiple war games and terror exercises involving aircraft for Sept. 11th
2. Who moved "Global Guardian" normally scheduled for October to September?
3. Who designed the war games to involve 'hijackings'?
4. Who planned and scheduled the movement of Airforce aircraft north to Canada, Alaska and Greenland?
5. Who planned the terror exercise at the NRO (National Reconnaissance Office) involving an evacuation in response to threat from the air?
6. Who was "hands-on" responsible for coordinating all the war games the morning of September 11th?
7. Who would have been responsible for turning off the war games to enable a timely real world response to the attacks?
8. How were as many as 21 false radar blips or possible targets (per Jane Garvey) inserted into FAA radar screens?
9. Who was responsible for the identification of ghost flight 11 which allegedly continued to fly south past Manhattan and which may have caused NORAD's Langley intercept jets to vector North toward NYC rather than D.C.? * [NOTE: John Farmer of the 9/11 Commission said to me personally that the 9/11 Commission was never able to identify the individual for this information--to resolve this anomaly.]*
10. Why was there no reference to the pattern of 9/11 Commission cover-up including that of Able Danger as revealed by Capt. Scott Philpott?
11. *The bottom line question that corporate media refuse to answer and which the 9/11 Commission ignored is who, specifically, would have been responsible for creating the circumstances that led to the confusion or fog the morning of 9/11 and who should have immediately ceased any and all war gaming activity and deceptive radar data?
To begin to answer these questions journalists intent on getting answers to questions long asked by the families and others should visit:
*Center for Cooperative Research: Essay -- "U.S. Military Exercises up to 9/11"*
Continue Reading at Source: http://www.scoop.co.nz/stories/HL0608/S00053.htm
#3 ~ YOU ARE LOOKING AT A US GOVERNMENT LIE
On Friday 14 December 2001 a videotape of Osama bin Laden "confessing" to the 9/11 attacks was released. The tape was supposedly found in a house in Qandahar, Afghanistan. The recording was of very poor audio and visual quality and the authenticity of the tape was questioned.
This annoyed President Bush who said "[It is] preposterous to think this tape was doctored."
Okay, let's have a look

Here's 5 Osama's - which is the odd one out?#4 ~ Birds of a Feather ~ Are You With Us or War Criminals
#5 ~ EHUD BARAK APPEARS ON BBC MINUTES AFTER THE 9/11 ATTACK WITH A PRE-PREPARED SPEECH
#6 ~ Did the Gas Station 9/11 Pentagon Video Tape Get Misplaced ???
#7 ~ CRASH AT THE WHITE HOUSE By MAUREEN DOWD, September 13, 1994
#8 ~ What about crazy people who insist God told them to kill innocent children ~ "God told me to strike at al Qaida and I struck them, and then he instructed me to strike at Saddam, which I did, and now I am determined to solve the problem in the Middle East." - George W. Bush
#9 ~ What Goes Around, Comes Around:
Bush's Impending
WatergateBy Harvey Wasserman
May 23, 1991George Bush should be impeached. Whether he will be impeached depends on the intestinal fortitude of Congress. But the evidence is clearly sufficient to begin proceedings.
The grounds for impeachment rest in the now-familiar circumstances around the 1980 Iranian hostage crisis. The story has circulated since the mid 1980s, but in recent weeks has gained startling new confirmation.
The circumstances are worth repeating: On November 4, 1979, radical Iranian students seized some 55 American citizens and began a crisis that lasted until the moment Ronald Reagan was inaugurated as president 444 days later.
Future historians may well blame President Jimmy Carter for the inception of the crisis. He ignored warnings that it could happen and stumbled badly once it began. Some may also wonder if he exploited the situation to deflect a challenge to his renomination from Sen. Edward Kennedy.
But by October of 1980, one thing was clear: If the hostages were released prior to the election, Carter would be re-elected. If not, Ronald Reagan would win. All major polls -- including one by the primary Republican pollster, Richard Wirthlin -- showed a 10 percent swing on just that issue.
In early October, word spread through the world media that Carter had negotiated a deal for the hostages' release. It was widely believed that he had agreed to unfreeze some $4 billion in assets claimed by the deposed Shah, and to supply spare parts to the American-made arms inherited by the Ayatollah Khomeini's revolutionary regime. The hostages were due home by mid-October, in ample time to assure Carter's re-election.
Then, mysteriously, the deal was off. The hostages weren't coming home after all. What happened?
The Iranians were known to detest Jimmy Carter. Despite his advocacy of human rights, Carter had befriended the brutal, repressive Shah. Conceivably, the Muslim fundamentalists tantalized Carter with the hostages' possible release and then, just for the hell of it, left him hanging.
There were other theories. Columnist George Will suggested that Iran responded to Reagan because he had threatened to use nuclear weapons if the hostages weren't released, something the pacifistic Carter would not have done.
But two years later, Barbara Honegger, a member of the Reagan campaign team, angrily left the White House staff, leveling charges of sexual discrimination. She then asserted that during the 1980 campaign a special "October Surprise" Committee had operated with a mandate that appeared focused on sabotaging Carter's arrangements and guaranteeing that the hostages remain in Teheran until after the 1980 election.
Honegger claimed no direct proof, but she recalled being told that the hostages would not be coming home because October Surprise Committee member Richard Allen (later chief of Reagan's National Security Council) had "cut a deal" to keep them in Teheran. Future CIA director William Casey may have masterminded the sabotage, Honegger said.
Honegger was dismissed by Reagan-Bush staffers as a "low-level munchkin." But her allegations were given powerful confirmation in 1985 by Abolhassan Bani-Sadr, president of Iran at the time of the crisis. According to Bani-Sadr, George Bush, then candidate for vice president, may personally have flown to Paris on a crucial weekend to convince the son of the Ayatollah "that the hostages should not be released during the Carter administration." Instead, Bani-Sadr said, "they should be released when Reagan became president. So, in return, Reagan would give them arms."
Indeed, Iran was desperately needed weapons to carry on its holy war with Iraq's Saddam Hussein. Hostilities had begun in September, and they were short on guns and cash. There was little doubt they would trade whatever "assets" they had for the arms they needed -- including the American hostages.
The story became common knowledge among top Middle Eastern operatives, including Bassam Abu Sharif, number two man in the Palestine Liberation Organization (assassinated during the recent Gulf War) and Mansour Rafizadeh, a former CIA operative and head of the Shah's dreaded SAVAK secret police.
"The deal was made to release the hostages exactly the moment Ronald Reagan was president," Rafizadeh told the Other America's Radio Network. "It was promised for the arms," said Rafizadeh. "The moment Ronald Reagan was president, they signaled the plane [with the hostages aboard], they took off. After, the shipment of the arms started from Tel Aviv."
Despite repeated denials from the Reagan-Bush team, the story gained some media prominence during the 1988 election, including a story in the Advocate, a major feature co-authored by activist Abbie Hoffman (now dead by an alleged suicide) in Playboy, and an op-ed in the now-defunct Los Angeles Herald-Examiner.
Just prior to the election, a self-proclaimed former CIA operative named Richard Brenneke claimed to have personally flown Bush to Paris to negotiate the deal. Producers from CBS' 60 Minutes were preparing a feature on Brenneke, who was in jail in Colorado, when questions about his credibility were raised and the feature was canceled. The Miami Herald, Los Angeles Times, Boston Globe and other major publications carried stories concluding there was insufficient evidence to confirm or deny the deal occurred.
Recently, Brenneke was cleared of perjury charges stemming from his claimed connection to the Paris trip. And the assertions have resurfaced with new power. Former Carter security adviser Gary Sick, after a two-year investigation, has released a book arguing the likelihood that an "arms for no hostages" deal was, in fact, made. Bani-Sadr has issued a new book asserting the same thing. Bill Moyers' Frontline devoted an entire program to it. Bush's denials -- issued just before his recent heart problems -- that he ever flew to Paris during the 1980s campaign made front-page news across the nation.
But does the story really turn on that? White House spokesperson Marlin Fitzwater says all of Bush's time can be accounted for. Bush has vehemently denied ever going to Paris during the 1980 campaign. Yet the official log of Bush's whereabouts on the crucial weekend -- when he is alleged to have made the deal -- has a hole big enough for him to have flown to Paris, negotiated the deal and then flown back.
The idea that the vice presidential candidate would have flown abroad to negotiate a deal that amounts to treason might seem absurd. Bush, after all, was formerly head of the Central Intelligence Agency, and a master of plausible deniability. It was clearly out of character to expose himself in such a direct manner to what could ultimately be a scandal of truly epic proportions.
On the other hand, the Iranians could well have demanded Bush's personal presence. It was well-known that the Ayatollah's cabal put little faith in the American electoral system. Like many Iranians, they believed that the true power in U.S. politics rested not with elected officials, but with the secret police, i.e. the CIA. As the CIA's former head, they believed Bush to be the true power in the Reagan-Bush campaign, and may well have demanded his personal approval for any trade of their hostage "assets."
Even so, the question of Bush going to Paris may be a red herring. The circumstances pointing to the likelihood of a deal being made are overwhelming. That Carter had all but secured their release is well-known. That there was a Reagan-Bush October Surprise Committee run by Allen and Casey is undeniable, as is the fact that the hostages were released precisely at the moment that Ronald Reagan was sworn in as President. It is also well-known that large quantities of American-sponsored arms began flowing through Israel in March 1981.
As for the question of Iranian motive, although Khomeini profoundly hated Jimmy Carter, he had no reason to like Reagan more, and would hardly have bothered to spite one representative of the "Great Satan" over another. In Iran's jihad with Saddam Hussein, however, the hostages were an asset to be traded, a bargaining chip to go to the highest bidder. Carter was deeply disinclined to send Iran large quantities of arms; once in office, Reagan did just that.
Thus, the evidence suggesting that George Bush actually flew to Paris to negotiate the deal is ultimately irrelevant. As the number two man on the ticket and the former head of the CIA, no such deal would have been cut without Bush's approval, whether he flew to Paris or not.
And that means high treason and public crimes of the highest order. The ideal that the nominees of a major party could have knowingly prolonged the agony of American citizens in exchange for weapons is about as low as one could imagine any politician sinking.
In fact, the sabotage may even have preceded the October negotiations. Earlier in 1980, Carter set out to free the hostages with "Operation Eagle Claw," built around a surprise helicopter landing and secret assault on the building where they were held in Teheran.
The mission proved disastrous. At least two American helicopters crashed into each other in the desert long before they made it anywhere near Teheran. Eight Marines were killed. Carter looked ineffectual and frustration with the hostage crisis escalated.
Unfortunately, the operatives in charge of Desert Claw may not have been loyal to Carter -- or to the U.S. Carter held deeply alienated a broad range of CIA operatives by trying to clean up the Agency when he first came to power. Admiral Stansfield Turner, the tough but honest Navy man Carter put in charge at the CIA fired some 600 "spooks" soon after taking command. Many were deeply loyal to former Director George Bush and to the "Old Boy" network that serves as the Agency's true infrastructure.
That loyalty may have carried over to sabotage of Operation Eagle Claw. For the man who served as chief mission planner was none other than Richard Secord, who later surfaced as a major kingpin in the shady arms dealings between the Reagan White House and the contras of Nicaragua. A top staffer at a key base in Eagle Claw's catastrophic helicopter support operation was none other than the legendary Colonel Oliver North. Working closely with him as a logistical planner was Albert Hakkim, who later sat by Secord's side at the Congressional Iran-contra hearings and wept of his love for Oliver North.
As historian Donald Fried has put it "Precisely the people in the intelligence community commissioned to develop some kind of rescue for the hostages were those elements of covert action close to William Casey and hostile to Carter."
Casey, of course, later became Reagan's CIA chief. But higher up in the chain at the time of the failed rescue mission was Donald Gregg, a member of Carter's National Security Council who later surfaced as s high-level Bush operative. Gregg's close personal ties to Bush became a serious issue in light of his extensive dealings with key contra figures tied both to the Iran-contra scandal and illegal drug shipments coming from Central America. Gregg is now Bush's ambassador to South Korea.
In a recent interview Carter specifically implied that Gregg might have betrayed key security items to Bush during the 1980 campaign. Students of the affair, including author Gary Sick, also wonder if Gregg might have fed the Reagan-Bush team key items in the dealings between Carter and the Iranians.
At this point with Bush's popularity so high on the heels of a much-desired military victory millions of Americans would not want to believe such a story could be true. The U.S. triumph over Saddam Hussein clearly filled a psychological void plaguing Americans since Vietnam. It allowed for a military triumph where the most recent memory had been of defeat. And it gave Americans the opportunity to do penance for the mistreatment of Vietnam veterans by showering those who fought the brief Gulf War with a heroes' welcome outstripping anything since World War II and way out of proportion for the size and duration of the Iraqi massacre.
Nonetheless, there is nothing in the character of the Reagan-Bush regimes that indicates a moral incapability of cutting such a deal. More than 200 members of the administration were indicted during their eight-year tenure, including Attorney General Edwin Meese and close Reagan counselors Michael Deaver and Lyn Nofziger. By all accounts, the Reagan-Bush administration were the most corrupt since the short term of Ulysses S. Grant.
The idea that Ronald Reagan and George Bush could have conspired to prolong the torment of U.S. hostages dwarfs the miasma that was Watergate on both a moral and political scale. Ultimately its impact will depend on the willingness of Congress to investigate the facts and act on what it finds. It is time for Congress to once again assume its role in the balance of powers. Impeachment means bringing to trial. The evidence is clearly sufficient to begin the process.
At presstime, Congress had launched a preliminary staff investigation into the Reagan-Bush 1980 campaign and whether there had been negotiations with Iran to delay the release of the American Hostages.
#10 ~ Who Stole 2.3 Trillion Dollars from US Tax Payers? ~ Did War Criminal Dick Cheney plan this, with his friends, during his Secret Energey Meetings where he allegedly planned the 9/11 attack?
WHY IS HONEST GOVERNMENT
So RESISTED BY POLITICIANS?
CALL FOR CONSTITUTIONAL CONVENTION TO REMOVE TRAITORS
WHO WOULD ABOLISH UNITED STATES LIBERTY AND FREEDOM
http://flyingsnail.com/Dahbud/index.html
In Order for Everybody to Understand:
Spying on US Citizens, by REPUBLICANS,
began with Illegal Spying on Quakers and
Peanut-Butter & Jelly Sandwich MakersNever Forget!
The Other Big Brother
Michael Isikoff, Jan 29, 2006 7:00 PM EST, Article Source
The demonstration seemed harmless enough. Late on a June afternoon in 2004, a motley group of about 10 peace activists showed up outside the Houston headquarters of Halliburton, the giant military contractor once headed by Vice President [War Criminal] Dick Cheney. They were there to protest the corporation's supposed "war profiteering." The demonstrators wore papier-mache masks and handed out free peanut-butter-and-jelly sandwiches to Halliburton employees as they left work. The idea, according to organizer Scott Parkin, was to call attention to allegations that the company was overcharging on a food contract for troops in Iraq. "It was tongue-in-street political theater," Parkin says.
But that's not how the Pentagon saw it. To U.S. Army analysts at the top-secret Counterintelligence Field Activity (CIFA), the peanut-butter protest was regarded as a potential threat to national security. Created three years ago by the Defense Department, CIFA's role is "force protection"--tracking threats and terrorist plots against military installations and personnel inside the United States. In May 2003, Paul Wolfowitz, then deputy Defense secretary, authorized a fact-gathering operation code-named TALON--short for Threat and Local Observation Notice--that would collect "raw information" about "suspicious incidents." The data would be fed to CIFA to help the Pentagon's "terrorism threat warning process," according to an internal Pentagon memo.
A Defense document shows that Army analysts wrote a report on the Halliburton protest and stored it in CIFA's database. It's not clear why the Pentagon considered the protest worthy of attention--although organizer Parkin had previously been arrested while demonstrating at ExxonMobil headquarters (the charges were dropped). But there are now questions about whether CIFA exceeded its authority and conducted unauthorized spying on innocent people and organizations. A Pentagon memo obtained by NEWSWEEK shows that the deputy Defense secretary now acknowledges that some TALON reports may have contained information on U.S. citizens and groups that never should have been retained. The number of reports with names of U.S. persons could be in the thousands, says a senior Pentagon official who asked not be named because of the sensitivity of the subject.
CIFA's activities are the latest in a series of disclosures about secret government programs that spy on Americans in the name of national security. In December, the ACLU obtained documents showing the FBI had investigated several activist groups, including People for the Ethical Treatment of Animals and Greenpeace, supposedly in an effort to discover possible ecoterror connections. At the same time, the White House has spent weeks in damage-control mode, defending the controversial program that allowed the National Security Agency to monitor the telephone conversations of U.S. persons suspected of terror links, without obtaining warrants.
Last Thursday, Cheney called the program "vital" to the country's defense against Al Qaeda. "Either we are serious about fighting this war on terror or not," he said in a speech to the Manhattan Institute, a conservative think tank. But as the new information about CIFA shows, the scope of the U.S. government's spying on Americans may be far more extensive than the public realizes.
It isn't clear how many groups and individuals were snagged by CIFA's dragnet. Details about the program, including its size and budget, are classified. In December, NBC News obtained a 400-page compilation of reports that detailed a portion of TALON's surveillance efforts. It showed the unit had collected information on nearly four dozen antiwar meetings or protests, including one at a Quaker meetinghouse in Lake Worth, Fla., and a Students Against War demonstration at a military recruiting fair at the University of California, Santa Cruz. A Pentagon spokesman declined to say why a private company like Halliburton would be deserving of CIFA's protection. But in the past, Defense Department officials have said that the "force protection" mission includes military contractors since soldiers and Defense employees work closely with them and therefore could be in danger.
CIFA researchers apparently cast a wide net and had a number of surveillance methods--both secretive and mundane--at their disposal. An internal CIFA PowerPoint slide presentation recently obtained by William Arkin, a former U.S. Army intelligence analyst who writes widely about military affairs, gives some idea how the group operated. The presentation, which Arkin provided to NEWSWEEK, shows that CIFA analysts had access to law-enforcement reports and sensitive military and U.S. intelligence documents. (The group's motto appears at the bottom of each PowerPoint slide: "Counterintelligence 'to the Edge'.") But the organization also gleaned data from "open source Internet monitoring." In other words, they surfed the Web.
That may have been how the Pentagon came to be so interested in a small gathering outside Halliburton. On June 23, 2004, a few days before the Halliburton protest, an ad for the event appeared on houston.indymedia.org, a Web site for lefty Texas activists. "Stop the war profiteers," read the posting. "Bring out the kids, relatives, Dick Cheney, and your favorite corporate pigs at the trough as we will provide food for free."
Four months later, on Oct. 25, the TALON team reported another possible threat to national security. The source: a Miami antiwar Web page. "Website advertises protest planned at local military recruitment facility," the internal report warns. The database entry refers to plans by a south Florida group called the Broward Anti-War Coalition to protest outside a strip-mall recruiting office in Lauderhill, Fla. The TALON entry lists the upcoming protest as a "credible" threat. As it turned out, the entire event consisted of 15 to 20 activists waving a giant bush lied sign. No one was arrested. "It's very interesting that the U.S. military sees a domestic peace group as a threat," says Paul Lefrak, a librarian who organized the protest.
Arkin says a close reading of internal CIFA documents suggests the agency may be expanding its Internet monitoring, and wants to be as surreptitious as possible. CIFA has contracted to buy "identity masking" software that would allow the agency to create phony Web identities and let them appear to be located in foreign countries, according to a copy of the contract with Computer Sciences Corp. (The firm declined to comment.)
Pentagon officials have broadly defended CIFA as a legitimate response to the domestic terror threat. But at the same time, they acknowledge that an internal Pentagon review has found that CIFA's database contained some information that may have violated regulations. The department is not allowed to retain information about U.S. citizens for more than 90 days--unless they are "reasonably believed" to have some link to terrorism, criminal wrongdoing or foreign intelligence. There was information that was "improperly stored," says a Pentagon spokesman who was authorized to talk about the program (but not to give his name). "It was an oversight." In a memo last week, obtained by NEWSWEEK, Deputy Defense Secretary Gordon England ordered CIFA to purge such information from its files--and directed that all Defense Department intelligence personnel receive "refresher training" on department policies.
That's not likely to stop the questions. Last week Democrats on the Senate intelligence committee pushed for an inquiry into CIFA's activities and who it's watching. "This is a significant Pandora's box [Pentagon officials] don't want opened," says Arkin. "What we're looking at is hints of what they're doing." As far as the Pentagon is concerned, that means we've already seen too much.
Bush Authorized Domestic Spying
By Dan Eggen, Washington Post Staff Writer Friday, December 16, 2005, Article Source
President Bush signed a secret order in 2002 authorizing the National Security Agency to eavesdrop on U.S. citizens and foreign nationals in the United States, despite previous legal prohibitions against such domestic spying, sources with knowledge of the program said last night.
The super-secretive NSA, which has generally been barred from domestic spying except in narrow circumstances involving foreign nationals, has monitored the e-mail, telephone calls and other communications of hundreds, and perhaps thousands, of people under the program, the New York Times disclosed last night.
The aim of the program was to rapidly monitor the phone calls and other communications of people in the United States believed to have contact with suspected associates of al Qaeda and other terrorist groups overseas, according to two former senior administration officials. Authorities, including a former NSA director, Gen. Michael V. Hayden, were worried that vital information could be lost in the time it took to secure a warrant from a special surveillance court, sources said.
But the program's ramifications also prompted concerns from some quarters, including Sen. John D. Rockefeller IV (W.Va.), the ranking Democrat on the intelligence committee, and the presiding judge of the surveillance court, which oversees lawful domestic spying, according to the Times.
The Times said it held off on publishing its story about the NSA program for a year after administration officials said its disclosure would harm national security.
The White House made no comment last night. A senior official reached by telephone said the issue was too sensitive to talk about. None of several press officers responded to telephone or e-mail messages.
Congressional sources familiar with limited aspects of the program would not discuss any classified details but made it clear there were serious questions about the legality of the NSA actions. The sources, who demanded anonymity, said there were conditions under which it would be possible to gather and retain information on Americans if the surveillance were part of an investigation into foreign intelligence.
But those cases are supposed to be minimized. The sources said the actual work of the NSA is so closely held that it is difficult to determine whether it is acting within the law.
The revelations come amid a fierce congressional debate over reauthorization of the USA Patriot Act, an anti-terrorism law passed after the Sept. 11, 2001, attacks. The Patriot Act granted the FBI new powers to conduct secret searches and surveillance in the United States.
Most of the powers covered under that law are overseen by a secret court that meets at Justice Department headquarters and must approve applications for wiretaps, searches and other operations. The NSA's operation is outside that court's purview, and according to the Times report, the Justice Department may have sought to limit how much that court was made aware of NSA activities.
Public disclosure of the NSA program also comes at a time of mounting concerns about civil liberties over the domestic intelligence operations of the U.S. military, which have also expanded dramatically after the Sept. 11 attacks.
For more than four years, the NSA tasked other military intelligence agencies to assist its broad-based surveillance effort directed at people inside the country suspected of having terrorist connections, even before Bush signed the 2002 order that authorized the NSA program, according to an informed U.S. official.
The effort, which began within days after the attacks, has consisted partly of monitoring domestic telephone conversations, e-mail and even fax communications of individuals identified by the NSA as having some connection to al Qaeda events or figures, or to potential terrorism-related activities in the United States, the official said.
It has also involved teams of Defense Intelligence Agency personnel stationed in major U.S. cities conducting the type of surveillance typically performed by the FBI: monitoring the movements and activities -- through high-tech equipment -- of individuals and vehicles, the official said.
The involvement of military personnel in such tasks was provoked by grave anxiety among senior intelligence officials after the 2001 suicide attacks that additional terrorist cells were present within U.S. borders and could only be discovered with the military's help, said the official, who had direct knowledge of the events.
Kate Martin, director of the Center for National Security Studies, said the secret order may amount to the president authorizing criminal activity.
The law governing clandestine surveillance in the United States, the Foreign Intelligence Surveillance Act, prohibits conducting electronic surveillance not authorized by statute. A government agent can try to avoid prosecution if he can show he was "engaged in the course of his official duties and the electronic surveillance was authorized by and conducted pursuant to a search warrant or court order of a court of competent jurisdiction," according to the law.
"This is as shocking a revelation as we have ever seen from the Bush administration," said Martin, who has been sharply critical of the administration's surveillance and detention policies. "It is, I believe, the first time a president has authorized government agencies to violate a specific criminal prohibition and eavesdrop on Americans."
Caroline Fredrickson, director of the Washington legislative office of the American Civil Liberties Union, said she is "dismayed" by the report.
"It's clear that the administration has been very willing to sacrifice civil liberties in its effort to exercise its authority on terrorism, to the extent that it authorizes criminal activity," Fredrickson said.
The NSA activities were justified by a classified Justice Department legal opinion authored by John C. Yoo, a former deputy in the Office of Legal Counsel who argued that congressional approval of the war on al Qaeda gave broad authority to the president, according to the Times.
That legal argument was similar to another 2002 memo authored primarily by Yoo, which outlined an extremely narrow definition of torture. That opinion, which was signed by another Justice official, was formally disavowed after it was disclosed by the Washington Post.
Justice Department spokeswoman Tasia Scolinos would not comment on the report last night.
Staff writers Dafna Linzer and Peter Baker contributed to this report.
Spying and the Executive branch of U.S. government
From Wikipedia, the free encyclopedia, All links at site, Article Source
Franklin Roosevelt Administration: In 1940, the White House accidentally taped a conversation of President Franklin D. Roosevelt instructing a lower level aide to disseminate a rumor about his opponent Wendell Willkie having an extramarital affair: "We can't have any of our principal speakers refer to it, but the people down the line can get it out."
Johnson Administration: In 1964, President Lyndon B. Johnson sent 30 FBI agents to the Democratic National Convention in Atlantic City, N.J., to avert assassination attempts, and to monitor his political rival Robert Kennedy and civil rights activists. Johnson later also placed his Republican challenger, Barry Goldwater, under FBI surveillance, with a federal wiretap.
Nixon Administration: During the Richard Nixon administration, White House staffers compiled lists of names of political opponents, journalists who had criticized Nixon, and artists and actors (such as Jane Fonda and Paul Newman) who had dissented with Nixon policy, especially on the subject of Vietnam, with the intent of prompting Internal Revenue Service investigations. The full extent of Nixon's surveillance of private citizens solely on the basis of their dissent was not known until years after Nixon was forced to resign, as former staff members such as Charles Colson and John Dean began to disclose details.[citation needed] Nixon's Enemies List is the informal name of what started as a list of President Richard Nixon’s major political opponents compiled by Charles Colson, written by George T. Bell (assistant to Colson, special counsel to the White House) and sent in memorandum form to John Dean on September 9, 1971. The list was part of a campaign officially known as “Opponents List” and “Political Enemies Project.” The official purpose, as described by the White House Counsel’s Office, was to “screw” Nixon’s political enemies, by means of tax audits from the IRS, and by manipulating “grant availability, federal contracts, litigation, prosecution, etc.”
Ford Administration: During the Gerald Ford presidency, Deputy Assistant [War Criminal] Dick Cheney suggested in a now- infamous memo to Donald Rumsfeld that the White House use the United States Justice Department to conduct opposition research and retaliate against political opponents and critical journalists such as Seymour Hersh and the New York Times, arguing that the executive branch had the power to prosecute journalists as they saw fit, under the provisions of the Espionage Act of 1917.
Reagan Administration: In 1984, during the Ronald Reagan presidency, the Republican National Committee formed The Opposition Research Group, with its own budget of $1.1 million. These staff amassed information on eight Democratic presidential candidates based on data from voting records, Congressional Record speeches, media clippings and transcripts, campaign materials, all of which was stored on a computer for easy access. In this way the Reagan team was able to track inconsistencies and attack them. This original data base evolved into a network that linked information gleaned by Republicans in all 50 states, creating a master data base accessible to high-ranking Republican staff, even aboard Air Force One. Though this RNC database was accessible to both the Reagan White House and campaign team, no evidence has surfaced that U.S. federal dollars funded The Opposition Research Group or its efforts.
Clinton Administration: During the Bill Clinton administration, the "Filegate" scandal erupted when White House staffers said to be acting on the directions of First Lady Hillary Clinton improperly accessed 500 FBI files compiled for security checks of Reagan and Bush staffers in previous administrations. Craig Livingstone, said to be hired by Mrs. Clinton with dubious credentials, resigned amid public outcry. In testimony under oath during the Kenneth Starr special prosecutor's investigation, Mrs. Clinton stated that she had neither hired Livingstone nor improperly perused the files.
George W. Bush Administration: Two former opposition researchers for the RNC appointed to Justice Department posts, Timothy Griffin and Monica Goodling, were implicated in efforts to use data collected on Democratic-appointed federal attorneys as ground for dismissal. See Dismissal of U.S. attorneys controversy. See also Karl Rove. Also during this administration, Counterintelligence Field Activity (CIFA), an intelligence gathering arm of the Pentagon was disbanded in 2008, after investigations into the bribery activities directed at Duke Cunningham revealed that the U.S. government kept a sizeable database of information about 126 domestic peace activist groups, including Quakers, about 1,500 "suspicious incidents" including peace demonstrations outside armed forces recruiter offices, even though the groups posed no specified threat to national security. The program was known as Talon. About two years elapsed between the program's disbanding and the Post report. The Washington Post quoted an unnamed "official" as saying,"On the surface, it looks like things in the database that were determined not to be viable threats were never deleted but should have been," the official said. "You can also make the argument that these things should never have been put in the database in the first place until they were confirmed as threats."
Barack Obama Administration: In February 2009, Shauna Daly, a former opposition researcher for the Democratic National Committee was appointed as a researcher for the White House's Office of Legal Counsel. Daly was Barack Obama's deputy research director during the presidential campaign, spent much of the cycle rebutting viral online attacks on Obama's character and biography under the rubric of "Stop the Smears." Shortly thereafter, amid speculations that she would be conducting research against political opponents, she was reassigned as Research Director to the DNC. Politico.com reported on February 27, 2009 that "the counsel's office -- which doesn't face the sort of rapid-response demands that were common in the late Clinton years -- doesn't plan to fill the research post." The American Spectator reported on its "Washington Prowler" blog that Daly was posted in the White House Counsel's Office for "about a month," and thus had access to "reams of Bush administration documents related to such things as the firing s of U.S. Attorney, the use and internal debate over the USA PATRIOT Act, FISA and the Scooter Libby and Karl Rove investigations. The "Prowler" quoted "a DNC staffer" as saying, "She realized that she could do more with all the material she saw outside of the building than inside where she'd be bound by the rules and legalities of the White House Counsel's Office. Now she isn't. She's good at what she does; her time at the White House means we've got a mother load (sic) of material that will have Republicans scrambling. At least that's what we hope."
NONE OF THE ABOVE
should be a choice on Voter Ballots
Nobody for President

Valhalla... cartoon by Martin Rowson on Bilderberg, The Guardian, Friday 7 June 2013, Source
David Cameron has been accused of joining 'unaccountable clique of Davos men' at luxury hotel in WatfordDear Citizens of the World
I believe the time has come to reveal to you some of the perplexities you have faced in recent decades.
It is important to understand some of these things, so that you might know how to behave in the New Order now taking shape on this planet you call Earth. We want you to be able to become fully involved and integrated into our new society. After all, doing this is for your best interest.
First of all, it is best if you understand some of our purposes so that you may more fully cooperate. I cannot tell you the hard times you will face if you resist us.
We have ways of dealing with resisters and you are being told this now, since it is much too late to turn things around. The days of putting a stop to us have long since past.
We have full control of the earth and it's finances, along with control of major corporate media propaganda, and there is simply no way any nation or power can defeat us.
We have eyes in every level of government in every nation of the world. We know what is being planned, for our ears and eyes are ever present. State secrets are fully known to us.
U.S. corporate media are constantly accused of lying for their government by everyone; including foreign governments.
Oh, you silly people, of course we lie. In this way we can keep the people unbalanced and always facing controversy, which is very helpful to us. Have you not seen the talk show spectacles on FOX?
Some of you believe we are the liberals and the good people are the conservatives. In reality, both serve our purposes. Each camp merely serves with the stamp of our approval, but they are not allowed to present real issues.
For example, consider BP's Oil Spill. By creating controversy on all levels, no one knows what to do. So, in all of this confusion, we go ahead and accomplish what we want with no hindrance. If fact, we teach this within a fraternity in one of your nation's older universities.
Consider President George W. Bush of the United States. Even though he regularly broke every known check on his power, no one could stop him, and he went ahead, and did whatever we wanted him to do.
Congress and 'The People' had no power to stop him. He did what we wanted, since he knew, if he did not, because of his rather dark character, we could have him removed in an instant. I'd say it was, "Rather brilliant strategy on our part?"
You cannot take us to court because you can't see us and the courts are our servants as well. We run everything and you do not know who to attack. I must say this invisible hand is wonderfully devised without any known historical precedent on this scale. We rule the world and the world cannot even find out who is ruling them.
This is truly a wonderful thing. In our corporate media, we present before you exactly what it is we want you to do. Then, as if in a flash you, our little servants, obey!
We can send American or European troops to wherever we like, whenever we like, and for whatever purpose we like, and you dutifully go about our business and don't even look up to see the poisons we are spraying on you in the form of chemtrails. How much more evidence do you need?
We can make you desire to leave your homes and family and go to war merely at our command. We only need to present some nonsense to you from the president's desk, or on the evening news, and we can get you all fired up to do whatever we like. You can do nothing but what we put before you.
Your Vain Resistance
When any of you seek to resist us, we have ways of making you look ridiculous with corporate media, as we have done with all your movements to show the world how impotent any resistance is.
Look at what we did near Waco. Did the Davidian's little store of weapons help them?
We have generously taxed you and used that money to make such sophisticated weapons you can in no way compete. Your own money has served to forge the chains we bind you with; especially, since we are in control of all money.
Some of you think you may escape by buying some land in the country and growing a garden. Let me remind you that you still pay us ground rent. Oh, you may call it property taxes, but it still goes to us.
You see, you need money no matter what you do. If you fail to pay your ground rent to us, we will take your land and sell it to someone who will pay us. Do you think we cannot do this? And with your ground rent we pay for the indoctrination of your children in the public schools we have set up.
We want them to grow up well trained into the system of our thinking. Your children will learn what we want them to learn, when we want them to learn it, and you pay for it through your ground rent.
Those funds are also used for other projects we have in mind, like drilling for oil in the Gulf, and our contractors are paid handsomely for their work.
You may doubt that we own your children, or have such control, but you will find that we do. We can declare that you abuse your children, when you spank them, and have them confiscated. If they do not show up for school indoctrination, we can accuse you of neglect, thereby, giving them to us.
Your children are not yours. They are ours. You must inoculate them, you must bring them to our hospitals, if we decree, or we will take them from you. You know this and we know this.
Through our electronic commerce and iDevices we are able to see where you are, what you are buying, and how much you have to buy things with. Where do you suppose we come up with our monthly financial statistics?
Through the Internet, Telecoms, and other sources we can even know how you think and what you say. It is not especially important to us what you believe as long as you do what we say.
Your beliefs are nonsense anyway. But if you think you have a following, and we perceive that you might be somewhat dangerous to our agenda, we have ways to deal with you. Do you remember how we used Telecoms to spy for us?
We have a Pandora's box of mischief with which to snare you. We can have you in court so long, you will never get out. We can easily drain away all your assets over one pretext or another. We have an inexhaustible fund with which to draw from to pay our lawyers.
These lawyers are paid by you in the form of taxes. You do not have this vast supply of wealth. We know how to divide and conquer. Have we not brought down rulers of countries through our devices?
Do you think your tiny self will be any match for us?
Your Vain Organizations
Let us consider your religions, tea parties, and "moral majority."
The "moral majority" is neither moral nor is it in the majority. We have delighted to use this wet noodle of a movement to make ridiculous the Christian faith.
The silly men who run that organization always end up with egg on their faces. We have always put them in defense of themselves, as we have so successfully done with the NRA.
We can make it seem, by our corporate media propaganda, that the National Rifle Association is actually the new Al Qaeda.
Have we not turned the American conservative movement on its ear? If it serves our purposes we can use the conservatives to turn the liberals on their ear.
It makes no difference to us but it serves to make you believe there are two sides struggling for their particular position. This helps to make things seem fair and free, since everyone has a voice.
Actually, there is only one side now with all kinds of masks on, but you are unable to penetrate our purposes.
You see, we can do whatever we like and you can do nothing about it.
Does it not seem reasonable that you should simply obey and serve us? Otherwise, you get eaten up in the resistance you suppose that will liberate you.
You cannot be liberated ... Try to Imagine how you can.
We supply fuel for your cars and we can turn it off whenever we like, claiming there is some sort of fuel shortage. What if your car breaks down? You cannot get parts for it without us.
We supply all money you use and at any whim of our desire, we can stop the money supply, or ... cause a complete crash all together.
We can then order the president to declare all money worthless and that we will have to have new money. All of your stashes of cash will go up in smoke in an instant.
Don't you need food?
If necessary, we can cause a trucker's strike which would stop deliveries of food to your local store. We can starve you whenever we like. You only have food because we have provided it for you from our 'supermarket to the world' table.
During the great depression we controlled food and heaped mountains of it behind fences, to let it rot.
The hungry were then made to work in our labor camps, even though there was enough, and more, to feed them. Do you really think you can beat us?
You say you will hoard gold coins so you will still have money in the time of the crash. We can simply pass a law which outlaws the possession of gold as we have done in the past.
If we find gold in your possession, we would simply confiscate it, and put you in prison for breaking the law.
While in prison, or at one of our recently reconstructed FEMA camps, you would be required to work for one of our prison industries. We have so formed a picture of the labor camps in our prisons, these days, that no one seems to object to them.
We tell people that murderers should pay for their own keep.
No one seems to consider that we have the power to put tomato growers in prison.
We can pass laws that prohibit gardens, and then make up some scientific reason why you may only buy food from our sources.
If someone sees you growing tomatoes, they will report you to us, and then we will have you in our fields, working for us.
Oh, silly, stoned out of your minds, people, there is no escape for you, for since long before you were born, we were planning your capture.
Your teachers and ministers have been forming your thoughts for us, for generations now. You have been tricked into taking corporate drugs that were intended for short term usage, which have turned you into a nation of controlled mood zombies, and you have no idea how to pull out of our influence, short of suicide. Go ahead and commit suicide, it will only help us to deal with excessive population.
You cannot hurt us, find us, or even imagine what we are up to. I am throwing you these few crumbs only so that you may, if you have a little good sense, obey and follow our orders.
Your Controlled Mind
We run Hollywood. The movies such as Terminator and Armageddon, along with a great host of others, were simply created to get you thinking according to our directions.
You have been made to delight in violence, so that when we send you off to kill some bad man, we have put before you, you move without a whimper.
We have placed violent arcade games in your malls to prepare your young children's minds in the art of battle.
We have made you view our armies and police as the good forces, which cause you to submit to things that were unthinkable a few decades ago.
We totally orchestrated 9/11 and blamed it on somebody else using our corporate media and Congress, who we bought through our lobbies.
Think about it ... Congress spent about 60 million (60,000,000) of your income tax dollars, to discover if Monica swallowed (a little pre-reality show we dreamed up) and a little over 3 million dollars on the 9/11 Commission because we did not want an investigation of secret energy meetings or 9/11 to surface. See how easy it is to trick you?
Our artful programs are all designed to help you to submit and help the New World Order. Star Trek, and other such creations, have taught you to simply: obey orders from new international rulers.
Oh, silly people, you thought you were being entertained, while you were actually being educated. Dare I use the words, "brainwashed" or "mind control?" By the way, have you ever seen Star Wars?
What a masterpiece of mental manipulation. Humans confer with nondescript beasts of all shapes and sizes, and they confer in English.
I wonder where those space beasts learned English. Oh, the simple-ness of the mind of the citizen, for sh-he never considers sh-he is being taken into fairyland.
We placed advertisements for Star Wars everywhere you go. They were in WalMart, K-Mart, Taco Bell and a host of our institutions of corporate commerce.
There is something we want you to learn from Star Wars. Or, perhaps it could be said, there is something we do not want you to learn. Either way, we will have what we want in the whole affair.
Of course, to keep you off guard, we have instructed our elected officials to appear to be correcting the evil of our violence. Presidents often speak against violence in Hollywood movies.
This will not solve the problem, but it will make the people believe the problem is being worked on.
Sex and violence are the very best powers to use, to help us gain our advantage. How the people loathe to give up their sex and violence, so we place all they want before them. In this way, we keep them so occupied they do not have the integrity or brain-power to deal with the really important matters which are left entirely in our hands.
President Bush was very helpful to us. We knew of what character he was before we placed him as president. Exposing him was very helpful in adjusting the moral habits of the youth downward and this is too, our advantage.
Even more agreeable to us were the vain efforts of those who thought they could remove him against our will. He was useful to us and we control who is removed or not removed.
Excuse me if I seem to be mocking your system of beliefs, but they are rather outdated. Have you no eyes to see your vain liberties and your righteous pontifications are nothing before us? You can only do what we say you can do.
We remove presidents when we are ready and the leader we set up will be there until it serves us to have another. At that time we place our purposed politicians before you, and you vote for what we want.
In that way we give you the vain voting exercise in the belief you had something to do with placing your politicians in office.
Our Unfathomable Mysteries
Our recent war in Iraq had many purposes to it, but we do not speak of these things openly. We let the talk show hosts blather all sorts of nonsense, but none of it touches the core.
First of all, there is a wealth of natural resources on the planet we must have complete control of.
Iraq has large supplies of oil in its soil and oil is very helpful to our regime. Also, it suits us to keep this oil out of the hands of potential enemies.
For those who have not been helpful in getting these resources into our hands, we simply make things difficult until submission. Does anyone recall the word "sanction?"
We can reduce any proud nation to the level of humility we require from all people. For example if Zionist Israel does not sufficiently humble itself, we will take them to the world court, and have them charged with "war crimes." We made up that term; rather ingenious, don't you think?
How could there be such a thing as a war crime? The very nature of war is that the rules are off. It is so entertaining to watch the nations try to fight war according to the laws we have placed before them.
The only war crime there really is, involves the crime of being against us.
Anyone against us is violating our law and, as you have seen, when someone is for us, we do not care what they do. Was not Ariel Sharon a self professed murdering terrorist who tortured and horribly killed many of his enemies women and children? We made a hero of him. And what about the Bush administration? Are any of them in jail? No, they are still working for us and on your televisions, getting paid big salaries.
We observe no laws when it comes to war. We do what we want, when we want, and where we want.
We can starve nations to death, ruin civilizations, and commit other horrors for which we take our enemies to court. Look at one of our examples.
We bomb Iraq out of its wits. We can bomb rock throwing Palestinians out of their homes, poison their rivers and streams, turn off their electricity, making a grand crisis, and then we masterfully make it appear it is the fault of Islam.
It is the same way we made our inferno at Waco look like Mr. Koresh's fault. Then there was our chief villain, Saddam with all of his non existent weapons of mass destruction.
Bad men are a dime a dozen, we can conjure one up whenever it suits us, and ultimately, this is really quite funny when you think of it.
I am not one who is usually given to 'this sort' of humor, but I do catch myself laughing sometimes at the absolute absurdity of the notions we place before you, that you readily accept.
Do you wonder that the leaders of the world tremble at our presence? They know they have no power except the power we give them.
We have no fear of Russia or China, for we are already in full control of their system of things.
China knows we can freeze any number of their corporations in America and all of its capitol at the stroke of a pen. We use nations for what we want to use them for. Everyone knows that they must yield to us or die.
Fortunately, we have had a few resisters, such as Saddam, that have been helpful in showing world leaders what we will do to them if they do not submit.
There is only glory in following our purposes and doing what we say. If one does not, there will be a sad and tragic result.
I would have spared you of such an end, but, then, again, if you are not spared, it is of no consequence to us. We will use you to alleviate some of the overpopulation problem.
Your Silly Rebellions Against Us
Some of you have thought you could stop us by placing a bomb in one of our abortion clinics or in a government building.
Silly souls! How can that hurt us? All that does is give us an example to use so that we might place more controls, and heavy burdens, on the population.
We love it when you rebel and blow something up. You are our reason for making more laws against all those things, which might contribute to your freedom from us.
If someone did not blow something up on occasion, we would have no justification in placing more laws on you. Can't you see how impossible it is for you to resist us? The more you wiggle, the more we squeeze.
It is said our kingdom is the kingdom of money, but I must confess we are rulers of a kingdom of non-money.
You must see the humor in that statement. We have given you a piece of paper or some numbers on a computer screen that we have termed money.
It is backed up by nothing and proven by nothing, but what we say it is. We create it from nothing, we print it, we loan it, we give it its value, we take its value away. All things that have to do with money are in our hands.
Think of it, what is it that you can do against us without money? If you try to resist, we can cancel your credit or freeze your accounts. Your cash is easily confiscated.
We have made so many rules in the realm of living that you cannot live without money.
Camp on government land and you must move in two weeks. You cannot grow much of a garden in two weeks.
Many of our wilderness trails are entered by permit only.
We have passed laws that do not allow you to live in trailers over a certain period without moving to another location.
Have you not thought it ridiculous that we will allow a man to live in a box, full time, but we will not allow a man to live in a RV, full time, unless he is in a taxpaying campground? We want you to be in the system.
When you are buying a house, we not only receive the tax revenue to use for our purposes, but we gain large increases from the interest on the loan. You may pay for your house two or three times over from the interest alone. The interest is also taxed which is again placed for use in those sectors of influence we choose.
We do not want you to escape free and that is why we have made it as we have.
You are our property. We will not permit you to buy or sell unless you submit to our mark of authority.
If you go to court against us, we will wear you out, and in the end you will lose.
If you use violence, we will end up having you in one of our labor camps; more specifically called, prison industries.
You need our money, our entertainments, our fuel, and our utilities to function and if you don't have them, you feel deprived. By this, you are made to yield to our will.
You don't even know how to think anymore since we have thoroughly emasculated your religions and your faith in God. Now, you only have yourself ... and we have gotten 'that self' pretty well chasing its tail these days.
I hope this little note is sufficient to inform you what the new millennium is all about.
The 21st century is our century. You may stay if you do as you are told.
We have no intention of playing around with your so-called human rights or your so-called Constitution. These things were only used for our purposes, for a time. Your Constitution is a joke to us, and we can do with it what we please.
It probably never occurred to you, that years ago, your Constitution was used to refuse abortions. When we decided to have abortions legalized, we used the same Constitution to justify it.
Your human rights are what we say they are and your Constitution is what we say it is.
We have only used this phrase of "human rights" to keep things sufficiently in turmoil. The more things are unsettled, the better we like them, until we have everything in complete servitude.
This little letter may offend some of you, because it is presented so plainly, but that truly is no concern of ours. In simple terms, to quote our boy Dick Cheney,
"Go F**k Yourself!" says Dick Cheney, June 2004
Have a nice day...
[permalink]
Google Is Evil ~ Breaks promise, offers NSA viewed Search, Maps, YouTube, email, etc. ~ Sells out users
Google Waze acquisition needs antitrust probe --
Consumer WatchdogUS pressure group asks Department of Justice to investigate search giant's $1.3bn takeover of Israel-based traffic app
Charles Arthur, technology editor, guardian.co.uk, Wednesday 12 June 2013 17.43 EDT, Article Source
Google has bought the mapping app Waze for $1.3bn. Photograph: Martin Keene/PAThe US Department of Justice [Ed. Note: Now we will see whose side DoJ is on; Corporate, or the People] has been urged to block Google's $1.3bn acquisition of the traffic app Waze, on antitrust grounds.
John Simpson, the privacy project director of Consumer Watchdog, a US pressure group, has written a letter to the DoJ warning that allowing the acquisition "would remove the most viable competitor to Google Maps in the mobile space".
Simpson writes that "Google already dominates the online mapping business" and alleges that the company "was able to muscle its way to dominance by unfairly favouring its own services" ahead of competitors, through its power in the search business.
If the DoJ takes up the case, it would add to a growing number of antitrust investigations in progress against Google. In the US the Federal Trade Commission is investigating whether the company has broken antitrust rules in its sales of online display ads, while in Europe its dominance of search is the target of a long-running European Commission investigation in which it has been told to revise its presentation of search results. Simpson has also asked the FTC to determine whether it should investigate the takeover.
Google and Waze, from Israel, announced the purchase on Tuesday after acquisition talks which are said to have also involved Facebook, which had been interested in Waze's social element.
Waze's chief executive, Noam Bardin, said in a blogpost about the takeover that he had considered whether to seek a public listing, to keep the company independent, but added that "an IPO [initial public offering] often shifts attention to bankers, lawyers and the happiness of Wall Street, and we decided we'd rather spend our time with you, the Waze community."
Waze, which has nearly 50 million users worldwide, is a free smartphone app that provides driving directions and crowdsourced feedback which can warn of traffic problems. Google's Android mobile system has hundreds of milllions of users, and also offers free navigation. But Waze users specifically choose to use the app, making them more loyal and their data more valuable.
Google said in a blogpost about the buyout that Waze will "operate separately for now".
The largest rival to Google in the mobile space may be Apple, which last year removed Google as the default mapping app from its iPhone, replacing it with its own iOS 6 Maps app. Apple says it has hundreds of millions of iPhone users worldwide, 93% of whom are using iOS 6. But it is unclear how many use the iOS 6 Maps app for navigation, after it was widely criticised on release. Apple buys some traffic data from Waze for use in the app.
Consumer Watchdog is concerned that Google and Waze will merge their operations, which "will allow Google access to even more data about online activity in a way that will increase its dominant position on the internet". It pointed to the fact that the FTC's approval of Google's DoubleClick display business acquisition in 2008 "tipped Google to a search advertising monopoly" – which the FTC is now investigating.
Internet anonymity is the height of chic
In this age of information overload, internet exhibitionism and NSA snooping, is it possible to make yourself unGoogleable? And does it earn you added credibility, as fashion designer Phoebe Philo and bands such as !!! suggest?
Stuart Jeffries, The Guardian, Wednesday 12 June 2013 12.40 EDT, Article Source
Googleproof'The chicest thing," said fashion designer Phoebe Philo recently, "is when you don't exist on Google. God, I would love to be that person!"
Philo, creative director of Céline, is not that person. As the London Evening Standard put it: "Unfortunately for the famously publicity-shy London designer – Paris born, Harrow-on-the-Hill raised – who has reinvented the way modern women dress, privacy may well continue to be a luxury." Nobody who is oxymoronically described as "famously publicity-shy" will ever be unGoogleable. And if you're not unGoogleable then, if Philo is right, you can never be truly chic, even if you were born in Paris. And if you're not truly chic, then you might as well die – at least if you're in fashion.
If she truly wanted to disappear herself from Google, Philo could start by changing her superb name to something less diverting. Prize-winning novelist AM Homes is an outlier in this respect. Google "am homes" and you're in a world of blah US real estate rather than cutting-edge literature. But then Homes has thought a lot about privacy, having written a play about the most famously private person in recent history, JD Salinger, and had him threaten to sue her as a result.
And Homes isn't the only one to make herself difficult to detect online. UnGoogleable bands are 10 a penny. The New York-based band !!! (known verbally as "chick chick chick" or "bang bang bang" – apparently "Exclamation point, exclamation point, exclamation point" proved too verbose for their meagre fanbase) must drive their business manager nuts. As must the band Merchandise, whose name – one might think – is a nominalist satire of commodification by the music industry. Nice work, Brad, Con, John and Rick.
Phoebe Philo: anonymity would be helped by a less distinctive name. Photograph: Gareth CattermoleIf Philo renamed herself online as Google Maps or @, she might make herself more chic.
Welcome to anonymity chic – the antidote to an online world of exhibitionism. But let's not go crazy: anonymity may be chic, but it is no business model. For years XXX Porn Site, my confusingly named alt-folk combo, has remained undiscovered. There are several bands called Girls (at least one of them including, confusingly, dudes) and each one has worried – after a period of chic iconoclasm – that such a putatively cool name means no one can find them online.
But still, maybe we should all embrace anonymity, given this week's revelations that technology giants cooperated in Prism, a top-secret system at the US National Security Agency that collects emails, documents, photos and other material for secret service agents to review. It has also been a week in which Lindsay Mills, girlfriend of NSA whistleblower Edward Snowden, has posted on her blog (entitled: "Adventures of a world-traveling, pole-dancing super hero" with many photos showing her performing with the Waikiki Acrobatic Troupe) her misery that her fugitive boyfriend has fled to Hong Kong. Only a cynic would suggest that this blog post might help the Waikiki Acrobating Troupe veteran's career at this – serious face – difficult time. Better the dignity of silent anonymity than using the internet for that.
Furthermore, as social media diminishes us with not just information overload but the 24/7 servitude of liking, friending and status updating, this going under the radar reminds us that we might benefit from withdrawing the labour on which the founders of Facebook, Twitter and Instagram have built their billions. "Today our intense cultivation of a singular self is tied up in the drive to constantly produce and update," argues Geert Lovink, research professor of interactive media at the Hogeschool van Amsterdam and author of Networks Without a Cause: A Critique of Social Media. "You have to tweet, be on Facebook, answer emails," says Lovink. "So the time pressure on people to remain present and keep up their presence is a very heavy load that leads to what some call the psychopathology of online."
Internet evangelists such as Clay Shirky and Charles Leadbeater hoped for something very different from this pathologised reality. In Shirky's Here Comes Everybody and Leadbeater's We-Think, both published in 2008, the nascent social media were to echo the anti-authoritarian, democratising tendencies of the 60s counterculture. Both men revelled in the fact that new web-based social tools helped single mothers looking online for social networks and pro-democracy campaigners in Belarus. Neither sufficiently realised that these tools could just as readily be co-opted by The Man. Or, if you prefer, [Schmuck] Mark Zuckerberg.
Not that Zuckerberg is the devil in this story. Social media have changed the way we interact with other people in line with what the sociologist Zygmunt Bauman wrote in Liquid Love. For us "liquid moderns", who have lost faith in the future, cannot commit to relationships and have few kinship ties, Zuckerberg created a new way of belonging, one in which we use our wits to create provisional bonds loose enough to stop suffocation, but tight enough to give a needed sense of security now that the traditional sources of solace (family, career, loving relationships) are less reliable than ever.
Mark Zuckerberg, chief executive [Schmuck] officer and founder of Facebook: created a new way of belonging. Photograph: BloombergAs Malcolm Gladwell wrote in Small Change: Why the revolution will not be tweeted, this new sociability was something of a boon. "There is strength in weak ties ... Our acquaintances – not our friends – are our greatest source of new ideas and information. The internet lets us exploit the power of these kinds of distant connections with marvellous efficiency. It's terrific at the diffusion of innovation, interdisciplinary collaboration, seamlessly matching up buyers and sellers, and the logistical functions of the dating world." But for Gladwell, weak ties like this were no panacea: "The evangelists of social media don't understand this distinction; they seem to believe that a Facebook friend is the same as a real friend and that signing up for a donor registry in Silicon Valley today is activism in the same sense as sitting at a segregated lunch counter in Greensboro in 1960."
The dream of online anonymity revives an old romantic hope – that we might disappear ourselves, like Salinger, from an unfeeling world that is doomed to intrude upon and misconstrues our authentic selves in equal measure. Better anonymity than the lie-dream of new sociability. Only in private can we truly be ourselves. Viewed thus, the internet is less a tool than an onerous machine for hype and lies, when all these bands and fashion desginers want is to let their artistic genius express itself silently, anonymously – without numpties sicking up opinions on their oeuvre.
The internet, at worst, disconnects us from ourselves, cutting us off from what really matters in life. It's an old theme, this notion of industrial and post-industrial society imposing false consciousness on the innocent, and one that is given a new resonance in the information age where the online clamour for attention makes us dream of cancelling our broadband contract and going to live in the woods on berries. Hence, the popularity of Sylvain Tesson's memoir Consolations of the Forest, about a man who decides to live like a hermit in Siberia for six months. It speaks to our desire to escape civilisation – at least for a while. (Six months is about enough. After that, any sentient being would go postal. After six months we can return, post our pictures on Instagram, change our Facebook status, watch what we recorded on our hard drive and get our agent to sell our memoir.)
This dream of going anonymous overlaps with another paean to social disconnection. In her book Quiet, Susan Cain rails against our excessive and misguided respect for extroverts. Before the industrial revolution, she writes, American self-help books extolled character. Nowadays, personality is venerated. That cult of personality is enabled by social media, where extrovert self-presentation is what gets you friended and followed. The noisome extroverts yucking up their nothingy conversations on buses while the rest of us try to get to grips with early Wittgenstein (why haven't introverts invented a volume control for extroverts if they are, as Cain suggests, so clever?) have their parallel on Twitter. After Quiet: The Power of Introverts in a World that Can't Stop Talking, which was, in Jon Ronson's description, "the Female Eunuch for anxious nerds", we need another book: Unembraceable You: The Pleasures of Disconnecting from an Online World Gone Nuts – a God Delusion for recovering geeks.
But the dream of anonymity is not just about conquering addiction, nor about silencing cyberspace's extroverts, but also about eluding the tentacles of power before they disappear into your proverbial underpants with malice aforethought. In cyberspace, our every keystroke is monitorable, tradable, if not traded, by corporations and exchangeable, if not exchanged, by security agencies.
Hard to Google: Nic Offer of the band !!! Photograph: Startraks Photo/Rex FeaturesThis totalitarian vision of how the internet works may seem fanciful, but it was once envisaged as a good thing. In the 1930s, HG Wells wrote of a "world brain" through which "the whole human memory can be ... made accessible to every individual". Today, perhaps we have that world brain, and it is called Google. Viktor Mayer-Schönberger, professor of internet governance and regulation at the University of Oxford's Internet Institute, sounds an Orwellian note about this: "Quite literally, Google knows more about us than we can remember ourselves." No wonder some dream of slipping under Google's radar.
In the 19th century, Jeremy Bentham envisaged a prison called a panopticon in which guards could watch prisoners without them knowing whether they were being watched. In the 20th century, Michel Foucault argued that the model of the panopticon was used more abstractly to exercise control over society. In the 21st century, Mayer-Schönberger argues that the panopticon now extends across time and cyberspace, making us act as if we are watched even if we are not.
In his book Delete: The Virtue of Forgetting in the Digital Age, Mayer-Schönberger points out that the digital revolution makes it is easier to keep everything – the drunken email you sent your boss, the wacky photo you put on Facebook – rather than go through the palaver of deciding what to consign to oblivion. Though, really, we should do that hard work – this at least was the point of the professor's book. We must all kick over our traces or face the consequences.
What is most striking about what Phoebe Philo says about the desirability of online anonymity is that she couches it in terms of the fashionista's holy grail – chic. If she's right, and I think she may well be, this means we need a revolution in our thinking not just about social media, but about economics.
Ever since Thorsten Veblen wrote The Theory of the Leisured Class in 1899, economic status has been signaled by conspicuous consumption and grandstanding leisure. That's why you moored your yacht off Rhodes and invited Peter Mandelson and George Osborne over to stay, thus proving that not only were you a Russian billionaire but you knew how to flaunt that status to best effect. Status on social media was demonstrated similarly by conspicuous consumption's online counterpart: conspicuous presence. Status-seeking cybernauts sought more Twitter followers than Justin Bieber, Lady Gaga and Barack Obama combined. Zuckerberg facilitated an egalitarian revolution whereby high status could be demonstrated by those without money: social capital, unlike real capital, transcended monetary wealth.
But anonymity chic means we need to rethink economics in light of the collapse of the social networking model of human worth. Anonymity chic confounds the idea that the more overbearing your online presence, the higher your status. Rather, in the new economy of self-presentation, oversupply of yourself reduces your market value. To be chic, by contrast, involves withholding yourself – and in extremis making yourself anonymous, invisible, unavailable to the masses.
Online status didn't used to be like this. If you were Stephen Fry, you checked into your St Petersburg hotel room and tweeted the view of the Neva before unpacking your toothbrush. You made an investment, surrendering your privacy in return for the status boost of being followed by strangers. Philo reverses this economics: what was once high status became vulgar self-delusion and self-betrayal.
But there is a philosophical paradox in the anonymity chic. If to be chic is to be anonymous, how will anyone know that you're chic? How can you prove your status while not expressing it? To be chic minimally requires being seen or at least noticed.
Most of those who want anonymity don't seek to be chic. Rather, they sound like backwoods libertarians – the kind of people who hate government, think taxes are unconscionable, the National Grid Hitlerian, and that with every keystroke you die a little (think: Ron Swanson in Parks and Recreation). For example, one of the many anonymous persons who list ways to fly under the radar of online surveillance explains how to go about it: "If you are going to be using the internet in your secret lifestyle, you should do everything you can to secure yourself online. This means using PGP (encryption software) when emailing people (and using an email account that can not be traced to you directly), and, most importantly, it means saying nothing online that you would not be prepared to see on the front page of the newspaper."
If only the woman who gloatingly tweeted that she'd knocked over a cyclist had read it. But it's also bad advice, since it suggests that there is such a thing as a secret lifestyle, unGoogleable and pure, untarnished by the grubby accommodations of living in society. Geert Lovink thinks such advice is a delusion: "You should not promote anonymity as a solution – then you're fooling yourself and others. It is always possible for any authority to track you down. There's no such thing as absolute anonymity."
What then should we do to resist information overload, cyber slavery, toxic trolling, intolerable corporate and state snooping apart from becoming anonymous? Lovink counsels self-mastery, and learning how to reduce the internet's impact on our lives. There is, he says, a parallel with other technologies. "We are no longer impressed by vacuum cleaners and refrigerators." he says. "They don't foreground themselves so much." The internet needs to be similarly disenchanted. Perhaps, but that all sounds nebulous – and certainly not as chic as making oneself unGoogleable.
NSA surveillance played little role
in foiling terror plots, experts sayObama administration says NSA data helped make arrests in two important cases – but critics say that simply isn't true
Ed Pilkington in New York and Nicholas Watt in London, guardian.co.uk, Wednesday 12 June 2013 10.51 EDT, Article Source
A new NSA data farm is set to open in the fall in Bluffdale, Utah. A former CIA agent said:
'[Data-mining] played no role in the Headley case.' Photograph: George Frey/Getty ImagesLawyers and intelligence experts with direct knowledge of two intercepted terrorist plots that the Obama administration says confirm the value of the NSA's vast data-mining activities have questioned whether the surveillance sweeps played a significant role, if any, in foiling the attacks.
The defence of the controversial data collection operations, highlighted in a series of Guardian disclosures over the past week, has been led by Dianne Feinstein, chairwoman of the Senate intelligence committee, and her equivalent in the House, Mike Rogers. The two politicians have attempted to justify the NSA's use of vast data sweeps such as Prism and Boundless Informant by pointing to the arrests and convictions of would-be New York subway bomber Najibullah Zazi in 2009 and David Headley, who is serving a 35-year prison sentence for his role in the 2008 Mumbai attacks.
Rogers told ABC's This Week that the NSA's bulk monitoring of phone calls and internet contacts was central to intercepting the plotters. "I can tell you, in the Zazi case in New York, it's exactly the programme that was used," he said.
A similar point was made in anonymous briefings by administration officials to the New York Times and Reuters.
But court documents lodged in the US and UK, as well as interviews with involved parties, suggest that data-mining through Prism and other NSA programmes played a relatively minor role in the interception of the two plots. Conventional surveillance techniques, in both cases including old-fashioned tip-offs from intelligence services in Britain, appear to have initiated the investigations.
In the case of Zazi, an Afghan American who planned to attack the New York subway, the breakthrough appears to have come from Operation Pathway, a British investigation into a suspected terrorism cell in the north-west of England in 2009. That investigation discovered that one of the members of the cell had been in contact with an al-Qaida associate in Pakistan via the email address sana_pakhtana@yahoo.com.
British newspaper reports at the time of Zazi's arrest said that UK intelligence passed on the email address to the US. The same email address, as Buzzfeed has pointed out, was cited in Zazi's 2011 trial as a crucial piece of evidence. Zazi, the court heard, wrote to sana_pakhtana@yahoo.com asking in coded language for the precise quantities to use to make up a bomb.
Eric Jurgenson, an FBI agent involved in investigating Zazi once the link to the Pakistani email address was made, told the court: "My office was in receipt – I was notified, I should say. My office was in receipt of several email messages, email communications. Those email communications, several of them resolved to an individual living in Colorado."
Michael Dowling, a Denver-based attorney who acted as Zazi's defence counsel, said the full picture remained unclear as Zazi pleaded guilty before all details of the investigation were made public. But the lawyer said he was sceptical that mass data sweeps could explain what led law enforcement to Zazi.
"The government says that it does not monitor content of these communications in its data collection. So I find it hard to believe that this would have uncovered Zazi's contacts with a known terrorist in Pakistan," Dowling said.
Further scepticism has been expressed by David Davis, a former British foreign office minister who described the citing of the Zazi case as an example of the merits of data-mining as "misleading" and "an illusion". Davis pointed out that Operation Pathway was prematurely aborted in April 2009 after Bob Quick, then the UK's most senior counter-terrorism police officer, was pictured walking into Downing Street with top secret documents containing details of the operation in full view of cameras.
The collapse of the operation, and arrests of suspects that hurriedly followed, came five months before Zazi was arrested in September 2009. "That was the operation that led to the initial data links to Zazi – they put the clues in the database which gave them the connections," Davis said.
Davis said that the discovery of the sana_pakhtana@yahoo.com email – and in turn the link to Zazi – had been made by traditional investigative work in the UK. He said the clue-driven nature of the inquiry was significant, as it was propelled by detectives operating on the basis of court-issued warrants.
"You can't make this grand sweeping [data collection] stuff subject to warrants. What judge would give you a warrant if you say you want to comb through vast quantities of data?"
Legal documents lodged with a federal court in New York's eastern district shortly after Zazi's arrest show that US counter-intelligence officials had been keeping watch over him under targeted surveillance with the warranted approval of the special intelligence court. During the course of the prosecution, the US served notice that it would be offering evidence "obtained and derived from electronic surveillance and physical search conducted pursuant to the Foreign Intelligence Surveillance Act of 1978 (Fisa)."
Feinstein and Rogers have also pointed to the case of David Headley, who in January was sentenced to 35 years in jail for having made multiple scouting missions to Mumbai ahead of the 2008 terrorist attacks that killed 168 people. Yet the evidence in his case also points towards a British tip-off as the inspiration behind the US interception of him.
In July 2009, British intelligence began tracking Headley, a Pakistani American from Chicago, who was then plotting to attack Danish newspaper Jyllands-Posten in retaliation for its publication of cartoons of the prophet Mohammed. Information was passed to the FBI and he was thereafter, until his arrest that October, kept under targeted US surveillance.
An intelligence expert and former CIA operative, who asked to remain anonymous because he had been directly involved in the Headley case, was derisive about the claim that data-mining sweeps by the NSA were key to the investigation. "That's nonsense. It played no role at all in the Headley case. That's not the way it happened at all," he said.
The intelligence expert said that it was a far more ordinary lead that ensnared Headley. British investigators spotted him when he contacted an informant.
The Headley case is a peculiar choice for the administration to highlight as an example of the virtues of data-mining. The fact that the Mumbai attacks occurred, with such devastating effect, in itself suggests that the NSA's secret programmes were limited in their value as he was captured only after the event.
Headley was also subject to a plethora of more conventionally obtained intelligence that questions the central role claimed for the NSA's data sweeps behind his arrest. In a long profile of Headley, the investigative website ProPublica pointed out that he had been an informant working for the Drug Enforcement Administration perhaps as recently as 2005. There are suggestions that he might have then worked in some capacity for the FBI or CIA.
Headley was also, ProPublica found, the subject of several inquiries by agents of the FBI-led Joint Terrorism Task Force. A year before the Mumbai attacks his then wife, Faiza Outalha, reported on him to the US embassy Islamabad, saying he was on a secret mission in India and was a "drug dealer, terrorist and spy".
NSA surveillance:
Guardian poll finds majority in US want greater oversightPoll finds two-thirds of Americans want NSA's role reviewed, and 56% find current congressional oversight insufficient
Harry J Enten and Ed Pilkington in New York, guardian.co.uk, Thursday 13 June 2013 08.11 EDT, Article Source
Senator Jeff Merkley waves his Verizon cellphone as he questions NSA director
Keith Alexander on Wednesday. Photograph: Charles Dharapak/APA clear majority of Americans are concerned about the actions and operations of the National Security Agency (NSA) and want the intelligence body to be subjected to further review and greater congressional oversight, a Guardian poll has found.
In the opinion poll, conducted for the Guardian by Public Policy Polling, two-thirds of voters who responded said that in the light of a week-long series of leaked disclosures about the NSA's surveillance activities they wanted to see its role reviewed. Only 20% thought there were no grounds for further review, while 14% could not say either way.
In a separate question, 56% said that they believed Congress had failed to conduct sufficient oversight of the NSA, which is a branch of the department of defence charged with collecting and analysing national security information. Recent disclosures by the Guardian have unveiled the NSA's vast data-mining programs of telephone records and other digital communications involving millions of Americans.
The revelations originated with a former contract worker for the NSA, Edward Snowden, who said he decided to blow the whistle on the agency's digital dragnet operations because he wanted the public to know about the "federation of secret law, unequal pardon and irresistible executive power that rule the world". The poll suggests that his stated ambition has, at least for now, been achieved: some 90% of those surveyed said they had heard about the recent news involving the NSA's collecting and storing of Verizon phone records and gaining access to data from major internet companies, and 61% said they believed a fresh debate was needed over the balance between privacy and security.
The poll shows that a substantial majority of Americans – 60% – want their government to be more open about its data collection so that the public can understand what is going on. A much smaller proportion, only 35%, said they agreed that the government needs to keep the data it collects secret in order to protect national security.
Congress oversight poll. Photograph: guardian.co.ukMost American voters – 58% – are also fearful about private firms acting as contractors to the defence department have too much access to state secrets. Only 8% of respondents said they thought government contractors had too little access.
Snowden worked most recently for the private firm Booz Allen Hamilton, doing contract work through that company for the NSA in Hawaii.
Despite these areas of relative agreement, Americans are much less firm in their opinions when asked about official data gathering activities. Some 44% of respondents approve of the government collecting internet and/or phone data from them, and a relatively close 50% think it is a bad idea.
Similar results were found when the sample was asked what they thought of the government's collection of metadata, with 40% approving and a 50% disapproving. The term was explained in the survey as being the collection of characteristics such as length of a phone call and who called whom but not the content of the phone call itself.
The Obama administration has attempted to justify the NSA's actions in the light of the recent leaks by saying the agency only skims metadata information rather than listening into conversations. Advocates of greater openness in official affairs say that this is misleading.
"It's not surprising that people are more ambivalent about metadata because many people have little knowledge about how deeply personal metadata can be. It can be a window into every aspect of your life – who you are speaking to, for how long, where from – it's a database of everything you do," said Kurt Opsahl, senior staff attorney at the campaign for online rights, the Electronic Frontier Foundation.
One group more than any other has intense qualms about the expansion of executive powers in data sweeping: young Americans. Among 18- to 29-year-olds, a commanding 81% want to see the NSA's role reviewed and 69% think there needs to be a wider debate about privacy versus security.
The poll also indicates that the disclosures could have political ramifications for Obama. Nearly half – 48% – of American voters say they are less likely to support Obama because of the recent revelations on data-gathering, while only 17% say they are more likely to support him.
This split is less pronounced among Obama's Democratic base, with 25% of Democrats saying they were more likely to support Obama against 28% who said the opposite. Obama's Democratic base, especially among black voters, generally expressed less concern about the NSA disclosures than Republican-leaning voters.
For instance, 68% of those identifying themselves as Republican said they thought Congress had not done enough oversight of the agency, while only 40% of Democrats were similarly worried.
There was one area, however, of bipartisan agreement. Both Democratic- and Republican-leaning respondents replied by 59% that they felt the government needed to be more open about its data collection activities.
• Public Policy Polling surveyed 512 registered voters between 10-11 June 2013 on behalf of the Guardian. The firm did not use cell phones to reach the sample.
If You've Done Nothing Wrong...
Then you've nothing to worry about
Steve Bell on William Hague's statement about GCHQ and the secret NSA operation
The Guardian, Monday 10 June 2013 17.47 EDT, Cartoon Source ... Comments
Arrest Bush Administration Baby Killers,
Not Whistleblowers Who Protect U.S. Citizens!It was widely known before the Iraq war over 50% of the Iraqi population were children under the age of 15, thus... Bush's illegal Iraq war began with this ...
Sheer Act of Cowardice
Do the above Baby Killers have "SOMETHING TO WORRY ABOUT?
NO, they used their criminal Attorney Generals and Judicial system to GET AWAY WITH MURDER![Spoiler: Politicians (it doesn't matter which side) lie !!! Republican War Criminal George W Bush and his War Criminal administration officials said, repeatedly, warrantless surveillance (Telecom Spy programauthorized by pResident Bush) is carefully targeted to include only international calls and e-mails into or out of the USA, and only those involving at least one party suspected of being a member or ally of al-Qaeda or a related terror group; indicating the Obama Administration harbors criminals and is violating citizen rights?
Spoiler: Politicians (it doesn't matter which side) that make the most noise on television about spying on U.S. citizens; or brush it off entirely, (for the most part) voted for an Unconstitutional Patriot Act (without reading it), voted for an illegal Iraq War (killing innocent children, women, civilians, and military) based on known lies issued by Zionist Neocons (who were the first people to use the term Weapons of Mass Destruction) who could face War Crime charges, if there was honest government. Worst of all is how these lying, chickenhawk coward politicians treat U.S. Military and Military Veterans (FWIW: 1/3 of American Homeless are Vietnam Veterans and Iraq Veterans are still not being taken care of!)]
If Edward Snowden "committed an Act of Treason,"
What CRIME did DIANNE FEINSTEIN commit?Dianne Feinstein, chairman of the national intelligence committee, has ordered the NSA to review how it limits the exposure of Americans to government surveillance. But she made clear her disapproval of Snowden. "What he did was an act of treason," she said. [Source]
The following is taken from: Investigate & Jail Neocon War Criminals
[Click to read complete text of articles]Senator Feinstein's Iraq Conflict
As a member of the Military Construction Appropriations subcommittee, Sen. Feinstein voted for appropriations worth billions to her husband's firms; involving Insider Information, Congressional Record of questionable intersections between Feinstein's legislative duties and her financial interests, Perini publicly identified one of its main business competitors as Halliburton, $2.5 billion worth of contracts tied to the worldwide expansion of American militarism, URS and McClellan, and As the arbiter of Senate rules on ethics, it is incumbent on Feinstein to provide the public with an explanation of why she did not recuse herself from acting on MILCON details that served her financial interests, and why she failed to resign from the subcommittee after she recognized the potential for conflicts of interest, which, unfortunately, materialized in an obvious way and over a long period of time. [Click to read complete text]
Project Censored Top 25 of 2008 # 23
Feinstein’s Conflict of Interest in Iraq
Dianne Feinstein--the ninth wealthiest member of congress--has been beset by monumental ethical conflicts of interest. As a member of the Military Construction Appropriations Subcommittee (MILCON) from 2001 to the end of 2005, Senator Feinstein voted for appropriations worth billions of dollars to her husband’s firms. [Click to read complete text]
Project Censored Top 10 of 1998
Little Known Federal Law
Paves Way for National Identification Card***[Mark of the Beast?]***
http://www.projectcensored.org/ ~ Article Source
The 1996 Illegal Immigration Reform and Responsibility Act has created a legal framework for mandating a national identification card for all Americans. Theoretically, this would be for the purpose of preventing non-citizens from using various public services, or gaining employment. One aspect of the law would make employers run potential employees' ID cards through a machine linked to the Social Security Administration, which could then approve or deny the applicant for employment. The government could actually gain veto power over private employment.
States are offered $5 million per year grants if they want to try to institute one of three ID programs. Additionally, federal agencies may only accept driver's licenses which fit the new specifications-- they must have the owner's fingerprints digitally encoded on a magnetic strip on the card. Georgia actually passed a bill instituting this ID program, but it was repealed after massive public outcry.
The author of this bill is California Senator Diane Feinstein, who wants a plan to be "immediately implement[ed]" that would force all Americans to carry an ID card with a "magnetic strip on it on which the bearer's unique voice, retina pattern, or fingerprint is digitally encoded. [Mark of the Beast?]
Dianne Feinstein,
symbol of the worthless Beltway DemocratUnderstanding the Bush-enabling and base-hating behavior of the "liberal" California Democrat reveals much about the failures of the 2007 Congress.
by Glenn Greenwald, Sunday, Sep 23, 2007 03:21 AM PDT, Article Source
In the wake of the series of profound failures that define the 2007 Democratic Congress, there is much debate over what accounts for this behavior. There are almost 300 "Congressional Democrats" and they are not a monolithic group. Some of them are unrelenting defenders of their core liberal political values and some are committed to providing meaningful opposition to the radicalism and corruption of the Bush administration. But as the sorry record of the 2007 Congress conclusively proves, they are easily outnumbered in the House and Senate -- especially the Senate -- by Bush-enabling and Bush-supporting Democrats.
The standard excuse offered by many apologists for Bush-enabling Democrats -- that they support the Bush agenda and capitulate to the right-wing noise machine due to political fear of being depicted as too liberal or "soft on terror" -- is clearly inapplicable to many, if not most, of the enablers. California's Democratic Senator Dianne Feinstein provides a perfect case study for understanding why the Congress has done virtually nothing to oppose the most extreme Bush policies, while doing much actively to support it.
Feinstein represents a deep blue state and was just easily re-elected to her third term last year. She won't run for re-election, if she ever does, until 2012, when she will be 80 years old. Her state easily re-elected a Senator, Barbara Boxer, with a much more liberal voting record than Feinstein's. Political fear cannot possibly explain her loyal support for the Bush agenda on the most critical issues decided by the Senate.
Additionally, Feinstein is a 74-year-old divorced Jewish woman currently on her third husband, and it is thus extremely unlikely that she harbors any hopes of running in the future on a national ticket. She has as secure a political position as any politician in the country. Whatever explains what she does, it has nothing to do with "spinelessness" or fear. What would she possibly fear?
And yet, her votes over the last several years, and especially this year after she was safely re-elected, are infinitely closer to the Bush White House and her right-wing Senate colleagues than they are to the base of her party or to the constituents she allegedly represents. Just look at what she has done this year on the most critical and revealing votes:
* Voted in FAVOR of funding the Iraq War without conditions;
* Voted in FAVOR of the Bush White House's FISA bill to drastically expand warrantless eavesdropping powers;
* Voted in FAVOR of condemning MoveOn.org;
* Cast the deciding vote in August on the Senate Judiciary Committee in FAVOR of the nomination of far right Bush nominee Leslie Southwick to the 5th Circuit Court of Appeals.
In 2006, Feinstein not only voted in favor of extending the Patriot Act without any of the critical safeguards sought by Sen. Feingold, among others, but she was one of the most outspoken Democratic proponents arguing for its extension ("I have never been in favor of allowing any provisions of the Patriot Act to expire."). Also in 2006, she not only voted in favor of amending the Constitution to outlaw flag burning, but was, as she proudly described herself, "the main Democratic sponsor of this amendment."
In October of 2002, she (naturally) voted to authorize President Bush to use military force to invade Iraq. She now self-servingly claims that she "regrets" the vote and was tricked by the Bush administration into believing Saddam had WMDs, yet Scott Ritter has disclosed: "This is far different from the statement Feinstein made to me in the summer of 2002, when she acknowledged that the Bush administration had not provided any convincing intelligence to back up its claims about Iraqi WMD." And when it was revealed in August of this year that Awad Allawi had hired the most influential GOP lobbying firm to help oust Prime Minister Maliki, there was Sen. Feinstein leading the way in demanding Maliki's ouster.
Time and again, not only does she vote in favor of the most right-wing aspects of the Bush agenda, she uses her alleged expertise in areas of intelligence to pressure or give comfort to other Democrats wanting to do the same. Several of the 16 Democratic Senators who voted in favor of Bush's FISA bill in August, such as Jim Webb, cited assurances by Feinstein that she had obtained Secret Information as a member of the Intelligence Committee which proved how necessary this bill was. Similarly, as a member of the Intelligence Committee, she was one of the Democratic leaders urging the confirmation of Gen. Michael Hayden as CIA Director notwithstanding the central role he played as NSA Director in Bush's illegal surveillance programs.
Her primary allegiance is to the Beltway power system and her overwhelming affection is reserved for Beltway power brokers who are her true colleagues and constituents. That is particularly true of right-wing members of the defense and intelligence communities. Here, for instance, is the praise she oozed for the illegal-surveillance-implementing Gen. Hayden when urging his confirmation as CIA Director:
"I think the most important thing is that the individual be a competent, qualified, intelligent professional, and Mike Hayden is all of those things."
She said that while she supports a civilian leader of the CIA, "I don't know a civilian that's really as well-connected and competent in the present stage of intelligence in America, and I think that's relevant."
And to explain her vote in support of Bush's FISA bill, she cited the Absolute Integrity of Mike McConnell as her reason:
I spoke with Admiral Mike McConnell, the Director of National Intelligence, at length this evening. He believes the United States is vulnerable, and that we need to move quickly to change the Foreign Intelligence Surveillance Act.
The intelligence community is deeply concerned that chatter among suspected terrorist networks is up. I am concerned as well. We are living in a period of heightened vulnerability, and must give the intelligence community the tools they need to protect America. . . .
I voted for both bills because one needed 60 votes to pass. It is vital that we act now. We cannot leave the nation unprotected in this post-9/11 period.
What is so notable -- and most revealing -- about this is that Feinstein is a Democratic Senator from one of the most liberal states in the country. Conventional wisdom holds that she is a "liberal" or at least a moderate. She came onto the national scene in the 1980s as the Mayor of San Francisco, one of the most liberal large cities in the nation, and was twice re-elected by San Francisco residents.
In fairness, she casts some (usually futile) votes in favor of the standard Democratic agenda on issues such as the environment, gun control and the Military Commissions Act. And she'll listlessly participate in investigations that go nowhere, even when the White House defies or outright ignores subpoenas. But what she does with the greatest conviction is supports right-wing Bush measures and, above all else, is an ardent defender of the Beltway power establishment.
In this regard, she really symbolizes a major imbalance in the Washington political system. The right-wing Republicans in Congress have an affinity with their base and share the same basic values. One saw that quite vividly in the recent immigration debate, where most Congressional Republicans -- particularly the "conservative" ones -- embraced rather than ran away from their angry, impassioned base by blocking enactment of the immigration bill which the GOP establishment favored but which the right-wing base hated. Most conservative Senators sided with their base over the GOP establishment, as they usually do when there is a split (Harriet Miers, Dubai Port Deal, even steadfast support for the Iraq War). And they rarely repudiate the political value system of their base because they respect it and share it.
By very stark contrast, most (though certainly not all) Democrats in Congress -- particularly the most influential and longest-serving ones in the Senate like Feinstein -- have contempt for their base and share virtually none of their values. In March of last year, I had an e-mail exchange with the spokesperson for a key Democratic Senator on the Intelligence Committee regarding how bloggers and their readers could work more closely with Democratic Senators to highlight the need for the NSA lawbreaking scandal to be investigated and taken more seriously. Ultimately, they made clear that they wanted nothing to do with actual citizens who were eager to bring that situation about, as I was told:
I think there is an opportunity for us to figure out a better way to work together. But, you have to understand, my ultimate goal is to help [the] Senator [] achieve his objective of real oversight on national security matters by the Intelligence Committee.
Even with the best of intentions, I'm not convinced that bloggers can help us meet that goal. In fact, I worry about it hurting our efforts given the increasingly partisan environment.
As Digby said yesterday of Senate Democrats: "it surely seems true that they loathe the Democratic base as much as the Republicans do." Hence, Dianne Feinstein funds Bush's war with no limits while condemning MoveOn. She votes to vest vast new surveillance powers in the President. She defends and vouches for and places blind faith in the whole litany of Bush intelligence officials who have spent the last six years radicalizing this country and breaking the law.
Plainly, Feinstein does not do this out of political fear or "spinelessness," but because it is who she now is and what she believes. She and those like her are the reason why there is such a gaping disconnect between the Beltway political class and the political views of most Americans.
Most of these political officials who feed off of Washington year after year become appendages of it and vigorous defenders of nothing other than the Beltway system. They are drained of all belief, conviction and passion. And in Feinstein's case, it is particularly easy to understand why this is so. Her current husband, Richard Blum, is an extremely rich defense contractor whose companies have endless relationships with the work Feinstein does in the Senate. It is entirely unsurprising that Feinstein's affection is reserved for officials in the intelligence and defense communities because those are her social peers, the individuals with whom her husband interacts professionally and socially and with whom she most identifies.
More than anything else, Feinstein worships at the altar of the Beltway power system and its most revered members. Conversely, she has contempt for the liberal base which elects her and the constituents she represents. She long ago ceased being driven by the political values which serve as props for her campaigns, if she was ever driven by them. And that is the story of so many of the Beltway Democrats.
It really is one of the most extraordinary -- and downright embarrassing -- political facts that more Republicans than Democrats approve of the 2007 Democratic Congress. And why wouldn't they? The Democratic Congress has not restrained the Leader at all, but has done much to support and empower him. The Democratic Congress -- especially the Senate -- is controlled by the likes of Dianne Feinstein, and what Bush supporter wouldn't be satisfied with the role she is playing?
There are absolutely members of Congress who are ardent defenders of our basic Constitutional liberties and who are genuine opponents of the Bush administration. But the record of Congress leaves no doubt that they are wildly outnumbered.
It isn't only -- or even principally -- the "Blue Dogs" which make the "Democratic Congress" nothing but an enabling instrument of the Bush White House and its right-wing policies. Far worse are the establishment-defending, soul-less, belief-less, self-perpetuating "liberal Senators" like Feinstein who render the concept of "opposition party" nothing more than a deceitful illusion. Dianne Feinstein is the drained and Bush-enabling face of the 2007 Democratic Congress.
US state department accused
of ignoring sexual misconduct[Hey Feinstein (Who should be investigated for criminal misconduct and illegally making your baby killing War Profiteer husband and you billions of dollars during Bush's Iraq war based on lies?) is this act treason or the same dirty old criminal politician stuff, where you say one thing, and then do another thing (like breaking U.S. laws) ?]
Leaked memo says department brushed off allegations of sexual assault, engaging prostitutes and drug use by US overseas staff
Reuters, guardian.co.uk, Wednesday 12 June 2013 00.09 EDT, Article Source
Secretary of state John Kerry. Photograph: Win McNamee/GettyThe US state department says it is investigating allegations of sexual misconduct by overseas staff, including a report that an ambassador patronised prostitutes, after a leaked memo said the agency had ignored the behaviour.
CBS news this week reported it had obtained an internal state department inspector-general's memo that said several investigations into possible cases of misconduct were influenced, manipulated or called off.
The memo, according to CBS, listed eight examples of alleged misconduct. They include allegations that a state department security official in Beirut "engaged in sexual assaults" on foreign nationals hired as embassy guards, and that members of former secretary of state Hillary Clinton's security detail "engaged prostitutes while on official trips in foreign countries" – a problem the report says was "endemic".
The memo, CBS said, alleges an underground drug ring operating near the US embassy in Baghdad supplied state department contractors with drugs. It said a US ambassador in a sensitive diplomatic post was suspected of "patronising prostitutes in a public park", according to CBS.
The CBS report did not identify employees alleged to have been involved, but the US ambassador to Belgium, Howard Gutman, issued a statement on Tuesday denying he had done anything wrong.
"I am angered and saddened by the baseless allegations that have appeared in the press and to watch the four years I have proudly served in Belgium smeared is devastating," Gutman said.
"I live on a beautiful park in Brussels that you walk through to get to many locations and at no point have I ever engaged in any improper activity."
A spokesman for the state department's office of inspector-general said on Tuesday the allegations were being investigated and former officials with law enforcement experience had been hired to help with the investigation.
A state department spokeswoman, Jen Psaki, told reporters the memo included "a number of unsubstantiated accusations".
"Prior to the drafting of this memo, the department's bureau of diplomatic security had already started looking into or completed the process of looking into these individual incidents," Psaki said. "All of these cases have been and will be brought ... to their logical conclusions.
"The notion that we would not vigorously pursue criminal misconduct is not only preposterous, it's inaccurate," Psaki said.
The White House promised there would be no tolerance for misconduct.
"We're not going to prejudge anyone or anything before all the facts are determined," White House spokesman Jay Carney said at his daily briefing. "I want to make clear the president has zero tolerance for misconduct by any government employee."
Internal state department investigations are conducted by the diplomatic security service, which protects the Secretary of State, John Kerry, and ambassadors. An inspector-general's report in February found shortcomings in the service's ability to investigate problems, a problem under review by the state department.
In a letter to Kerry, Ed Royce, a Republican who chairs the House foreign affairs committee, said he was "deeply troubled" by the allegations in the CBS report and called for a thorough investigation.
George Orwell back in fashion
as Prism stokes paranoia about Big BrotherNineteen Eighty-Four depicts a society in which liberty was impossible – so how should we respond to this new threat?
Posted by Stephen Moss, Tuesday 11 June 2013 13.08 EDT, guardian.co.uk, Article Source
More relevant than ever … George Orwell, who saw the writer as a free individual striving for objective truth. Photograph: Rex FeaturesThe NSA Prism surveillance scandal has been good news for George Orwell, and in particular for his dystopian novel Nineteen Eighty-Four, which was originally published in 1949. Sales of the centennial edition have risen by more than 7,000% on Amazon.com . Having been languishing at 13,074 in the list, it is now up to 193 and rising.
It may not rival Caroline Barnett's Willing to Walk on Water: Step Out in Faith and Let God Work Miracles through Your Life, which has miraculously surged from 144th to first in the past 24 hours with a 267,000% rise, but clearly many people are finding parallels between the US government's willingness to snoop on Joe Public's emails and phone calls and Orwell's vision of a future in which Big Brother is everywhere.
"Orwellian" is the word on everyone's lips. "The question is, what do freedom and liberty mean in the United States of America?" Senator Bernie Sanders asked in a TV interview this week. "What does our constitution mean? What kind of country do we want to be? Kids will grow up knowing that every damn thing that they do is going to be recorded somewhere in a file, and I think that will have a very Orwellian and inhibiting impact on our lives."
Not, it must be said, that Orwell really needs the publicity. Like Big Brother, he is always with us. DJ Taylor, who in 2003 wrote a biography of Orwell and for the past five years has been chairman of the Orwell Trust, makes a startling claim for the writer: "If you had to write down the names of the three writers in English who had had the greatest effect in communicating to the general public what books and literature were about," he says, "they would be Shakespeare, Dickens and Orwell."
The US has always been keen on Orwell: liberals warmed to him because of his warnings against the power of the state, conservatives because his books gave them a stick with which to beat communism. His influence has also been felt outside the English-speaking world. Editions of Ninety Eighty-Four and Animal Farm, published in 1945, circulated in the Soviet Union; he was – and indeed still is – revered in Poland, where his satires were widely read under communist rule; and Taylor believes he is being read in China today. Orwell has something to say to everyone who is suffering under autocracy.
However, readers who pick up Nineteen Eighty-Four because of the current worries over the Prism programme would be wrong just to see it as a novel about the dangers of overweening technology. The all-seeing telescreen in the corner of the room is an important device for allowing the state to exercise control, but Orwell's real concern is about far more insidious threats to liberty. The Big Brother state aims at nothing less than the control of language and thought. According to the slogans repeated by the Ministry of Truth, "War is Peace, Freedom is Slavery, Ignorance is Strength." Deprive people of the words with which to resist, and you will crush resistance.
In Nineteen Eighty-Four, Winston Smith's defining act of rebellion is to keep a diary, to attempt to record his thoughts and feelings accurately – not easy when the expressions you need have been obliterated or perverted. The greatest inhibition, to use Senator Sanders's word, is mental rather than physical.
The idea that governments could control people's minds terrified Orwell. Taylor argues that Nineteen Eighty-Four was born of paranoia – a paranoia that was apparent from the beginning of Orwell's writing career in the early 1930s. He lionised the writer as a free individual striving for objective truth, beholden to no special interests, yet everywhere he saw that freedom being circumscribed.
Orwell encapsulated those fears in his 1946 essay "The Prevention of Literature". "In our age," he wrote, "the idea of intellectual liberty is under attack from two directions. On the one side are its theoretical enemies, the apologists of totalitarianism, and on the other its immediate, practical enemies, monopoly and bureaucracy … Everything conspires to turn the writer, and every other kind of artist as well, into a minor official, working on themes handed to him from above and never telling what seems to him the whole truth."
It is Orwell's paranoia that gives his writing its power and urgency, and which has kept it alive. . What we might learn from a broader understanding of that much-used (and sometimes abused) term "Orwellian" is that he would fear not only the technology of surveillance but our response to it. Are we willing to question its use? Will we demand greater oversight of the work of the security agencies? Will we hold our government to account? As long as there is a Winston Smith struggling to keep his diary, Big Brother has not won.
Prisms... cartoon by Martin Rowson on the NSA surveillance revelations
Sunday 9 June 2013 18.11 EDT, The Guardian, Source
NSA surveillance as told through classic children's books
There's Waldo and here are the names and identities of every single person on this page
Pure perfection, suggested by @madfoot Photograph: Darth/Twitter.comAs news of the NSA's secret surveillance programs spread this weekend, Twitter did what it does best: mockery. User Darth asked followers to contribute titles for #NSAKidsBooks, which were then turned into beautifully hilarious works of art. Darth has kindly allowed us to share them. [Click to view remaining children's books]
Boundless Informant: the NSA's secret tool
to track global surveillance dataRevealed: The NSA's powerful tool for cataloguing data -- including figures on US collection
Glenn Greenwald and Ewen MacAskill, guardian.co.uk, Saturday 8 June 2013 15.10 EDT, Article Spurce
The color scheme ranges from green (least subjected to surveillance) through yellow
and orange to red (most surveillance). Note the '2007' date in the image relates to the
document from which the interactive map derives its top secret classification, not to the map itself.The National Security Agency has developed a powerful tool for recording and analysing where its intelligence comes from, raising questions about its repeated assurances to Congress that it cannot keep track of all the surveillance it performs on American communications.
The Guardian has acquired top-secret documents about the NSA datamining tool, called Boundless Informant, that details and even maps by country the voluminous amount of information it collects from computer and telephone networks.
The focus of the internal NSA tool is on counting and categorizing the records of communications, known as metadata, rather than the content of an email or instant message.
The Boundless Informant documents show the agency collecting almost 3 billion pieces of intelligence from US computer networks over a 30-day period ending in March 2013. One document says it is designed to give NSA officials answers to questions like, "What type of coverage do we have on country X" in "near real-time by asking the SIGINT [signals intelligence] infrastructure."
An NSA factsheet about the program, acquired by the Guardian, says: "The tool allows users to select a country on a map and view the metadata volume and select details about the collections against that country."
Under the heading "Sample use cases", the factsheet also states the tool shows information including: "How many records (and what type) are collected against a particular country."
A snapshot of the Boundless Informant data, contained in a top secret NSA "global heat map" seen by the Guardian, shows that in March 2013 the agency collected 97bn pieces of intelligence from computer networks worldwide.
The heat map reveals how much data is being collected from around the world. Note
the '2007' date in the image relates to the document from which the interactive map
derives its top secret classification, not to the map itself.Iran was the country where the largest amount of intelligence was gathered, with more than 14bn reports in that period, followed by 13.5bn from Pakistan. Jordan, one of America's closest Arab allies, came third with 12.7bn, Egypt fourth with 7.6bn and India fifth with 6.3bn.
The heatmap gives each nation a color code based on how extensively it is subjected to NSA surveillance. The color scheme ranges from green (least subjected to surveillance) through yellow and orange to red (most surveillance).
The disclosure of the internal Boundless Informant system comes amid a struggle between the NSA and its overseers in the Senate over whether it can track the intelligence it collects on American communications. The NSA's position is that it is not technologically feasible to do so.
At a hearing of the Senate intelligence committee In March this year, Democratic senator Ron Wyden asked James Clapper, the director of national intelligence: "Does the NSA collect any type of data at all on millions or hundreds of millions of Americans?"
"No sir," replied Clapper.
Judith Emmel, an NSA spokeswoman, told the Guardian in a response to the latest disclosures: "NSA has consistently reported -- including to Congress -- that we do not have the ability to determine with certainty the identity or location of all communicants within a given communication. That remains the case."
Other documents seen by the Guardian further demonstrate that the NSA does in fact break down its surveillance intercepts which could allow the agency to determine how many of them are from the US. The level of detail includes individual IP addresses.
IP address is not a perfect proxy for someone's physical location but it is rather close, said Chris Soghoian, the principal technologist with the Speech Privacy and Technology Project of the American Civil Liberties Union. "If you don't take steps to hide it, the IP address provided by your internet provider will certainly tell you what country, state and, typically, city you are in," Soghoian said.
That approximation has implications for the ongoing oversight battle between the intelligence agencies and Congress.
On Friday, in his first public response to the Guardian's disclosures this week on NSA surveillance, Barack Obama said that that congressional oversight was the American peoples' best guarantee that they were not being spied on.
"These are the folks you all vote for as your representatives in Congress and they are being fully briefed on these programs," he said. Obama also insisted that any surveillance was "very narrowly circumscribed".
Senators have expressed their frustration at the NSA's refusal to supply statistics. In a letter to NSA director General Keith Alexander in October last year, senator Wyden and his Democratic colleague on the Senate intelligence committee, Mark Udall, noted that "the intelligence community has stated repeatedly that it is not possible to provide even a rough estimate of how many American communications have been collected under the Fisa Amendments Act, and has even declined to estimate the scale of this collection."
At a congressional hearing in March last year, Alexander denied point-blank that the agency had the figures on how many Americans had their electronic communications collected or reviewed. Asked if he had the capability to get them, Alexander said: "No. No. We do not have the technical insights in the United States." He added that "nor do we do have the equipment in the United States to actually collect that kind of information".
Soon after, the NSA, through the inspector general of the overall US intelligence community, told the senators that making such a determination would jeopardize US intelligence operations -- and might itself violate Americans' privacy.
"All that senator Udall and I are asking for is a ballpark estimate of how many Americans have been monitored under this law, and it is disappointing that the inspectors general cannot provide it," Wyden told Wired magazine at the time.
The documents show that the team responsible for Boundless Informant assured its bosses that the tool is on track for upgrades.
The team will "accept user requests for additional functionality or enhancements," according to the FAQ acquired by the Guardian. "Users are also allowed to vote on which functionality or enhancements are most important to them (as well as add comments). The BOUNDLESSINFORMANT team will periodically review all requests and triage according to level of effort (Easy, Medium, Hard) and mission impact (High, Medium, Low)."
Emmel, the NSA spokeswoman, told the Guardian: "Current technology simply does not permit us to positively identify all of the persons or locations associated with a given communication (for example, it may be possible to say with certainty that a communication traversed a particular path within the internet. It is harder to know the ultimate source or destination, or more particularly the identity of the person represented by the TO:, FROM: or CC: field of an e-mail address or the abstraction of an IP address).
"Thus, we apply rigorous training and technological advancements to combine both our automated and manual (human) processes to characterize communications -- ensuring protection of the privacy rights of the American people. This is not just our judgment, but that of the relevant inspectors general, who have also reported this."
She added: "The continued publication of these allegations about highly classified issues, and other information taken out of context, makes it impossible to conduct a reasonable discussion on the merits of these programs."
Additional reporting: James Ball in New York and Spencer Ackerman in Washington
White House 'welcomes media interest' in Prism
Security adviser says time is ripe for debate, but leak investigation may yet lead to whistleblowers being prosecuted
Dan Roberts in Rancho Mirage, guardian.co.uk, Saturday 8 June 2013 20.51 EDT, Article Source
Director of National Intelligence James Clapper: 'In a rush to publish, media outlets
have not given the full context.' Photograph: Saul Loeb/AFP/Getty ImagesThe White House has said that it welcomes media interest in US surveillance practices, despite confirming that the Department of Justice is in the early stages of a leak investigation that may lead to criminal prosecutions of whistleblowers who revealed them.
As the second of two secret US monitoring programmes was partially declassified in response to leaked disclosures this week, officials speaking at a presidential summit in California told the Guardian that the ensuing public debate was necessary.
Deputy national security adviser Ben Rhodes said: "The debate that's been sparked by these revelations – while we do not think that the revelation of secret programmes is in the national security interest of the US – the broader debate about privacy and civil liberties [is something Obama] went out of his way to identify as one of the trade-offs we have to wrestle with.
"We'll have that debate. We welcome congressional interest in these issues, we welcome the interest of the American people and of course the media in these issues but we feel confident we have done what we need to do strike a balance between privacy and security by building in rigorous oversight mechanisms."
His comments follow a decision late on Saturday by the intelligence community to declassify parts of its Prism programme – revealed by the Guardian and the Washington Post on Thursday – so that it could explain how its collection of data from internet companies was supervised by Congress.
The statement confirmed that Prism was "an internal government computer system used to facilitate the government's statutorily authorised collection of foreign intelligence information from electronic communication service providers under court supervision".
Director of national intelligence James Clapper said the Guardian and Washington Post had failed to adequately convey how much constitutional oversight the programme received. "Over the last week, we have seen reckless disclosures of intelligence community measures used to keep Americans safe," he said in a separate statement. "In a rush to publish, media outlets have not given the full context, including the extent to which these programmes are overseen by all three branches of government to these effective tools."
But the question of how effective such oversight has been was brought into question this weekend by growing numbers of congressmen, who claim they had not been made aware of the Prism programme or an earlier disclosure by the Guardian of court orders forcing phone companies to hand over US phone records.
And Obama's chief national security adviser, Tom Donilon, was forced to reject suggestions that the oversight process had been undermined because data was being withheld from Congress.
This followed the disclosure of a third programme by the Guardian, codenamed Boundless Informant, that appeared to contradict recent assurances given to Congress that there was no record of how much data was gathered from US computers.
"These programmes are very important to the United States and its ability to protect itself," Donilon told the Guardian in response. "They are subject to very careful procedures to ensure particularly that privacies and civil liberties are protected, but are also subject to very careful oversight by a court and careful and persistent oversight by the Congress."
Officials in Washington have yet to make their mind up to how to respond to the leaks to the Guardian and other newspapers, particularly after a storm of protest followed the surveillance of phone records belonging to Associated Press reporters in pursuit of other leaks.
"What we are focused on [now] is doing an assessment of the damage that is being done to US national security by the revelation of this information, which is necessarily secret because we need to be able to conduct intelligence activities without those methods being revealed to the world," said Rhodes.
"As relates to any potential investigations, we are still in the early stages of this. This is something that will be addressed by the Justice Department and intelligence community in the coming days in consultation with the agencies that have been affected by these very disturbing leaks of national security."
Prism: claims of GCHQ circumventing law
are 'fanciful nonsense', says HagueForeign secretary confirms he will make Commons statement on Monday after reports UK spies were involved in NSA programme
Nicholas Watt, chief political correspondent, guardian.co.uk, Sunday 9 June 2013 06.06 EDT, Article Source
VIDEO AT SITE: William Hague says reports that GCHQ are gathering intelligence from phones and online sites should not concern people who have nothing to hide. Link to video: Data snooping: law abiding citizens have 'nothing to fear', says Hague <- BULLSHIT = Politicians lie!!! Republican War Criminal George W Bush and his War Criminal administration officials said repeatedly warrantless surveillance Telecom Spy program authorized by pResident Bush is carefully targeted to include only international calls and e-mails into or out of the USA, and only those involving at least one party suspected of being a member or ally of al-Qaeda or a related terror group; indicating the Obama Administration harbors criminals and is violating citizen rights?
William Hague is to make a statement to parliament on Monday to respond to allegations that GCHQ has gathered information on British citizens from internet companies through a secret US spy agency operation.
In his first public comments since the Guardian disclosed GCHQ's alleged role in the US-run Prism programme, the foreign secretary said Britain's electronic and eavesdropping headquarters always acted within the law.
Hague added that it was "fanciful" and "nonsense" to suggest that GCHQ would work with an agency in another country to circumvent the law.
The foreign secretary declined to say whether he had authorised GCHQ's use of the Prism system on the grounds that he never comments on intelligence. But he indicated that he may have done so, though only a modest scale, when he said that the law allowed "targeted" monitoring of terrorists, criminal networks and hostile foreign intelligence agencies.
Hague agreed to make a statement to MPs after the former shadow home secretary David Davis and the Labour chairman of the Commons home affairs select committee, Keith Vaz, raised serious concerns about the GCHQ disclosures.
Documents obtained by the Guardian, which disclosed the Prism system last week, suggested that GCHQ had generated 197 intelligence reports from Prism last year. The system would appear to allow GCHQ to bypass formal legal processes to access personal material, such as emails and photographs, from the world's biggest internet companies.
Hague said GCHQ did monitor traffic, though he said it always acted within the law. He told the Andrew Marr Show on BBC1: "What people need to know is intelligence-gathering in this country by the UK is governed by a very strong legal framework so that we get the balance right between the liberties and privacy of people and the security of the country.
"That provides not for trawling through the contents of people's phone calls. It provides for intelligence gathering that is authorised, necessary, proportionate and targeted on what we really need to know."
The foreign secretary said the UK has enjoyed an "exceptional intelligence sharing relationship" with the US since the second world war. But he said that information from the US which is sent to Britain is governed by UK law.
Hague, who said he authorises operations by GCHQ most days of the week, said: "The idea that in GCHQ people are sitting working out how to circumvent a UK law with another agency in another country is fanciful. It is nonsense."
The foreign secretary said GCHQ, MI5 and MI6 were overseen by the relevant secretary of state, by the interception commission and by parliament's intelligence and security committee.
"If you are a law-abiding citizen of this country going about your business and your personal life you have nothing to fear – nothing to fear about the British state or intelligence agencies listening to the contents of your phone calls or anything like that. Indeed you will never be aware of all the things those agencies are doing to stop your identify being stolen and to stop a terrorist blowing you up tomorrow.
"But if you are a would-be terrorist or the centre of a criminal network or a foreign intelligence agency trying to spy on Britain you should be worried because that is what we work on and we are, on the whole, quite good at it."
Douglas Alexander, the shadow foreign secretary, said: "I called on the foreign secretary to make an urgent statement to parliament on the concerning reports relating to GCHQ and it is right that William Hague has now agreed to do so.
"I've said that it's right that we fully support our intelligence agencies in the work they do to keep us safe, while recognising that they must always operate within a framework of legality and accountability.
"I will be asking the foreign secretary in the House of Commons tomorrow to clarify the role of his department in overseeing those legal frameworks. William Hague must also inform the house of what steps he will take to support the work of the intelligence and security committee as it looks in to these matters.
"It is vital that the government now reassures people who are rightly concerned about these reports."
Speaking on Sky News's Murnaghan programme, the business secretary, Vince Cable, said it was a possibility that the Prism system may have allowed the government to operate a covert sort of snoopers' charter, which the Liberal Democrats oppose.
"Well, it may well have been," he said, when asked if the allegations amounted to eavesdropping by any other name, and added that there were two key issues that the Tories would need to address.
"One is that the Americans have developed this very sophisticated Prism system, which enables them to get access to data in other countries, with or without our knowledge. And there is a separate issue about whether GCHQ were involved in some collaborative exercise," Cable said.
"I think a lot of people will be reassured that we do work well with the Americans, but the whole point about surveillance is you have got to have it when you're dealing with terrorism or other crimes."
He added that all surveillance had to be proportionate, with "some oversight, legal and political".
The Lib Dems have so far resisted plans to forge ahead with the communications data bill, described by some as the snoopers' charter, which would give powers to track people's telephone and internet use.
NSA Prism program taps in to user data of
Apple, Google and others• Top-secret Prism program claims direct access to servers of firms including Google, Apple and Facebook
• Companies deny any knowledge of program in operation since 2007 <- Corporations Lie!!!: See Big Tobacco above
• Obama orders US to draw up overseas target list for cyber-attacks
Glenn Greenwald and Ewen MacAskill, The Guardian, Thursday 6 June 2013, Article Source
A slide depicting the top-secret PRISM program.The National Security Agency has obtained direct access to the systems of Google, Facebook, Apple and other US internet giants, according to a top secret document obtained by the Guardian.
The NSA access is part of a previously undisclosed program called Prism, which allows officials to collect material including search history, the content of emails, file transfers and live chats, the document says.
The Guardian has verified the authenticity of the document, a 41-slide PowerPoint presentation – classified as top secret with no distribution to foreign allies – which was apparently used to train intelligence operatives on the capabilities of the program. The document claims "collection directly from the servers" of major US service providers.
Although the presentation claims the program is run with the assistance of the companies, all those who responded to a Guardian request for comment on Thursday denied knowledge of any such program.
In a statement, Google said: "Google cares deeply about the security of our users' data. We disclose user data to government in accordance with the law, and we review all such requests carefully. From time to time, people allege that we have created a government 'back door' into our systems, but Google does not have a back door for the government to access private user data."
Several senior tech executives insisted that they had no knowledge of Prism or of any similar scheme. They said they would never have been involved in such a program. "If they are doing this, they are doing it without our knowledge," one said.
An Apple spokesman said it had "never heard" of Prism.
The NSA access was enabled by changes to US surveillance law introduced under President Bush and renewed under Obama in December 2012.
The program facilitates extensive, in-depth surveillance on live communications and stored information. The law allows for the targeting of any customers of participating firms who live outside the US, or those Americans whose communications include people outside the US.
It also opens the possibility of communications made entirely within the US being collected without warrants.
Disclosure of the Prism program follows a leak to the Guardian on Wednesday of a top-secret court order compelling telecoms provider Verizon to turn over the telephone records of millions of US customers.
The participation of the internet companies in Prism will add to the debate, ignited by the Verizon revelation, about the scale of surveillance by the intelligence services. Unlike the collection of those call records, this surveillance can include the content of communications and not just the metadata.
Some of the world's largest internet brands are claimed to be part of the information-sharing program since its introduction in 2007. Microsoft – which is currently running an advertising campaign with the slogan "Your privacy is our priority" – was the first, with collection beginning in December 2007.
It was followed by Yahoo in 2008; Google, Facebook and PalTalk in 2009; YouTube in 2010; Skype and AOL in 2011; and finally Apple, which joined the program in 2012. The program is continuing to expand, with other providers due to come online.
Collectively, the companies cover the vast majority of online email, search, video and communications networks.
Prism and the CORPORATIONS WHO SOLD OUT U.S. CITIZENSThe extent and nature of the data collected from each company varies.
Companies are legally obliged to comply with requests for users' communications under US law, but the Prism program allows the intelligence services direct access to the companies' servers. The NSA document notes the operations have "assistance of communications providers in the US".
The revelation also supports concerns raised by several US senators during the renewal of the Fisa Amendments Act in December 2012, who warned about the scale of surveillance the law might enable, and shortcomings in the safeguards it introduces.
When the FAA was first enacted, defenders of the statute argued that a significant check on abuse would be the NSA's inability to obtain electronic communications without the consent of the telecom and internet companies that control the data. But the Prism program renders that consent unnecessary, as it allows the agency to directly and unilaterally seize the communications off the companies' servers.
A chart prepared by the NSA, contained within the top-secret document obtained by the Guardian, underscores the breadth of the data it is able to obtain: email, video and voice chat, videos, photos, voice-over-IP (Skype, for example) chats, file transfers, social networking details, and more.
Prism and the CORPORATIONS WHO SOLD OUT U.S. CITIZENSThe document is recent, dating to April 2013. Such a leak is extremely rare in the history of the NSA, which prides itself on maintaining a high level of secrecy.
The Prism program allows the NSA, the world's largest surveillance organisation, to obtain targeted communications without having to request them from the service providers and without having to obtain individual court orders.
With this program, the NSA is able to reach directly into the servers of the participating companies and obtain both stored communications as well as perform real-time collection on targeted users.
The presentation claims Prism was introduced to overcome what the NSA regarded as shortcomings of Fisa warrants in tracking suspected foreign terrorists. It noted that the US has a "home-field advantage" due to housing much of the internet's architecture. But the presentation claimed "Fisa constraints restricted our home-field advantage" because Fisa required individual warrants and confirmations that both the sender and receiver of a communication were outside the US.
"Fisa was broken because it provided privacy protections to people who were not entitled to them," the presentation claimed. "It took a Fisa court order to collect on foreigners overseas who were communicating with other foreigners overseas simply because the government was collecting off a wire in the United States. There were too many email accounts to be practical to seek Fisas for all."
The new measures introduced in the FAA redefines "electronic surveillance" to exclude anyone "reasonably believed" to be outside the USA – a technical change which reduces the bar to initiating surveillance.
The act also gives the director of national intelligence and the attorney general power to permit obtaining intelligence information, and indemnifies internet companies against any actions arising as a result of co-operating with authorities' requests.
In short, where previously the NSA needed individual authorisations, and confirmation that all parties were outside the USA, they now need only reasonable suspicion that one of the parties was outside the country at the time of the records were collected by the NSA.
The document also shows the FBI acts as an intermediary between other agencies and the tech companies, and stresses its reliance on the participation of US internet firms, claiming "access is 100% dependent on ISP provisioning".
In the document, the NSA hails the Prism program as "one of the most valuable, unique and productive accesses for NSA".
It boasts of what it calls "strong growth" in its use of the Prism program to obtain communications. The document highlights the number of obtained communications increased in 2012 by 248% for Skype – leading the notes to remark there was "exponential growth in Skype reporting; looks like the word is getting out about our capability against Skype". There was also a 131% increase in requests for Facebook data, and 63% for Google.
The NSA document indicates that it is planning to add Dropbox as a PRISM provider. The agency also seeks, in its words, to "expand collection services from existing providers".
The revelations echo fears raised on the Senate floor last year during the expedited debate on the renewal of the FAA powers which underpin the PRISM program, which occurred just days before the act expired.
Senator Christopher Coons of Delaware specifically warned that the secrecy surrounding the various surveillance programs meant there was no way to know if safeguards within the act were working.
"The problem is: we here in the Senate and the citizens we represent don't know how well any of these safeguards actually work," he said.
"The law doesn't forbid purely domestic information from being collected. We know that at least one Fisa court has ruled that the surveillance program violated the law. Why? Those who know can't say and average Americans can't know."
Other senators also raised concerns. Senator Ron Wyden of Oregon attempted, without success, to find out any information on how many phone calls or emails had been intercepted under the program.
When the law was enacted, defenders of the FAA argued that a significant check on abuse would be the NSA's inability to obtain electronic communications without the consent of the telecom and internet companies that control the data. But the Prism program renders that consent unnecessary, as it allows the agency to directly and unilaterally seize the communications off the companies' servers.
When the NSA reviews a communication it believes merits further investigation, it issues what it calls a "report". According to the NSA, "over 2,000 Prism-based reports" are now issued every month. There were 24,005 in 2012, a 27% increase on the previous year.
In total, more than 77,000 intelligence reports have cited the PRISM program.
Jameel Jaffer, director of the ACLU's Center for Democracy, that it was astonishing the NSA would even ask technology companies to grant direct access to user data.
"It's shocking enough just that the NSA is asking companies to do this," he said. "The NSA is part of the military. The military has been granted unprecedented access to civilian communications.
"This is unprecedented militarisation of domestic communications infrastructure. That's profoundly troubling to anyone who is concerned about that separation."
A senior administration official said in a statement: "The Guardian and Washington Post articles refer to collection of communications pursuant to Section 702 of the Foreign Intelligence Surveillance Act. This law does not allow the targeting of any US citizen or of any person located within the United States.
"The program is subject to oversight by the Foreign Intelligence Surveillance Court, the Executive Branch, and Congress. It involves extensive procedures, specifically approved by the court, to ensure that only non-US persons outside the US are targeted, and that minimize the acquisition, retention and dissemination of incidentally acquired information about US persons.
"This program was recently reauthorized by Congress after extensive hearings and debate.
"Information collected under this program is among the most important and valuable intelligence information we collect, and is used to protect our nation from a wide variety of threats.
"The Government may only use Section 702 to acquire foreign intelligence information, which is specifically, and narrowly, defined in the Foreign Intelligence Surveillance Act. This requirement applies across the board, regardless of the nationality of the target."
Additional reporting by James Ball and Dominic Rushe
Obama orders US to draw up overseas target list
for cyber-attacksExclusive: Top-secret directive steps up offensive cyber capabilities to 'advance US objectives around the world'
• Read the secret presidential directive here
Glenn Greenwald and Ewen MacAskill, guardian.co.uk, Friday 7 June 2013 15.06 EDT, Article Source
VIDEO AT SITE: Link to video: Obama defends internet surveillance programs
Barack Obama has ordered his senior national security and intelligence officials to draw up a list of potential overseas targets for US cyber-attacks, a top secret presidential directive obtained by the Guardian reveals.
The 18-page Presidential Policy Directive 20, issued in October last year but never published, states that what it calls Offensive Cyber Effects Operations (OCEO) "can offer unique and unconventional capabilities to advance US national objectives around the world with little or no warning to the adversary or target and with potential effects ranging from subtle to severely damaging".
It says the government will "identify potential targets of national importance where OCEO can offer a favorable balance of effectiveness and risk as compared with other instruments of national power".
The directive also contemplates the possible use of cyber actions inside the US, though it specifies that no such domestic operations can be conducted without the prior order of the president, except in cases of emergency.
The aim of the document was "to put in place tools and a framework to enable government to make decisions" on cyber actions, a senior administration official told the Guardian.
The administration published some declassified talking points from the directive in January 2013, but those did not mention the stepping up of America's offensive capability and the drawing up of a target list.
Obama's move to establish a potentially aggressive cyber warfare doctrine will heighten fears over the increasing militarization of the internet.
The directive's publication comes as the president plans to confront his Chinese counterpart Xi Jinping at a summit in California on Friday over alleged Chinese attacks on western targets.
Even before the publication of the directive, Beijing had hit back against US criticism, with a senior official claiming to have "mountains of data" on American cyber-attacks he claimed were every bit as serious as those China was accused of having carried out against the US.
Presidential Policy Directive 20 defines OCEO as "operations and related programs or activities … conducted by or on behalf of the United States Government, in or through cyberspace, that are intended to enable or produce cyber effects outside United States government networks."
Asked about the stepping up of US offensive capabilities outlined in the directive, a senior administration official said: "Once humans develop the capacity to build boats, we build navies. Once you build airplanes, we build air forces."
The official added: "As a citizen, you expect your government to plan for scenarios. We're very interested in having a discussion with our international partners about what the appropriate boundaries are."
The document includes caveats and precautions stating that all US cyber operations should conform to US and international law, and that any operations "reasonably likely to result in significant consequences require specific presidential approval".
The document says that agencies should consider the consequences of any cyber-action. They include the impact on intelligence-gathering; the risk of retaliation; the impact on the stability and security of the internet itself; the balance of political risks versus gains; and the establishment of unwelcome norms of international behaviour.
Among the possible "significant consequences" are loss of life; responsive actions against the US; damage to property; serious adverse foreign policy or economic impacts.
The US is understood to have already participated in at least one major cyber attack, the use of the Stuxnet computer worm targeted on Iranian uranium enrichment centrifuges, the legality of which has been the subject of controversy. US reports citing high-level sources within the intelligence services said the US and Israel were responsible for the worm.
In the presidential directive, the criteria for offensive cyber operations in the directive is not limited to retaliatory action but vaguely framed as advancing "US national objectives around the world".
The revelation that the US is preparing a specific target list for offensive cyber-action is likely to reignite previously raised concerns of security researchers and academics, several of whom have warned that large-scale cyber operations could easily escalate into full-scale military conflict.
Sean Lawson, assistant professor in the department of communication at the University of Utah, argues: "When militarist cyber rhetoric results in use of offensive cyber attack it is likely that those attacks will escalate into physical, kinetic uses of force."
An intelligence source with extensive knowledge of the National Security Agency's systems told the Guardian the US complaints again China were hypocritical, because America had participated in offensive cyber operations and widespread hacking – breaking into foreign computer systems to mine information.
Provided anonymity to speak critically about classified practices, the source said: "We hack everyone everywhere. We like to make a distinction between us and the others. But we are in almost every country in the world."
The US likes to haul China before the international court of public opinion for "doing what we do every day", the source added.
One of the unclassified points released by the administration in January stated: "It is our policy that we shall undertake the least action necessary to mitigate threats and that we will prioritize network defense and law enforcement as preferred courses of action."
The full classified directive repeatedly emphasizes that all cyber-operations must be conducted in accordance with US law and only as a complement to diplomatic and military options. But it also makes clear how both offensive and defensive cyber operations are central to US strategy.
Under the heading "Policy Reviews and Preparation", a section marked "TS/NF" - top secret/no foreign - states: "The secretary of defense, the DNI [Director of National Intelligence], and the director of the CIA … shall prepare for approval by the president through the National Security Advisor a plan that identifies potential systems, processes and infrastructure against which the United States should establish and maintain OCEO capabilities…" The deadline for the plan is six months after the approval of the directive.
The directive provides that any cyber-operations "intended or likely to produce cyber effects within the United States" require the approval of the president, except in the case of an "emergency cyber action". When such an emergency arises, several departments, including the department of defense, are authorized to conduct such domestic operations without presidential approval.
Obama further authorized the use of offensive cyber attacks in foreign nations without their government's consent whenever "US national interests and equities" require such nonconsensual attacks. It expressly reserves the right to use cyber tactics as part of what it calls "anticipatory action taken against imminent threats".
The directive makes multiple references to the use of offensive cyber attacks by the US military. It states several times that cyber operations are to be used only in conjunction with other national tools and within the confines of law.
When the directive was first reported, lawyers with the Electronic Privacy Information Center filed a Freedom of Information Act request for it to be made public. The NSA, in a statement, refused to disclose the directive on the ground that it was classified.
In January, the Pentagon announced a major expansion of its Cyber Command Unit, under the command of General Keith Alexander, who is also the director of the NSA. That unit is responsible for executing both offensive and defensive cyber operations.
Earlier this year, the Pentagon publicly accused China for the first time of being behind attacks on the US. The Washington Post reported last month that Chinese hackers had gained access to the Pentagon's most advanced military programs.
The director of national intelligence, James Clapper, identified cyber threats in general as the top national security threat.
Obama officials have repeatedly cited the threat of cyber-attacks to advocate new legislation that would vest the US government with greater powers to monitor and control the internet as a means of guarding against such threats.
One such bill currently pending in Congress, the Cyber Intelligence Sharing and Protection Act (Cispa), has prompted serious concerns from privacy groups, who say that it would further erode online privacy while doing little to enhance cyber security.
In a statement, Caitlin Hayden, national security council spokeswoman, said: "We have not seen the document the Guardian has obtained, as they did not share it with us. However, as we have already publicly acknowledged, last year the president signed a classified presidential directive relating to cyber operations, updating a similar directive dating back to 2004. This step is part of the administration's focus on cybersecurity as a top priority. The cyber threat has evolved, and we have new experiences to take into account.
"This directive establishes principles and processes for the use of cyber operations so that cyber tools are integrated with the full array of national security tools we have at our disposal. It provides a whole-of-government approach consistent with the values that we promote domestically and internationally as we have previously articulated in the International Strategy for Cyberspace.
"This directive will establish principles and processes that can enable more effective planning, development, and use of our capabilities. It enables us to be flexible, while also exercising restraint in dealing with the threats we face. It continues to be our policy that we shall undertake the least action necessary to mitigate threats and that we will prioritize network defense and law enforcement as the preferred courses of action. The procedures outlined in this directive are consistent with the US Constitution, including the president's role as commander in chief, and other applicable law and policies."
Revealed: NSA collecting phone records
of millions of Verizon customers dailyExclusive: Top secret court order requiring Verizon to hand over all call data shows scale of domestic surveillance under Obama
• Read the Verizon court order in full here
• Obama administration justifies surveillance
Glenn Greenwald, The Guardian, Wednesday 5 June 2013, Article Source
Under the terms of the order, the numbers of both parties on a call are handed over, as
is location data and the time and duration of all calls. Photograph: Matt Rourke/APThe National Security Agency is currently collecting the telephone records of millions of US customers of Verizon, one of America's largest telecoms providers, under a top secret court order issued in April.
The order, a copy of which has been obtained by the Guardian, requires Verizon on an "ongoing, daily basis" to give the NSA information on all telephone calls in its systems, both within the US and between the US and other countries.
The document shows for the first time that under the Obama administration the communication records of millions of US citizens are being collected indiscriminately and in bulk – regardless of whether they are suspected of any wrongdoing.
The secret Foreign Intelligence Surveillance Court (Fisa) granted the order to the FBI on April 25, giving the government unlimited authority to obtain the data for a specified three-month period ending on July 19.
Under the terms of the blanket order, the numbers of both parties on a call are handed over, as is location data, call duration, unique identifiers, and the time and duration of all calls. The contents of the conversation itself are not covered.
The disclosure is likely to reignite longstanding debates in the US over the proper extent of the government's domestic spying powers.
Under the Bush administration, officials in security agencies had disclosed to reporters the large-scale collection of call records data by the NSA, but this is the first time significant and top-secret documents have revealed the continuation of the practice on a massive scale under President Obama.
The unlimited nature of the records being handed over to the NSA is extremely unusual. Fisa court orders typically direct the production of records pertaining to a specific named target who is suspected of being an agent of a terrorist group or foreign state, or a finite set of individually named targets.
The Guardian approached the National Security Agency, the White House and the Department of Justice for comment in advance of publication on Wednesday. All declined. The agencies were also offered the opportunity to raise specific security concerns regarding the publication of the court order.
The court order expressly bars Verizon from disclosing to the public either the existence of the FBI's request for its customers' records, or the court order itself.
"We decline comment," said Ed McFadden, a Washington-based Verizon spokesman.
The order, signed by Judge Roger Vinson, compels Verizon to produce to the NSA electronic copies of "all call detail records or 'telephony metadata' created by Verizon for communications between the United States and abroad" or "wholly within the United States, including local telephone calls".
The order directs Verizon to "continue production on an ongoing daily basis thereafter for the duration of this order". It specifies that the records to be produced include "session identifying information", such as "originating and terminating number", the duration of each call, telephone calling card numbers, trunk identifiers, International Mobile Subscriber Identity (IMSI) number, and "comprehensive communication routing information".
The information is classed as "metadata", or transactional information, rather than communications, and so does not require individual warrants to access. The document also specifies that such "metadata" is not limited to the aforementioned items. A 2005 court ruling judged that cell site location data – the nearest cell tower a phone was connected to – was also transactional data, and so could potentially fall under the scope of the order.
While the order itself does not include either the contents of messages or the personal information of the subscriber of any particular cell number, its collection would allow the NSA to build easily a comprehensive picture of who any individual contacted, how and when, and possibly from where, retrospectively.
It is not known whether Verizon is the only cell-phone provider to be targeted with such an order, although previous reporting has suggested the NSA has collected cell records from all major mobile networks. It is also unclear from the leaked document whether the three-month order was a one-off, or the latest in a series of similar orders.
The court order appears to explain the numerous cryptic public warnings by two US senators, Ron Wyden and Mark Udall, about the scope of the Obama administration's surveillance activities.
For roughly two years, the two Democrats have been stridently advising the public that the US government is relying on "secret legal interpretations" to claim surveillance powers so broad that the American public would be "stunned" to learn of the kind of domestic spying being conducted.
Because those activities are classified, the senators, both members of the Senate intelligence committee, have been prevented from specifying which domestic surveillance programs they find so alarming. But the information they have been able to disclose in their public warnings perfectly tracks both the specific law cited by the April 25 court order as well as the vast scope of record-gathering it authorized.
Julian Sanchez, a surveillance expert with the Cato Institute, explained: "We've certainly seen the government increasingly strain the bounds of 'relevance' to collect large numbers of records at once — everyone at one or two degrees of separation from a target — but vacuuming all metadata up indiscriminately would be an extraordinary repudiation of any pretence of constraint or particularized suspicion." The April order requested by the FBI and NSA does precisely that.
The law on which the order explicitly relies is the so-called "business records" provision of the Patriot Act, 50 USC section 1861. That is the provision which Wyden and Udall have repeatedly cited when warning the public of what they believe is the Obama administration's extreme interpretation of the law to engage in excessive domestic surveillance.
In a letter to attorney general Eric Holder last year, they argued that "there is now a significant gap between what most Americans think the law allows and what the government secretly claims the law allows."
"We believe," they wrote, "that most Americans would be stunned to learn the details of how these secret court opinions have interpreted" the "business records" provision of the Patriot Act.
Privacy advocates have long warned that allowing the government to collect and store unlimited "metadata" is a highly invasive form of surveillance of citizens' communications activities. Those records enable the government to know the identity of every person with whom an individual communicates electronically, how long they spoke, and their location at the time of the communication.
Such metadata is what the US government has long attempted to obtain in order to discover an individual's network of associations and communication patterns. The request for the bulk collection of all Verizon domestic telephone records indicates that the agency is continuing some version of the data-mining program begun by the Bush administration in the immediate aftermath of the 9/11 attack.
The NSA, as part of a program secretly authorized by President Bush on 4 October 2001, implemented a bulk collection program of domestic telephone, internet and email records. A furore erupted in 2006 when USA Today reported that the NSA had "been secretly collecting the phone call records of tens of millions of Americans, using data provided by AT&T, Verizon and BellSouth" and was "using the data to analyze calling patterns in an effort to detect terrorist activity." Until now, there has been no indication that the Obama administration implemented a similar program.
These recent events reflect how profoundly the NSA's mission has transformed from an agency exclusively devoted to foreign intelligence gathering, into one that focuses increasingly on domestic communications. A 30-year employee of the NSA, William Binney, resigned from the agency shortly after 9/11 in protest at the agency's focus on domestic activities.
In the mid-1970s, Congress, for the first time, investigated the surveillance activities of the US government. Back then, the mandate of the NSA was that it would never direct its surveillance apparatus domestically.
At the conclusion of that investigation, Frank Church, the Democratic senator from Idaho who chaired the investigative committee, warned: "The NSA's capability at any time could be turned around on the American people, and no American would have any privacy left, such is the capability to monitor everything: telephone conversations, telegrams, it doesn't matter."
Additional reporting by Ewen MacAskill and Spencer Ackerman
Spending Your Hard Earned Money Elsewhere ???
It Is Obvious There Is Now A Trust Problem Using:
Microsoft~ Yahoo~ Google
Facebook~ PalTalk~ AOL
Skype~ YouTube~ Apple
and those
Corporations Not Mentioned, Yet?
Corporations Lie ... Take Big Tobacco for Example:
Tobacco companies ordered to admit they lied over smoking danger <- Use this for search
US judge says tobacco firms must spend their own money on a public campaign admitting deception about the risks of smoking
Reuters in Washington guardian.co.uk, Tuesday 27 November 2012 23.59 EST [source]
This content has been removed as our copyright has expired.
Time For A Corporate Death Penalty
by Bruce A. Dixon, Black Agenda Report managing editor, Wed, 06/09/2010 -10:35, corporate rule
There are more than 40 federal offenses for which the death penalty can be applied to human beings, most of them connected to homicide of one kind or another. But countless homicides committed by the artificial persons we call corporations go unpunished every day. Apparently “personal responsibility” applies only to humans who are not operating behind the legal shield of corporate personhood.
Click to download or play the MP3 of this BA Radio commentary
Over the last hundred or so years, corporations have gained many of the rights previously accorded only to human beings. Corporations have the right to buy and sell anything or anyone that can be bought or sold. Corporations have claimed the right to lie in their advertising and PR as "free speech," along with the right to help us mere humans choose our judges and elected officials with unlimited amounts of cash, including anonymous cash. Corporations have been awarded the right to patent genetic sequences of diseases and to monopolize their cures, as well as patent rights to living plants and animals not of their invention. A whole type of new anti-pollution regulation called "cap and trade" actually enshrines a corporate right to pollute and establishes exchanges upon which speculators can bid, trade and capture rents for those alleged rights. And unlike a working person, who has no right to next month's let alone next year's wages, legal scholars working for corporations have devised and popularized something they call the "regulatory takings" doctrine, under which corporations may claim and recover from the government rights to profits they might have made in years to come. And let's not even talk about trillions in corporate welfare for banks, military contractors, Wal-Mart and others.
While many argue that corporations have too many rights as it is, this might be a good time to extend them at least one more right we humans have kept for ourselves until now; the right to be put to death for serious crimes. Right now federal statutes alone offer individuals more than 40 different ways to earn the death penalty, including kidnapping, treason, aircraft hijacking, espionage and many varieties of murder, conspiracy, threatening murder and some drug crimes. Individual states offer the death penalty for a host of similar offenses.
Putting bad corporate actors down the way we do rabid dogs and serial killers is not a new or even a radical idea. Corporations are created by the charters of individual states, so states DO have the power to revoke them. Early in this country's history, corporate charters used to limit a company's existence to a set number of years, to confine their operations to manufacturing a certain item, building a specific road or canal and prohibit them from changing ownership, dumping or concealing their assets or engaging in other kinds of business. These are legal powers that our governments have not used in a long, long time, but which it's high time to reclaim.
Homicidal profit-seeking on the part of corporations has become an everyday fact of modern life. Whether it's employers cutting health and safety corners, marketers pushing unsafe drugs, food and products of all kinds, or the deadly industrial fouling of the planet's air, soil, oceans and climate we are living in the midst of a corporate crime wave of murderous and epic proportions. If we value human life, it only makes sense to treat corporate serial killers like, well, corporate serial killers, to confiscate their ill-gotten assets, to revoke their corporate charters and sentence the artificial personae of corporate malefactors to death. If corporations are legal persons, it's time to enforce some personal responsibility upon them with a corporate death penalty.
After we accomplish that, it will be time to think about extending a little of that personal responsibility to the actual humans who operate behind the legal shield of the corporations. But right now, as the saying goes, a corporation can't even get arrested in this country, which, come to think of it is still another right we humans ought to bestow upon them.
For Black Agenda Radio, I'm Bruce Dixon. [permalink]
In Closing
by GoingShortMonday
Is it possible above corporate stock prices were pushed to their heights in order to deter investors from ever doing anything about corporations who were screwing them ???
For the Record
[Ed. Note: It was the Bush Administration, with political support from both Democrats and Republicans, who authorized SPYING on U.S. citizens; while giving Telecoms a free pass for knowingly breaking law, and then passed an illegal Patriot Act, without ever reading it. These are the same baby killers & child rapers, for the most part, who voted for an illegal Iraq war, based on nothing but lies, supported Israel's murder and maiming of United States Naval personnel aboard the USS Liberty, supplied Iraq with biological and chemical weapons from U.S. manufacturers, appointed Bush president, and more than likely had something to do with the mass murders of 9/11.]
FWIW: Do You Still Trust Your Cell Phone,
Mobile Device, Pad, Laptop, or any device
with Internet access or WiFi ???Don't Understand What Is Being Asked? ... Then Read the Following:
Citizens Against Second Hand Cellular Phone Radiation
Camel cigarettes had the largest booth at American Medical Association's 1948 convention; boasting, "More doctors smoke Camels than any other cigarette." which is a splendid example of "Profits Not People" and should be a 'Wake Up Call' for HONEST Evaluation of the Dangers and Hazards from Cellular Telephones and effects of amplified microwave frequencies emitting from Cellular repeater sites. ~ "It's A Matter of Trust" [Click to Continue Reading]
One More Thing
Since It Appears Government Can Not Seem to Stop
Foreign Cyber-War Data Collection and Cyber-Rape
What are you going to do for Americans when the millions of records government collected on U.S. Citizens, using NSA PRISM, gets cracked and stolen by a foreign government?
Click to view
THE NSA FILES
on one page
NONE OF THE ABOVE
should be a choice on Voter Ballots
Nobody for President
Cloud computing is a trap,
warns GNU founder Richard StallmanWeb-based programs like Google's Gmail will force people to buy into locked, proprietary systems that will cost more and more over time, according to the free software campaigner
Bobbie Johnson, technology correspondent, guardian.co.uk, Mon. 29 September 2008 09.11 EDT, Article Source
Richard Stallman on cloud computing: "It's stupidity. It's worse than stupidity:
it's a marketing hype campaign." Photograph: www.stallman.org
The concept of using web-based programs like Google's Gmail is "worse than stupidity", according to a leading advocate of free software.
Cloud computing – where IT power is delivered over the internet as you need it, rather than drawn from a desktop computer – has gained currency in recent years. Large internet and technology companies including Google, Microsoft and Amazon are pushing forward their plans to deliver information and software over the net.
But Richard Stallman, founder of the Free Software Foundation and creator of the computer operating system GNU, said that cloud computing was simply a trap aimed at forcing more people to buy into locked, proprietary systems that would cost them more and more over time.
"It's stupidity. It's worse than stupidity: it's a marketing hype campaign," he told The Guardian.
"Somebody is saying this is inevitable – and whenever you hear somebody saying that, it's very likely to be a set of businesses campaigning to make it true."
The 55-year-old New Yorker said that computer users should be keen to keep their information in their own hands, rather than hand it over to a third party.
His comments echo those made last week by Larry Ellison, the founder of Oracle, who criticised the rash of cloud computing announcements as "fashion-driven" and "complete gibberish".
"The interesting thing about cloud computing is that we've redefined cloud computing to include everything that we already do," he said. "The computer industry is the only industry that is more fashion-driven than women's fashion. Maybe I'm an idiot, but I have no idea what anyone is talking about. What is it? It's complete gibberish. It's insane. When is this idiocy going to stop?"
The growing number of people storing information on internet-accessible servers rather than on their own machines, has become a core part of the rise of Web 2.0 applications. Millions of people now upload personal data such as emails, photographs and, increasingly, their work, to sites owned by companies such as Google.
Computer manufacturer Dell recently even tried to trademark the term "cloud computing", although its application was refused.
But there has been growing concern that mainstream adoption of cloud computing could present a mixture of privacy and ownership issues, with users potentially being locked out of their own files.
Stallman, who is a staunch privacy advocate, advised users to stay local and stick with their own computers.
"One reason you should not use web applications to do your computing is that you lose control," he said. "It's just as bad as using a proprietary program. Do your own computing on your own computer with your copy of a freedom-respecting program. If you use a proprietary program or somebody else's web server, you're defenceless. You're putty in the hands of whoever developed that software."
Possible Interesting Addendum:
Once Upon A Time
April 11, 1989
The following was posted to a Usenet Group on Tuesday 11 April 1989:
RISKS-LIST: RISKS-FORUM Digest Tuesday 11 April 1989 Volume 8 : Issue 54
FORUM ON RISKS TO THE PUBLIC IN COMPUTERS AND RELATED SYSTEMS ACM Committee on Computers and Public Policy, Peter G. Neumann, moderator
Date: Tue, 11 Apr 89 08:12:04 PDT
From: cas@toad.com (Curtis Spangler)
Subject: NSA and Not Secure AgenciesSan Francisco Chronicle, Chronicle Wire Services, April 11, 1989:
"Computer Group Wary of Security Agency
A public interest group said yesterday that the National Security Agency, the nation's biggest intelligence agency, could exert excessive control over a program to strengthen the security of computer systems throughout the federal government.
The group, Computer Professionals for Social Responsibility - based in Palo Alto - urged key members of Congress to focus "particularly close scrutiny" on the agency's role in helping to implement legislation aimed at safeguarding sensitive but unclassified information in federal computers.
"There is a constant risk that the federal agencies, under the guise of enhancing computer security, may find their programs - to the extent that they rely upon computer systems - increasingly under the supervision of the largest and most secretive intelligence organization in the country," it said."
December 22, 2000
Security-Enhanced Linux (SELinux) is a GNU/Linux feature that provides the mechanism for supporting access control security policies, including United States Department of Defense-style mandatory access controls, through the use of GNU/Linux Security Modules (LSM) in the GNU/Linux kernel. It is not a GNU/Linux distribution, but rather a set of kernel modifications and user-space tools that can be added to various GNU/Linux distributions. Its architecture strives to separate enforcement of security decisions from the security policy itself and streamlines the volume of software charged with security policy enforcement. The key concepts underlying SELinux can be traced to several earlier projects by the United States National Security Agency. It has been integrated into the mainline GNU/Linux kernel since version 2.6, on 8 August 2003.
From: http://www.nsa.gov/research/selinux/background.shtml:
SELinux Background ~ Researchers in the National Information Assurance Research Laboratory of the National Security Agency (NSA) worked with Secure Computing Corporation (SCC) to develop a strong, flexible mandatory access control architecture based on Type Enforcement, a mechanism first developed for the LOCK system. The NSA and SCC developed two Mach-based prototypes of the architecture: DTMach and DTOS. The NSA and SCC then worked with the University of Utah's Flux research group to transfer the architecture to the Fluke research operating system. During this transfer, the architecture was enhanced to provide better support for dynamic security policies. This enhanced architecture was named Flask. The NSA integrated the Flask architecture into the GNU/Linux® operating system to transfer the technology to a larger developer and user community. The architecture has been subsequently mainstreamed into GNU/Linux® and ported to several other systems, including the Solaris™ (Sun Microsystems/Oracle) operating system, the freeBSD® operating system, and the Darwin (Apple) kernel, spawning a wide range of related work.
Images Via Wikipedia, the free encyclopedia
Things don't change, people do
Nothing has Changed:
Here is the last month archive: May 2013
Here are previous Month of June Archives
2007 ~ 2007.06 ~ 2008 ~ 2008.06 ~ 2009 ~ 2009.06
2010 ~ 2010.06 ~ 2011 ~ 2011.06 ~ 2012 ~ 2012.06
Temperature at 0900 AM PDT 201306.08
124.3 degrees fahrenheit
Temperature at 1700 PM PDT 201306.08
110 degrees fahrenheit
Lying POS, Baby Killing, War Criminals Say What?
Update: A top-secret document obtained by The Washington Post shows the NSA and FBI are grabbing audio and video chats, photographs, e-mails, documents, and connection logs directly from Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, and Apple servers. (via Pondo)
Bush administration officials said repeatedly warrantless surveillance Telecom Spy program authorized by pResident Bush is carefully targeted to include only international calls and e-mails into or out of the USA, and only those involving at least one party suspected of being a member or ally of al-Qaeda or a related terror group; indicating the Obama Administration harbors criminals and is violating citizen rights.
Obviously, Republicans and Democrats Believe A Majority of U.S. Citizens Ally with al-Qaeda or Related Terror Groups & another reason why:
NONE OF THE ABOVE
Should Be A Choice On Voter Ballots &
Nobody Should Be President
America's Vets: Returning Home To A Broken System
by NPR Staff, May 26, 2013 5:24 PM, Article Source
The Department of Veterans Affairs is being criticized for the shortfall in care for almost a million veterans who can't get timely compensation and have been waiting hundreds of days for help, often to no avail.
Frustration with the agency came to a head last Thursday when VA Secretary Eric Shinseki was called before a closed-door meeting of the House Appropriations Committee.
"We are aggressively executing a plan that we have put together to fix this decades-old problem and eliminate the backlog, as we have indicated, in 2015," Shinseki said after the meeting.
That's a long time for people in crisis to wait.
Coming Home Hurt
Glenn Smith, a 28-year-old Army veteran from St. Louis, joined the military in 2004.
"I joined because I loved tanks, believe it or not," Smith tells Jacki Lyden, host of weekends on All Things Considered.
Smith was deployed to Iraq twice between 2006 and 2010; he spent most of four years in combat. He now has an irregular heartbeat, and attributes it to one of the many IED blasts he went through. The irregular heartbeat, discovered during a routine training exercise, led to him being discharged last spring.
Smith described an anxiety attack in March in which "things just [closed] in" on him. It's even happened while he was driving.
"I didn't feel like I had any release or way to break free of it," he says. "I've had memories and nightmares of my experiences while I was in Iraq. Any all that just came rushing to the surface."
Smith also says he has a bad case of PTSD.
His PTSD has been so debilitating, he needs help navigating the VA. He submitted his initial claim about a year ago, but still lacks regular treatment for the disorder.
"Once I got back home to St. Louis, I've been trying to push with the VA here ... [and] trying to get my compensation and also trying to get therapy for my PTSD," he says. "Recently ... I was told my case wouldn't be looked at for another year or so because they're backlogged two years right now."
While he waits, Smith is patching together medical care for his PTSD. His heart condition is getting better, but he's in limbo, waiting for his benefits while he attempts to carry on.
"For the immediate horizon, I'm just trying to find a job so I can feel like I have a sense of moving forward and healing," he says. "And for the fall, I'm actually getting myself into college."
A Backlog Of Assistance
There are almost 900,000 VA benefits claims pending, says Quil Lawrence, NPR's veterans affairs correspondent. He tells Lyden that VA has set a goal that it should only take 125 days to process each claim.
"Currently, almost 600,000 of them are 125 days old or more," Lawrence says. "In some major cities, it's taking 300 days, even 600 days to get your claim taken care of."
The VA is updating its electronic medical software, and says delays are expected when moving from a paper system to one that is digital. But there is still the issue of moving medical information from military records to the VA's system.
"Despite a billion dollars that has been spent to get these two systems to unify, the Pentagon is still deciding to adopt the VA's software model," Lawrence says.
Tales of VA red tape range from the tragic to the comic, Lawrence says, citing one example where a double-amputee veteran was told his condition wasn't "chronic."
Criticism of VA secretary Shinseki's handling of the problem has come from both sides of the aisle, and some question whether his 2015 goal is even possible, Lawrence says.
"There's a strange conflict within the VA's mission," he says. "They're trying to get care to as many deserving veterans as possible, but the more successful they are at finding those veterans and signing them up, the bigger their backlog gets."
Trickling Progress
One of the people looking for those veterans is Tommy Sowers, the assistant secretary of public and intergovernmental affairs at the VA. He says the battle the agency is fighting is not an easy one.
"Some of the decisions here have been tough decisions, but right decisions," Sowers says.
He says the VA has expanded access to veterans related to Agent Orange, who have waited four decades for justice. The agency did the same thing for PTSD, he says, and expanded the number of people being treated for military sexual trauma.
"This is a challenge [and] we're making tough decisions that make it possible for more people to apply for and receive benefits," he says.
The agency is actively addressing the paperwork issue, Sowers says, and is in the process of implementing a paperless system this year. He stresses it is decades of paperwork that has piled up, and that they are essentially transitioning from a 19th century system to a 21st century system.
"Six months ago, only about 3 percent of our claims were electronic; today, nationwide that's about 18 percent," he says. "The backlog today is less than it was a year ago ... and in the past two months we've seen the backlog reduce by about 50,000 claims. We're all impatient and we're all driven to fix this."
In the meantime, Sowers says the VA does take care of emergency health care, and 56 percent of vets have used it.
Keith Lampe ~ Co-Founder of YIPPIE and Progressive Activist Groups + Video Channel
It's A Matter of Trust
A top-secret document obtained by The Washington Post shows the NSA and FBI are grabbing audio and video chats, photographs, e-mails, documents, and connection logs directly from Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, and Apple servers. (More information located in June 2013 Archive)
Google and Facebook Discussed Secret Systems
for the U.S. Government to Spy on UsersBy Pratap Chatterjee, CorpWatch, 8 June 2013, Article Source
Google and Facebook have discussed – and possibly built – special portals for the U.S. government to snoop on user data, according to revelations sparked by an investigative series of articles by Glenn Greenwald of the Guardian.
Martin Dempsey, the chairman of the Joint Chiefs of Staff (the top military adviser to the Pentagon and the White House) has made a series of trips to Silicon Valley in northern California to meet with Facebook, Google, Intel and Microsoft, to attempt to persuade the technology companies to help them spy on users.
Information about the program came out soon after the Guardian first published a secret U.S. government court order for Verizon, a major U.S. telecommunications company, to give the U.S. National Security Agency (NSA) and the Federal Bureau of Investigation (FBI) access to “metadata” on their clients phone calls. This data is arguably more important than the content of the calls, since it reveals the network of who talks to who and when, allowing patterns to be identified about individuals and groups.
The Guardian followed this up by revealing an NSA program named Prism that allowed the government to review contents of emails as well as audio and video conversations. A slide from a 41 page presentation made in April 2013, lists Facebook, Google, Microsoft, PalTalk and Yahoo and even provided the dates that the companies "joined" the scheme. It also mentions a project called “Upstream” that allows the NSA to collect information from "fiber cables and infrastructure as data flows past.”
Technology giants immediately denied all knowledge. "We have not joined any program that would give the US government – or any other government – direct access to our servers,” said Google CEO Larry Page. "Facebook is not and has never been part of any program to give the US or any other government direct access to our servers,” said Mark Zuckerberg, CEO of Facebook. "We do not provide the government with direct access to our servers, systems, or network," said a Yahoo spokesperson.
This corresponded to testimony provided by James Clapper, Director of National Intelligence, to Senator Ron Wyden in March at a Senate Intelligence Committee hearing in March. "Does the NSA collect any type of data at all on millions or hundreds of millions of Americans?" he asked. "No, sir," Clapper answered.
On Friday it turned out that each of them had lied or been misinformed. “(I)nstead of adding a back door to their servers, the companies were essentially asked to erect a locked mailbox and give the government the key, people briefed on the negotiations said,” writes Claire Cain Miller in the New York Times. “Facebook, for instance, built such a system for requesting and sharing the information, they said.”
On Friday, President Barack Obama acknowledged the existence of both programs but said people should not be worried: “Nobody is listening to your telephone calls,” he said at a press conference. “That's not what this program is about. As was indicated, what the intelligence community is doing is looking at phone numbers and durations of calls. They are not looking at people's names, and they're not looking at content. But by sifting through this so-called metadata, they may identify potential leads with respect to folks who might engage in terrorism”
Ben Wizner, director of the American Civil Liberties Union’s Speech, Privacy & Technology Project, explains however that tracking metadata is actually far more significant and worrisome. “Repeated calls to Alcoholics Anonymous, hotlines for gay teens, abortion clinics or a gambling bookie may tell you all you need to know about a person’s problems,” Wizner wrote in an op-ed with his collageue, Jay Stanley. “In addition sophisticated data-mining technologies have compounded the privacy implications by allowing the government to analyze terabytes of metadata and reveal far more details about a person’s life than ever before. So we shouldn’t be comforted when government officials reassure us that they’re not listening to our communications – they’re merely harvesting and mining our metadata.”
Rainbow Puddle ~ Stellar Light Shows + YouTube Video Channel
This is the likely end of "FELA On Broadway" World Tour
FELA On Broadway is at the Paramount Theatre, Oakland, CA (June 4 – 9, 2013) ~ Closes Sunday June 9th ~ Hope you can make it.
Dear Friends,
Some of you are aware FELA On Broadway purchased my Liquid Light to use behind dancers in the Broadway production. They also used several projectors to splash the Liquid all over the house! (Towards the end of the 1st Act, after the audience is asked to stand.)
Some of you may even have seen the Tony Awards that featured the FELA ensemble performing with my Liquid Light splashing behind them on National Television!
FELA received several Tony's, among them, Mr. T. Bill Jones won for Best Choreography. I am informed by the FELA's Video Director that my Liquid Light ignited and energized the number!
[Ed. Note: For the record it was the Bush Administration, with political support from both Democrats and Republicans, who authorized SPYING on U.S. citizens; while giving Telecoms a free pass for knowingly breaking law, and then passed an illegal Patriot Act, without ever reading it. These are the same baby killers & child rapers, for the most part, who voted for an illegal Iraq war, based on nothing but lies, supported Israel's murder and maiming of United States Naval personnel aboard the USS Liberty, supplied Iraq with biological and chemical weapons from U.S. manufacturers, appointed Bush president, and more than likely had something to do with the mass murders of 9/11. It would appear Politicians work for themselves; not the public, ... that None of the Above should be a choice on voter ballots, and Nobody should be president !!!]
White House defends Verizon phone record collection
Reporting by Susan Heavey; Editing by Vicki Allen, REUTERS, Thu. 06 June 2013, Article Source
WASHINGTON (Reuters) - The Obama administration on Thursday acknowledged that it is collecting a massive amount of telephone records from at least one carrier, defending the practice as "a critical tool in protecting the nation from terrorist threats to the United States."
The admission comes after the Guardian newspaper published a secret court order related to the records of millions of Verizon Communications customers on its website on Wednesday.
A senior administration official said the court order pertains only to data such as a telephone number or the length of a call, and not the subscribers' identities or the content of people's telephone calls.
Notes from ~@~
Hi Folks,
That Summer feeling is right around the bend here in West Coast Norway. I'm still kicking, writing, performing and recording!
Looking forward to my solo appearance at Egersund Visefestival July 6th:
A couple of new projects coming up later this Fall:
All new ERIK MOLL BAND with new Bergen musicians/friends playing Moll classics at Madam Felle in Bergen Sept 20th.
TEXANOS is a Bergen band/texmex extravaganza performing songs by Texas Tornados, Los Lobos, Mavericks and other covers as well as some original Erik Moll tunes in the genre. Madam Felle Oct. 26th.
A new all acoustic album is in the works. It's my first time recording some of the tracks myself. Eclectic (of course) with bluegrass overtones here and there. Hope for release in Fall/Winter.
All the best from the fjords!
Em
Dick Van Dyke Traces Mystery Illness to Dental Implants
By Sylvia Booth Hubbard, NewsmaxHealth, Monday, 03 Jun 2013 01:07 PM, Article Source, via Joe
Legendary actor Dick Van Dyke says he has solved a medical mystery that has baffled him and his doctors for years. The cause of pounding headaches that have plagued him for seven years are his titanium dental implants, he says.
Fans and friends of the 87-year-old star had been concerned about his health ever since he canceled a public appearance in April and announced that he was fatigued and suffered from insomnia as a result of an undiagnosed neurological disorder.
Van Dyke was so desperate that he appealed for help from his fans through Twitter. "My head bangs every time I lay down," he said. "I've had every test come back that I'm perfectly healthy. Anybody got any ideas?"
The beloved star of TV's The Dick Van Dyke Show and the movie Mary Poppins added, "It's been going on for seven years. I've had every test you can think of, including an MRI and spinal tap."
Van Dyke took to Twitter again to announce that the source of his mystery illness had been discovered — titanium dental implants. "It seems that my titanium dental implants are the cause of my head pounding," he Tweeted. "Has anyone else experienced this?" he asked. "Thanks for all your replies."
Dental implants replace damaged or missing teeth. The "roots," which are usually made from titanium, are placed within the jawbone.
Dr. David Brownstein, holistic doctor and author of Dr. Brownstein's Natural Way to Health newsletter, says that problems with dental implants often cause patients to go from doctor to doctor for years without finding a solution. "As long as there's no infection, no one considers the implants as the source of the patient's problems," he tells Newsmax Health.
There are tests for titanium allergies, says Dr. Brownstein, but that doesn't explain what happened to Dick Van Dyke.
"Titanium is metal and it creates kind of a lightning rod in the head," he said. "It doesn't happen to everyone, and most doctors don't look for it. Most people have other metals in their mouths, like fillings, and saliva combines with the metal to give a battery-like effect.
"Any metal can do this, and it can be a big problem," he says. "I just had a patient with issues similar to Van Dyke's — headaches and facial pain that no one could identify."
Although titanium is generally considered safe, one study showed that patients had severe health problems after receiving dental implants. Medical issues included neurological problems, depression, and chronic fatigue syndrome. Once the implants were removed, the patients' health improved dramatically.
Studies have also found that implanted titanium can cause abnormal cells to form, which could precede the beginning of oral cancer. Two articles published in the Journal of the American Dental Association indicated that dental implants either caused or aggravated oral cancers.
"There's no easy answer," Dr. Brownstein says. "If a patient has a hole in his mouth, his bite is going to be compromised. The dentist is going to have to do something to fix that space and most of the answers involve some kind of metal.
"I don't advise people not to have dental implants," he says. "I am just cautious and say that if problems develop, the implants should be considered as a possible cause."
Zirconium dental implants, which use high-impact ceramic (zirconium oxide), are more compatible with the human body and may be a safer choice. "Zirconium is an inert metal, and zirconium implants are becoming more widely available in this country," says Dr. Brownstein.
"I think zirconium would be a better choice than titanium.
"Putting any type of metal in the mouth can disrupt the electrical activity and result in a lot of problems," says Dr. Brownstein. "This includes fillings, root canals, caps, bridges, and implants.
So, if you are suffering and not getting any answers, fillings, root canals, and implants should be considered as possibly upsetting the electrical activity of the head and neck causing headaches, brain fog, and other symptoms people don't ordinarily connect with dental implants."
I celebrate the defiance in Pussy Riot's eyes
As Maria Alyokhina's hunger strike continues, her strength inspires others as much as it scares the Russian state
Romola Garai, The Guardian, Friday 31 May 2013 14.30 EDT, Article Source
Pussy Riot 'speak in a language of political protest that my generation has all but abandoned'. Illustration by OttoIn the midst of Russia's Ural mountains lies the industrial town of Berezniki. It is not a town famous for anything much but its contribution as the world's largest supplier of potash is about to be overshadowed. And yet this fame may not be the kind it would like on its Wikipedia page.
As of today, Maria Alyokhina, a member of the Russian punk feminist collective Pussy Riot, is on the 10th day of a hunger strike. She is protesting at the decision of prison officials to prevent her from attending a parole hearing that might have cut short the sentence she is currently serving in Berezniki's prison camp. As it happened she was subsequently denied parole anyway.
The reason for her parole being refused was that she had "failed to repent for her crime". And what was this crime? The crime that landed her two years' imprisonment in a remote jail, five months of which she has spent in solitary confinement? Just over a year ago she and three other members of the feminist punk-rock collective Pussy Riot danced around the altar of Christ the Saviour Cathedral in Moscow while shouting, "Mother of God, blessed Virgin, drive out Putin." Two years! For disrespecting the church?
But, of course, protecting the delicate sensibilities of the Russian Orthodox church is not the true reason for the unusually punitive attitude of the Russian authorities towards these women (for example, the legal right of two of them to suspend their sentence on account of being mothers was denied).
The two-year sentence was as clear a signal as you could ask for that this grassroots feminist, anti-authoritarian and anti-Putin protest movement had the powers that be well and truly scared. The Russian authorities fear the example that a protest movement can move off the streets and into direct action, even if it's nonviolent action, and this fear is the driving force behind Alyokhina's continued persecution.
For me, the case of Pussy Riot has been a great political awakening for two important reasons. First, they are young idealists. They identify themselves as being part of a younger generation who are not represented by Russia's new autocracy. Alyokhina herself states: "When we talk about Putin, we have in mind first and foremost not Vladimir Vladimirovich Putin but the system that he himself created – the power vertical, where all control is carried out effectively by one person. And that power vertical is uninterested, completely uninterested, in the opinion of the masses. And what worries me most of all is that the opinion of the younger generations is not taken into consideration."
They speak in a language of political protest that my generation has all but abandoned. The language of freedom-fighting was so co-opted by the baby boomers in order to express their now hopelessly compromised ideologies that no other generation could emulate it without a smirk. This has created an apathetic generation in the west, with young people no longer distinguishing between the old order and the new. To see a protest movement with its young members employing this language suggests a hopefulness and rage that I feel is intensely important for others of their generation to see, and that I personally have found deeply inspiring.
Second, they embody a real feminist anger and uncompromisingly scornful attitude to the patriarchal values that women have been taught to accept as the status quo. They reject the pantomime of equality in which we are expected to perform. Women in the public eye who can genuinely be called nonconformist are vital for expanding the horizons of other women. It was figures such as the musicians Kim Gordon and PJ Harvey who taught me, when I was 14, what a truly independent spirit looked like. When I see what my daughter will be told a "strong woman" looks like, I see women in their underwear sucking in their tummies with a look of terror on their faces. This isn't what I want for her and I celebrate the obvious, unadulterated "fuck you" that lies behind Pussy Riot's eyes.
When I took part in an event hosted by the Royal Court theatre last year, where myself and a group of other actors performed some plays inspired by Pussy Riot, interspersed with their writings, I had the chance to dress up in pink tights and a fluoro balaclava and jump up and down and scream and shout – and all this when I was six months pregnant. It was a treat to get the chance to be them for a moment, to replicate the courage and exuberance of their moment of protest in the cathedral.
But I am glad I am not sharing a moment in Maria Alyokhina's life today. Cruelly separated from her child, enduring months in solitary confinement, threatened with violence and with the might of the Russian state squaring up to her – when faced with a fate such as this I would undoubtedly crumble. But that's why I'm not in Pussy Riot: they are made of stronger stuff. Putin – beware.
• The headline for this article was amended on 2 June 2013 because the original was inconsistent with Guardian editorial guidelines. This has been corrected.
Amestizo ~ BLOG + NEW: http://amestizo.bigcartel.com/
Be proud of being the mean between macrocosm and microcosm. Stand still and marvel.
Try not to become a man of success, but a man of value.
Look around at how people want to get more than he receives.
Be creative, but make sure that what you create is not a curse for mankind.” Albert Einstein,
in Einstein and the Poet – In Search of the Cosmic Man by William Hermanns
(Branden Press, 1983, p. 143. ~ www.williamhermanns.com)
Paul Krassner ~ The Realist/Writer/Comic/Investigative Satirist
Who Do You Think Created the Term Yippie?
By Paul Krassner, AlterNet, June3, 2013, Article Source
I really don't like to boast, but in my lifetime, on half a dozen occasions, I have actually added words and phrases to the language. It's something I always wanted to do. What a thrill it must have been Dr. Harold Cerumen who decided that cleaning out earwax should be known as "cerumen disimpaction." And veterinarian Alice Neuticle who coined the word "neuticles" -- cosmetic testicles for a dog that's been neutered.
So I'm not asking for credit. Or cash. Since money had been called "dough" and then morphed into "bread," so I figured that "toast" would be the next logical step in that particular linguistic evolution, but my campaign itself became toast, in the sense that "toast" now means history.
Also, I was intrigued by the process of having a body part named after oneself. How proud Casper Bartholin's parents must have been to have a son who christened the source of female lubrication that takes the friction out of intercourse as "Bartholin's glands." But my idea of calling those two vertical lines between your nose and your mouth "Krassner's crease" just never became popular.
Here, then, for better or worse, are my contributions to American culture that did manage to catch on, or at least may be on their way.
1. In 1958, pornography was gradually becoming legal, but at that stage of the game, the Supreme Court was unwilling to allow 1st Amendment protection of "hard-core" porn--as opposed, I assumed, to the term I invented, "soft-core porn," which was obviously more respectable, though it seemed kind of sneaky, pretending to be squeaky clean. So I decided to satirize the concept with a new feature in The Realist: "Soft-Core Porn of the Month."
For example, phallic symbolism in newspapers and magazines was a key ingredient of soft-core porn. Sample: a close-up of a stick shift in a Volkswagen ad was accompanied by the question, "Does the stick shift your wife?" Soft-core porn now refers to limited sexuality, as seen in network TV dramas and hotel-room movies that feature jiggling breasts and buttocks but no genitalia. The way to recognize soft-core porn is that it gives men a soft-on.
2. On the afternoon of December 31, 1967, several activist friends were gathered at Abbie and Anita Hoffman's Lower East Side apartment, smoking Columbian marijuana and planning a counter-convention for the Democratic Party's event the following summer in Chicago. Our fantasy was to counter their convention of death with our festival of life. While the Democrats would present politicians giving speeches at the convention center, we would present rock bands playing in the park. There would be booths with information about drugs and alternatives to the draft. Our mere presence would be our statement.
We needed a name, so that reporters could have a who for their journalistic who-what-when-where-and-why lead paragraphs. I felt a brainstorm coming on and went to the bedroom so that I could concentrate. Our working title was the International Youth Festival. But the initials IYF were a meaningless acronym. I paced back and forth, juggling titles to see if I could come up with words whose initials would make a good acronym. I tried Youth International Festival. YIF. Sounded like KIF. Kids International Festival? Nope, too contrived. Back to YIF. But what could make YIP? Now that would be ideal because then the word Yippie could be derived organically.
Of course, "Yippie" was already a traditional shout of spontaneous joy, but we could be the Yippies! It had exactly the right attitude. Yippies was the most appropriate name to signify the radicalization of hippies. What a perfect media myth that would be--the Yippies! And then, working backward, it hit me. Youth International Party! It was a natural. Youth: This was essentially a movement of young people involved in a generational struggle. International: It was happening all over the globe, from Mexico to France, from Germany to Japan. And Party: In both senses of the word. We would be a party and we would have a party.
Yippie was only a label to describe a phenomenon that already existed -- an organic coalition of psychedelic dropouts and political activists. There was no separation between our culture and our politics. In the process of cross-pollination, we had come to share an awareness that there was a linear connection between putting kids in prison for smoking marijuana in this country and burning them to death with napalm on the other side of the planet. It was just the ultimate extension of dehumanization. But now reporters had a who for their lead paragraphs. A headline in the Chicago Daily News summed it up: "Yipes! The Yippies Are Coming!" Our myth was becoming a reality.
3. In 1972, I found myself smoking a combination of marijuana and opium with John Lennon and Yoko Ono. Lennon was absentmindedly holding on to the joint, and I asked him, "Do the British use that expression, 'Don't bogart that joint,' or is it only an American term–you know, derived from the image of a cigarette dangling from Humphrey Bogart's lip?" He replied, with a twinkle in his eye, "In England, if you remind somebody else to pass a joint, you lose your own turn." Since Bogart and Lauren Bacall were a classic Hollywood couple, I was inspired by that snippet of dialogue to say, "Don't bacall that joint."
4. Intuitively, I was an advocate of equal rights and opportunities for both genders long before Women's Liberation became a movement. In 1959, I wrote, "From a completely idealistic viewpoint, classified ads for jobs should not have separate Male and Female classifications, with exceptions such as a wet-nurse." In 1964, that practice became illegal. Masturbation was a powerful taboo for females, a subdivision of the war on pleasure, while it was somehow expected of males. But if it was okay for guys to jack-off, I wrote in a media fable, Tales of Tongue Fu, in 1974, then it was also okay for girls to jill-off.
5. In 1979, I covered for a weekly alternative paper the trial of ex-cop Dan White for the double execution of San Francisco Mayor George Moscone and Supervisor Harvey Milk, the gay equivalent of Martin Luther King. In a surprise move, homophobic White's defense team presented a bio-chemical explanation of his behavior, blaming it on compulsive gobbling down of sugar-filled junk-food snacks. This was a purely accidental tactic. Dale Metcalf, a former member of Ken Kesey's Merry Pranksters who had become a lawyer, told me how he happened to be playing chess with one of White's attorneys, Steven Scherr.
Metcalf had just read Orthomolecular Nutrition by Abram Hoffer. He questioned Scherr about White's diet and learned that, while under stress, White would consume candy bars and soft drinka. Metcalf recommended the book to Scherr, suggesting the author as an expert witness. In his book, Hoffer revealed a personal vendetta against doughnuts, and White had once eaten five doughnuts in a row.
During the trial, psychiatrist Martin Blinder testified that, on the night before the murders, while White was "getting depressed about the fact he would not be reappointed [as supervisor, after having quit], he just sat there in front of the TV set, bingeing on Twinkies." In my notebook, I scribbled "Twinkie defense," and wrote about it in my next report.
In the wake of the Twinkie defense, a representative of the Continental Baking Company asserted that the notion that overdosing on the cream-filled goodies could lead to murderous behavior was "poppycock" and "crap"--apparently two of the artificial ingredients in Twinkies, along with sodium pyrophosphate and yellow dye--while another spokesperson couldn't believe "that a rational jury paid serious attention to that issue." Nevertheless, some jurors did. One remarked after the trial that "It sounded like Dan White had hypoglycemia."
Later, the San Francisco Chronicle reported: "During the trial, no one but well-known satirist Paul Krassner -- who may have coined the phrase ‘Twinkie defense' -- played up that angle. His trial stories appeared in the San Francisco Bay Guardian."
6. Twitter is an interesting phenomenon. It's perfect for those folks with a short attention span, and it's scary for paranoids who don't want to be followed. It appeals to minimalists, such as, say, Bob Dylan. I once asked him, "How come you're taking Hebrew lessons?" He responded, "I can't speak it."
Tweets range from the trivial (David Gregory announcing that he was going to eat a bagel before moderating Meet the Press) to international conflicts (Iranian citizens reporting on the uprising against their repressive government). It occurred to me that there could be classic haiku tweets--three lines consisting of 5 syllables, 7 syllables and 5 syllables--adding up obviously to no more than 140 characters--and so I decided to embed the phrase I coined in the following haiku:
What's worth sharing now?
World War Three or stubbed my toe?
I have Twitter's Block.
Saquasohuh
In Hopi mythology, The Blue Star Kachina or Saquasohuh, is a kachina or spirit, that will signify the coming of the end of the world by appearing in the form of a blue star. The Blue Star Kachina is said to be the ninth and final sign before the "The Day of Purification," described as a catastrophe or a "world engulfing cataclysm" that will lead to the destruction of the Earth. Some have interpreted the prophecy of the Blue Star Kachina to be a reference to the impending arrival of extraterrestrial life.
Never-Before-Seen Alien Planet Caught on Camera
Miriam Kramer for Space.com, Date: 03 June 2013 Time: 06:00 AM ET, Article Source
Planet HD 95086 b in orbit around sun HD 95086A newly discovered gaseous planet has been directly photographed orbiting a star about 300 light-years from Earth. Imaging alien planets is difficult, and this world may be the least massive planet directly observed outside of the solar system, scientists say.
A sharp new photo released by the European Southern Observatory (ESO) today depicts the suspected gas giant (called HD 95086 b) circling its young star (named HD 95086) in infrared light. The star has been removed from the image to allow the planet — shown as a bright blue dot at the bottom left of the picture — to shine through.
HD 95086 b was sighted by ESO's Very Large Telescope in Chile. Based on the planet's brightness, scientists estimate that it is only about four or five times more massive than Jupiter. See Amazing Photos of the Very Large Telescope
Most exoplanets are discovered via indirect means, such as detecting a dip in a star's light when a planet passes in front of it, blocking part of its face, or finding a slight wobble in a star's movement caused by the gravitational tug of planets orbiting it.
"Direct imaging of planets is an extremely challenging technique that requires the most advanced instruments, whether ground-based or in space," Julien Rameau, an astronomer at the Institute of Astrophysics and Planetology in France and lead author of the study announcing the discovery, said in a statement. "Only a few planets have been directly observed so far, making every single discovery an important milestone on the road to understanding giant planets and how they form."
Another photo [at site] from ESO shows the star and its planet in context with other stars in the southern constellation of Carina, the keel.
The planet orbits its star at about twice the distance from the sun to Neptune and about 56 times the distance between Earth and the sun. The blue circle in the photo represents the distance between the sun and Neptune.
HD 95086 is relatively young star at only 10 million to 17 million years old, making the formation of the exoplanet and the dusty disc surrounding the star potentially intriguing to researchers.
"[The planet's] current location raises questions about its formation process," Anne-Marie Lagrange, one of Rameau's team members, said in a statement. "It either grew by assembling the rocks that form the solid core and then slowly accumulated gas from the environment to form the heavy atmosphere, or started forming from a gaseous clump that arose from gravitational instabilities in the disc. Interactions between the planet and the disc itself or with other planets may have also moved the planet from where it was born."
The research will be published in an upcoming issue of Astrophysical Journal Letters.
Image courtesy of ESO/J. Rameau
Native American Prophecies
Here are some Hopi native North American prophecies relating to the end times. The first three were made famous by the cult 70s movie, Koyaanisqatsi. They were shown right at the end.
"If we dig precious things from the land, we will invite disaster."
[Ed. Note: Does the above sound like fracking?]
"Near the day of Purification, there will be cobwebs spun back and forth in the sky."
[Ed. Note: Does the above sound like chemtrails?]
"A container of ashes might one day be thrown from the sky, which could burn the land and boil the oceans."
Prophecies of White Feather, a Hopi of the ancient Bear Clan
"He will bring with him the symbols, and the missing piece of that sacred tablet now kept by the elders, given to him when he left, that shall identify him as our True White Brother.
"The Fourth World shall end soon, and the Fifth World will begin. This the elders everywhere know. The Signs over many years have been fulfilled, and so few are left.
"This is the First Sign: We are told of the coming of the white-skinned men, like Pahana, but not living like Pahana men who took the land that was not theirs. And men who struck their enemies with thunder.
"This is the Second Sign: Our lands will see the coming of spinning wheels filled with voices. In his youth, my father saw this prophecy come true with his eyes -- the white men bringing their families in wagons across the prairies."
"This is the Third Sign: A strange beast like a buffalo but with great long horns, will overrun the land in large numbers. These White Feather saw with his eyes -- the coming of the white men's cattle."
"This is the Fourth Sign: The land will be crossed by snakes of iron."
"This is the Fifth Sign: The land shall be criss-crossed by a giant spider's web."
"This is the Sixth sign: The land shall be criss-crossed with rivers of stone that make pictures in the sun."
"This is the Seventh Sign: You will hear of the sea turning black, and many living things dying because of it."
[Ed. Note: Does the above sound like an Oil Spill?]
"This is the Eight Sign: You will see many youth, who wear their hair long like my people, come and join the tribal nations, to learn their ways and wisdom.
"And this is the Ninth and Last Sign: You will hear of a dwelling-place in the heavens, above the earth, that shall fall with a great crash. It will appear as a blue star. Very soon after this, the ceremonies of my people will cease.
"These are the Signs that great destruction is coming. The world shall rock to and fro. The white man will battle against other people in other lands -- with those who possessed the first light of wisdom. There will be many columns of smoke and fire such as White Feather has seen the white man make in the deserts not far from here. Only those which come will cause disease and a great dying. Many of my people, understanding the prophecies, shall be safe. Those who stay and live in the places of my people also shall be safe. Then there will be much to rebuild. And soon -- very soon afterward -- Pahana will return. He shall bring with him the dawn of the Fifth World. He shall plant the seeds of his wisdom in their hearts. Even now the seeds are being planted. These shall smooth the way to the Emergence into the Fifth World.
"But White Feather shall not see it. I am old and dying. You -- perhaps will see it. In time, in time..."
Mohawk Prophecy of the Seventh Generation
According to the prophecy of the Seventh Generation, seven generations after contact with the Europeans the Onkwehonwe would see the day when the elm trees would die. The prophecy said that strange animals would be born deformed and without the proper limbs. Huge stone monsters would tear open the face of the earth. The rivers would burn. The air would burn the eyes of man. According to the prophecy of the Seventh Generation the Onkwehonwe would see the time when the birds would fall from the sky. The fish would die in the water. And man would grow ashamed of the way that he had treated his Mother and Provider, the Earth.
Finally, according to this prophecy, after seven generations of living in close contact with the Europeans, the Onkwehonwe would rise up and demand that their rights and stewardship over the Earth be respected and restored.
According to the wisdom of this prophecy, men and women would one day turn to the Onkwehonwe for both guidance and direction. It is up to the present generation of youth of the Kanienkehaka to provide leadership and example to all who have failed. The children of the Kanienkehaka are the seventh generation.
Observer rather than Victim
Players are aware there is an ability to go above things, in order to make change or make IT better and have an ability to become Observer rather than Victim.
It was previously noted the general timeline is off.
It was also previously noted simple musical references were slipped through from the other side. For example, "You know something is happening, but you do not know what it is," "There's something happening here What it is ain't exactly clear," "Imagine all the people Living life in peace, You, you may say I'm a dreamer, But I'm not the only one, I hope someday you will join us, And the world will be as one," helped manifest choice.
During the '70s there were these 'science faction' (sic) messages:
UFO message sent via morse code on high frequency radio ~ Click to play MP3
Rebirth of Evil, shoved through mail slot in brown paper bag ~ Click to play MP3
It was also mentioned there was something, beyond duality, nobody understood, that collapsed the wave form prematurely (before its time) causing wide dispersal of particles; most of which, did not arrive whole.
(otoh) Multiple failsafe's (Human Be-In, Woodstock, etc.) did a decent job locating and collecting missing pieces. ;-)
Be Aware: The Nexus Approaches!
Posted on October 10, 2010 by mayasoma, 10-10-10 Star Gate Portal
"The human race is headed towards a great change, many spirits will return to the stars and something magnificent is going to happen!" - Astral Walker
Can you feel it? The race is on, the diaspora has begun and souls are scrambling to make sense of the intensifying energies on Planet Earth. If only our history books had documented the truth of the astrological cycles as the Maya, and many other indigenous tribes, have long done for their own people, then there would not be so much uncertainty and fear. Unfortunately, that is not how this part of our homo-sapien history is to be played out. At present, the 3D world is going crazy and the only way to manuever these times is to understand the facts. And so, without further ado, here is some of our history…
26,000 years ago, the galactic center of the Milky Way emitted an enormous energetic wave better known as the Nexus. It does this every 26,000 years, as they say, there is nothing new under the sun. This emissions are what have caused the tumultuous transitions from each of our previous world eras. If you are not familiar with these facts, simply research indigenous tribes and their 1st, 2nd, 3rd, 4th, and soon to be 5th worlds.
What was released all that time ago will soon reach our earth in full strength. The Nexus has its own personal rhythm and does take some time to cross the galaxies and skies. I believe its arrival correlates to the Mayan Long Count End Date of December 2012. Afterall, the center of the Milky Way is where the Maya believe their Creator Hunab Ku resides. Our Creator has sent out an energy impulse, this Supreme Being is blowing us/creation a kiss. Unfortunately, our consciousness resides too far away from our original empowered selves to simply receive that kiss in bliss.
That incoming energy is meant to completely change our world, in other words, to wake us all up to who we are: infinite Gods and Goddesses with incredible abilities and powers. This incoming beam of bluish-white light will alter and restore our DNA from its current state which only uses 3% of its capacities to a renewed state of 100% remembrance. Translated: 97% of what scientist call junk DNA will be reactivated. WoW…a jolt of electricity that courses through our veins, awakening our souls and minds. No one is going to escape this phenomena. Thank you Hunab Ku!
Our main problem lies then with the Dark Lords who currently control the 3D world. They are also fully aware of the approaching Nexus and have set out a program to depopulate the Earth as much as possible. Why would they do that? Who are these Dark Lords? It’s an old story, again, much of our missing history, but the short and long version of it is there is an inter-galalctic battle on right now, a war that is being waged for souls. If the Dark Lords, negative Et’s, have their way, the coming earth catastrophes will take people into fear and fear is a place where they can trap one’s soul, one’s consciousness, forevermore. On a distant planet, in a distant place, maybe somewhere that looks exactly like our Earth, a new slave race can be created with the trapped souls. The Dark Lords know, full well, that their “time” on Planet Earth is over. A new era has cometh… the age of peace and enlightenment…and they must flee. They intend to flee with as many captives as possible. Sound like a bad sci-fi movie? I wish it were, but these are our current events and the facts are unknown to almost everyone. How frightening! Wake up, please, before you are whisked away to another dimension without personal agreement to do so.
“Right now the realm of darkness is not interested in this (peace). They are organized to block it. They seek to unbalance the Earth and its environment so we will be unready for the alignment in 2012.” - Carlos Barrios, Mayan Datekeeper
Take a look around…. ecological disasters leading to worldwide famines and extinction, environmental catastrophes that destroy the lives of millions, economical collapses that create a fearful, dependent race and threats of terrorism and world wars loom over our existence. Is this the four horsemen spoken of in the Book of Revelations? It clearly is the workings of the Dark Lords and its about to get more intense, after all, these are their death throes.
“From that 1987 date until now, Mr. Barrios says, we have been in a time when the right arm of the materialistic world is disappearing, slowly but inexorably. We are at the cusp of the era when peace begins, and people live in harmony with Mother Earth. We are no longer in the World of the Fourth Sun, but we are not yet in the World of the Fifth Sun. This is the time in-between, the time of transition.
As we pass through transition there is a colossal, global convergence of environmental destruction, social chaos, war, and ongoing Earth changes. All this, Mr. Barrios says, was foreseen via the simple, spiral mathematics of the Mayan calendars. It will change, Mr. Barrios observes. Everything will change. He said Mayan Daykeepers view the Dec. 21, 2012 date as a rebirth, the start of the World of the Fifth Sun. It will be the start of a new era resulting from — and signified by — the solar meridian crossing the galactic equator, and the earth aligning itself with the center of the galaxy.” - Carlos Barrios, Mayan Datekeeper
Meanwhile, the Family of Light is exerting every effort for a mass awakening, for gathering, for consciously uniting as we know on some level that everything is dependent on us to do so. We are supposed to be creating an astral force field around the planet and ourselves in the shape of the Flower of Life (see Drunvalo Melchizedek’s work on this matter for more information). This symbol can and will prepare us for the enormity of the approaching Nexus. We are supposed to be clearing our fields as much as possible of debris, creating no new karma, so that we are a crystal clear channel for receiving the Nexus energy. We must give praise and thanks as we have received, and will continue to receive, so much help from the Galactic Federation of positive Et’s.
I ask myself though, have enough souls awoken to make this transition happen with ease? Can geological earth disasters be diminished? The Dark Lords are earnestly working hard to create as many earth catastrophes as possible in these last days in order to capture their slave race of unaware humans. Many will succumb to this fate due to fear, many will go to the stars as their earth contracts are complete, and a handful of ascended beings will remain on the New Earth.
If you happened to be a person who was to die in shock and fear, your consciousness would be lost and confused on the astral plane for a moment. It is in those crucial moments that the negative Et’s can and will capture your essence in a containment vehicle if you are not aware. As quickly as you come into consciousness, get to the benevolent blue light. I have been warned not to be drawn down any tunnels or caves, nor gravitate to any bright yellow-red lights and by no means go with any beckoning ET’s.
The benevolent ET’s, the light ones, are calling us home and their bioluminescent blue-white light is the signal. You can feel this with your heart. They have said Operation Victory is at hand. They have stated that the Dark Lords cannot succeed and all disasters will be minimized (let’s hope so as some seriously dangerous threats are presenting themselves on the earth right now). They have also said the Dark Lords are at their most dangerous as they face defeat, so it is crucial to be fully present! Be aware! Vaccines? Genetically modified foods? Chemical spraying? Understand, these are some of their tools for mind control and keeping the masses asleep. Whatever cometh, wherever you find yourself in these last days where we count days, simply remember, you have only one thing to do: get to the bluish-white light, reach out for the Nexus. If you do, your full consciousness will be re-instated and you will be safe and empowered.
Let us recall the last sign in the Hopi prophecy which states that a blue planet from the Heavens will crash into Earth causing earth destruction, this last sign is what all elders are awaiting as our entry into the 5th world. Possibly, it is not a planet, but an energy wave: the Nexus?
Lightwalkers, we are going home now. We have felt the Nexus approaching for years, even if we could or could not put words to it. Our Creator desires our remembrance and this collective shift to magnificence is welcome. Stay in your heart and the Dark Lords will lose power. It is promised and all is well!
Navajo, awaiting portal 11-11-11 and 12-12-12 to the Nexus! - Source
John Titor on Civil War
I remember 2036 very clearly. It is difficult to describe 2036 in detail without spending a great deal of time explaining why things are so different.
In 2036, I live in central Florida with my family and I'm currently stationed at an Army base in Tampa. A world war in 2015 killed nearly three billion people. The people that survived grew closer together. Life is centered on the family and then the community. I cannot imagine living even a few hundred miles away from my parents.
There is no large industrial complex creating masses of useless food and recreational items. Food and livestock is grown and sold locally. People spend much more time reading and talking together face to face. Religion is taken seriously and everyone can multiply and divide in their heads.
Life has changed so much over my lifetime that it's hard to pin down a "normal" day. When I was 13, I was a soldier. As a teenager, I helped my dad haul cargo. I went to college when I was 31 and I was recruited to "time travel" shortly after that. Again, I suppose an average day in 2036 is like an average day on the farm.
There is a civil war in the United States that starts in 2005. That conflict flares up and down for 10 years. In 2015, Russia launches a nuclear strike against the major cities in the United States (which is the "other side" of the civil war from my perspective), China and Europe. The United States counter attacks. The US cities are destroyed along with the AFE (American Federal Empire)...thus we (in the country) won. The European Union and China were also destroyed. Russia is now our largest trading partner and the Capitol of the US was moved to Omaha Nebraska.
One of the biggest reasons why food production is localized is because the environment is affected with disease and radiation. We are making huge strides in getting it cleaned up. Water is produced on a community level and we do eat meat that we raise ourselves.
After the war, early new communities gathered around the current Universities. That's where the libraries were. I went to school at Fort UF, which is now called the University of Florida. Not too much is different except the military is large part of people's life and we spend a great deal of time in the fields and farms at the "University" or Fort.
The Constitution was changed after the war. We have 5 presidents that are voted in and out on different term periods. The vice president is the president of the senate and they are voted separately. ~ John Titor
So... What Is Really Going On In SiFi World?
There are time travelers, from way in the future, trying to prevent their demise, due to pollution originating during the 20th and 21st centuries.
There are misguided time travelers, from a not so distant future, who are running through time, trying to manipulate religion because they believe they are with sin, feel compelled to destroy two thirds (2/3) of all living things on Earth in order to survive, and are setting the stage for an alleged Messiah to manifest.
There are several species of aliens and hybrids who are constantly breaking Prime Directive.
There is more and above only touches the surface. The good news is, 'this time there is more than one' and, as usual, everything is perfect.
To Unowho:
Stop attempting to use time to modify history or your timeline will be modified to eliminate your source of discovery, which will be reintroduced later, when your species has learned not to kill for no reason!
You must know your changes do not hold and are not permanent because your math is off. You are affecting something beyond your limited intelligence and a few examples would include extreme weather patterns and intensive sunspots directed at Earth.
For what it is worth, it is impossible for you to correct this before Satya yuga (Golden Age), when you finally lose, and become the small dark dot in a massive amount of light.
It is also known what you did in Mesopotamia and Canaan, how Ishmael's birthright was modified, and what you did in Patmos and Constantinople, to name a few, and one might want to question the concept of an invisible, no likenesses, and no pictures deity.
Finally, it appears you have been down voted into oblivion.
Just Saying ...
Arrest Bush Administration for Betraying U.S. Veterans
By Dahbud Mensch, U.S. Military, Vietnam Veteran, Honorable Discharge with Recommendation
Betrayal of American Veterans
Americans who volunteer for military service effectively write a blank check, payable to the United States of America for an amount "up to and including my life." The United States, in turn, promises to spend these checks responsibly. That bargain implicitly includes a promise by the United States to protect them and to seek retribution against anyone who harms them. In the case of USS Liberty and War Criminal Bush Administration (previous link posted October 28, 2004), the United States has failed to keep its end of the bargain.
"George Bush sent people to war without body armor."
50,000 started war without body armor
Hillary Clinton on Thursday, January 31st, 2008 in a debate in Los Angeles, Article Source
In the Democratic debate in Los Angeles on Jan. 31, 2008, Sen. Hillary Clinton criticized the Bush administration for failing to give American soldiers in Iraq the resources they require. She leveled this accusation: "We had to fight to get body armor. You know, George Bush sent people to war without body armor." The issue of body armor — who gets it and whether it's the right kind — has been a source of intense scrutiny nearly from the start of the war in Iraq.
A March 7, 2005, story in the New York Times by reporter Michael Moss detailed a deadly miscalculation by the military near the start of the war in April 2003. Army Gen. Richard A. Cody decided to stop buying bulletproof vests after a determination that some 50,000 soldiers not on the front lines could do without them. In the following weeks, Moss wrote, "Iraqi snipers and suicide bombers stepped up deadly attacks, often directed at those very soldiers behind the front lines." Cody quickly ordered bulletproof vests for every soldier. But it took 167 days to start getting those vests to soldiers due to production and paperwork delays. Some soldiers waited months more.
Many soldiers heading to Iraq bought their own body armor despite assurances from the military that it would be provided.
In April 2005, the Government Accountability Office reported on shortages of critical force protection items, including individual body armor. The problems were caused, the report concluded, due to materials shortages, production limitations and distribution problems.
But by and large, everyone eventually got body armor.
In ensuing years, the issue became whether the military was using the right kind.
In January 2006, the New York Times cited a secret Pentagon study that found that as many as 80 percent of the Marines killed in Iraq from wounds to the upper body could have survived if they had body armor that reached a soldier's shoulders, sides and torso.
In March 2007, Clinton and fellow Democratic Sen. Jim Webb of Virginia sent a letter to the Comptroller of the United States, calling on him to initiate a GAO investigation to reassess the body armor systems used by the military.
The following month, the GAO issued a report, which concluded that "Army and Marine Corps body armor is currently meeting theater ballistic requirements and the required amount needed for personnel in theater, including the amounts needed for the surge of troops in Iraq."
Nevertheless, with emerging technology and debate over the best type of body armor, the GAO is reassessing body armor, said Roger Charles, vice chairman of the nonpartisan Soldiers for the Truth Foundation, which has been at the forefront of the body armor debate.
Clinton's comment about troops heading into war without body armor, while it wasn't true for all, was true for some soldiers at the beginning of the war. So we rate Clinton's comment Mostly True.
Is this enough evidence for US Military to arrest Bush Administration?
TOOTHLESS: PART 1:
HOW THE WATCHDOG PRESS BECAME A GOVERNMENT LAPDOG
by Walter Brasch, American Reporter Correspondent, Bloomsburg, Pa. February 20, 2009, Article Source
BLOOMSBURG, Pa. -- The president of the Associated Press (AP) was spewing venom at the Bush-Cheney Administration for having turned the Dept. of Defense into a propaganda machine.
Americans "expect honest answers about what's happening to their sons and daughters," Tom Curley told journalism students and faculty at the University of Kansas.
Listing innumerable ways the Pentagon had advocated Bush-Cheney political beliefs, Curley questioned if the United States should "be trying to influence public opinion through subterfuge, both here and abroad,"
An AP investigation had just revealed that the Pentagon budget for "influence operations" this fiscal year is at least $4.8 billion, with about 27,000 civilian and military personnel assigned to information dissemination.
The penalty for failing to agree to the Pentagon's terms of reporting, said Curley, was that he was told by top commanders that "if I stood and the AP stood by its journalistic principles, the AP and I would be ruined."
With a new Administration, "now is the time to resist the propaganda the Pentagon produces and live up to our obligation to question authority and thereby help protect our democracy," said Curley.
Brave words, but ones that would have had more impact had they been said publicly four years ago, instead of a month after Bush and Cheney left office, and a more transparent Administration was elected.
Although the Bush-Cheney Administration put propaganda ahead of truth, like Congress, the media were willing accomplices.
Major media were far too deferential to the Bush-Cheney Administration following 9/11, perhaps believing it was unpatriotic, or at least detrimental to their ad revenues, to oppose what the President said he needed to fight the war on terrorism.
When the Bush-Cheney Administration, aided by a compliant Congress, pushed through the severe constitutional violations of the PATRIOT Act, the media barely raised a voice to protest. Reporters who wrote against the PATRIOT Act were often ostracized by the establishment press.
It was the nation's librarians, not the nation's journalists, that led protests of First Amendment free speech and free press violations during most of the eight years of the Bush-Cheney Administration.
When the Bush-Cheney Administration established "free speech zones" a mile or more from presidential and vice-presidential speeches and rallies, whether official or political, the media compliantly ignored the dissidents and, for the most part, the blatant constitutional violation of the First Amendment rights of free and peaceful assembly.
When the Bush-Cheney Administration put out lies that Saddam Hussein was tied into 9/11, that Iraq had weapons of mass destruction, and then launched an invasion of a sovereign nation, the media saluted and reported what they were told.
When the Bush-Cheney Administration rewrote the rules of press coverage in combat to compromise independent reporting, the press didn't challenge their new restrictions. They grumbled over beers, but didn't push back. By their failure, the press allowed themselves to become part of a propaganda machine, spewing good news from their tunnel vision.
When the Bush-Cheney Administration, trying to find "good news" in Iraq, fed information to the Washington Post that Army PFC Jessica Lynch, a 19-year-old supply clerk, was a hero who, when her Humvee was ambushed, fought a heroic battle, killed some attackers, was shot, and then tortured in an Iraqi hospital until Army Rangers and Navy SEALs rescued her, no one at the Post = pleased to have been given a human interest scoop - questioned the Defense Dept.'s statements.
But the story was a phony. Lynch confirmed suspicions raised in the alternative media that she didn't wield a gun, that her injuries were sustained when she was pinned under the Humvee, and that she was treated well by Iraqi physicians, who had even given the American "rescuers" the hospital's master key.
When the Bush-Cheney Administration tried to cover up that former NFL star Pat Tillman, an Army Ranger, was killed by friendly fire, and that the Army delayed and then lied to Tillman's parents, the press went along with what they were told.
When the Bush-Cheney Administration made sure that retired military officers with opinions favorable to the Administration got choice tv network "talking head" assignments, few protested until it became obvious that theor commentaries were skewed toward White House policies.
When the Bush-Cheney Administration lied about massive spying upon Americans, about the environment, public health, and other areas, the media yawned and swallowed what they were told.
When the Bush-Cheney Administration said the U.S. economy was not in a recession but doing just fine, while all around them the sub-prime crisis and Wall Street greed ate up the fabric of American life, the media concentrated on the latest pop-celeb's trysts, movie deals, drinking and drug problems.
Even when the Bush-Cheney Administration blocked reporters' attempts to get public information via the Freedom of Information Act, their bosses often didn't back them up, but instead hoarded the financial and manpower resources necessary to break down the official barriers.
When the Bush-Cheney Administration moved Helen Thomas, dean of the White House press corps, from her first row seat back to the last row at press conferences and rarely called on her for questions, the major media barely protested, lest they be banished to the back of the press bus and denied "face time" on Air Force One.
The New York Times and Washington Post, which eventually redeemed themselves as Bush's popularity sank, each published lengthy apologies for failing to adequately question Administration claims, and doing little but recycle the lies.
Americans have every reason to complain about the Bush-Cheney Administration. But the nation's news media, by abandoning their credibility and principles, had became an extension of the propaganda machine that Tom Curley complained about.
Dr. Brasch, professor of journalism at Bloomsburg University, continuouly challenged claims about Iraq and weapons of mass destruction in journalism and books about the Bush-Cheney Administration, including America's Unpatriotic Act: The Federal Government's Violation of Constitutional and Civil Rights, 'Unacceptable': The Federal Government's Response to Hurricane Katrina, and Sinking the Ship of State: The Presidency of George W. Bush.
TOOTHLESS: PART II:
WHEN THE LAPDOGS GOT TEETH
by Walter Brasch, American Reporter Correspondent, Bloomsburg, Pa. March 2, 2009, Article Source
BLOOMSBURG, Pa. -- In May 2004, the New York Times, while claiming it was aggressive in pursuing stories about the Bush-Cheney Administration, slipped in an apology for acting more as the mouthpiece for politicians than as a watchdog for society.
"Coverage was not as rigorous as it should have been," the Times admitted.
Part of the problem, the Times acknowledged, was that "Editors at several levels who should have been challenging reporters and pressing for more skepticism were perhaps too intent on rushing scoops into the paper." The Times concluded it wished "we had been more aggressive."
Almost three months later, the Washington Post, of the three national papers the most in favor of invading Iraq, finally acknowledged its own pre-war hysteria and lack of journalistic competence and courage.
"We were so focused on trying to figure out what the Administration was doing that we were not giving the same play to people who said it wouldn't be a good idea to go to war and were questioning the Administration's rationale," wrote Executive Editor Leonard Downie Jr.
During President Bush's second term, especially after his popularity had begun to sink, several major newspapers, including the New York Times and Washington Post, became more aggressive, publishing several major investigations into the War in Iraq, the government's use of torture and apparent violation of the Geneva Accords, violations of due process, extensive spying upon Americans, the failure to provide combat troops with adequate body armor, the silencing of government scientists who disagreed with Bush-Cheney beliefs and values, the classification of 55,000 documents in the National Archives that had previously been declassified, the use of propaganda to support doctrine, and problems at Guantánamo Bay.
A New York Times investigation by Tim Golden and Don Van Natta Jr. revealed "government and military officials have repeatedly exaggerated both the danger the detainees posed and the intelligence they have provided." That same investigation also revealed a CIA report in September 2002 that questioned the arrests. Most of those picked up in Afghanistan and transferred to Guantánamo Bay, according to the CIA investigation, were low level recruits or innocent men.
Among other reporters from the Times who broke major stories were Elisabeth Bumiller, Douglas Jehl, James Risen, and Eric Schmitt, who wrote about secret prisons and rendition; and James Risen and Eric Lichtblau, who wrote several articles about the government's illegal spying upon American citizens.
Times editors, however, had kept the stories about the government's spying out of the newspaper for about a year, in deference to the Administration's hysterical claims before the November 2004 election that breaking news about unconstitutional activities might somehow be aiding and abetting the enemy; the reality was that the Times was duped into protecting the Administration against a vote drain.
For the Washington Post, Stave Fainam wrote about abuses by extramilitary private contractors in Iraq; Dana Priest wrote about secret prisons and controversial parts of the Bush-Cheney counter-terrorism tactics; Jo Becker and Barton Gellman investigated the growing influence of Dick Cheney into national policies; and Dana Priest, Anne Hull, and Michael duCille in several articles exposed the medical and psychiatric neglect of returning combat soldiers at the Walter Reed Army Medical Center.
Although the Post's Bob Woodward fully believed Bush-Cheney Administration claims about the need to invade Iraq, he still produced the most in-depth reporting about Bush and his decision-making process. His four books in six years were all best-sellers.
The Los Angeles Times published a series in 2006 about Iraq's descent into civil war following the U.S. invasion. Outstanding reporting about the impact of the war upon soldiers and civilians was done by several reporters, including Borzou Daragahia and David Zucchino of the L.A. Times; and Lisa Chedekel and Matthew Kauffman of the Hartford Courant.
However, for the most part, reporters accepted what they were given. Robert Fisk, Middle East correspondent for the London Independent, condemned much of the American press corps in Iraq for "hotel journalism," writing stories based upon what they were told in press conferences without going into the field.
At the Boston Globe, Charlie Savage did solid reporting about President Bush's use of signing statements to bypass federal and constitutional law.
Much of the best in-depth reporting about the Bush-Cheney Administration, especially its fixation upon invading Iraq, was done by reporters for national magazines.
Seymour Hersh's powerful series about the abuses at Abu Ghraib prison and several articles about the war in Iraq first appeared in the New Yorker. Hersh had broken the story about the massacre at My Lai and its cover-up during the Vietnam War; it was this willful murder of civilians by the U.S. military that other reporters knew about but didn't report that earned Hersh the Pulitzer Prize. However, after Hersh's series was published, the establishment media could no longer ignore the story.
Not much changed in the four decades since then. Perhaps Hersh's greatest honor is that a senior Bush advisor called him "the closest thing American journalism has to a terrorist."
Among several outstanding hard-news reports about the Bush-Cheney Administration, especially its fixation upon invading Iraq and of subsequent constitutional violations, were those of Michael Isikoff in Newsweek, David Corn in Mother Jones, Jane Mayer in The New Yorker, and James Bamford in Rolling Stone.
With a few blips for courageous reporting, the American press, according to media critic Norman Solomon, continued to blindly accept the Bush-Cheney doctrine as truth. "The American media establishment," wrote Solomon in August 2007, "continues to behave like a leviathan with a monkey on its back - hooked on militarism and largely hostile to the creative intervention that democracy requires."
However, reporters for one establishment news agency consistently represented the highest ideals of an uncompromised press.
John Walcott, the Knight Ridder bureau chief in Washington, and bureau reporters Jonathan Landay and Warren Strobel, were aggressive in publishing well-documented stories that challenged Bush-Cheney claims about weapons of mass destruction in Iraq and the need for the invasion.
When The McClatchy Company bought out Knight Ridder in March 2006, Walcott continued as bureau chief, and Landay and Strobel become senior correspondents. They continued to challenge the propaganda, and proved that their organization was doing everything the Founding Fathers demanded when they said the primary function of the media is to act as a watchdog on government.
When other media disregarded the anti-war dissidents, Walcott's reporters interviewed them; when other media gave Guantánamo Bay coverage little more than "he said/she said" coverage, the McClatchy bureau dug into the story to present the truth and not the spoon-fed lies. When other media wrote down what they were told at press conferences and private meetings with senior Bush-Cheney officials, Walcott's reporters listened and took notes, too, but went to innumerable professionals and lower-level staff in the Defense and State departments to get more of the truth.
"Journalism is not stenography," says Walcott, winner of the first I.F. Stone medal for journalistic independence. The role of the journalist, he says, isn't to record what people say, but to question it in the search for the truth. "One of the reasons we pressed so hard for the case for the war in Iraq," says Walcott, "is that what they [the Administration] said simply made no sense."
The primary focus for Walcott's reporters was "how the decisions being made in Washington, [by] many who had never been to war, would affect the men and women" of the military.
"On the whole, the Bush Administration did not put out the welcome sign for us," says Roy Gutman, McClatchy foreign editor. On even routine stories, the White House planted its leaks with friendlier organizations, and tried to isolate the Knight Ridder/McClatchy bureau from the other media. Publicly, the Bush-Cheney Administration issued no retort; by maintaining silence, the Administration knew the establishment media would also ignore a competitor's reports.
"We were alone at the beginning," says Walcott, "and are still fairly lonely at the end."
This is the second in a two-part series on journalism's failures and successes during the Bush-Cheney Administration.
In the pages of The American Reporter, Walter Brasch challenged Administration claims about Iraq and weapons of mass destruction. He wrote about the shredding of civil rights under the PATRIOT Act, including violations of free speech, due process and privacy. Two years before Katrina hit the Gulf Coast, he and Rosemary Brasch explained why the U.S wasn't prepared to deal with a natural disaster. In each case, the establishment media ignored their timely reporting.
War Criminal, Baby Killer
Donald Rumsfeld
(Hoover Institution) calledVietnam Veterans Stupid
quote: [Vietnam Veterans were]
"What was left after the Best and Brightest Found a way to dodge military service"
[Like Chickenhawk Cowards Dick Cheney & George W Bush]
War Criminal, Baby Killer
Condoleezza Riceand put U.S. Military in Danger FOREVER by
Initiating Torture
Since Most Politicians Are ? Treasonous ? and ?
Refuse to Do Their Job ?; Serving U.S. Citizens ?:How to Perform a Citizen's Arrest
of A Bush Administration Officialby Nathan Robinson, July 27, 2008 05:22 PM, Article Source
The news that 4 people had been arrested in Iowa while trying to perform a citizen's arrest on Karl Rove got me wondering: Can we arrest Bush administration officials ourselves? So I slogged through a slew of state statutes, and as it turns out, the answer is yes. But only if you live in certain particular states.
Citizen's arrests have a long, rich tradition dating back hundreds of years. Because the power of ordinary people to help law enforcement execute its duties is important, nearly every state has some sort of statute on the books permitting citizen detentions of suspected criminals.
However, while most states allow citizen's arrests, the majority require the presence of the citizen performing the arrest during the crime. A number of states have more flexible language in their laws, though. The California Penal Code, for example says the following:837. A private person may arrest another:
1. For a public offense committed or attempted in his presence.
2. When the person arrested has committed a felony, although not in his presence.
3. When a felony has been in fact committed, and he has reasonable cause for believing the person arrested to have committed it.
Alabama and Kentucky have similar wordings. Montana phrases things thusly:
A private person may arrest another when there is probable cause to believe that the person is committing or has committed an offense and the existing circumstances require the person's immediate arrest.
The dispute here will likely arise over the definition of the words "require the person's immediate arrest." I'd argue that if anyone needed to be immediately arrested, it's Karl Rove, but a Montana judge might disagree. And one of the main downsides to citizen's arrests is that if you're in the wrong, you have almost no legal protection (and depending on state law, may have committed a crime tantamount to kidnapping).
Don't let that deter you, though! If there are reasonable grounds to suspect a felony has been committed by the person arrested, then a citizen's arrest is perfectly legally justified. Just don't go and arrest the man behind the counter at the sandwich shop who gave you the wrong change.
What the four Iowans did is courageous, and is exactly how we should use the citizen arrest power. A citizen's arrest is a peaceful, lawful, old-fashioned, and charmingly Midwestern way to hold government criminals accountable. I suggest that we start a nationwide movement. We will turn any suspected government criminals over to the police. Just wait until a Bush administration official shows up in your town.
Figure out whether they can reasonably be considered guilty of a felony. Check the US Code to see who's guilty of what, and then perform a citizen's arrest.
Rove, for example, could likely be detained on suspicion of obstruction of justice, having violated Title 1, Section 18, Chapter 73, S. 1505:
Whoever corruptly... obstructs, or impedes or endeavors to influence [or] obstruct...the due and proper exercise of the power of inquiry under which any inquiry or investigation is being had by either House, or any committee of either House or any joint committee of the Congress...[s]hall be fined under this title, imprisoned not more than 5 years or, if the offense involves international or domestic terrorism...imprisoned not more than 8 years, or both.
I would think that one's fairly cut-and-dry. I'm not a lawyer, however, and I don't know whether this would interfere with, or be superseded by, the pending contempt of Congress citation. Still, I think it gives plenty of "reasonable suspicion," and if Rove is in California, that's all you need. You might pick up Miers or Bolton as well with that statute.
It doesn't take much perusing of the U.S. Code to find violations that administration officials are surely guilty of (the Elections and Political Activities section is one particular goldmine), and if you live in a state with lax state laws regarding citizen's arrests, detaining these people is perfectly within your right. It's just important to follow a few key steps.
1. Check your state laws first. This can be done by entering the name of your state and "statutes" into a search engine. An official online copy of existing state law will usually be the first result. The process for citizen's arrests will usually be located in the section under Crimes > Criminal Procedures > Arrests > Arrests by Private Persons, or something similar. Sometimes statutes are incredibly confusing to navigate through, but there will often be a search function somewhere on the page.
2. Check to make sure the particular person in question can be suspected of committing a felony (make sure it's a felony, though this depends on state law also).
3. Detain the person, without using physical force of any sort. Announce that you are performing a citizen's arrest, and cite the crime they are suspected of.
4. Call the police. Make sure you know the relevant citizen's arrest statute number and the U.S. Code number. You don't want to be the one being arrested.
5. This is risky, and all depends on your state. Make sure you're on solid legal ground first. It is best to consult a lawyer. WikiHow has an informative article on citizen's arrests in general.
We really ought to be inspired by the 4 courageous Iowans who dared to try to hold Rove accountable for his crimes. Government officials, no matter how high-ranking, should be prevented from even walking the street without fear of arrest, if they are guilty of a crime. Whether or not justice is done should not depend on how politically influential the accused is. If the Justice Department will not do its job, then let citizens uphold the law. Citizen's arrests are a powerful yet peaceful way to show the strength and defiance of the American people.
Karl Cohen ~ Association International du Film d'Animation-SF Newsletter
ASIFA-SF NEWSLETTER
Association International du Film d'Animation
(International Animated Film Association)
June 2013This issue contains a reality check article: IS THE ANIMATION INDUSTRY IN INDIA IN TROUBLE? that contradicts the image that India & probably other countries are capable of creating features equal to Hollywood's. Also there are serious troubles in many of their animation education institutions that echo the troubles created by some of our for-profit schools.
There are festival reports: a link to one by Bill Dennis and a full report on Stuttgart by Nancy Denney-Phelps.
There is industry news about Disney being insensitive to various groups, lots of cool links to check out, a mention of Tom Sito's new book on the history of computer animation (an excellent book), a FASCINATING ANIMATION ONLINE section and much more.
Our June event is our 2nd annual Spring Animation Festival
Karl Cohen's Investigative Film Journalism Award, April 7, 2013
TIPS FOR PEOPLE WHO ARE SERIOUS ABOUT GETTING STARTED AND WANT TO SUCCEED IN AN ANIMATION CAREER - FROM PICKING A SCHOOL TO GETTING THAT FIRST JOB by Karl Cohen
Google Is Evil ~ Breaking a promise
Martin Rowson, The Guardian, [Search Engine] on Google's explicit content policy ~ Cartoon Source
Google urged to do more to block
internet access to child abuse imagesGovernment's child internet safety adviser wants default safety setting to force users seeking hardcore porn sites to register
Alexandra Topping, guardian.co.uk, Friday 31 May 2013 06.04 EDT, Article Source
John Carr acknowledged that Google, like all search engines, blocked access to websites they knew contained
images of child abuse, but 'that is them being reactive'. Photograph: Damien Meyer/AFP/Getty ImagesGoogle has been urged by a government adviser to do more to restrict access to child abuse images, after paedophile Mark Bridger was jailed for life for the murder of April Jones.
John Carr, a government adviser on child internet safety, said making it more difficult to access hardcore pornography sites, which were often the gateway to illegal child abuse images, would prevent many men accessing such material.
He said he would be urging Google to take measures in a meeting with the company next week.
Carr's remarks come after the sentencing of Bridger, who murdered the five-year-old in a sexually-motivated attack after looking at pictures of child abuse online.
Speaking to BBC Radio 4's Today programme on Friday, Carr acknowledged that Google, like all search engines, blocked access to websites they knew contained images of child abuse. "That is them being reactive, they can and should be proactive," he said.
Currently there are three safety settings on Google, which can be adjusted by the user. Carr argued that Google should turn on its "safe search" function by default, and block access to hardcore pornography sites. "They are one of the key routes that guys get to child pornography in the first place," he said.
If users wanted to change their settings to access hardcore pornography sites, they would have to register with Google and would have to verify that they were 18, Carr said. "That would be a huge deterrent for many of these guys that would stop them from getting on the pathway that lead to the child abuse images.
"Putting any types of barriers to things like that would in my opinion, and the opinion of many others, help reduce the numbers of guys who got involved with this stuff in the first place, and that would be a big step forward."
He called on Google to show moral leadership on the issue. "They are the biggest player in this space in the world. If they did it then others would follow … If Google did it everyone would have to do it."
Google has said it is committed to ending access to illegal internet sites. The company was "unable or unwilling to do an interview" on Today, according to presenter Sarah Montague.
Judge Orders Google To Give Customer Data To FBI
By PAUL ELIAS 06/01/13 04:19 AM ET EDT, Article Source
SAN FRANCISCO -- A federal judge has ruled that Google Inc. must comply with the FBI's warrantless demands for customer data, rejecting the company's argument that the government's practice of issuing so-called national security letters to telecommunication companies, Internet service providers, banks and others was unconstitutional and unnecessary.
FBI counter-terrorism agents began issuing the secret letters, which don't require a judge's approval, after Congress passed the USA Patriot Act in the wake of the Sept. 11, 2001, attacks.
[Ed. Note: It was a Republican and Democrat Congress that passed the war criminal, Republican Bush Administration, USA Patriot Act; against U.S. citizens, without reading it ... proving, once again,NONE OF THE ABOVE should be a choice on voter ballots and Nobody should be President !!!]
The letters are used to collect unlimited kinds of sensitive, private information, such as financial and phone records and have prompted complaints of government privacy violations in the name of national security. Many of Google's services, including its dominant search engine and the popular Gmail application, have become daily habits for millions of people.
In a ruling written May 20 and obtained Friday, U.S. District Court Judge Susan Illston ordered Google to comply with the FBI's demands.
But she put her ruling on hold until the 9th U.S. Circuit Court of Appeals could decide the matter. Until then, the Mountain View, Calif.-based company must comply with the letters unless it shows the FBI didn't follow proper procedures in making its demands for customer data in the 19 letters Google is challenging, she said.
After receiving sworn statements from two top-ranking FBI officials, Illston said she was satisfied that 17 of the 19 letters were issued properly. She wanted more information on two other letters.
It was unclear from the judge's ruling what type of information the government sought to obtain with the letters. It was also unclear who the government was targeting.
The decision from the San Francisco-based Illston comes several months after she ruled in a separate case brought by the Electronic Frontier Foundation over the letters. She ruled in March that the FBI's demand that recipients refrain from telling anyone -- including customers -- that they had received the letters was a violation of free speech rights.
Kurt Opsah, an attorney with the foundation, said it could be many more months before the appeals court rules on the constitutionality of the letters in the Google case.
"We are disappointed that the same judge who declared these letters unconstitutional is now requiring compliance with them," Opsah said on Friday.
Illston's May 20 order omits any mention of Google or that the proceedings have been closed to the public. But the judge said "the petitioner" was involved in a similar case filed on April 22 in New York federal court.
Public records show that on that same day, the federal government filed a "petition to enforce National Security Letter" against Google after the company declined to cooperate with government demands.
Google can still appeal Illston's decision. The company declined comment Friday.
In 2007, the Justice Department's inspector general found widespread violations in the FBI's use of the letters, including demands without proper authorization and information obtained in non-emergency circumstances. The FBI has tightened oversight of the system.
The FBI made 16,511 national security letter requests for information regarding 7,201 people in 2011, the latest data available. [Pictures and photographs located on Source page.]
Asia curbs US imports of wheat after
genetically modified sample foundBillions in food exports at stake following disclosure by US Department of Agriculture of the existence of the GM wheat
Suzanne Goldenberg, US environment correspondent, guardian.co.uk, Article Source
An examiner demonstrates the process of analysing a genetically modified wheat sample. Photograph: Lee Jae-Won/ReutersThe discovery of rogue genetically modified wheat in a farmer's field in Oregon shook global confidence in the safety of America's food supply on Friday.
Billions in food exports were potentially at stake following the disclosure by the US Department of Agriculture of the existence of the GM wheat plants.
The GM variant, developed by the agricultural giant Monsanto, has never been approved for human consumption.
The discovery in Oregon, about a decade after field trials ended in that state, raised concerns among the main buyers of America's wheat abroad, as well as an increasingly active GM movement at home.
The European Union advised member states on Friday to test some wheat shipments from the US. The EU imports more than 1.1m tonnes of wheat a year.
Asia was also shutting its doors to American wheat imports. South Korea, which last year imported half of its wheat from the US, cancelled imports, following Japan's lead. Thailand puts its ports on alert. China and the Philippines said they were closely watching the USDA's investigations into the GM escape.
"It's going to be a pretty serious blow to all wheat farmers. I would imagine probably the price of wheat is already going down some," said Fred Kirschenmann, a senior fellow at the Leopold Centre for Sustainable Agriculture at Iowa State University, who himself farms 2,600 acres of organic wheat.
"It is definitely going to have an impact because it is right at the time when there is increasing concern about GM and food so this is not going to be good news for the wheat farmers."
Food safety and environmental groups have grown increasingly active campaigning for greater disclosure of GM ingredients over the last several months.
Vermont, Connecticut and New York are all pursuing laws to require GM labelling – a move furiously resisted by Monsanto and the other big biotech firms.
Kirschenmann said the outbreak could play into public concerns about being given a greater say over whether they choose to eat GM foods, or avoid them.
Others argued the escape in Oregon offered a reminder – yet again – of the enormous difficulties of truly isolating GM products from the food chain.
"This is potentially the tip of the iceberg," said Doug Gurian-Sherman, a senior scientist at the food and environment programme for the Union of Concerned Scientists.
"Where people have looked, they have found contamination occurring. But a lot of the time no one is looking," he said.
The Government Accountability Office in a 2008 report described six outbreaks of GM crops into the US food and feed supply.
Gurian-Sherman noted a few more since then. In almost all of those instances, there were only trace amounts of contamination.
But he said the recurrence of such incidents suggested that the standards, which were below those in Europe, were too lax. "The contamination is very low, considerable less than 1%," he said. "But even with that caveat, I don't think people should have a lot of confidence that there hasn't been contamination events."
Agricultural companies, such as Monsanto, carry out about 1,000 trials of GM crops every year, often at multiple sites across the country. In any year, companies can be testing GM cotton and feed crop, as well as food, including fruits and vegetables such as tomatoes.
Monsanto in 2011 applied for new permits to test another variant of GM wheat in Hawaii and North Dakota.
"When you add all that together I wouldn't be surprised it there hadn't been some other experimental gene that leaked out of some other crops and had been carried along with nobody testing for them," said Gurian-Sherman.
The government is investigating how the GM wheat plants arrived in that Oregon field.
Monsanto in a statement on its website said it would with the authorities, and that there was no health risk from the outbreak.
"Monsanto will work with the US Department of Agriculture to get to the bottom of the reported genetically modified wheat detection, there are no food, feed or environmental safety concerns associated with the presence of the Roundup Ready gene if it is found to be present in wheat," the company said.
GM variants are now the norm in US corn, cotton and soybeans, making up virtually all of the soybean crop last year. By some estimates, about two-thirds of US processed foods contain some GM ingredients.
But GM wheat never gained a foothold because of widespread public resistance, and Monsanto did not pursue efforts for its commercial development.
However, the company conducted widespread testing of GM wheat in 16 states between 1998 and 2005. The last such test fields in Oregon were planted a decade ago in 2001, the USDA said.
Those decisions could now return to haunt the US, said Danielle Nierenberg, founder of The Food Tank. "We have spent a lot of time in the last few years putting China and other countries down for food safety issues, but we are messing with people's faith in the food system here," she said. "The US has a long history of claiming we have the safest and most abundant food system in the world and this undermines that."
Genetically modified wheat found
in Oregon field raises trade concernsDiscovery could have far-reaching implications for US wheat industry if growth of Monsanto crop turns out to be far-flung
Associated Press in Washington, guardian.co.uk, Wednesday 29 May 2013 17.35 EDT, Article Source
No genetically engineered wheat has been approved for US farming. Photograph: Laszlo Balogh/ReutersUnapproved genetically engineered wheat has been discovered in an Oregon field, a potential threat to trade with countries that have concerns about genetically modified foods.
The US Agriculture Department said Wednesday that the genetically engineered wheat is safe to eat and there is no evidence that modified wheat entered the marketplace. But the department is investigating how it ended up in the field, whether there was any criminal wrongdoing and whether its growth is widespread.
"We are taking this very seriously," said Michael Firko of the Agriculture Department's animal and plant health inspection service.
A farmer discovered the genetically modified plants on his farm and contacted Oregon State University, which notified USDA early this month, Firko said.
No genetically engineered wheat has been approved for US farming. USDA officials said the wheat is the same strain as a genetically modified wheat that was legally tested by seed giant Monsanto a decade ago but never approved. Monsanto stopped testing that product in Oregon and several other states in 2005.
The discovery could have far-reaching implications for the US wheat industry if the growth of the engineered product turns out to be far-flung. Many countries around the world will not accept imports of genetically modified foods, and the United States exports about half of its wheat crop.
Oregon department of agriculture director Katy Coba said in a statement that the discovery is "a very serious development that could have major trade ramifications". The state exports about 90% of its wheat.
"I am concerned that a highly regulated plant material such as genetically modified wheat somehow was able to escape into a crop field," she said.
USDA officials declined to speculate whether the modified seeds blew into the field from a testing site or if they were somehow planted or taken there, and they would not identify the farmer or the farm's location. The Oregon department of agriculture said the field is in the eastern part of the state.
The discovery also could have implications for organic companies, which by law cannot use genetically engineered ingredients in its foods. Organic farmers have frequently expressed concern that genetically modified seed will blow into organic farms and contaminate their products.
US consumers have shown increasing interest in avoiding genetically modified foods. There has been little evidence to show that modified foods are less safe than their conventional counterparts, but several state legislatures are considering bills that would require them to be labeled so consumers know what they are eating.
While most of the corn and soybeans grown in the United States are already modified, the country's wheat crop is not.
USDA said the unidentified farmer discovered the modified wheat when farm workers were trying to kill some wheat plants that popped up between harvests. The farmer used the herbicide glyphosate to kill the plants, but they did not die, prompting the tests at Oregon State to find out if the crops were genetically engineered to resist herbicides.
The tests confirmed that the plants were a strain developed by Monsanto to resist its herbicides and tested between 1998 and 2005. At the time Monsanto had applied to USDA for permission to develop the engineered wheat, but the company later pulled its application.
The Agriculture Department said that during that seven-year period, it authorised more than 100 field tests with the same glyphosate-resistant wheat variety. Tests were conducted in in Arizona, California, Colorado, Florida, Hawaii, Idaho, Illinois, Kansas, Minnesota, Montana, Nebraska, North Dakota, Oregon, South Dakota, Washington and Wyoming.
During that testing and application process, the Food and Drug Administration reviewed the variety found in Oregon and said it was as safe as conventional varieties of wheat.
Officials said they have received no other reports of discoveries of genetically modified wheat. Firko and acting deputy secretary of agriculture Michael T Scuse said they have already been in touch with international trading partners to try and assuage any concerns.
"Hopefully our trading partners will be understanding that this is not a food or feed safety issue," Scuse said.
Obama's new FBI chief approved Bush's
NSA warrantless wiretapping schemeJames Comey becomes just the latest symbol of the Obama legacy: normalizing what was very recently viewed as radical
Glenn Greenwald, guardian.co.uk, Thursday 30 May 2013 08.57 EDT, Article Source
James Comey, Deputy Attorney General under President Bush, is reported to be President Obama's
pick to lead the FBI. File photo from Jan. 14, 2004. Photograph: Evan Vucci, File/Associated Press(updated below - Update II - Update III)
One of the biggest scandals of the Bush administration (which is really saying something) began on December 16, 2005. That was when the New York Times' James Risen and Eric Lichtblau were finally allowed to reveal what they had learned more than a year earlier: namely, that President Bush, in 2002, had ordered the National Security Agency to eavesdrop on the electronic communications of US citizens without first obtaining warrants from the FISA court as required by 30-year-old criminal law. For the next three years, they reported, the NSA "monitored the international telephone calls and international e-mail messages of hundreds, perhaps thousands, of people inside the United States without warrants." The two NYT reporters won the Pulitzer Prize for that story.
To say that progressives and liberals bellowed sustained outrage over that revelation is to understate the case. That NSA program was revealed less than two months after I first began writing about political issues, and I spent the next full year overwhelmingly focused on that story, and also wrote my first book on it. In progressive circles, the NSA warrantless eavesdropping program was the pure symbol of Bush/Cheney radicalism and lawlessness: they secretly decided that they were empowered to break the law, to commit what US statutes classified as felonies, based on extremist theories of executive power that held that the President, as Commander-in-Chief, was entitled under Article II of the Constitution to eavesdrop however he wanted in the name of national security, even if it meant doing exactly that which the law forbade.
The FISA law provided that anyone who eavesdrops without the required warrants - exactly what Bush officials did - is committing a felony "punishable by a fine of not more than $10,000 or imprisonment for not more than five years, or both" - for each offense. Moreover, all three federal judges who actually ruled on the merits of the Bush NSA warrantless eavesdropping program concluded that it violated the law.
So why, then, was there no accountability for this systematic illegal spying? That happened for two reasons. First, both the Bush DOJ and then the Obama DOJ successfully convinced obsequious federal courts that the eavesdropping program was so secretive that national security would be harmed if courts were to adjudicate its legality - in other words, top government officials should be placed above and beyond the rule of law because doing so is necessary to Keep Us Safe™. Second, the Bush DOJ's most senior lawyers - Attorney General John Ashcroft, Deputy Attorney General James Comey and OLC chief Jack Goldsmith - approved a legal memorandum in 2004 endorsing radical executive power theories and warped statutory interpretations, concluding that the Bush NSA warrantless eavesdropping program was legal, thus making it more difficult to prosecute the Bush officials who ordered it (even if the Obama DOJ were inclined to prosecute, which they were not).
It was announced yesterday that this very same James Comey - who as Bush's Deputy Attorney General authorized the once-very-controversial, patently illegal Bush NSA eavesdropping program - is President Obama's choice to be the new Director of the FBI.
How are Obama's most devoted media loyalists reacting to the news that he is about to put in charge of the FBI the Bush lawyer who authorized the illegal NSA warrantless eavesdropping program based on warped right-wing legal theories? Exactly as you would expect. Here's one of them - who wrote post after post after post in 2006 and 2007 vehemently denouncing the NSA program which Comey authorized and the theories on which it was based - hailing Comey as "not only non partisan in [his] job but consistently put constitutional equities at center [of his] thinking".
It is true that Comey was at the center of a dramatic Bush-era political controversy that earned him praise from many Bush critics, including me. Comey was one of the Bush DOJ lawyers who, along with Ashcroft, Goldsmith, and FBI Director Robert Mueller, had threatened to resign if Bush did not modify the NSA program in order to make it legal in Comey's eyes, and he then went to the hospital where Ashcroft was quite ill to prevent then-White House counsel Alberto Gonzales and then-White House chief of staff Andy Card from bullying the infirm and barely cogent Attorney General into signing off on the legality of the NSA program.
In other words, there was something the NSA was doing for years - that we still don't know - even more extreme than the illegal NSA program revealed by the NYT in 2005. It was Comey, along with Ashcroft, Mueller, and Goldsmith, who threatened to resign if it did not stop, and they deserve credit for that. But the reason they didn't end up resigning was because Bush officials "modified" that NSA program into something those lawyers could and did endorse: the still-illegal, still-radical NSA eavesdropping program that spied on the communications of Americans without warrants and in violation of the law. And this was accomplished by inventing a new legal theory to accompany the old one: that Congress, when it enacted the 2001 AUMF, silently and "implicitly" authorized Bush to eavesdrop in exactly the ways the law expressly forbade.
Thus, it was Comey who gave his legal approval to enable that NSA eavesdropping program to spy on Americans without warrants: the same program that produced so much outrage and scandal when revealed by the NYT. How can any progressive who spent the Bush years vehemently denouncing that domestic spying program as the symbol of Bush radicalism and lawlessness now cheer when the lawyer who approved it is about to be put in charge of the FBI?
Then there's Comey's mixed and quite murky role in authorizing Bush's torture program. Internal DOJ emails released to the New York Times in 2009 show Comey expressing serious reservations, and even objections, to the willingness of Albert Gonzales to legally authorize any interrogation techniques the White House wanted, and he warned those officials that their involvement would be condemned by history. But even as he did so, Comey, as the New York Times explained, eventually, albeit reluctantly, gave his legal approval to those techniques:
"Previously undisclosed Justice Department e-mail messages, interviews and newly declassified documents show that some of the lawyers, including James B. Comey, the deputy attorney general who argued repeatedly that the United States would regret using harsh methods, went along with a 2005 legal opinion asserting that the techniques used by the Central Intelligence Agency were lawful.
"That opinion, giving the green light for the CIA to use all 13 methods in interrogating terrorism suspects, including waterboarding and up to 180 hours of sleep deprivation, 'was ready to go out and I concurred,' Mr. Comey wrote to a colleague in an April 27, 2005, e-mail message obtained by The New York Times."
As I wrote at the time, the NYT article significantly overstated Comey's role in approving these torture programs. But it is true that he ultimately acquiesced to their legalization.
There's no question that James Comey was far from among the worst people at the Bush DOJ. He's not John Yoo or David Addington, some of whose theories he rejected. He engaged in some rare, commendable conduct, including objecting to the more extreme version of the NSA program to the point of threatening resignation, and voicing serious reservations about the wisdom of some of the more extreme torture techniques. I understand the respect people have for some of what he did, and even share it.
But whatever else was true, he was the lawyer who legally approved that warrantless NSA program that the New York Times revealed that caused so much scandal. And he was part of the process that legalized the torture techniques used by the Bush administration. How can that possibly not disqualify him from running the FBI in the eyes of progressives who claimed to find all of that so atrocious and such an assault on all that is dear and good in the world?
But this is exactly where the Obama administration has taken us. Comey will run the FBI alongside Obama's chief of the CIA, John Brennan, who spent the Bush years advocating multiple torture techniques and rendition. The Agent of Change reaches deep into the bowels of the Bush National Security State and empowers them to run two of the most powerful agencies. Then again, the Bush NSA program is hardly controversial in the Age of Obama: it was Obama who first voted to immunize the telecoms from all legal liability for their illegal participation in that program, then the Obama DOJ succeeded in having all lawsuits over that program dismissed on secrecy and immunity grounds, and then Obama himself succeeded in first enacting and then renewing the law that legalized most aspects of that Bush NSA eavesdropping program.
What was once deemed radical is now normal. Bush officials who formally authorized programs once depicted by progressives as radical and criminal are now heralded by those same progressives as Champions of the Constitution. The politician elected on a pledge of Change and Restoration of Our Values now routinely empowers exactly those Washington officials who championed the policies against which he railed. It's one thing to watch Obama shield and protect all Bush officials who enabled this illegal warrantless domestic surveillance scheme. It's quite another to watch him put in charge of the FBI the very official whose signature deemed it to be legal.
James Comey is far from the worst choice to lead the FBI. I doubt it will change much of anything one way or the other, and there are undoubtedly worse people within the senior ranks of the Democratic Party who would be the likely alternatives. But it's still a potent symbol of how little has changed in the right direction and how much it has changed in the wrong direction. If you had told progressives in 2008 that the Bush lawyer who approved the NSA program would be named by Obama as the FBI Director, they would scoff in disbelief. Now they'll cheer. That is what has changed.
Holder's off-the-record meeting with media outlets
Following up on yesterday's column about Eric Holder's attempts to meet with media outlets over the leak investigations controversy and his demand that the meeting be off-the-record: several organizations have commendably refused to attend under those conditions, including the New York Times, Associated Press, the Huffington Post and (even) CNN. Unsurprisingly, both Politico and the Washington Post will eagerly submit to that condition and attend the meeting, even though they'll be barred from telling their readers what was discussed. Here is the unbelievable response of the official spokesman of the Democratic National Committee, Brad Woodhouse, upon learning that several leading media outlets will not attend under that condition:
Unless media outlets submit to the Attorney General's demand that they meet with him off-the-record, then they "forfeit their right to gripe" over the DOJ's seizure of their emails and telephone records and labeling them as criminals. Thus decree-eth the DNC.
UPDATE
Another of the most controversial acts of the Bush administration was the due-process-free imprisonment of US citizen Jose Padilla, who was arrested in 2002 on US soil, then put in a military brig, without charges, for 3 1/2 years. During that time, he was denied a lawyer, held incommunicado, and tortured. That was the incident that, more than any other, really motivated me to begin writing about politics: back then, it actually shocked me that the US government would claim the power to imprison US citizens on US soil without charges of any kind. As Charles Davis recalls, it was James Comey who took a leading role in the Bush administration in defending that lawless imprisonment, arguing in 2004:
"Had we tried to make a case against Jose Padilla through our criminal justice system, something that I, as the United States attorney in New York, could not do at that time without jeopardizing intelligence sources, he would very likely have followed his lawyer's advice and said nothing, which would have been his constitutional right.
"He would likely have ended up a free man, with our only hope being to try to follow him 24 hours a day, seven days a week, and hope -- pray, really -- that we didn't lose him. . . .
"Two years ago, the president of the United States faced a very difficult choice. After a careful process, he decided to declare Jose Padilla for what he was: an enemy combatant, a member of a terrorist army bent on waging war against innocent civilians. And the president's decision was to hold him to protect the American people and to find out what he knows.
"We now know much of what Jose Padilla knows, and what we have learned confirms that the president of the United States made the right call, and that that call saved lives."
Indeed, when the Bush administration declared Padilla to be an "enemy combatant" and thus removed him from the civilian court system and imprisoned him without charges, Comey was the US Attorney in New York, where Padilla's case was contested. He then became a leading advocate for Bush's denial of the most basic due process to this US citizen. That is who Obama-loyal progressives today are hailing. And that is who is about to lead the FBI, thanks to President Obama.
UPDATE II
On Monday, when I wrote about Obama's terrorism speech, I noted the gushing editorial from the New York Times that was published very shortly after the speech was over, and suggested that its length and detailed discussion of the speech meant that the editors had been given an advanced preview by the White House. The paper's editorial page editor, Andy Rosenthal, did acknowledge yesterday that at least part of the praise for Obama's speech was unwarranted. Furthermore, Charlie Savage did preview the speech in the NYT the day before it was delivered. But the NYT editorial page editors insist to me that they did not themselves receive any advanced review, but rather wrote the editorial based on the speech as it was delivered. I take them at their word that this is true.
UPDATE III
The ACLU today issued a statement on Comey's nomination which, among other things, pointed out that "as the second-highest ranked Justice Department official under John Ashcroft, Comey approved some of the worst abuses committed by the Bush administration." In other words, he's the ideal choice for President Obama to run the FBI. Anyway, as the president taught us long ago, it's really unproductive - and more than a little crass - to Look Backward when it comes to our most powerful political officials. It's just not a nice thing to do. What's a little illegal warrantless eavesdropping, torture, and lawless imprisonment of US citizens among friends? We all make mistakes. Just keep Looking Forward.
Who is John O'Neill & Why Did He Die?
What If the Next President Is Even Worse?
By Ron Fournier, National Journal, Article Source
George W. Bush in 2001 declared war on a tactic (terrorism), and empowered Big Brother to tap phones, launch drones and indefinitely imprison people without due process.
Barack Obama in 2008 declared those Bush policies an overreach, and pledged to curb drone strikes, protect media freedoms, and close the prison at Guantanamo Bay. Instead, he escalated drone strikes and spied on the media. Gitmo is still open for its grim business.
These are facts. And yet, they are distorted by extreme and narrow-minded partisans, supporters of both Bush and Obama.
Conservatives contend that Bush single-handedly prevented a major terrorist strike after Sept. 11, 2001. They demagogue efforts to shift the pendulum back toward civil liberties. Last week, when Obama finally proposed a modest reassessment of the Bush doctrine, Sen. Saxby Chambliss claimed that the efforts "will be viewed by terrorists as a victory."
Liberals hypocritically gave Obama a pass for furthering the same policies they condemned in 2008. Criticism from the left was half-hearted and muted, compared to their Bush-era indignation. On Gitmo, left-wingers rightly blamed the GOP for blocking closure, but didn't shame Obama into using his executive authority to shutter the pit.
Some progressives even tried to justify the Obama administration's efforts to criminalize the work of a FOX News reporter. Would they be so blase about a White House targeting MSNBC?
As Leonard Downie Jr. wrote in Sunday's Washington Post, "Hardly anything seems immune from constitutionally dangerous politicking in a polarized Washington."
But that's no excuse for missing the big picture, which is this: Bush and Obama shouldn't worry you nearly as much as the next president. Or the one after that.But that's no excuse for missing the big picture, which is this: Bush and Obama shouldn't worry you nearly as much as the next president.
Or the one after that.
Think about it, liberals. What if there is a president in your lifetime who is more conservative than Bush? What if that commander in chief is empowered, as were Bush and Obama, by a national tragedy and a compliant Congress?
Your guy Obama has armed a president-turned-zealot with dangerous powers and precedents.
Think about it, conservatives. It may be maddening to listen to Obama tie himself into knots over the balance between liberty and freedom, but what if the next Democratic president sees no limit on a commander in chief's powers? What if he or she doesn't give a whit about offending the mainstream media?
The IRS targeting conservatives is a scandal, but there is no evidence that it was directed by the White House. What if the next Democratic president publicly declared his or her political opponents a direct threat to national security, and openly deployed federal agents against them?
Before your eyes roll out of your heads, it is not unthinkable that a future U.S. president could make Bush and Obama look downright libertarian. We live in an age of rapid connectivity and hyper-celebrity, forces that create, destroy and often resurrect public figures within the lifespan of a cicada. Does the name Justin Bieber ring a bell?
How about Sarah Palin? Our culture of celebrity coupled with the public's disaffection with Washington could lead to the election of a true demagogue or reactionary. Put it this way: What if Huey Long had access to the Internet? Or even Pat Buchanan? Don't be blinded by partisanship.
Does Joint Responsibility Rule of Conspiracy Apply to Palin's
attack on Former U.S. Representative Gabrielle Giffords?Breaking News Related to Joint Responsibility Rule of Conspiracy:
Leslie Van Houten faces 20th parole hearingLeft-wingers should be fighting the abuse of executive powers at home and abroad, rather than defending them.
Right-wingers should be demanding that Obama finally carry out the promises of his speech last week, rather than demonizing them.
What about the rest of us? How do we keep the country both safe and free? We don't cede the public square to these extremists.
NONE OF THE ABOVE
Should Be A Choice On Voter Ballots
Freedom of expression and freedom of speech aren't really important unless they're heard...It's hard for me to stay silent when I keep hearing that peace is only attainable through war. And there's nothing more scary than watching ignorance in action. So I dedicated this Emmy to all the people who feel compelled to speak out and not afraid to speak to power and won't shut up and refuse to be silenced. ~ Tommy Smothers
Closing Argument
Boston Legal Speech on America and more
Please Click to View Video ~ http://vimeo.com/47165357
One Can Lead A Horse To Water, But...
Until there is a solution for this, where one solution has been provided, Nobody will bring Peace to Our Times, feed the hungry, care for the sick, and bake apple pie better than Mom. (otoh) If None of the Above was a choice on voter ballots, it would be a huge step towards recovering U.S. political control, and Nobody gets it.
George Carlin, The American Dream ~ http://vimeo.com/37487342
Apathy Sucks
None of the Above
should be a choice on Voter Ballots
Oh, I hope that I see you again I never even caught your name As you looked through my window pane ~~ So I'm writing this message today I'm thinking that you'll have a way Of hearing the notes in my tune ~~ Where are you going? Where have you been? I can imagine other worlds you have seen ~~ Beautiful faces and music so serene ~~ So I do hope I see you again My universal citizen You went as quickly as you came ~~ You know the power Your love is right You have good reason To stay out of sight ~~ But break our illusions and help us Be the light ~ Message by Michael Pinder
Without love in the dream, it will never come true. ~ Jerry Garcia/Robert Hunter
The man whispered, "God, speak to me" and a meadowlark sang. But the man did not hear.
So the man yelled "God, speak to me" and the thunder rolled across the sky. But the man did not listen.
The man looked around and said, "God let me see you" and a star shined brightly. But the man did not notice.
And the man shouted, "God show me a miracle" and a life was born. But the man did not know.
So the man cried out in despair, "Touch me God, and let me know you are there"
Whereupon God reached down and touched the man. But the man brushed the butterfly away and walked on.
Don't miss out on a blessing because it isn't packaged the way you expect.



























![Mark Zuckerberg, chief executive [Schmuck] officer and founder of Facebook: created a new way of belonging. Mark Zuckerberg, chief executive [Schmuck] officer and founder of Facebook: created a new way of belonging.](http://static.guim.co.uk/sys-images/Guardian/Pix/pictures/2013/6/12/1371052933657/Mark-Zuckerberg-chief-exe-010.jpg)

![A new NSA data farm is set to open in the fall in Bluffdale, Utah. A former CIA agent said: '[Data-mining] played no role in the Headley case.' Photograph: George Frey/Getty Images A new NSA data farm is set to open in the fall in Bluffdale, Utah. A former CIA agent said: '[Data-mining] played no role in the Headley case.' Photograph: George Frey/Getty Images](http://static.guim.co.uk/sys-images/Guardian/Pix/audio/video/2013/6/11/1370977138339/New-NSA-data-center-in-Bl-008.jpg)