Tell-A-Vision = Why Not Try Love Again?
Freedom of expression and freedom of speech aren't really important unless they're heard...It's hard for me to stay silent when I keep hearing that peace is only attainable through war. And there's nothing more scary than watching ignorance in action. So I dedicated this Emmy to all the people who feel compelled to speak out and not afraid to speak to power and won't shut up and refuse to be silenced. ~ Tommy Smothers
Cree Prophecy
Only after the last tree has been cut down,
Only after the last river has been poisoned,
Only after the last fish has been caught,
Only then will you find money cannot be eaten.
Climate study predicts a watery future
for New York, Boston and MiamiStudy shows that 1,700 places in the United States are at greater risk of rising sea levels than previously thought
Suzanne Goldenberg, US environment correspondent, theguardian.com, 29 July 2013 20.17 EDT, Article Source
For nearly 80 US cities, the watery future would come much sooner, within the next decade. Photograph: Joe Raedle/Getty ImagesMore than 1,700 American cities and towns – including Boston, New York, and Miami – are at greater risk from rising sea levels than previously feared, a new study has found.
By 2100, the future of at least part of these 1,700 locations will be "locked in" by greenhouse gas emissions built up in the atmosphere, the analysis published in the Proceedings of the National Academy of Sciences on Monday found.
The survey does not specify a date by which these cities, or parts of them, would actually fall under water. Instead, it specifies a "locked-in" date, by which time a future under water would be certain – a point of no return.
Because of the inertia built into the climate system, even if all carbon emissions stopped immediately, it would take some time for the related global temperature rises to ease off. That means the fate of some cities is already sealed, the study says.
"Even if we could just stop global emissions tomorrow on a dime, Fort Lauderdale, Miami Gardens, Hoboken, New Jersey will be under sea level," said Benjamin Strauss, a researcher at Climate Central, and author of the paper. Dramatic cuts in emissions – much greater than Barack Obama and other world leaders have so far agreed – could save nearly 1,000 of those towns, by averting the sea-level rise, the study found.
"Hundreds of American cities are already locked into watery futures and we are growing that group very rapidly," Strauss said. "We are locking in hundreds more as we continue to emit carbon into the atmosphere."
A recent study, also published in PNAS by the climate scientist Anders Levermann found each 1C rise in atmospheric warming would lead eventually to 2.3m of sea-level rise. The latest study takes those figures, and factors in the current rate of carbon emissions, as well as the best estimate of global temperature sensitivity to pollution.
For the study, a location was deemed "under threat" if 25% of its current population lives below the locked-in future high-tide level. Some 1,700 places are at risk in this definition. Even if bar is set higher, at 50% of the current population, 1,400 places would be under threat by 2100.
The list of threatened communities spans Sacramento, California – which lies far from the sea but would be vulnerable to flooding in the San Joaquin delta – and Norfolk, Virginia. The latter town is home of America's largest navy base, whose miles of waterfront installations would be at risk of being locked in to future sea level rises by the 2040s. The Pentagon has already begun actively planning for a future under climate change, including relocating bases.
About half the population of Cambridge, Massachusetts, across the Charles River from Boston and home to Harvard and MIT, could be locked in to a future below sea level by the early 2060s, the study found. Several coastal cities in Texas were also vulnerable.
But the region at highest risk was Florida, which has dozens of towns which will be locked by century's end. The date of no-return for much of Miami would be 2041, the study found. Half of Palm Beach with its millionaires' estates along the sea front would be beyond saving by the 2060s. The point of no return for other cities such as Fort Lauderdale would come before that.
"Pretty much everywhere it seems you are going to be under water unless you build a massive system of dykes and levees," Strauss said.
Cities Below Future Seas• This article was amended on 29 July 2013 to correct a mischaracterisation of the study. The original article stated that 1,700 American cities would be under sea level by 2100. In fact, the analysis states that these locations, or at least part of them would be "locked in" to a future below high-tide levels, which would come at an unspecified later date.
Apple investigates new claims of
China factory staff mistreatmentConditions for 70,000 workers at Pegatron plants allegedly worse than those reported in the Foxconn scandal
Rupert Neate, The Guardian, Monday 29 July 2013 14.30 EDT, Article Source
Apple is investigating new claims of worker mistreatment in China. Photograph: Saeed Khan/AFP/Getty ImagesApple has been accused of benefiting from the exploitation of more than 70,000 Chinese factory workers in conditions described as even worse than those at Foxconn, the supplier hit by employee suicides and accusations of excessive working hours.
The iPhone and iPad maker is accused of breaching its promise to improve working conditions after the Foxconn revelations by using another supplier alleged to have broken 86 labour laws, including forcing pregnant women to work 11 hours a day, six days a week, standing up.
The US-based human rights watchdog China Labour Watch (CLW) also accused the company in question, Pegatron, of employing underage staff and discriminating against applicants shorter than 4ft 11in, older than 35 or from certain ethic minorities. The fresh claims of worker mistreatment are particularly embarrassing for Apple after it switched some iPhone and iPad manufacturing from Foxconn to Pegatron after intense negative publicity surrounding Foxconn.
Li Qiang, executive director of CLW, said: "Our investigations have shown labour conditions at Pegatron factories are even worse than at Foxconn factories. Apple has not lived up to its own standards. Apple is worsening conditions for workers, not improving them."
Apple on Monday promised to investigate the claims and ensure "corrective actions" are taken. The company said it would force Pegatron to compensate for lost wages. "We are dedicated to protecting every worker in our supply chain," a spokesman said. The Californian company said it had carried out 15 comprehensive audits at Pegatron factories since 2007, but admitted that many of the CLW claims were "new to us". Apple confirmed CLW's claim that some employment agencies were withholding worker ID cards and demanded Pegatron "put a stop" to it.
Jason Cheng, chief executive of Pegatron, said he would immediately investigate the allegations, many of which the company denied. "We strive to make each day at Pegatron better than the last for our employees. They are the heart of our business," he said. "That's why we take these allegations very seriously."
CLW sent undercover investigators posing as employees into three Pegatron factories and conducted more than 200 interviews with staff. Its 60-page report claimed the majority of Pegatron's factory staff worked 66- to 69-hour weeks, above the Chinese legal limit of 49 hours and Apple's limit of 60 hours a week. Apple said its latest Pegatron survey found employees making its products worked 46-hours a week on average.
"In these factories, pregnant women were made to work the same long hours as other workers, putting in 11-hour days for six days per week," the CLW report said. Chinese law restricts employers from asking pregnant women to work more than eight hours a day.
CLW also claimed Pegatron employs workers under 18 – breaching both Chinese law and Apple's strict employment code. "Underage workers often enter the factories as student 'interns' required to work at factories by vocational schools," the report said. Pegatron denied that it employed underage staff.
Pegatron, which recently won the contract to make Apple's forthcoming cheaper iPhone, allegedly displays posters listing "hiring standards" that discriminates against minority groups. The list bans applicants who are less than 4ft 11in, over 35, pregnant, or from the Hui, Tibetan or Uighur ethnic groups. CLW also claimed that male applicants were forced to take off their shirts to prove they did not have tattoos.
It said the average hourly wage of Pegatron workers making Apple products is no more than $1.50 (£0.98) an hour, which it claims is not enough to live on and effectively forces staff to work overtime to earn a living wage.
The undercover investigators also claim Pegatron managers threaten and abuse staff. Managers are alleged to have said: "If you don't obey, I will expose you to the blazing sun until 12 o'clock."
The allegations come a year after Apple chief executive Tim Cook visited Foxconn's Chinese factories and promised regular inspections of working conditions at its biggest suppliers.
"We believe that workers everywhere have the right to a safe and fair work environment, which is why we've asked the Fair Labour Assocation [FLA] to independently assess the performance of our largest suppliers," he said. "The inspections now under way are unprecedented in the electronics industry, both in scale and scope, and we appreciate the FLA agreeing to take the unusual step of identifying the factories in their reports."
Conservatives bashed me for speaking
out about the Zimmerman verdictAmerica may be a nation of 'free speech', but be prepared to be bullied and harassed for speaking up, especially on race
Anthea Butler, theguardian.com, Monday 29 July 2013 08.30 EDT, Article Source
Supporters of both sides in the case have issued calls for restraint. Photograph: Scott Olson/Getty ImagesHours after the George Zimmerman verdict, I found myself at my computer, calling to mind a text I had first read in seminary. The text, Is God a White Racist, By Rev. Dr. William Jones, is still studied by theologians and academics and taught in institutes of higher learning. The book called into question the chief construction of black liberation theology: that God is on the side of the oppressed.
Jones' thesis was simple: God wasn't on the side of the oppressed, and that the tortured history of African Americans' experience in America with slavery, violence and the civil rights proved it. The theme resonated with me as I sat down to write a piece reacting to the Zimmerman verdict for the online magazine Religion Dispatches. Little did I know that the book's title alone would cause an avalanche of vitriol against me, my race, my institution – even my hair.
The screeds came via Twitter, email to myself and my university, conservative blogs, and – the coup de grace – Rush Limbaugh's airways. The piece was hijacked and "repurposed" from its original meaning to show that I was a racist because I had dared to talk about race. I had dared to talk about an "American god", which was clearly not GOD.
In the wake of the Zimmerman verdict, several Black academics have received the hate tweet and email treatment from those disgruntled with our analysis of the role of race in the trial. Some, like Mark Sawyer of UCLA, even had social media accounts hacked. I created a Tumblr of racist tweets and emails to both chronicle the racist missives of my detractors, both for campus security and as a teaching tool. Several theologians wrote responses buttressing my piece, but the right wing spin machine portrayed me as a racist, liberal professor with bad ratings who should be fired.
What is the role of a public intellectual in the age of Twitter and soundbites? Is it to share your thoughts for the public good, or is it to curate the heaps of hate emails, tweets and right-wing articles that trash your intellectual and social work?
As an academic who occasionally appears on television and writes both for the academy and the public, these questions are at the forefront of my mind as I both teach and mentor graduate students. It is one thing to endure the ire of your peers, quite another to have hatred heaped on you publically. Tenure was a walk in the park compared to the harassment I receive. Since September of 2012, when I made a comment on Twitter about a movie that was then thought to be the reason behind the attack on the American embassy in Benghazi, I have been routinely subjected to screeds from Fox news, Weazel Zippers, Twitchy, News Busters, and a myriad of other sites that have targeted me for my "liburl" viewpoint.
The University of Pennsylvania, and my wonderful colleagues in the Department of Religious Studies have been routinely sent hate emails about me. Calls to fire me are numerous. Some have even come from within the university. The Penn Switchboard is flooded with calls, and the more conservative alums threaten to stop contributing.
In this age of pseudo parity, when everyone, anyone with a computer can critique one's work and life, what passes for knowledge? We know how to measure the worth of articles and books in the academy. The public has another standard altogether. In the age of conservative grievances about education however, how many people will be willing to go through what I do every time I publish an op-ed or in order to share what they have spent a lifetime to learn?
Not many. Because of what David Frum so aptly referred to as the "conservative entertainment complex", the feeding frenzy on the web to be the first to soundbite words and opinion pieces to get page hits and followers is fierce. Spin, spew and repeat is the name of this game. In the hopes of silencing me, they are willing to attempt to deny my first amendment rights through a barrage of hate in order to preserve theirs. Religion, race, and sexuality are all subjects they feel free to weigh in on, and these are the ones they so often attack when the viewpoints expressed are not conservative ones.
While I am a tenured faculty member, many younger scholars are being stymied from sharing with the public because of these types of attacks. There are plenty of battles within the academy about race and racism. When the right-wing echo chamber comes together to disparage and shout down voices engaging the public by accusing us of racism, they become the race baiters they so desperately seek to call me. I only wonder what William Buckley or Barry Goldwater would say if their could see their intellectual heirs today. I have no illusion that either man would like me, but I could imagine we could have a more civil conversation than what I experienced in this last academic year.
America is in a fragile place right now. Those on the right believe that they want to take their nation back, and those on the left believe that what our nation stands for is being eroded away by the policies of those on the right who want to return to the good old days. Universities and colleges are one of the few places in America that we can engage these ideas in the classroom without cursing and denigrating those we disagree with. Whatever side you find yourself on, ask yourself if the present state of discourse in print and on the air is what you want your children and students to grow up with.
Major opinion shifts, in the US and Congress,
on NSA surveillance and privacyPew finds that, for the first time since 9/11, Americans are now more worried about civil liberties abuses than terrorism
Glenn Greenwald, theguardian.com, Monday 29 July 2013 07.33 EDT, Article Source
The NSA headquarters in Fort Meade, Maryland. Photograph: EPANumerous polls taken since our reporting on previously secret NSA activities first began have strongly suggested major public opinion shifts in how NSA surveillance and privacy are viewed. But a new comprehensive poll released over the weekend weekend by Pew Research provides the most compelling evidence yet of how stark the shift is.
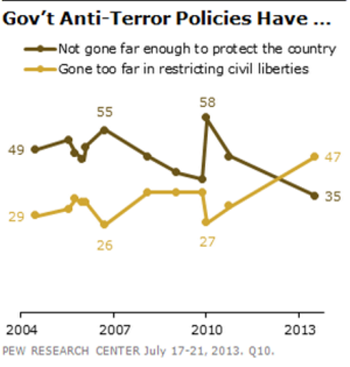
Among other things, Pew finds that "a majority of Americans – 56% – say that federal courts fail to provide adequate limits on the telephone and internet data the government is collecting as part of its anti-terrorism efforts." And "an even larger percentage (70%) believes that the government uses this data for purposes other than investigating terrorism." Moreover, "63% think the government is also gathering information about the content of communications." That demonstrates a decisive rejection of the US government's three primary defenses of its secret programs: there is adequate oversight; we're not listening to the content of communication; and the spying is only used to Keep You Safe™.
But the most striking finding is this one:
"Overall, 47% say their greater concern about government anti-terrorism policies is that they have gone too far in restricting the average person's civil liberties, while 35% say they are more concerned that policies have not gone far enough to protect the country. This is the first time in Pew Research polling that more have expressed concern over civil liberties than protection from terrorism since the question was first asked in 2004."
For anyone who spent the post-9/11 years defending core liberties against assaults relentlessly perpetrated in the name of terrorism, polling data like that is nothing short of shocking. This Pew visual underscores what a radical shift has occurred from these recent NSA disclosures:
Perhaps more amazingly still, this shift has infected the US Congress. Following up on last week's momentous House vote - in which 55% of Democrats and 45% of Republicans defied the White House and their own leadership to vote for the Amash/Conyers amendment to ban the NSA's bulk phone records collection program - the New York Times has an article this morning which it summarizes on its front page this way:
The article describes how opposition to the NSA, which the paper says was recently confined to the Congressional "fringes", has now "built a momentum that even critics say may be unstoppable, drawing support from Republican and Democratic leaders, attracting moderates in both parties and pulling in some of the most respected voices on national security in the House."
It describes how GOP Rep. Jim Sensenbrenner - a prime author of the Patriot Act back in 2001 and a long-time defender of even the most extremist War on Terror policies - has now become a leading critic of NSA overreach. He will have "a bill ready when Congress returned from its August recess that would restrict phone surveillance to only those named as targets of a federal terrorism investigation, make significant changes to the secret court that oversees such programs and give businesses like Microsoft and Google permission to reveal their dealings before that court."
Democratic Rep. Zoe Lofgren is quoted this way: "There is a growing sense that things have really gone a-kilter here". Yesterday on This Week with George Stephanopoulos, Democratic Sen Dick Durbin, one of Obama's closest Senate allies, said that the recently revealed NSA bulk record collection program "goes way too far".
The strategy for the NSA and its Washington defenders for managing these changes is now clear: advocate their own largely meaningless reform to placate this growing sentiment while doing nothing to actually rein in the NSA's power. "Backers of sweeping surveillance powers now say they recognize that changes are likely, and they are taking steps to make sure they maintain control over the extent of any revisions," says the NYT.
The primary problem enabling out-of-control NSA spying has long been the Intelligence Committees in both houses of Congress. That's an ironic twist given that those were the committees created in the wake of the mid-1970s Church Committee to provide rigorous oversight, as a response to the recognition that Executive Branch's surveillance powers were being radically abused - and would inevitably be abused in the future - without robust transparency and accountability.
But with a few rare and noble exceptions, the Intelligence Committees in both houses of Congress are filled with precisely those members who are most slavishly beholden to, completely captured by, the intelligence community over which they supposedly serve as watchdogs. Many receive large sums of money from the defense and intelligence industries.
There is a clear and powerful correlation between NSA support and amounts of money received by these members from those industries, as Wired's Dave Kravets adeptly documented about last week's NSA vote and has been documented before with similar NSA-protecting actions from the Intelligence Committee. In particular, the two chairs of those committees - Democrat Dianne Feinstein in the Senate and Republican Mike Rogers in the House - are such absolute loyalists to the NSA and the National Security State generally that it is usually impossible to distinguish their behavior, mindset and comments from those of NSA officials.
In sum, the Senate and House Intelligence Committees are the pure embodiment of the worst of Washington: the corrupting influence of money from the very industries they are designed to oversee and the complete capture by the agencies they are supposed to adversarially check. Anything that comes out of the leadership of those two Committees that is labeled "NSA reform" is almost certain to be designed to achieve the opposite effect: to stave off real changes in lieu of illusory tinkering whose real purpose will be to placate rising anger.
But that trick seems unlikely to work here. What has made these disclosures different from past NSA scandals - including ones showing serious abuse of their surveillance powers - are the large numbers of the NSA's own documents that are now and will continue to be available for the public to see, as well the sustained, multi-step nature of these disclosures, which makes this far more difficult for NSA defenders to predict, manage and dismiss away. At least as much as they are shining long-overdue light on these specific NSA domestic programs, the NSA disclosures are changing how Americans (and people around the world) think about the mammoth National Security State and whether it can and should be trusted with unchecked powers exercised in the dark. Those public opinion shifts aren't going to disappear as the result of some blatantly empty gestures from Dianne Feinstein and Mike Rogers masquerading as "reform".
Despite the substantial public opinion shifts, Pew found that Americans are largely split on whether the NSA data-collection program should continue. The reason for this is remarkable and repugnant though, at this point, utterly unsurprising:
Nationwide, there is more support for the government's data-collection program among Democrats (57% approve) than among Republicans (44%), but both parties face significant internal divisions: 36% of Democrats disapprove of the program as do 50% of Republicans.
Just as Democrats went from vehement critics of Bush's due-process-free War on Terror policies to vocal cheerleaders of Obama's drone kills and even Guantanamo imprisonments, the leading defenders of the NSA specifically and America's Surveillance State generally are now found among self-identified Democrats. That was embodied by how one of the most vocal Democratic NSA critics during the Bush years - Nancy Pelosi - in almost single-handedly saved the NSA from last week's House vote. If someone had said back in 2007 that the greatest support for NSA surveillance would be found among Democrats, many would find the very idea ludicrous. But such is life in the Age of Obama: one of his most enduring legacies is transforming his party from pretend-opponents of the permanent National Security State into its most enthusiastic supporters.
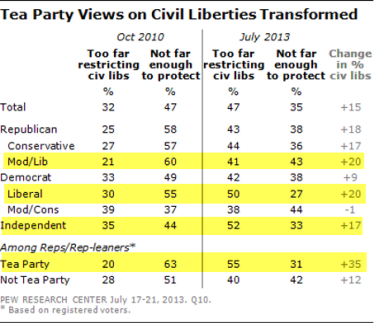
But despite that hackish partisan opportunism, the positive opinion changes toward NSA surveillance and civil liberties can be seen across virtually all partisan and ideological lines:
The largest changes toward demanding civil liberties protections have occurred among liberal Democrats, Tea Party Republicans, independents and liberal/moderate Republicans. Only self-identified "moderate/conservative Democrats" - the Obama base - remains steadfast and steady in defense of NSA surveillance. The least divided, most-pro-NSA caucus in the House for last week's vote was the corporatist Blue Dog Democrat caucus, which overwhelmingly voted to protect the NSA's bulk spying on Americans.
As I've repeatedly said, the only ones defending the NSA at this point are the party loyalists and institutional authoritarians in both parties. That's enough for the moment to control Washington outcomes - as epitomized by the unholy trinity that saved the NSA in the House last week: Pelosi, John Bohener and the Obama White House - but it is clearly not enough to stem the rapidly changing tide of public opinion.
Other related matters
(1) I was on ABC's This Week with Stephanopoulos discussing our newest NSA revelation coming this week about the actual surveillance powers of low-level NSA analysts. That interview be seen here.
(2) On Wednesday morning, I'll be testifying, by remote video, before an ad hoc committee in the House of Representatives about NSA disclosures. It begins at 9:30 am ET and will, I believe, be broadcast on C-SPAN. Following my testimony will be an excellent panel featuring representatives of the ACLU and the Cato Institute on the dangers and excesses of the NSA.
(3) At an event in Geneva over the week, Noam Chomsky was asked about Edward Snowden and these NSA stories. The transcript of his response is here, and the video can be seen here (it begins at roughly 1:21:00). It's definitely worth reading or watching what he has to say.
(4) If I had to pick the most astonishing aspect of this episode so far, it would be that everyone now knows that the Obama administration's top national security official, Director of National Intelligence James Clapper, outright lied to the Senate about NSA programs. And yet - as I said on ABC yesterday morning - not only isn't he being prosecuted for that crime - as much of a crime as anything Edward Snowden is accused of doing - but he still has his job. That, of course, is because the "law" does not apply to high-level Washington officials and DC's National Security State is an accountability-free zone. But the law that makes Clapper's behavior a felony is clear and concise, and can be read here.
Did the Bush & Obama Administrations Commit Crimes Worse than Whistler Blower Bradley Manning?
NSA amendment's narrow defeat spurs privacy advocates for surveillance fight
Did George Zimmerman Commit A Crime Worse than Whistler Blower Bradley Manning?
Zimmerman juror comes forward and says he 'got away with murder'
Did Halliburton Commit Crimes Worse than Whistler Blower Bradley Manning?
Gulf oil spill: Halliburton to plead guilty to destroying evidence
Keith Lampe ~ Co-Founder of YIPPIE and Progressive Activist Groups + YouTube Video Channel
Edward Snowden's not the story. The fate of the internet is
The press has lost the plot over the Snowden revelations. The fact is that the net is finished as a global network and that US firms' cloud services cannot be trusted
John Naughton, The Observer, Saturday 27 July 2013, Article Source
While the press concentrates on the furore surrounding Edward Snowden's search for political asylum,
it has forgotten the importance of his revelations. Photograph: Tatyana Lokshina/APRepeat after me: Edward Snowden is not the story. The story is what he has revealed about the hidden wiring of our networked world. This insight seems to have escaped most of the world's mainstream media, for reasons that escape me but would not have surprised Evelyn Waugh, whose contempt for journalists was one of his few endearing characteristics. The obvious explanations are: incorrigible ignorance; the imperative to personalise stories; or gullibility in swallowing US government spin, which brands Snowden as a spy rather than a whistleblower.
In a way, it doesn't matter why the media lost the scent. What matters is that they did. So as a public service, let us summarise what Snowden has achieved thus far.
Without him, we would not know how the National Security Agency (NSA) had been able to access the emails, Facebook accounts and videos of citizens across the world; or how it had secretly acquired the phone records of millions of Americans; or how, through a secret court, it has been able to bend nine US internet companies to its demands for access to their users' data.
Similarly, without Snowden, we would not be debating whether the US government should have turned surveillance into a huge, privatised business, offering data-mining contracts to private contractors such as Booz Allen Hamilton and, in the process, high-level security clearance to thousands of people who shouldn't have it. Nor would there be – finally – a serious debate between Europe (excluding the UK, which in these matters is just an overseas franchise of the US) and the United States about where the proper balance between freedom and security lies.
These are pretty significant outcomes and they're just the first-order consequences of Snowden's activities. As far as most of our mass media are concerned, though, they have gone largely unremarked. Instead, we have been fed a constant stream of journalistic pap – speculation about Snowden's travel plans, asylum requests, state of mind, physical appearance, etc. The "human interest" angle has trumped the real story, which is what the NSA revelations tell us about how our networked world actually works and the direction in which it is heading.
As an antidote, here are some of the things we should be thinking about as a result of what we have learned so far.
The first is that the days of the internet as a truly global network are numbered. It was always a possibility that the system would eventually be Balkanised, ie divided into a number of geographical or jurisdiction-determined subnets as societies such as China, Russia, Iran and other Islamic states decided that they needed to control how their citizens communicated. Now, Balkanisation is a certainty.
Second, the issue of internet governance is about to become very contentious. Given what we now know about how the US and its satraps have been abusing their privileged position in the global infrastructure, the idea that the western powers can be allowed to continue to control it has become untenable.
Third, as Evgeny Morozov has pointed out, the Obama administration's "internet freedom agenda" has been exposed as patronising cant. "Today," he writes, "the rhetoric of the 'internet freedom agenda' looks as trustworthy as George Bush's 'freedom agenda' after Abu Ghraib."
That's all at nation-state level. But the Snowden revelations also have implications for you and me.
They tell us, for example, that no US-based internet company can be trusted to protect our privacy or data. The fact is that Google, Facebook, Yahoo, Amazon, Apple and Microsoft are all integral components of the US cyber-surveillance system. Nothing, but nothing, that is stored in their "cloud" services can be guaranteed to be safe from surveillance or from illicit downloading by employees of the consultancies employed by the NSA. That means that if you're thinking of outsourcing your troublesome IT operations to, say, Google or Microsoft, then think again.
And if you think that that sounds like the paranoid fantasising of a newspaper columnist, then consider what Neelie Kroes, vice-president of the European Commission, had to say on the matter recently. "If businesses or governments think they might be spied on," she said, "they will have less reason to trust the cloud, and it will be cloud providers who ultimately miss out. Why would you pay someone else to hold your commercial or other secrets, if you suspect or know they are being shared against your wishes? Front or back door – it doesn't matter – any smart person doesn't want the information shared at all. Customers will act rationally and providers will miss out on a great opportunity."
Spot on. So when your chief information officer proposes to use the Amazon or Google cloud as a data-store for your company's confidential documents, tell him where to file the proposal. In the shredder.
For the Record
It was the Bush Administration, with Democrat and Republican support, who authorized SPYING on U.S. citizens; while giving Telecoms and Tech Corporations a free pass for knowingly breaking law, and passed an illegal Patriot Act without ever reading it. These are the same baby killers & child sodomizers who, for the most part, voted for an illegal Iraq war based on lies, supported Israel's murder and maiming of United States Naval personnel aboard the USS Liberty, supplied Iraq with biological and chemical weapons from U.S. manufacturers, appointed Bush president, and more than likely had something to do with the mass murders of 9/11. The criminal sentence for these atrocities & crimes against humanity and US citizens was a political pardon by a "Yes We Can" liar man.
THEY RETURNED
THEY Took Your Jobs
THEY Took Your Money
THEY Took Your Homes
THEY Started Illegal Wars
THEY Destroyed the Economy
THEY Murdered Women & Children
THEY Put Martha Stewart & Tommy Chong In Jail
THEY Held the Teachers Accountable
THEY Committed the Real Crimes,
Brought Disgrace to The People of the United States,
were never brought up on charges, thanks to Obama,
and WALK FREE TODAY !!!
Amash amendment: the full roll call
The full roll call of votes for and against the Amash amendment to rein in the National Security Agency
guardian.co.uk, Wednesday 24 July 2013 22.48 EDT, Article Source
The Amash amendment was defeated narrowly in a congressional vote. Photograph: Alex Wong/Getty ImagesAyes: 205 (Republican 94, Democrat 111)
Amash, Amodei, Bachus, Barton, Bass, Becerra, Bentivolio, Bishop (UT), Black, Blackburn, Blumenauer, Bonamici, Brady (PA), Braley (IA), Bridenstine, Broun (GA), Buchanan, Burgess, Capps,Capuano, Cárdenas, Carson (IN), Cartwright, Cassidy, Chabot, Chaffetz, Chu, Cicilline, Clarke, Clay, Cleaver, Clyburn, Coffman, Cohen, Connolly, Conyers, Courtney, Cramer, Crowley, Cummings, Daines, Davis D, Davis R, DeFazio, DeGette, DeLauro, DelBene, DeSantis, DesJarlais, Deutch, Dingell, Doggett, Doyle, Duffy, Duncan (SC), Duncan (TN), Edwards, Ellison, Eshoo, Farenthold, Farr, Fattah, Fincher, Fitzpatrick, Fleischmann, Fleming, Fudge, Gabbard, Garamendi, Gardner, Garrett, Gibson, Gohmert, Gosar, Gowdy, Graves (GA), Grayson, Green G, Griffin (AR), Griffith (VA), Grijalva, Hahn, Hall, Harris, Hastings (FL), Holt, Honda, Huelskamp, Huffman, Huizenga (MI), Hultgren, Jeffries, Jenkins, Johnson (OH), Jones, Jordan, Keating, Kildee, Kingston, Labrador, LaMalfa, Lamborn, Larson (CT), Lee (CA), Lewis, Loebsack, Lofgren, Lowenthal, Lujan Grisham (NM), Luján BR (NM), Lummis, Lynch, Maffei, Maloney C, Marchant, Massie, Matsui, McClintock, McCollum, McDermott, McGovern, McHenry, McMorris Rodgers, Meadows, Mica, Michaud, Gary Miller, George Miller, Moore, Moran, Mullin, Mulvaney, Nadler, Napolitano, Neal, Nolan, Nugent, O'Rourke, Owens, Pascrell, Pastor (AZ), Pearce, Perlmutter, Perry, Petri, Pingree (ME), Pocan, Poe (TX), Polis, Posey, Price (GA), Radel, Rahall, Rangel, Ribble, Rice (SC), Richmond, Roe (TN), Rohrabacher, Ross, Rothfus, Roybal-Allard, Rush, Salmon, Linda T Sánchez, Loretta Sanchez, Sanford, Sarbanes, Scalise, Schiff, Schrader, Schweikert, Scott (VA), Sensenbrenner, Serrano, Shea-Porter, Sherman, Smith (MO), Smith (NJ), Southerland, Speier, Stewart, Stockman, Swalwell (CA), Takano, Thompson (MS), Thompson (PA), Tierney, Tipton, Tonko, Tsongas, Vela, Velázquez, Walz, Waters, Watt, Waxman, Weber (TX), Welch, Williams, Wilson (SC), Yarmuth, Yoder, Yoho, Young (AK)
Noes: 217 (Republican 134, Democrat 83)
[Ed. Note: These are the ??? perverted politicians ??? who want to spy on US voters and sold out US citizens:]
Aderholt, Alexander, Andrews, Bachmann, Barber, Barr, Barrow (GA), Benishek, Bera (CA), Bilirakis, Bishop (GA), Bishop (NY), Boehner, Bonner, Boustany, Brady (TX), Brooks (AL), Brooks (IN), Brown (FL), Brownley (CA), Bucshon, Butterfield, Calvert, Camp, Cantor, Capito, Carney, Carter, Castor (FL), Castro (TX), Cole, Collins (GA), Collins (NY), Conaway, Cook, Cooper, Costa, Cotton, Crawford, Crenshaw, Cuellar, Culberson, Davis (CA), Delaney, Denham, Dent, Diaz-Balart, Duckworth, Ellmers, Engel, Enyart, Esty, Flores, Forbes, Fortenberry, Foster, Foxx, Frankel (FL), Franks (AZ), Frelinghuysen, Gallego, Garcia, Gerlach, Gibbs, Gingrey (GA), Goodlatte, Granger, Graves (MO), Green A, Grimm, Guthrie, Gutiérrez, Hanabusa, Hanna, Harper, Hartzler, Hastings (WA), Heck (NV), Heck (WA), Hensarling, Higgins, Himes, Hinojosa, Holding, Hoyer, Hudson, Hunter, Hurt, Israel, Issa, Lee Jackson, Johnson (GA), Johnson EB, Johnson S, Joyce, Kaptur, Kelly (IL), Kelly (PA), Kennedy, Kilmer, Kind, King (IA), King (NY), Kinzinger (IL), Kirkpatrick, Kline, Kuster, Lance, Langevin, Lankford, Larsen (WA), Latham, Latta, Levin, Lipinski, LoBiondo, Long, Lowey, Lucas, Luetkemeyer, Sean Maloney, Marino, Matheson, McCarthy (CA), McCaul, McIntyre, McKeon, McKinley, McNerney, Meehan, Meeks, Meng, Messer, Miller (FL), Miller (MI), Murphy (FL), Murphy (PA), Neugebauer, Noem, Nunes, Nunnelee, Olson, Palazzo, Paulsen, Payne, Pelosi, Peters (CA), Peters (MI), Peterson, Pittenger, Pitts, Pompeo, Price (NC), Quigley, Reed, Reichert, Renacci, Rigell, Roby, Rogers (AL), Rogers (KY), Rogers (MI), Rooney, Ros-Lehtinen, Roskam, Royce, Ruiz, Runyan, Ruppersberger, Ryan (OH), Ryan (WI), Schakowsky, Schneider, Schwartz, Scott A, Scott D, Sessions, Sewell (AL), Shimkus, Shuster, Simpson, Sinema, Sires, Slaughter, Smith (NE), Smith (TX), Smith (WA), Stivers, Stutzman, Terry, Thompson (CA), Thornberry, Tiberi, Titus, Turner, Upton, Valadao, Van Hollen, Vargas, Veasey, Visclosky, Wagner, Walberg, Walden, Walorski, Wasserman, Schultz, Webster (FL), Wenstrup, Westmoreland, Whitfield, Wilson (FL), Wittman, Wolf, Womack, Woodall, Young (FL), Young (IN),
Not voting: 12 (Republican 6, Democrat 6)
Barletta, Beatty, Bustos, Campbell, Coble, Herrera Buetler, Horsford, McCarthy, Negrete McLeod, Pallone, Rokita, Schock
NSA surveillance:
narrow defeat for amendment to restrict data collectionFirst major challenge to NSA's bulk collection of phone records defeated by only 217 votes to 205 in House of Representatives
Spencer Ackerman in Washington, The Guardian, Wednesday 24 July 2013, Article Source
Justin Amash, said he introduced the amendment to 'defend the fourth amendment …
to defend the privacy of each and every American'. Photo: J Scott Applewhite/APThe first major legislative challenge to the National Security Agency's bulk collection of phone records from millions of Americans was defeated by only a narrow margin on Wednesday, sending a clear signal to the Obama administration that congressional anger about the extent of domestic surveillance is growing.
Despite a concerted lobbying effort by the White House and senior intelligence figures, the attempt to rein in the NSA failed by only 12 votes. The final vote was 205 in favor and 217 against, exposing deep restiveness in Congress over the wisdom and constitutionality of the bulk surveillance on Americans less than two months after the Guardian exposed it, thanks to leaks from whistleblower Edward Snowden. A shift of seven votes would have changed the outcome.
Civil libertarians disappointed by the vote promised not to relent in opposing what they consider an unnecessary and unconstitutional violation of Americans' privacy.
The principal author of the effort, Michigan Republican Justin Amash, said he introduced his amendment to the annual Defense Department appropriations bill to "defend the fourth amendment, to defend the privacy of each and every American."
In opposition, the chairman of the House intelligence committee, Mike Rogers of Michigan, asked: "Have we forgotten what happened on September 11?" Swiping at Amash, who was supported by an online campaign, he asked: "Are we so small we can only look at how many Facebook likes we have?"
Congressman Mac Thornberry, a Texas Republican on the intelligence committee, called the abridgment of the NSA's power "foolhardy," saying it was an "overreaction that increases the danger" from terrorism.
There were some unlikely alliances: the Democratic minority leader, Nancy Pelosi, voted against the amendment with Michele Bachmann, a Tea Party Republican. John Boehner, the House speaker, found himself in the rare position of being on the same side as President Obama.
The measure, known as the Amash amendment, sought to end the NSA's years-long secret practice of collecting the phone records of millions of Americans unsuspected of any crime or foreign intelligence threat. Senator Ron Wyden, an Oregon Democrat, said the effort dangerously provided the NSA with a "human relationship database," something as or potentially more intrusive than the contents of Americans' phone calls.
Members of Congress of both parties opposed to the bulk NSA surveillance compared it to general warrants issued by the British colonists. The raucous and passionate debate exposed deep divisions in Congress over the propriety of the surveillance, contrary to assertions by the Obama administration and its allies that Congress had already granted its approval for the effort before it became public.
Campaigners said the narrow margin of defeat sent a clear signal about the strength of opposition to the measures. Michelle Richardson, the surveillance lobbyist at the American Civil Liberties Union, described the vote as a "sea change" in how Congress views bulk surveillance. "This is a great first step. It's the best vote we've ever had on the Patriot Act," said the ACLU's surveillance lobbyist.
Richardson cited a pledge made during the debate by Rogers, the intelligence committee chairman, to add privacy protections on the program into the forthcoming intelligence authorization bill. "I think he has to do that now," she said. "It also puts pressure on the administration to release more information on the program, because Congress isn't buying what they're selling."
David Segal, executive director of Demand Progress, which helped organize an online campaign to support the amendment, said: "Today's vote shows that the tide is turning, that the American people, when they are aware of these programs, overwhelmingly reject them, and the expiration date on these programs is coming due."
Leading members of the House intelligence committee welcomed the vote. Rogers, the chairman, and ranking Democrat Dutch Ruppersberger, said the amendment would have "eliminated a crucial counterterrorism tool" and rejected privacy concerns. In a joint statement, they said: "The charge that the program tramples on the privacy of citizens is simply wrong. This program balances our duty to protect the privacy of our fellow Americans with the equal duty to protect the nation."
They promised to take measures to address public confidence in the progrmas, but did not give details.
The Obama administration, the intelligence agencies and their allies in Congress had made an all-out push to quash the amendment after it unexpectedly made it past the House rules committee late on Monday. For four hours on Tuesday, General Keith Alexander, the director of the NSA, implored legislators that preventing his agency from collecting the phone records on millions of Americans would have dire consequences for national security.
The White House entered the fray on Tuesday night, taking the unusual step of publicly objecting to a proposed amendment to a bill. Hours before the House began consideration of the Amash amendment, the US director of national intelligence, James Clapper, warned legislators that "acting in haste to defund the Fisa business records program risks dismantling an important intelligence tool."
While most contentious House votes in recent years have been marked by partisanship, the Amash amendment crossed party lines. Obama was joined in opposing Amash by seven Republican committee chairmen in the House, the Wall Street Journal, the conservative thinktank the Heritage Foundation, and an array of Bush-era national security officials, some of whom helped design the phone-records collection program.
For his part, Amash, a Republican, was joined by a coalition of libertarian Republicans and progressive Democrats. His amendment's principal Democratic ally was longtime Michigan representative John Conyers, the ranking member of the House judiciary committee. Applause broke out from both sides of the party aisle for speakers for and against the Amash amendment.
Joe Barton, a Texas Republican, said it was "simply wrong" for the NSA, which he called well-intentioned, to "collect the data in the first place of every phone call of every American every day."
Meanwhile, an announcement of the Amash amendment, issued by the House Democratic leadership, described the NSA's bulk phone records collection program as harvesting data from people "not already subject to an investigation".
In opposition to the Amash amendment, Tom Cotton, an Arkansas Republican and Iraq war veteran, said, "Folks, we are at war. You might not like that truth. I wish we were not at war. But it is the truth."
Before the vote, Mike Pompeo, a Kansas Republican, offered what appeared to be alternative to Amash's amendment, albeit one that "clarified" NSA could collect no content from Americans. It succeeded by a wide margin, having 15 minutes for members to vote. Legislators had only two minutes to vote for the Amash amendment.
The Amash amendment:
a vital shield from unwarranted NSA surveillanceCongress must use this crucial vote on the NSA's data dragnet to protect our privacy from the agency's intent to 'collect it all'
Alexander Abdo, guardian.co.uk, Wednesday 24 July 2013 07.00 EDT, Article Source
Deputy attorney general James Cole, Robert S Litt, general counsel in the Office of
Director of National Intelligence, NSA deputy director John Ingliss. Photograph: J Scott Applewhite/APThere's an extremely important vote taking place in Congress Wednesday 24 July that, if successful, would shut down the program under which the NSA indiscriminately collects the phone records of literally every US citizen and resident. The bipartisan amendment, proposed by Representative Justin Amash (Republican, Michigan), would forbid the NSA from expending any of its funds on the bulk collection of Americans' records, including our phone records collected pursuant to the program revealed in June by this newspaper.
Under that program, the NSA has forced American telecommunications providers – like AT&T, Sprint and Verizon – to turn over details about every single call that every single American makes "on an ongoing daily basis". The program is not limited to suspected terrorists, foreign agents or even everyday criminals. The NSA is collecting everything.
Did you call someone today? If so, the NSA has a record of it.
Ending this egregious overreach by the NSA is critical, but it's even more significant than most people realize. Here's why.
The NSA's collection of our phone records is not an isolated program. It represents a truly radical shift in the way the intelligence agencies do business. The government's goal is not just to collect all of our phone records, but, as one former intelligence official admitted, to "collect it all".
The NSA's endgame can be seen in the legal justification it offers for the program now being debated by Congress. The NSA argues that its collection of every American's phone records is constitutional because the agency stores the records in a lockbox and looks at the records only if and when it has a reason to search them. In other words, it claims that the constitution is not concerned with the acquisition of our sensitive data, only with the later searching of it.This is an extremely dangerous argument. For two centuries, American courts have taken the view that the constitution is concerned with the government's initial intrusion upon privacy, and not only with the later uses to which the government puts the information it has collected. That's why it is unconstitutional for the government, without a warrant, to seize your journal even if it never reads it; to record your phone call even if it never listens to it; or to videotape your bedroom activities even if it never presses play.
It is also the reason that the laws against wiretapping criminalize not only the use of our intercepted communications, but also their interception in the first place. Of course, the government's use of private information may aggravate the unlawful invasion of our privacy. But the constitution protects us from both.
This is as it should be. Even if the NSA isn't reading our every email or listening to our every call, knowing that an analyst might one day pull up our emails or web-browsing history for further scrutiny is chilling. Dissent and debate are stifled by the simple knowledge that our activities and communications are being recorded and archived.
But perhaps the most fundamental problem with the NSA's constitutional theory is that it has no limit. If the constitution is blind to the collection of our data and limits only the NSA's later uses of it, then the NSA truly can "collect it all" now and ask questions later. Our emails, phone calls and internet activities would all be very simple for the NSA to collect under the NSA's theory. But it could go much further. It could put video cameras on every street corner, it could install microphones in every home and it could even remotely copy the contents of every computer hard drive.
Some of this may sound far-fetched today, but the NSA's radical view of the constitution would, if accepted by Congress and the courts, fundamentally transform the relationship between citizen and government.
The vote in Congress Wednesday is an opportunity to reject that myopic view of our privacy rights. The amendment proposed by Congressman Amash wouldn't end all of the NSA's unconstitutional programs; but it would be a start, and it would be an important signal that Congress understands the implications of accepting the arguments that the NSA is now making.
House vote reflects growing revolt over NSA surveillance
Six weeks ago, only a few in Congress were ready to challenge the government on surveillance – but opposition has grown
Ewen MacAskill in New York, guardian.co.uk, Wednesday 24 July 2013 17.14 EDT, Article Source
Justin Amash has added his voice to the chorus of criticism over the NSA's bulk
collection of metadata. Photograph: J Scott Applewhite/APThe House vote to block NSA funding for one of its data collection programmes is the biggest manifestation yet of a revolt that has steadily grown over the last two months.
When the Guardian and Washington Post first revealed the documents leaked by former NSA contractor Edward Snowden, there were relatively few in Congress prepared openly to challenge the government over intrusions into privacy.
The challenge was largely restricted to the two long-term sceptics, senators Ron Wyden and Mark Udall. This left Barack Obama able to claim that the surveillance was not secret because every member of Congress had been briefed about it, and that every piece of legislation since 2006 related to it had been passed with large bipartisan majorities.
Towards the end of June, opposition to the surveillance programme began to grow. Wyden and Udall were joined by 24 other senators to send a joint letter to to intelligence chiefs complaining about a secret body of laws and misleading statements by officials.
At a House judiciary hearing last week, member after member said that while they had little sympathy for Snowden, they were glad about the revelations and repeatedly challenged the NSA and justice department officials at the hearing.
The scheduled House vote brings together a potent combination of progressive Democrats and libertarian Republicans. Such is the strength of feeling that they are prepared to defy not only pleas from the White House and personal appearances on the Hill by intelligence chiefs, but their own congressional leaders.
The very fact that the vote was to be held enraged the Wall Street Journal, which, in an editorial, wrote: "Few things are more dangerous than Congress in heat, and so it is this week as a libertarian-left wing coalition in the House of Representatives is rushing to neuter one of the National Security Agency's anti- terror surveillance programs."
It added: "The last thing Congress should do is kill a program in a rush to honor the reckless claims of Mr Snowden and his apologists."
Congress is due to begin a five-week recess at the start of August, and much of the momentum will go out off the issue, at least on the Hill. But there will be more hearings in in the autumn, and more votes. Proposed reform of the Patriot Act, which authorises much of the surveillance, has already been introduced. One of the changes would require the government to demonstrate a clear link to terrorism or spying before being allowed to collect Americans' private information.
Changes are also proposed to reform the ultra-secret Fisa court, which issues warrants for surveillance. Many members of Congress vote because they regard such issues as a matter of principle but others are also motivated by pressure from voters.
Wyden mentioned this on Tuesday in speech in Washington, saying Americans were stunned by the scale of the surveillance. "And, boy, are they angry. You hear it in the lunchrooms, town hall meetings and senior citizen centres," Wyden said.
And the public will almost certainly be still engaged in that debate when Congress returns in September. A Washington Post/ABC News poll published Wednesday showed concerns about personal privacy have grown. The poll suggested about three-quarters of Americans see the NSA programmes as infringing on their rights to privacy.
In the aftermath of 9/11, when there was overwhelming concern over security, the balance has gradually shifted, with the poll finding 57% in favour of unfettered investigations and 39% seeing protection of privacy as the more important.
There will likely be more disclosures in the media that will keep the debate alive. And legal actions are pending. A preliminary court hearing is scheduled for Thursday in New York at which the American Civil Liberties Union is challenging the constitutionality of the NSA's mass collection of phone records. The ACLU said it will be the first time that the government has been forced to address NSA surveillance in court.
All this puts pressure on the White House to act. The Obama administration responds that it has already made gestures but these are so minor and modest they have made little impact on public consciousness. Big concessions will be required to allay public concerns.
The growing revolt helps Snowden. The Washington Post/ABC News poll shows a drop in public support for him, with 53% saying he should be charged with a crime for his leaks against 43% less than a month ago. But the debate he started can only help him if he is ever arrives back on US soil. Given the debate he has started, it makes it harder for the justice department to argue that he is not a whistleblower,
For the moment, Snowden is at the mercy of the Russian authorities, possibly doomed to a life of exile there unless they relent and allow him to leave for Latin America – assuming a way can be found for him to get there avoiding US attempts to intercept him.
But he can at least have the satisfaction of feeling that the revolt has vindicated the disclosures he made in Hong Kong.
White House urges Congress to reject moves
to curb NSA surveillanceObama administration alarmed by vote on 'Amash amendment' aimed at blocking blanket surveillance of phone records
Spencer Ackerman in Washington, guardian.co.uk, Tuesday 23 July 2013 23.01 EDT, Article Source
The Obama administration has pleaded for Congress to scrap curbs on the power of the NSA
to tap into phone records. Photograph: Patrick Semansky/APThe Obama administration has forcefully urged the defeat of a legislative measure to curb its wide-ranging collection of Americans' phone records, setting up a showdown with the House of Representatives over domestic surveillance.
A statement from the White House press secretary, Jay Carney, late on Tuesday evening capped an extraordinary day of near-revolt on Capitol Hill concerning the secret National Security Agency surveillance programes revealed by ex-NSA contractor Edward Snowden and published by the Guardian and Washington Post.
The White House urged House members to vote against a measure from Representative Justin Amash, a Michigan Republican, that would stop the NSA siphoning up the telephone records of millions of Americans without suspicion of a crime.
"This blunt approach is not the product of an informed, open or deliberative process," said the statement emailed from the White House late on Tuesday in anticipation of a House debate on the Amash measure scheduled for Wednesday.
"We urge the House to reject the Amash amendment and instead move forward with an approach that appropriately takes into account the need for a reasoned review of what tools can best secure the nation."
In a reflection of how seriously the Obama administration is taking Amash's amendment to the defence department's annual appropriations bill – which unexpectedly cleared the House rules committee late on Monday – the NSA's director, General Keith Alexander, spent four hours on Capitol Hill on Tuesday in closed-door meetings Amash described to the Guardian as a "general informational briefing".
Hours after Alexander's bull sessions with legislators, two of his main congressional allies, Representatives Mike Rogers and Dutch Ruppersberger, the Republican and Democratic leaders of the House intelligence committee, also urged colleagues to vote down Amash's amendment.
"While many members have legitimate questions about the NSA metadata program, including whether there are sufficient protections for Americans' civil liberties, eliminating this program altogether without careful deliberation would not reflect our duty under article 1 of the constitution to provide for the common defence," Rogers and Ruppersberger wrote in an open letter to their colleagues on Tuesday, warning Amash's effort would have "unintended consequences for the intelligence and law enforcement communities beyond the metadata program".
It is relatively rare for the White House to voice its perspective on a legislative manoeuvre ahead of its adoption by a chamber of congress. Amash's measure – one of several amendments to the defence department funding bill — is scheduled for debate on Wednesday and for a vote as early as Wednesday night or Thursday morning. A vote to include it in the bill would not be the end of congressional debate over the bulk collection of phone records.
"It's been an extraordinary day on Capitol Hill as insiders scramble to block the growing chorus of support for the Amash anti-surveillance amendment," said David Segal, the executive director of the progressive organisation Demand Progress, which supports Amash's amendment.
"It's appropriate: Just as the NSA's domestic spying apparatus is evidence of some of our leaders' fear of the American people, these extraordinary actions by the White House and the NSA evidence their fear that the will of Americans will be codified in the law tomorrow.
"They've been brought to this point because in the last 24 hours tens of thousands of Americans, organised by a broad coalition of progressive and conservative organisations – along with several web platforms – have called Congress to make it known that they will not stand for broad based domestic spying by our own government."
Earlier on Tuesday, one of the leading legislative critics of the NSA's bulk surveillance on Americans' phone records, Senator Ron Wyden, an Oregon Democrat, attacked both the surveillance and what he described as a "culture of misinformation" by administration and intelligence officials about it.
Wyden, who predicted two weeks ago that the administration might be open to changing the bulk phone-records programme, suggested during a speech at the Centre for American Progress that intelligence officials would fight an effort to restrict a growing series of post-9/11 surveillance powers.
"As we have seen in recent days, the intelligence leadership is determined to hold on to this authority," Wyden said. "Merging the ability to conduct surveillance that reveals every aspect of a person's life with the ability to conjure up the legal authority to execute that surveillance, and finally, removing any accountable judicial oversight, creates the opportunity for unprecedented influence over our system of government."
Wyden termed that effort a threat that "chips needlessly away at the liberties and freedoms our founders established for us, without the benefit of actually making us any safer".
The White House – which did not release much information about the secret bulk surveillance efforts it has maintained after inheriting the regime from the Bush administration – portrayed itself on Tuesday as open to a continuing dialogue about the proper limits of surveillance. It framed Amash's amendment as rashly ending the bulk surveillance of phone records, while the administration was committed thoughtfully reforming it, although it has yet to publicly announce any reforms.
"In light of the recent unauthorised disclosures the president has said that he welcomes a debate about how best to simultaneously safeguard both our national security and the privacy of our citizens," said the statement attributed to Carney.
"We look forward to continuing to discuss these critical issues with the American people and the Congress."
Wyden noted during his speech at the administration-aligned thinktank that he thought the administration had agreed with him when it first came to office about the problems of maintaining widespread secrecy over surveillance.
"In the summer of 2009 I received a written commitment from the justice department and the office of the director of national intelligence that a process would be created to start redacting and declassifying Fisa court opinions so that the American people could have some idea of what the government believes the law allows it to do," Wyden said. "In the last four years exactly zero opinions have been released."
Nobody Listens the First Time Around
None of the Above
Should Be A Choice On Voter Ballots
http://www.nobodyforpresident.org/
Interesting Reads:
Space invasion: Solar storms pose critical threat to US infrastructure
Police departments and data mining companies team up to track license plates
Black Hat hackers break into any iPhone in under a minute, using a malicious charger
BitTorrent Sync released: The secure, cloud-avoiding sync tool you’ve been waiting for
Keith Lampe ~ Co-Founder of YIPPIE and Progressive Activist Groups + Video Channel
Keith Lampe, Ro-Non-So-Te, Ponderosa Pine
Happy 82nd Birthday Pondo !!! - July 25th
Notes from ~@~
PHOENIX ~ SACRAMENTO ~ KANSAS CITY ~ MINNEAPOLIS ~ CHICAGO ~ CLEVELAND ~ BIRMINGHAM ~ DALLAS ~ SEATTLE ~ BRIDGEPORT ~ NEW YORK ~ DENVER ~ LOS ANGELES ~ Sponsored by Speed and Strength
Boycott Google ~ For their role in an illegal surveillance program used against their own users
Ben Jennings on David Cameron's instruction to web companies to block child sexual abuse searches, Source
NOW IT'S YOUR MORAL DUTY TO BLOCK THESE SEARCH TERMS. POST-HASTE!
DAVE'S SEARCH ENGINE BLACK LIST:
LYNTON CROSBY (or LIZARD of OZ)
REPPERCUSSIONS of FRACKING
PLAIN CIGARETTE PACKAGING IN UK
LIVING WAGE
BEDROOM TAX
NHS PRIVATISATION
2010 TORY MANIFESTO
(or ANY QUOTES/PROMISES FROM ELECTION CAMPAIGN)
[CONTINUED...]
Bombs dropped on Great Barrier Reef marine park
[Ed. Question: Has the Obama Administration declared that The Great Barrier Reef is a terrorist?]
Senator asks 'have we gone mad?' after US planes jettison four unarmed bombs in training exercise gone wrong
Associated Press in Canberra, guardian.co.uk, Saturday 20 July 2013 21.20 EDT, Article Source
The US military said four unarmed bombs were dropped in the Great Barrier Reef marine park.
Photograph: Grant V Faint/GettyThe US Navy says it may try to salvage four unarmed bombs dropped by fighter jets into Australia's Great Barrier Reef marine park last week when a training exercise went wrong.
The two AV-8B Harrier jets, launched from the aircraft carrier USS Bonhomme Richard, each jettisoned an inert practice bomb and an unarmed laser-guided explosive bomb into the World Heritage-listed marine park off the coast of Queensland on Tuesday, the US 7th Fleet said in a statement on Saturday.
The four bombs, weighing a total 1.8 metric tons (4,000 pounds), were dropped into more than 50 metres (164ft) of water, away from coral, to minimise possible damage to the reef, the statement said. None exploded.
The Great Barrier Reef marine park authority said in a statement that identifying options for the "rapid recovery" of the bombs so that they could pose no risk to the marine park was "a high priority". But the authority also said the ordnances posed a "low risk to the marine environment".
US 7th Fleet spokesman Lieutenant David Levy said on Monday the Navy was reviewing the possibility of retrieving the ordnances in consultation with Australian authorities.
"If the park service and the government agencies of Australia determine that they want those recovered, then we will co-ordinate with them on that recovery process," Levy said in an email.
The jets, from the 31st Marine Expeditionary Unit, had intended to drop the ordnances on the Townshend Island bombing range, but aborted the mission when controllers reported the area was not clear of hazards.
"It was not safe to drop the bombs. There were civilian boats right below them," fleet commander William Marks told Australian ABC radio on Monday.
The pilots conducted the emergency jettison because they were low on fuel and could not land with their bomb load, the Navy said.
"The Harriers ... needed to get back to the ship, and so they conducted an emergency jettison," Marks said.
The emergency happened on the second day of the biennial joint training exercise Talisman Saber, which brings together 28,000 US and Australian military personnel over three weeks. The US Navy and Marine Corps were working with Australian authorities to investigate the incident, the Navy said.
A 7th Fleet spokesman did not immediately respond on Sunday, when asked by email whether the dumping posed any environmental risk.
Australian Senator Larissa Waters, the Greens spokeswoman on the Great Barrier Reef, described the dumping of bombs in such an environmentally sensitive area as "outrageous" and said it should not be allowed.
"Have we gone completely mad?" she told the ABC. "Is this how we look after our World Heritage area now? Letting a foreign power drop bombs on it?"
Graeme Dunstan, who is among environmentalists and anti-war activists demonstrating against the joint exercises, said the mishap proved that the US military could not be trusted to protect the environment.
"How can they protect the environment and bomb the reef at the same time? Get real," Dunstan said from the Queensland coastal town of Yeppoon, near where the war games are taking place.
The Great Barrier Reef, the world's largest network of coral structures, is rich in marine life and stretches more than 3,000km (1,800 miles) along Australia's north-east coast.
Helen Thomas - in pictures
Helen Thomas, UPI Washington Reporter, at work in the White House ~ Photograph: Bettmann/CorbisThe pioneering White House correspondent Helen Thomas has died, aged 92. The veteran journalist covered 10 presidencies, becoming a White House fixture from 1961 until her retirement in 2010 ~ Click to view photographs
Josy Forsdike, guardian.co.uk, Saturday 20 July 2013 12.20 EDT, Article/Picture Source
Apple Developer site hack:
Turkish security researcher claims responsibilityTurkish security researcher claims to have found flaw in system, which has been offline since Thursday as company 'rebuilds and strengthens' security around databases
Charles Arthur, guardian.co.uk, Monday 22 July 2013 04.55 EDT, Article Source
Developers at Apple's Worldwide Developers Conference in June. Some may have now
seen details stolen by hackers. (AP Photo/Eric Risberg) Photograph: Eric Risberg/APApple says its Developer portal has been hacked and that some information about its 275,000 registered third-party developers who use it may have been stolen.
The portal at developer.apple.com had been offline since Thursday without explanation, raising speculation among developers first that it had suffered a disastrous database crash, and then that it had been hacked.
A Turkish security researcher, Ibrahim Balic, claims that he was behind the "hack" but insisted that his intention was to demonstrate that Apple's system was leaking user information. He posted a video on Youtube which appears to show that the site was vulnerable to an attack, but adding "I have reported all the bugs I found to the company and waited for approval." A screenshot in the video showed a bug filed on 19 July - the same day the site was taken down - saying "Data leaks user information. I think you should fix it as soon as possible."
The video appears to show developer names and IDs. However, a number of the emails belong to long-deprecated services, including Demon, Freeserve and Mindspring. The Guardian is trying to contact the alleged owners of the emails.
Balic told the Guardian: "My intention was not attacking. In total I found 13 bugs and reported [them] directly one by one to Apple straight away. Just after my reporting [the] dev center got closed. I have not heard anything from them, and they announced that they got attacked. My aim was to report bugs and collect the datas [sic] for the purpose of seeing how deep I can go with it."
Apple said in an email to developers late on Sunday night that "an intruder attempted to secure personal information of our registered developers… [and] we have not been able to rule out the possibility that some developers' names, mailing addresses and/or email addresses may have been accessed."
It didn't give any indication of who carried out the attack, or what their purpose might have been. Apple said it is "completely overhauling our developer systems, updating our server software, and rebuilding our entire database [of developer information]."
Some people reported that they had received password resets against their Apple ID - used by developers to access the portal - suggesting that the hacker or hackers had managed to copy some key details and were trying to exploit them.
If they managed to successfully break into a developer's ID, they might be able to upload malicious apps to the App Store. Apple said however that the hack did not lead to access to developer code.
The breach is the first known against any of Apple's web services. It has hundreds of millions of users of its iTunes and App Store e-commerce systems. Those systems do not appear to have been affected: Apple says that they are completely separate and remained safe.
Apple's Developer portal lets developers download new versions of the Mac OS X and iOS 7 betas, set up new devices so they can run the beta software and access forums to discuss problems. A related service for developers using the same user emails and passwords, iTunes Connect, lets developers upload new versions of apps to the App Store. While developers could log into that service, they could not find or update apps and could not communicate with Apple.
But if the hack provided access to developer IDs which could then be exploited through phishing attacks, there would be a danger that apps could be compromised. Apps are uploaded to the App Store in a completed form - so hackers could not download "pieces" of an existing app - and undergo a review before being made publicly available.
High-profile companies are increasingly the target of increasingly skilful hackers. In April 2011, Sony abruptly shut down its PlayStation Network used by 77 million users and kept it offline for seven days so that it could carry out forensic security testing, after being hit by hackers - who have never been identified.
It has also become a risk of business for larger companies and small ones alike. On Saturday, the Ubuntu forums were hacked, and all of the passwords for the thousands of users stolen - although they were encrypted. On Sunday, the hacking collective Anonymous said that it hacked the Nauruan government's website.
On Sunday, the Apple Store, used to sell its physical products, was briefly unavailable - reinforcing suspicions that the company was carrying out a wide-ranging security check. The company has not commented on the reasons for the story going down.
Marco Arment, a high-profile app developer, noted on his blog before Apple confirmed the hack that " I don't know anything about [Apple's] infrastructure, but for a web service to be down this long with so little communication, most 'maintenance' or migration theories become very unlikely."
He suggested that the problem could either be "severe data loss" in which restoring from backups has failed - but added that the downtime "is pretty long even for backup-restoring troubles" - or else "a security breach, followed by cleanup and increases defenses".
Of the downtime, he said "the longer it goes, especially with no statements to the contrary, the more this [hacking hypothesis] becomes the most likely explanation."
BRADLEY MANNING ~ THIS IS YOUR LIFE PLUS 154 YEARS
Steve Bell on the Bradley Manning trial, The Guardian,
Thursday 18 July 2013 18.01 EDT, Cartoon Source
NSA warned to rein in surveillance
as agency reveals even greater scopeNSA officials testify to angry House panel that agency can perform 'three-hop queries' through Americans' data and records
Spencer Ackerman, in Washington, guardian.co.uk, Wednesday 17 July 2013 15.19 EDT, Article Source
NSA officials James Cole, Robert S Litt and John Inglis appear before House committee. Photograph: J Scott Applewhite/APThe National Security Agency revealed to an angry congressional panel on Wednesday that its analysis of phone records and online behavior goes exponentially beyond what it had previously disclosed.
John C Inglis, the deputy director of the surveillance agency, told a member of the House judiciary committee that NSA analysts can perform "a second or third hop query" through its collections of telephone data and internet records in order to find connections to terrorist organizations.
"Hops" refers to a technical term indicating connections between people. A three-hop query means that the NSA can look at data not only from a suspected terrorist, but from everyone that suspect communicated with, and then from everyone those people communicated with, and then from everyone all of those people communicated with.
Inglis did not elaborate, nor did the members of the House panel – many of whom expressed concern and even anger at the NSA – explore the legal and privacy implications of the breadth of "three-hop" analysis.
But Inglis and other intelligence and law enforcement officials testifying before the committee said that the NSA's ability to query the data follows rules set by the secret Fisa court, although about two dozen NSA officials determine for themselves when those criteria are satisified.
A document published last month by the Guardian detailing the history of the NSA's post-9/11 bulk surveillance on telephone and internet data refer to one- or two-hop analysis performed by NSA. The document, provided by ex-NSA contractor Edward Snowden, does not explicitly mention three-hop analysis, nor does it clearly suggest that such analysis occurs.
Wednesday's hearing was the second major public congressional hearing about the NSA's surveillance activities since the Guardian and the Washington Post disclosed some of them in early June. Unlike the previous hearing on June 18 before the House intelligence committee, members of the House judiciary committee aggressively questioned senior officials from the NSA, FBI, Justice Department and Office of the Director of National Intelligence.
One senior member of the panel, congressman James Sensenbrenner, the author of the 2001 Patriot Act, warned the officials that unless they rein in the scope of their surveillance on Americans' phone records, "There are not the votes in the House of Representatives" to renew the provision after its 2015 expiration.
"You're going to lose it entirely," Sensenbrenner said.
Inglis and deputy attorney general James Cole repeatedly argued that the NSA's surveillance was limited because it only searches through its databases of phone records when it has a "reasonable, articulable suspicion" of a connection to terrorism.
But several members of the committee, of both parties, said they were concerned not merely about the analysis of the phone records but about NSA's collection of millions of Americans' phone data in the first place, without an individual suspicion of connections to terrorism.
"The statute says 'collection'," congressman Jerrold Nadler told Cole. "You're trying to confuse us by talking use."
Congressman Ted Poe, a judge, said: "I hope as we move forward as a Congress we rein in the idea that it's OK to bruise the spirit of the constitution in the name of national security."
Inglis, Cole and Robert Litt, the senior legal counsel for the Office of the Director of National Intelligence, also argued that the surveillance activities were restricted by the oversight of Congress and the Fisa court. Legislators challenged both contentions.
Congressman Spencer Bachus said he "was not aware at all" of the extent of the surveillance, since the NSA programs were primarily briefed to the intelligence committees of the House and Senate.
Congresswoman Zoe Lofgren revealed that an annual report provided to Congress by the government about the phone-records collection, something cited by intelligence officials as an example of their disclosures to Congress, is "less than a single page and not more than eight sentences".
Congressman Hakeem Jeffries, challenged Litt's contention that the Fisa court was "not a rubber stamp" by way of a baseball analogy. Jeffries noted that some of the greatest hitters in baseball history – the Cardinals' Stan Musial, the Red Sox's Ted Williams, the Tigers' Ty Cobb and the Yankees' Babe Ruth – did not hit more than four balls safely per 10 times at bat, for career batting averages ranging from Musial's .331 to Cobb's .366.
He then noted that the Fisa court approves over 99% of government requests for surveillance – which would give the government a lifetime batting average of .999 – saying: "But you've taken the position that the Fisa court is an independent check."
Litt, continuing the analogy, said that when the government submits a surveillance request or "throws a pitch", the Fisa court "says 'throw a little bit higher, a little more inside'" rather than ruling it out of the strike zone.
3.3-magnitude quake reported on Cobb
Slew of court challenges threaten
NSA's relationship with tech firmsUnlikely coalition takes NSA – and the telecoms firms who own much of the web's infrastructure – to court over bulk surveillance
Spencer Ackerman, guardian.co.uk, Wednesday 17 July 2013 08.37 EDT, Article Source
The lawsuits threaten to split the financial and legal interests of the telecoms and ISPs
from those of the NSA. Photograph: OJO Images/Rex FeaturesAn avalanche of legal challenges to the National Security Agency threaten to upend one of the most delicate balances the surveillance agency labors to strike: its critical relationship with telecommunications and internet companies.
An unlikely coalition of advocacy groups are taking the NSA to court, claiming the bulk surveillance it conducts on Americans phone records and their online habits is unconstitutional. One of them is aiming beyond the NSA itself, and at the companies the NSA partners with for much of that data.
The NSA's relationship with those companies is critical, since much of the telecommunications infrastructure of the United States is owned and operated by private firms. While the lawsuits face significant obstacles, they stand a chance of splitting the financial and legal interests of the telecoms firms and and Internet Service Providers from those of the NSA – something that could restrict the surveillance efforts more than any legislation Congress is likely to pass.
"Without the companies' participation," said former NSA codebreaker William Binney, "it would reduce the collection capability of the NSA significantly."
The lawsuits, which take several different paths to blocking the bulk surveillance, are proliferating quickly.
One filed on Tuesday in a California federal court united a coalition of 19 gun owners, human-rights groups, Muslim organizations, environmentalists and marijuana legalization advocates seeking a "preliminary and permanent injunction" against NSA surveillance. Their claims about the surveillance violating their speech and privacy rights echoed another suit filed last month in a New York federal court by the ACLU challenging the programs' constitutionality.
Similarly, a suit first filed in California five years ago was resurrected last week after a judge ruled that revelations about bulk surveillance published by the Guardian and the Washington Post and confirmed by the government prevent the Justice Department from quashing the suit as a state secret. The Electronic Privacy Information Center petitioned the supreme court last week to "vacate an unlawful order" by the secretive Fisa court for mass phone records from Americans.
Those cases still face the considerable challenges of fighting and defeating what are sure to be vigorous Justice Department challenges to their viability. Thus far, the courts have most often ruled for the government in NSA surveillance suits. Unlike in the past, however, the NSA documents published by the Guardian and the Post revealed for the first time that telecoms and Internet Service Providers were directly providing NSA with bulk customer information, allowing those customers – including the ACLU, a Verizon customer – standing to sue.
But even if all those cases fail, there's another legal avenue to contest the surveillance, albeit a difficult one: lawsuits against the companies themselves.
That's what the conservative group Judicial Watch is attempting. The organization filed a class-action suit last month against the internet companies named as participating in the NSA's Prism program, including Microsoft, AOL, Facebook, Google and Apple. Cases like that have long frightened the NSA.
The NSA and its allies in Congress have gone to great lengths to legally shield the private-sector telephone and internet companies it works with. A 2008 law that broadened the scope of the Foreign Intelligence Surveillance Act, known as the Fisa Amendments Act, retroactively immunized any participating telecom firm from legal liability. According to an internal NSA history of the program, several firms specifically requested NSA compel them to comply through Fisa court orders, fearing an eventual court case.
Underscoring how delicately the NSA treats the sanctity of its private-sector partners, the NSA would only refer to them even in a classified internal document as "Company A" and similar pseudonyms.
That sensitivity exists because the telecommunications firms largely own and operate the infrastructure used to make phone calls, send emails and conduct web searches, unlike in authoritarian countries like China, North Korea and the former East Germany. Without the companies' participation, the NSA could still perform so-called "upstream" collection, such as accessing data as it transmits, for instance, across fiberoptic cables before the companies process them. "But they can't get a complete copy of everything without going to the companies," Binney said.
Lawsuits against the companies place tensions, both legal and financial, on their partnership with NSA. Even the threat of spending money in court to quash customer lawsuits carries the potential for the companies to reassess the scope of their longstanding relationships with the surveillance agency.
The lawsuits are a more direct challenge to the NSA than the convoluted and uncertain legislative or political processes. While several senators and members of Congress are talking about revising the Patriot Act to restrict bulk telephone records collection, support in Congress for the NSA runs deep, and it is difficult to forecast what reforms, if any, might pass. Similarly, the secret Fisa Court bristles at accusations that it's a rubber stamp, but it approves almost all surveillance requests.
That leaves citizens upset with the surveillance to pursue their rights as customers of the companies participating with the NSA.
"If you want to raise costs to the companies participating with NSA, you raise the time and effort they spend defending themselves from allegations that their participation in NSA surveillance programs is unlawful," said Amie Stepanovich, a lawyer with the Electronic Privacy Information Center. "But the downfall of suing the companies are the companies' inevitable filings that they were just complying with the law."
Yet the obstacles to suing the companies are significant. The 2008 law explicitly says: "No cause of action shall lie in any court against any electronic communication service provider for providing any information, facilities, or assistance."
Alex Abdo, a lawyer with the ACLU working on the civil liberties group's challenge to the NSA, said the immunization provisions are not necessarily insurmountable for suing the companies.
"You could still sue Verizon and ask them to stop, even if you're not asking for damages," Abdo said. "I don't think the immunity provision applies to that."
Even as the scope of the companies' liability is set to be litigated, some of the NSA's partners are attempting to limit their customers' discontent. On Tuesday, Microsoft publicly asked Attorney General Eric Holder to lift the veil of secrecy over its cooperation with NSA so it can "publish the volume of national security requests we have received." That followed a Monday ruling by the Fisa court for the Justice Department to release information showing Yahoo at times resisted cooperation even when compelled by the court.
Time for a corporate death penalty?
Millions of US license plates tracked and stored,
new ACLU report findsAlarming number of databases across US are storing details of Americans' locations – not just government agencies
Ed Pilkington, in New York, guardian.co.uk, Wednesday 17 July 2013 10.07 EDT, Article Source
'License plate readers are the most pervasive method of location tracking
that nobody has heard of.' Photograph: Robert Landau/CorbisMillions of Americans are having their movements tracked through automated scanning of their car license plates, with the records held often indefinitely in vast government and private databases.
A new report from the American Civil Liberties Union has found an alarming proliferation of databases across the US storing details of Americans' locations. The technology is not confined to government agencies – private companies are also getting in on the act, with one firm National Vehicle Location Service holding more than 800m records of scanned license plates.
"License plate readers are the most pervasive method of location tracking that nobody has heard of," said Catherine Crump, ACLU lawyer and lead author of the report. "They collect data on millions of Americans, the overwhelming number of whom are entirely innocent of any wrongdoing."
Crump said that the creeping growth of license plate scanners echoed the debate over the National Security Agency. "It raises the same question as the NSA controversy: do we want to live in a world where the government makes a record of everything we do – because that's what's being created by the growth of databases linked to license plate readers."
ACLU based their research on the results of freedom of information requests to 300 police departments and other agencies nationwide that generated 26,000 pages of documents. The mountain of training materials, internal memos and policy statements retrieved by the group has opened a door on a previously little understood world.
Crump said that it's impossible to put a figure on the scale of the license plate scanning phenomenon as information still remains patchy. But what is clear is that by using scanners mounted on police patrol cars, on road signs and bridges and outside public buildings such as libraries and schools, databases are now storing millions of data points.
Typically, the systems collect photographs, license plate numbers, as well as the date, time and location where the vehicle was seen. What is of concern to ACLU is the fact that the information gathering is indiscriminate – it sucks in the details of all passing cars – and that the data is stored with minimal safeguards and often for long periods or even forever.
"Even if license plate reader data is not being misused already, we should all be concerned about it lingering in government databases for years as we never know how it will be used in future," Crump said.
The purpose of vehicle scanning is to provide law enforcers with an extra tool in their search for criminals or stolen cars. Scanned data is checked against "hot lists" of stolen vehicles, felony warrants, offenders on probation and sex offenders, and when matches are achieved the authorities are alerted to the "hits".
But ACLU's analysis of the information it gathered on the scanning systems found that only a minuscule proportion of recorded license plates were related to any criminal or other law enforcement issue. In Maryland, some 29m license plates were recorded in 2012, but of those only 0.2% were "hits" associated with crimes or other wrongdoings; and of that 0.2%, about 97% were for a traffic misdemeanour or a violation of the state's vehicle emissions rules. To express that another way, out of every 1m license plates read in Maryland, only 47 were linked to more serious crime such as a wanted suspect or terrorist organisation.
That would not matter so much were there proper controls in place for how to store the data and for how long. But ACLU found that only five states have introduced laws to govern these scanning devices, while at a local level standards vary enormously across the country.
Some authorities such as Minnesota State Patrol delete all their scanned records after 48 hours. Others are much looser in their regulations, such as the town of Milpitas in California, population 67,000, which stores almost 5m plate reads with no time limits at all.
Many police authorities have few or no regulations over use of the scanners other than that they should not be deployed to track people of personal interest such as spouses or friends. Pittsburg police department in California stated on the documents submitted to ACLU that the scanners can be used for "any routine patrol operation or criminal investigation – reasonable suspicion or probably cause is not required". The police department in Scarsdale New York was glowing about the potential of the technology, saying the scanners had potential that "is only limited by the officer's imagination".
In New York city, the NYPD used license plate readers as part of their controversial monitoring of mosques in the wake of 9/11, according to an investigation by Associated Press.
Mike Katz-Lacabe from San Leandro, California, became curious about the use of license plate scanners after he heard that his town's police department was investing in a system. In 2010 he submitted requests for information on the data stored on him and was astonished that over a two-year period some 112 images had been gathered and held on him, including pictures of his two cars in front of his house, friends' houses, the local library and so on.
One captured image showed Katz-Lacabe and his daughters getting out of the car. "I was amazed by how much information they had gathered on me over a short period of time."
The police force has recently introduce a one-year limit on storing the data, but he thinks that's still too long. "People should be concerned about this for so many reasons: maybe they visit an abortion clinic, or have sensitive medical treatment, or attend a political demonstration – all those movements can be gleaned from this kind of data," he said.
Anonymous claims hack of US's Fema
in retaliation for 'implied threats'Hacking collective posts contact information for agency employees but unconfirmed if servers have been compromised
Amanda Holpuch in New York, guardian.co.uk, Wednesday 17 July 2013 17.26 EDT, Article Source
President Obama at Fema headquarters to talk about the cleanup efforts
in the wake of Superstorm Sandy. Photograph: Martin H Simon/EPAThe Anonymous hacking collective claims it has compromised US Federal Emergency Management Agency (Fema) servers and has posted the contact information of people connected to the agency online.
Anonymous said it released the information because recent events, including the NSA surveillance revelations, have brought "oblique and cowardly implied threats against Anonymous very much back into the forefront of the hive's consciousness".
The release includes the names, mailing addresses and email addresses of contractors, subcontractors and government employees linked to Fema, including private defense contractors, federal agents and local authorities.
Much of the information was already accessible online to someone determined to find it, though Anonymous said it redacted social security numbers and login information because its "intent is not to harm, merely to issue a firm warning".However, the mailing addresses connected to some of the people listed on the release are not publicly affiliated with their employers and Anonymous referred to them as home addresses in an email. It did respond to a question asking why this does not fall under the banner of harmful information.
Anonymous said it targeted Fema because of a training exercise the agency used in 2012 to prepare employees for a cyberattack. In the scenario, a fictional group called "The Void" launches a cyberattack on US businesses and infrastructure.
Anonymous sees The Void as a stand-in for their organization and feels that the training exercise made some unfair implications about the collective. It said actions taken by The Void "implicitly link financial gain and fraud to activist hackers". Anonymous was also upset because it believes the exercise implies the collective is anti-American.
Fema did not respond to requests for confirmation on whether its servers were compromised.
The Fema exercise occurred in 2012, but Anonymous said in a statement that it believes the exercise was used "as part of the ongoing justifications for Prism and the other NSA spy programs". With these recent developments, Anonymous said it wanted to show it "does not wave the white flag".
We are not fighting any one government or corporation, we are fighting any enemy of freedom of speech and anyone compromising the right to remain anonymous online, without fear of reprisals from governments or corporations with the legal authority or financial resources to destroy the lives of anyone who dares express opinions contrary to their own official line.
Anonymous seemed to imply a threat of its own at the end of the release and said: "Also, please return to us Barrett Brown, we are asking nicely. Pretty please, with sugar on top."
Brown has been imprisoned since September after being accused of 17 offenses springing from his affiliation with Anonymous. Brown is not a hacker but had close ties to the collective and helped publicize some of their most renowned hacks including the Stratfor hack in 2011.
The Fema exercise was co-ordinated by homeland security consulting company Obsidian Analysis, who appointed former Fema chief of staff John McNamara to be company vice-president in May. The National Level Exercise: Cybertop Capabilities Tabletop Exercise, can be downloaded from the Fema site here.
Fuse Exclusive: Watch Woman Attack
Lester Chambers Over Trayvon Martin TributeFuse News captured footage of the onstage assault and spoke with the soul legend afterwards
Fuse Staff, July 15, 2013, Article Source, via Phoenix
Saturday night, just before a Florida jury acquitted George Zimmerman in the shooting death of 17-year-old Trayvon Martin, Lester Chambers, a member of soul-rock vets the Chambers Brothers, was attacked onstage for dedicating a song to Martin. Fuse News had cameras on the scene and captured exclusive footage of the attack--watch above.
Chambers, 73, was performing at the Hayward Russell City Blues Festival in Hayward, California, when a 43-year-old woman, identified by police as Dinalynn Andrews Potter, jumped onstage and knocked Chambers down. Chambers' wife, Lola, told the Mercury News that the singer had just dedicated Curtis Mayfield and the Impressions' "People Get Ready" to Martin, saying that if Mayfield were alive today, he'd change the lyrics from "there's a train a comin'" to "there's a change a comin'."
Andrews Potter was wrestled to the ground and subdued by stage hands, and Chambers was wheeled away to an ambulance. As the video shows, he was still in good spirits, even flashing a peace sign. Chambers was treated at the hospital and released. A photo posted to Facebook by his son, Dylan, shows Chambers' injuries: a "bruised rib muscle and nerve damage and he is sore all over," wrote Dylan.
Andrews Potter, meanwhile, was arrested on suspicion of battery, cited and released. According to Billboard, Chambers' family is pushing authorities to file hate crime charges.
Fuse spoke with Chambers following the incident. "I was asking for peace," he explains. "She got in my face and called me all kinds of MFs, saying that I started all this."
After the attack Chambers was "totally out of it," he says. "I've never been so shocked and traumatized." Watch the full interview below.
Trayvon Martin,
one more among so many black men killed in my lifetimeI feel the grief of all people who love fairness and justice. But George Zimmerman has his own conscience to reckon with
Alice Walker, The Guardian, Monday 15 July 2013, Article Source
A memorial to Trayvon Martin outside The Retreat at Twin Lakes in Sanford, Florida, in 2012.
Photograph: Roberto Gonzalez/Getty ImagesI deliberately watched none of the Zimmerman trial, just as I have deliberately not read a draft of a new book by Jen Marlowe and others, soon to be published: I Am Troy Davis, about a young black man in Georgia who was, by all indications, innocent of any crime – but was put to death recently by the state. News of these deaths, of Troy, of Trayvon, is so painful that I protect myself in this way.
So many killings of black men in my lifetime. The physical shock is astounding.
I write this, remembering that when Martin Luther King Jr was assassinated in 1968, the shock to my system was so severe I lost the child I was carrying. This shock, this assault on the psyche and body, is what is intended.
That, too, is painful, though we may feel glad not to be, ourselves, so cruel and sadistic. I feel the grief of all people who love fairness and justice coursing through my body, deep into my soul. We are united in our suffering. Being aware of this helps.
Contemplating Zimmerman's exoneration for the shooting death of Trayvon Martin in a letter to a friend yesterday, I wrote this, with a few thoughts added today:
Just heard the Zimmerman verdict. It makes me think of the man given the "pleasure" of assassinating Che Guevara. He was young, and it was his birthday. He was strutting and proud to be offered this "work", as Che stood bleeding, weakened and alone, before him.
Fast forward to recently, when the assassin became old and ill and needed surgery – and Cuban doctors (who loved Che Guevara) did their best to heal him.
The ache of realization, of what he has done, when it comes for Zimmerman, will be all the punishment he will ever deserve. I remember now, with understanding, that our parents used to say, about things they regretted they had done and that they got away with: "I'd rather take a whipping …"
Zimmerman will wish many times in his life that they had given him 100 years.
Trayvon Martin was an honor student with a 3.7 GPA, received a full college scholarship, volunteered for 600 service hours, a devoted member of his church, a loyal friend, a loving son, and an INNOCENT boy.
3.4~magnitude quake reported on Cobb
Coup d’etat
by Paul Craig Roberts, Article Source
The American people have suffered a coup d’etat, but they are hesitant to acknowledge it. The regime ruling in Washington today lacks constitutional and legal legitimacy. Americans are ruled by usurpers who claim that the executive branch is above the law and that the US Constitution is a mere “scrap of paper.”
An unconstitutional government is an illegitimate government. The oath of allegiance requires defense of the Constitution “against all enemies, foreign and domestic.” As the Founding Fathers made clear, the main enemy of the Constitution is the government itself. Power does not like to be bound and tied down and constantly works to free itself from constraints.
The basis of the regime in Washington is nothing but usurped power. The Obama Regime, like the Bush/Cheney Regime, has no legitimacy. Americans are oppressed by an illegitimate government ruling, not by law and the Constitution, but by lies and naked force. Those in government see the US Constitution as a “chain that binds our hands.”
The South African apartheid regime was more legitimate than the regime in Washington. The apartheid Israeli regime in Palestine is more legitimate. The Taliban are more legitimate. Muammar Gaddafi and Saddam Hussein were more legitimate.
The only constitutional protection that the Bush/Obama regime has left standing is the Second Amendment, a meaningless amendment considering the disparity in arms between Washington and what is permitted to the citizenry. No citizen standing with a rifle can protect himself and his family from one of the Department of Homeland Security’s 2,700 tanks, or from a drone, or from a heavily armed SWAT force in body armor.
Like serfs in the dark ages, American citizens can be picked up on the authority of some unknown person in the executive branch and thrown in a dungeon, subject to torture, without any evidence ever being presented to a court or any information to the person’s relatives of his/her whereabouts. Or they can be placed on a list without explanation that curtails their right to travel by air. Every communication of every American, except face-to-face conversation in non-bugged environments, is intercepted and recorded by the National Stasi Agency from which phrases can be strung together to produce a “domestic extremist.”
If throwing an American citizen in a dungeon is too much trouble, the citizen can simply be blown up with a hellfire missile launched from a drone. No explanation is necessary. For the Obama tyrant, the exterminated human being was just a name on a list.
The president of the united states has declared that he possesses these constitutionally forbidden rights, and his regime has used them to oppress and murder US citizens. The president’s claim that his will is higher than law and the Constitution is public knowledge. Yet, there is no demand for the usurper’s impeachment. Congress is supine. The serfs are obedient.
The people who helped transform a democratically accountable president into a Caesar include John Yoo, who was rewarded for his treason by being accepted as a law professor at the University of California, Berkeley, Boalt school of law. Yoo’s colleague in treason, Jay Scott Bybee was rewarded by being appointed a federal judge on the US Court of Appeals for the Ninth Circuit. We now have a Berkeley law professor teaching, and a federal circuit judge ruling, that the executive branch is above the law.
The executive branch coup against America has succeeded. The question is: will it stand? Today, the executive branch consists of liars, criminals, and traitors. The evil on earth seems concentrated in Washington.
Washington’s response to Edward Snowden’s evidence that Washington, in total contravention of law both domestic and international, is spying on the entire world has demonstrated to every country that Washington places the pleasure of revenge above law and human rights.
On Washington’s orders, its European puppet states refused overflight permission to the Bolivian presidential airliner carrying President Morales and forced the airliner to land in Austria and be searched. Washington thought that Edward Snowden might be aboard the airliner. Capturing Snowden was more important to Washington than respect for international law and diplomatic immunity.
How long before Washington orders its UK puppet to send in a SWAT team to drag Julian Assange from the Ecuadoran embassy in London and hand him over to the CIA for waterboarding?
On July 12 Snowden met in the Moscow airport with human rights organizations from around the world. He stated that the illegal exercise of power by Washington prevents him from traveling to any of the three Latin American countries who have offered him asylum. Therefore, Snowden said that he accepted Russian President Putin’s conditions and requested asylum in Russia.
Insouciant americans and the young unaware of the past don’t know what this means. During my professional life it was Soviet Russia that persecuted truth tellers, while America gave them asylum and tried to protect them. Today it is Washington that persecutes those who speak the truth, and it is Russia that protects them.
The American public has not, this time, fallen for Washington’s lie that Snowden is a traitor. The polls show that a majority of Americans see Snowden as a whistleblower.
It is not the US that is damaged by Snowden’s revelations. It is the criminal elements in the US government that have pulled off a coup against democracy, the Constitution, and the American people who are damaged. It is the criminals who have seized power, not the American people, who are demanding Snowden’s scalp.
The Obama Regime, like the Bush/Cheney Regime, has no legitimacy. Americans are oppressed by an illegitimate government ruling, not by law and the Constitution, but by lies and naked force.
Under the Obama tyranny, it is not merely Snowden who is targeted for extermination, but every truth-telling American in the country. It was Department of Homeland Security boss Janet Napolitano, recently rewarded for her service to tyranny by being appointed Chancellor of the of the University of California system, who said that Homeland Security had shifted its focus from Muslim terrorists to “domestic extremists,” an elastic and undefined term that easily includes truth-tellers like Bradley Manning and Edward Snowden who embarrass the government by revealing its crimes. The criminals who have seized illegitimate power in Washington cannot survive unless truth can be suppressed or redefined as treason.
If Americans acquiesce to the coup d’etat, they will have placed themselves firmly in the grip of tyranny.
Computer Tech Corporations On:
Selling Out Their Cash Paying USERS...
How One Bad Apple Can Spoil the Whole Bunch?
Maybe It's Time For A Corporate Death Penalty ???
How Microsoft handed the NSA
access to encrypted messages
[Down in the meadow where the green grass grows, there stood Microsoft without any clothes. Along came NSA swinging a chain, pulled down their zipper and out it came. 3 months later, all was well. 6 months later Microsoft began to swell. 9 months later out comes little NSA swinging a chain.]
• Secret files show scale of Silicon Valley co-operation on Prism
• Outlook.com encryption unlocked even before official launch
• Skype worked to enable Prism collection of video calls
• Company says it is legally compelled to comply
Glenn Greenwald, Ewen MacAskill, Laura Poitras, Spencer Ackerman and Dominic Rushe
The Guardian, Thursday 11 July 2013, Article Source
Skype worked with intelligence agencies last year to allow Prism to
collect video and audio conversations. Photograph: Patrick Sinkel/APMicrosoft has collaborated closely with US intelligence services to allow users' communications to be intercepted, including helping the National Security Agency to circumvent the company's own encryption, according to top-secret documents obtained by the Guardian.
The files provided by Edward Snowden illustrate the scale of co-operation between Silicon Valley and the intelligence agencies over the last three years. They also shed new light on the workings of the top-secret Prism program, which was disclosed by the Guardian and the Washington Post last month.
The documents show that:
• Microsoft helped the NSA to circumvent its encryption to address concerns that the agency would be unable to intercept web chats on the new Outlook.com portal;
• The agency already had pre-encryption stage access to email on Outlook.com, including Hotmail;
• The company worked with the FBI this year to allow the NSA easier access via Prism to its cloud storage service SkyDrive, which now has more than 250 million users worldwide;
• Microsoft also worked with the FBI's Data Intercept Unit to "understand" potential issues with a feature in Outlook.com that allows users to create email aliases;
• In July last year, nine months after Microsoft bought Skype, the NSA boasted that a new capability had tripled the amount of Skype video calls being collected through Prism;
• Material collected through Prism is routinely shared with the FBI and CIA, with one NSA document describing the program as a "team sport".
The latest NSA revelations further expose the tensions between Silicon Valley and the Obama administration. All the major tech firms are lobbying the government to allow them to disclose more fully the extent and nature of their co-operation with the NSA to meet their customers' privacy concerns. Privately, tech executives are at pains to distance themselves from claims of collaboration and teamwork given by the NSA documents, and insist the process is driven by legal compulsion.
In a statement, Microsoft said: "When we upgrade or update products we aren't absolved from the need to comply with existing or future lawful demands." The company reiterated its argument that it provides customer data "only in response to government demands and we only ever comply with orders for requests about specific accounts or identifiers".
In June, the Guardian revealed that the NSA claimed to have "direct access" through the Prism program to the systems of many major internet companies, including Microsoft, Skype, Apple, Google, Facebook and Yahoo.
Blanket orders from the secret surveillance court allow these communications to be collected without an individual warrant if the NSA operative has a 51% belief that the target is not a US citizen and is not on US soil at the time. Targeting US citizens does require an individual warrant, but the NSA is able to collect Americans' communications without a warrant if the target is a foreign national located overseas.
Since Prism's existence became public, Microsoft and the other companies listed on the NSA documents as providers have denied all knowledge of the program and insisted that the intelligence agencies do not have back doors into their systems.
Microsoft's latest marketing campaign, launched in April, emphasizes its commitment to privacy with the slogan: "Your privacy is our priority."
Similarly, Skype's privacy policy states: "Skype is committed to respecting your privacy and the confidentiality of your personal data, traffic data and communications content."
But internal NSA newsletters, marked top secret, suggest the co-operation between the intelligence community and the companies is deep and ongoing.
The latest documents come from the NSA's Special Source Operations (SSO) division, described by Snowden as the "crown jewel" of the agency. It is responsible for all programs aimed at US communications systems through corporate partnerships such as Prism.
The files show that the NSA became concerned about the interception of encrypted chats on Microsoft's Outlook.com portal from the moment the company began testing the service in July last year.
Within five months, the documents explain, Microsoft and the FBI had come up with a solution that allowed the NSA to circumvent encryption on Outlook.com chats
A newsletter entry dated 26 December 2012 states: "MS [Microsoft], working with the FBI, developed a surveillance capability to deal" with the issue. "These solutions were successfully tested and went live 12 Dec 2012."
Two months later, in February this year, Microsoft officially launched the Outlook.com portal.
Another newsletter entry stated that NSA already had pre-encryption access to Outlook email. "For Prism collection against Hotmail, Live, and Outlook.com emails will be unaffected because Prism collects this data prior to encryption."
Microsoft's co-operation was not limited to Outlook.com. An entry dated 8 April 2013 describes how the company worked "for many months" with the FBI – which acts as the liaison between the intelligence agencies and Silicon Valley on Prism – to allow Prism access without separate authorization to its cloud storage service SkyDrive.
The document describes how this access "means that analysts will no longer have to make a special request to SSO for this – a process step that many analysts may not have known about".
The NSA explained that "this new capability will result in a much more complete and timely collection response". It continued: "This success is the result of the FBI working for many months with Microsoft to get this tasking and collection solution established."
A separate entry identified another area for collaboration. "The FBI Data Intercept Technology Unit (DITU) team is working with Microsoft to understand an additional feature in Outlook.com which allows users to create email aliases, which may affect our tasking processes."
The NSA has devoted substantial efforts in the last two years to work with Microsoft to ensure increased access to Skype, which has an estimated 663 million global users.
One document boasts that Prism monitoring of Skype video production has roughly tripled since a new capability was added on 14 July 2012. "The audio portions of these sessions have been processed correctly all along, but without the accompanying video. Now, analysts will have the complete 'picture'," it says.
Eight months before being bought by Microsoft, Skype joined the Prism program in February 2011.
According to the NSA documents, work had begun on smoothly integrating Skype into Prism in November 2010, but it was not until 4 February 2011 that the company was served with a directive to comply signed by the attorney general.
The NSA was able to start tasking Skype communications the following day, and collection began on 6 February. "Feedback indicated that a collected Skype call was very clear and the metadata looked complete," the document stated, praising the co-operation between NSA teams and the FBI. "Collaborative teamwork was the key to the successful addition of another provider to the Prism system."
ACLU technology expert Chris Soghoian said the revelations would surprise many Skype users. "In the past, Skype made affirmative promises to users about their inability to perform wiretaps," he said. "It's hard to square Microsoft's secret collaboration with the NSA with its high-profile efforts to compete on privacy with Google."
The information the NSA collects from Prism is routinely shared with both the FBI and CIA. A 3 August 2012 newsletter describes how the NSA has recently expanded sharing with the other two agencies.
The NSA, the entry reveals, has even automated the sharing of aspects of Prism, using software that "enables our partners to see which selectors [search terms] the National Security Agency has tasked to Prism".
The document continues: "The FBI and CIA then can request a copy of Prism collection of any selector…" As a result, the author notes: "these two activities underscore the point that Prism is a team sport!"
In its statement to the Guardian, Microsoft said:
We have clear principles which guide the response across our entire company to government demands for customer information for both law enforcement and national security issues. First, we take our commitments to our customers and to compliance with applicable law very seriously, so we provide customer data only in response to legal processes.
Second, our compliance team examines all demands very closely, and we reject them if we believe they aren't valid. Third, we only ever comply with orders about specific accounts or identifiers, and we would not respond to the kind of blanket orders discussed in the press over the past few weeks, as the volumes documented in our most recent disclosure clearly illustrate.
Finally when we upgrade or update products legal obligations may in some circumstances require that we maintain the ability to provide information in response to a law enforcement or national security request. There are aspects of this debate that we wish we were able to discuss more freely. That's why we've argued for additional transparency that would help everyone understand and debate these important issues.
In a joint statement, Shawn Turner, spokesman for the director of National Intelligence, and Judith Emmel, spokeswoman for the NSA, said:
The articles describe court-ordered surveillance – and a US company's efforts to comply with these legally mandated requirements. The US operates its programs under a strict oversight regime, with careful monitoring by the courts, Congress and the Director of National Intelligence. Not all countries have equivalent oversight requirements to protect civil liberties and privacy.
They added: "In practice, US companies put energy, focus and commitment into consistently protecting the privacy of their customers around the world, while meeting their obligations under the laws of the US and other countries in which they operate."
–
• This article was amended on 11 July 2013 to reflect information from Microsoft that it did not make any changes to Skype to allow Prism collection on or around July 2012.
[ Above makes one wonder how far APPLE and other turncoat corporations bent over to sell out their users?]
Once Upon A Time...
April 11, 1989
The following was posted to a Usenet Group on Tuesday 11 April 1989:
RISKS-LIST: RISKS-FORUM Digest Tuesday 11 April 1989 Volume 8 : Issue 54
FORUM ON RISKS TO THE PUBLIC IN COMPUTERS AND RELATED SYSTEMS ACM Committee on Computers and Public Policy, Peter G. Neumann, moderator
Date: Tue, 11 Apr 89 08:12:04 PDT
From: cas@toad.com (Curtis Spangler)
Subject: NSA and Not Secure AgenciesSan Francisco Chronicle, Chronicle Wire Services, April 11, 1989:
Computer Group Wary of Security Agency
A public interest group said yesterday that the National Security Agency, the nation's biggest intelligence agency, could exert excessive control over a program to strengthen the security of computer systems throughout the federal government.
The group, Computer Professionals for Social Responsibility - based in Palo Alto - urged key members of Congress to focus "particularly close scrutiny" on the agency's role in helping to implement legislation aimed at safeguarding sensitive but unclassified information in federal computers.
"There is a constant risk that the federal agencies, under the guise of enhancing computer security, may find their programs - to the extent that they rely upon computer systems - increasingly under the supervision of the largest and most secretive intelligence organization in the country," it said.
December 22, 2000
Security-Enhanced Linux (SELinux) is a GNU/Linux feature that provides the mechanism for supporting access control security policies, including United States Department of Defense-style mandatory access controls, through the use of GNU/Linux Security Modules (LSM) in the GNU/Linux kernel. It is not a GNU/Linux distribution, but rather a set of kernel modifications and user-space tools that can be added to various GNU/Linux distributions. Its architecture strives to separate enforcement of security decisions from the security policy itself and streamlines the volume of software charged with security policy enforcement. The key concepts underlying SELinux can be traced to several earlier projects by the United States National Security Agency. It has been integrated into the mainline GNU/Linux kernel since version 2.6, on 8 August 2003.
From: http://www.nsa.gov/research/selinux/background.shtml:
SELinux Background ~ Researchers in the National Information Assurance Research Laboratory of the National Security Agency (NSA) worked with Secure Computing Corporation (SCC) to develop a strong, flexible mandatory access control architecture based on Type Enforcement, a mechanism first developed for the LOCK system. The NSA and SCC developed two Mach-based prototypes of the architecture: DTMach and DTOS. The NSA and SCC then worked with the University of Utah's Flux research group to transfer the architecture to the Fluke research operating system. During this transfer, the architecture was enhanced to provide better support for dynamic security policies. This enhanced architecture was named Flask. The NSA integrated the Flask architecture into the GNU/Linux® operating system to transfer the technology to a larger developer and user community. The architecture has been subsequently mainstreamed into GNU/Linux® and ported to several other systems, including the Solaris™ (Sun Microsystems/Oracle) operating system, the freeBSD® operating system, and the Darwin (Apple) kernel, spawning a wide range of related work.
Images Via Wikipedia, the free encyclopediaTime For A Corporate Death Penalty?
US government assessment of BP oil spill
'will not account for damage'Efforts to put a price on damage from disaster fails to capture full extent of environmental losses in Gulf waters
Suzanne Goldenberg, US environment correspondent, guardian.co.uk, 11 July 2013 08.17 EDT, Article Source
A Kemp's Ridley turtle rescued from the BP oil spill is cleaned up at the Audubon Nature Institute
in New Orleans. Photograph: Bevil Knapp/EPAThe US government cannot hope to arrive at a full accounting of the environmental destruction caused by the BP oil disaster in the Gulf of Mexico using its current methods, an expert panel has said.
A report from the National Research Council said the US government's efforts to put a price on damage from the April 2010 disaster failed to capture the full extent of the environmental and economic losses in Gulf waters and coastal areas, fisheries, marine life, and the deep sea caused by BP's runaway well.
Compiled by a team of 16 scientists at the request of Congress, the study went on to call for a sweeping overhaul of methods for putting a price on environmental losses – especially after an event on the scale of the BP disaster.
"The full value of losses resulting from the spill cannot be captured … without consideration of changes in ecosystem services – the benefits delivered to society through natural processes," the report said.
The experts involved in drafting the report said on Wednesday they believed their findings could still influence the settlement of environmental claims against BP brought by the federal government and five state governments.
But they conceded the report would probably carry greater weight in guiding future efforts to account for environmental damage.
It digs into one of the great debates arising from the BP disaster: how to put a price on oiled coastlines, and marine animals, and how to hold the company accountable for restoration.
The researchers noted that 20 million people in the US alone lived and worked around the Gulf of Mexico. Before the April 2010 disaster, the Gulf accounted for about a quarter of the country's seafood catch. It also provided about 30% of America's oil and nearly 20% of natural gas. Meanwhile, coastal wetlands provided protection against storm surges.
But the report noted: "Disruptions in the ecosystem caused by the oil spill could impair these services, leading to economic and social impacts that may not be apparent from an assessment of environmental damage alone."
The April 2010 explosion killed 11 workers aboard the oil rig, and spewed more than 4m barrels of oil into the Gulf, according to the US government's estimate. It was the worst offshore oil spill in US history.
BP says it has spent $25bn so far in clean-up and restoration costs. It owes the government an additional $4.5bn in fines. The company is also on the hook for an $8bn settlement of economic claims – a figure which is uncapped and growing.
BP could be facing even more expensive litigation in the autumn, involving fines of up to $17.5bn under the Clean Water Act.
Billions more hinge on the outcome of a trial involving claims by the federal government and five Gulf states for restoring damage to natural resources. Government scientists are now engaged in a closely guarded exercise of trying to get a full accounting of the damage done to the Gulf, and the cost of restoring oiled coastlines and waters, and protecting populations of marine wildlife, such as dolphins, which have suffered die-offs since the disaster.
However, the report said it was not possible to capture the full extent of that damage with current accounting methods, which focus on tallying up the restoration costs for individual resources rather than the ecosystem in its entirety.
Researchers have been trying since the BP spill to come up with a method that could account for the full magnitude of the disaster in the Gulf of Mexico.
The recommendations of the expert committee for an ecosystems-based approach were welcomed by Donald Boesch, president of the University of Maryland's Centre for Environmental Science, who was a member of the White House commission on the BP oil spill.
"If you get stuck in the game of paying out 25 cents a crab for example, you are not really in a situation where you are understanding the broader impacts of the loss of that population," he said.
Boesch also said that putting a valuation on the environment of the Gulf might also help prevent misuse of funds. A report last month from the Inspector General's office in the Department of Interior found the state of Mississippi had mis-spent some $30m that had been designated for coastal restoration projects since 2007.
However, David Pettit, a senior attorney for the Natural Resources Defence Council, argued the approach devalued the environment. "It's more human economy centred, and less centred in the idea that wild things and wild places have an inherent value – whether or not they make somebodies' cash register ring," he said.
Notes from ~@~
Hubble telescope discovers alien 'deep blue' planet
The ageing space telescope has been used to identify the true colour of a planet beyond our solar system for the first time
Ian Sample, science correspondent, The Guardian, Thursday 11 July 2013, Article Source
An artist's impression of the blue planet, which is a gas giant. The same technique
could be used to identify habitable worlds. Image: NasaThe heavens are home to an alien world that shines a deep cobalt blue in a solar system far, far away from our own.
Astronomers used the ageing Hubble space telescope to determine the true colour of the distant world, the first time such a feat has been achieved for a planet that circles a star other than the sun.
Unlike the pale blue dot that harbours all known life in the cosmos, the "deep blue dot" is an inhospitable gas giant that lies 63 light years from Earth. On HD189733b, as the planet is named, the temperature soars to 1,000C and glassy hail whips through the air on hypersonic winds.
Though the planet is hostile to life as we know it, the same technique could be used to spot potentially habitable worlds, through changes in cloud cover and other features.
Frederic Pont at Exeter University observed the planet before, during, and after it passed behind its star. When the planet was on either side, the telescope collected light from the star along with light reflected from the planet's surface. But as the planet moved behind the star, the light it reflected was blocked out.
Using an instrument onboard the telescope called an imaging spectrograph, Pont noticed that blue light dimmed sharply as the planet passed behind its star, but brightened again when it emerged on the other side. "As far as I am aware, nobody has had actual results on the colour of an exoplanet," Pont said. "Now we can say that this planet is blue."
The deep cobalt colouration is thought to come from a similar process to that which makes Earth look blue from space, namely the scattering of blue light in the atmosphere. On the planet Pont observed, the scattering is probably due to a fine mist of silicate particles that are blown around by 7,000kph winds.
With more advanced technology, the colour of a planet could help astronomers work out which ones might be habitable. Most planets in our solar system are either entirely covered by cloud, or have no clouds at all. Earth is unusual in that roughly half of its surface is obscured by cloud, a product of the water cycle that is essential for life.
"If you could see the colour of an exoplanet change over time it would be very revealing. At first, the cloud cover would be the thing to go for," Pont said.
While future instruments could be sensitive enough to observe the changing hues of alien worlds, there may be no suitable telescopes in space to put them on. The Hubble observatory is more than 20 years old and was last repaired by a dedicated space shuttle mission in 2009. Without Hubble, there are no other space telescopes that could look at planets in visible wavelengths. Hubble's replacement, the James Webb Space Telescope, will pick up infra-red light only.
"Most colleagues in the field focussing on habitability concentrate on the detection of molecules in the infra-red, like water, carbon monoxide and methane," Pont said. "That's useful information of course, but my opinion is that we might be giving too much weight to this compared to visible colour, which gives a different kind of information, but maybe just as crucial to understand the general state of an Earth-like planet."
Missing BBS Files ~ Some of the first Bulletin Board Systems in the United States
DEF CON: Spot the Fed
Same Rules, Different year!
"Like a paranoid version of pin the tail on the donkey, the favorite sport at this gathering of computer hackers and phone phreaks seems to be hunting down real and imagined telephone security and Federal and local law enforcement authorities who the attendees are certain are tracking their every move... Of course, they may be right." — John Markhoff, NYT
Basically the contest goes like this: If you see some shady MIB (Men in Black) earphone penny loafer sunglass wearing Clint Eastwood to live and die in LA type lurking about, point him out. Just get my attention and claim out loud you think you have spotted a fed. The people around at the time will then (I bet) start to discuss the possibility of whether or not a real fed has been spotted. Once enough people have decided that a fed has been spotted, and the Identified Fed (I.F.) has had a say, and informal vote takes place, and if enough people think it's a true fed, or fed wanna-be, or other nefarious style character, you win a "I spotted the fed!" shirt, and the I.F. gets an "I am the fed!" shirt.
NOTE TO THE FEDS: This is all in good fun, and if you survive unmolested and undetected, but would still secretly like an "I am the fed!" shirt to wear around the office or when booting in doors, please contact me when no one is looking and I will take your order(s). Just think of all the looks of awe you'll generate at work wearing this shirt while you file away all the paperwork you'll have to produce over this convention. I won't turn in any feds who contact me, they have to be spotted by others.
DOUBLE SECRET NOTE TO FEDS: This year I am printing up extra "I am the Fed!" shirts, and will be trading them for coffee mugs, shirts or baseball hats from your favorite TLA. If you want to swap bring along some goodies and we can trade. Be stealth about it if you don't want people to spot you. Agents from foreign governments are welcome to trade too, but I gotta work on my mug collection and this is the fastest way. [Click to view current main page]
Articles from the Guardian (UK)
Worth A Click for those who want to know:
Apple played 'central role' in ebook price-fixing conspiracy, says federal judge
Tech company to face trial for damages over attempt to thwart Amazon's dominance after book publishers settle with US
Sarah Silverman's 'anal probe' tweet sparks political row
Comedian's response to US anti-abortion law no laughing matter for Republicans
Colombia asks US for explanation after reports it was targeted by NSA spying
Brazilian newspaper says documents leaked by Edward Snowden show US monitored its close ally's internet traffic
Tiny Utah-based ISP makes a name for itself by rebuffing government snoops
Meet Xmission, the internet service provider embracing transparency as it shields customers from warrantless authorities
NSA scandal delivers record numbers of internet users to DuckDuckGo

Gabriel Weinberg, founder of search engine with zero tracking, credits Prism revelations with prompting huge rise in traffic

Kipper Williams on BP, Cartoon Source, Tuesday 9 July 2013 04.00 EDT
Articles from the Guardian(UK)
Worth A Click for those who want to know:
US must fix secret Fisa courts, says top judge who granted surveillance orders
James Robertson breaks ranks and says he was shocked to hear of changes to allow broader authorisation of NSA programs
Key witness in Bradley Manning trial: Guantánamo files just 'baseball cards'
Former chief prosecutor Colonel Morris Davis says WikiLeaks detainee files contained information already available publicly
In today's corporations the buck never stops. Welcome to the age of irresponsibility
Our largest companies have become so complex that no one's expected to fully know what's going on. Yet the rewards are bigger than ever
US effort to recover remains of missing soldiers
a 'total failure' – reportInternal analysis suppressed by military shows mismanagement in pursuit of thousands still missing on former battlefields
Associated Press in Washington, guardian.co.uk, Monday 8 July 2013 11.44 EDT, Article Source
Shelia Reese's father, Chris Tench, is still missing in action from the Korean war. Photograph: Gerry Broome/APThe Pentagon's effort to account for tens of thousands of Americans missing in action from foreign wars is so inept, mismanaged and wasteful that it risks descending from "dysfunction to total failure," according to an internal study suppressed by military officials.
Largely beyond the public spotlight, the decades-old pursuit of bones and other MIA evidence is sluggish, often duplicative and subjected to too little scientific rigor, the report says.
The Associated Press obtained a copy of the internal study after Freedom of Information Act requests for it by others were denied.
The report paints a picture of a Joint POW/MIA Accounting Command, a military-run group known as JPAC and headed by a two-star general, as woefully inept and even corrupt. The command is digging up too few clues on former battlefields, relying on inaccurate databases and engaging in expensive "boondoggles" in Europe, the study concludes.
In North Korea, the JPAC was snookered into digging up remains between 1996 and 2000 that the North Koreans apparently had taken out of storage and planted in former American fighting positions, the report said. Washington paid the North Koreans hundreds of thousands of dollars to "support" these excavations.
Some recovered bones had been drilled or cut, suggesting they had been used by the North Koreans to make a lab skeleton. Some of those remains have since been identified, but their compromised condition added time and expense and "cast doubt over all of the evidence recovered" in North Korea, the study said. This practice of "salting" recovery sites was confirmed to the AP by one US participant.
JPAC's leaders authorized the study of its inner workings, but the then-commanding general, Army Maj Gen Stephen Tom, disavowed it and suppressed the findings when they were presented by the researcher last year.
Now retired, Tom banned its use "for any purpose", saying the probe went beyond its intended scope. His deputy concurred, calling it a "raw, uncensored draft containing some contentious material".
The AP obtained two internal memos describing the decision to bury the report. The memos raised no factual objections but said the command would not consider any of the report's findings or recommendations.
The failings cited by the report reflect one aspect of a broader challenge to achieving a uniquely American mission accounting for the estimated 83,348 service members still listed as missing from World War II, Korea and Vietnam.
Marine Sgt Alexander Mazza sweeps for human remains at an excavation site in South Korea in 2009.
Photograph: Jesse Shipps/US Defense DepartmentA sense of emptiness and unanswered questions haunted many families of the missing throughout the second half of the 20th century, when science and circumstance did not permit the almost exact accounting for the dead and the missing that has been achieved in Iraq and Afghanistan. While the government's efforts have provided closure for hundreds of families of the missing in recent years, many others are still waiting.
Over time, the obscure government bureaucracies in charge of the accounting task have largely managed to escape close public scrutiny despite clashing with a growing number of advocacy groups and individuals such as Frank Metersky, a Korean War veteran who has spent decades pressing for a more aggressive and effective U.S. effort.
The outlook for improvement at the Joint POW/MIA Accounting Command, he says, is not encouraging.
"Today it's worse than ever," he says.
'It's worse than dead'
People disagree on the extent of the problem. But even the current JPAC commander, Air Force Maj. Gen. Kelly K. McKeague, says he would not dispute those who say his organization is dysfunctional.
"I'd say you're right, and we're doing something about it," McKeague said in a telephone interview last week from his headquarters in Hawaii. He said changes, possibly to include consolidating the accounting bureaucracy and putting its management under the Joint Chiefs of Staff in Washington, are under consideration.
The internal report by Paul M. Cole was never meant to be made public. It is unsparing in its criticisms:
In recent years the process by which JPAC gathers bones and other material useful for identifications has "collapsed" and is now "acutely dysfunctional".
JPAC is finding too few investigative leads, resulting in too few collections of human remains to come even close to achieving Congress's demand for a minimum 200 identifications per year by 2015. Of the 80 identifications that JPAC's Central Identification Laboratory made in 2012, only 35 were derived from remains recovered by JPAC. Thirty-eight of the 80 were either handed over unilaterally by other governments or were disinterred from a US military cemetery. Seven were from a combination of those sources.
Some search teams are sent into the field, particularly in Europe, on what amount to boondoggles. No one is held to account for "a pattern of foreign travel, accommodations and activities paid for by public funds that are ultimately unnecessary, excessive, inefficient or unproductive". Some refer to this as "military tourism".
JPAC lacks a comprehensive list of the people for whom it's searching. Its main database is incomplete and "riddled with unreliable data."
"Sketch maps" used by the JPAC teams looking for remains on the battlefield are "chronically unreliable," leaving the teams "cartographically blind." Cole likened this to 19th century military field operations.
Absent prompt and significant change, "the descent from dysfunction to total failure ... is inevitable," Cole concluded.
He directed most of his criticism at the field operations that collect bones and other material, as opposed to the laboratory scientists at JPAC who use that material to identify the remains. Cole is a management consultant and recognized research expert in the field of accounting for war remains; he still works at JPAC.
More broadly, the government organizations responsible for the accounting mission, including the Pentagon's Defense Prisoner of War/Missing Personnel Office, or DPMO, which is in charge of policy, have sometimes complicated their task by making public statements that their critics view as disingenuous or erroneous.
Accounting for the nation's war dead has been a politically charged issue for decades. The debate is not about the practicality of the mission, which some might question, but how it should be pursued.
Sometimes overlooked amid the squabbling is the emotional toll on the families of the missing. They are often bewildered by the bureaucracy and left to watch hope wear away with the passage of time.
In 1975, more than two decades after Pfc. Kenneth F. Reese was declared missing in Korea, his widow, Chris Tench, who had by then remarried, described her feelings in her local newspaper, the Gastonia (North Carolina) Gazette.
She wrote that initially she was relieved to realize that the policeman who delivered the news about Reese on Dec. 18, 1950, was saying that her husband was missing, not dead. He might turn up alive, she recalled thinking.
Later she thought differently."No, missing isn't dead," she wrote. "It's worse than dead."
Articles from the Guardian(UK)
Worth A Click for those who want to know:Global corruption survey reveals one in four people paid a bribe in past year
Transparency International investigation highlights lack of public faith in politicians and widespread public concern about graftNSA and GCHQ spy programmes face legal challenge
Privacy campaigners file claim saying laws used to justify data trawling by Prism and Tempora programmes are being abusedUS privacy group challenging NSA and FBI collection of phone records
Electronic Privacy Information Center to file petition asking supreme court to suspend FBI's blanket collection of data
David Normal ~ Artist
"CRAZYOLOGY CO-LABORATORY"
Saturday, July 6th 2013 7:30PM to 10PM
Clemente Soto Velez Cultural Center 107 Suffolk St., NYC (Delancey and Essex)
Admission: Free!
You are invited to a solo exhibit of David Normal's unique light based art known as "Illuminations" that are double-sided lightboxes that glow like stained glass windows and feature Normal's inimitable imagery. The Illuminations, hanging and rotating gently in space, form a kind of portable cathedral of the absurd and the profane that is a complete immersive art environment comprised of individual paintings that are rich narrative experiences unto themselves speaking in a sophisticated visual language that references elements of popular culture and classical art, but also suffused with an influence from Normal's deep studies in Eastern art.
It's a style he calls "CRAZYOLOGY", and on the evening of July 6th Normal will expound the concepts and ideas of this, his own aesthetic system, in the first of what will be a series of forums known as "CRAZYOLOGY CO-LABORATORY". The purpose is not only to inform the public, but to engage other artists in collaborative works guided by the principles of CRAZYOLOGY.
The evening will include an artist reception beginning at 7:30 PM. At 8:30 Normal will give a lecture with multimedia presentation on the philosophy and history of CRAZYOLOGY. A question and answer session will follow and conversations will likely continue until the end of the event at 10 PM
For more info: http://www.davidnormal.com/#!crazyological-lightworks/c19mm
Facebook event page: https://www.facebook.com/events/189995397827242
Mike Wilhelm ~ Charlatans, Flamin' Groovies, Loose Gravel, and more
Crest of the Wave Productions
Mike Somavilla & Art House Gallery Present:
Mike Wilhelm & Hired Guns
Featuring: Jamie Webber and Gary Bouley
Art House Gallery & Cultural Center
2905 Shattuck Ave., Berkeley, CA 9470 (between Russell and Ashby)
July 20, 2013 ~ Show: 8:00 PM (door opens 7:00 PM)
For reservation: call 510-472-3170
Lack of transparency means
tainted justice for Bradley ManningMilitary obfuscation and compliant media make for an Orwellian trial of managed misinformation against the WikiLeaks source
Alexa O'Brien, guardian.co.uk, Saturday 6 July 2013 08.00 EDT, Article Source
Army Pfc Bradley Manning is escorted out of a courthouse in Fort Meade, Maryland. Photograph: Jose Luis Magana/APThe lack of contemporaneous access to court documents has caused irreparable harm to the American public's right to scrutinize the conduct of military prosecutors and the rulings of the presiding military judge. This will surely taint the final outcome of Pfc Bradley Manning's trial.
"Military confinement. That's like a term of art," said the spokesperson for the military district of Washington (MDW) – which is responsible for convening a fair and impartial trial for the accused – to an American TV reporter last summer. The reporter was known for investigating infotainment websites during pre-trial sessions. "The practical effect?" commented the spokesman to the reporter. "He's in jail."
As we wait for the second circuit to rule on the Department of Justice's midnight appeal of Judge Katherine Forrest's permanent injunction on indefinite military detention of American citizens without trial or charges, Jennifer Elsea, a legislative attorney who provides policy and legal analysis to the US Congress, reminds us that aiding the enemy (pdf) is "one of two offenses under the Uniform Code of Military Justice that apply to 'any person', rather than just members of the military, like Manning."
Despite Manning having been held longer than any accused awaiting court martial in US military law, Judge Lind ruled in February that the government had not violated his speedy trial rights. Moreover, in a case where the first amendment is vulnerable to chill and prohibition – namely, because the accused is charged with aiding the enemy and espionage for disclosing government information to the public – the public was denied access to not only the court's speedy trial ruling, but also over 30,000 pages of court documents until the third day of Manning's trial, which was 1,103 days into his pretrial confinement and 18 months into the legal proceeding.
It was unfounded allegations by a confidential government informant that Manning had leaked top-secret material (he had not) that was used as the basis of his pre-trial confinement in May 2010. That misinformation was amplified in the mainstream media, spoon-fed into a feeding frenzy by prominent government officials, calling for the death penalty for Manning; the designation of WikiLeaks as a terrorist organization; and the criminal prosecution of Julian Assange.
At Fort George "Orwell" Meade, home of the NSA and the US Defense Information School, managing the message for a "docketless" pre-trial was facilitated by the spokesperson for the military district of Washington. He was tasked with explaining the proceedings to a press pool, forced to compare notes after mile-a-minute recitations into the court record by the presiding military judge, Colonel Denise Lind.
"You would say, 'He's in a jail'?" asked the American TV reporter of her de facto MDW editor. The same reporter also inquired later whether I found George Clooney handsome. "I think 'military confinement' is the most accurate," replied the spokesperson. "Luckily, I have nothing to do with that."
For five and a half months, the former spokesperson for the MDW did not disclose to the anemic press that he was a former member of the prosecution. In fact, his emails with the Quantico Brig commander about Manning's underwear removal are part of the evidentiary record concerning Manning's unlawful pretrial punishment at the Quantico Brig, where he was stripped of his clothing against the recommendation of the Brig mental health providers. In light of this revelation, the military district of Washington recently required credentialed media to sign "ground rules" prohibiting them from naming staff without written approval.
On the first day of his trial, the public did not have a transcript of Manning's formal plea to ten lesser included offenses (LIOs), which included substituted dates for the offenses charged against him. The public did not know that this earnest young soldier volunteered to plea to the LIO for an April transmission of the Garani video three weeks after Judge Lind "cut his defense off at the knees", in his attorney David Coombs' words, by precluding evidence of the actual lack of harm from his disclosures.
Manning made his plea knowing the prosecution lacked forensic evidence for a transmission in November 2009. The November transmission fits into the US government's theory of the case that ties it to the grand jury investigation of WikiLeaks.
The public also did not know that military prosecutors not only rejected Manning's proposed plea, but even threatened to charge him with an additional ten-year offense on top of the life sentence plus 149 years he already faces if convicted on their case.
Moreover, the public did not know that Manning is charged with a newfangled offense, which is not tied to any existing US federal criminal violation or punitive article of the Uniform Code of Military Justice, called "wanton publication". All that military prosecutors have to prove to convict him is that he had knew that terrorists use the internet.
Transparency is vital to the public's perception of the legitimacy of the criminal proceedings. The obscurity managed by Col Denise Lind, the military district of Washington, and the US army has discredited the imminent outcome.
Edward Snowden is a whistleblower, not a spy
-- but do our leaders care?Legislators and journalists alike have been cavalier in their condemnations of the man responsible for the NSA leaks
Spencer Ackerman in Washington, guardian.co.uk, Friday 5 July 2013 13.03 EDT, Article Source
The Twitter account of House intelligence committee chairman Mike Rogers, left,
placed Edward Snowden in the company of two infamous double agents. Photograph: J Scott Applewhite/APAccording to US legislators and journalists, the surveillance whistleblower Edward Snowden actively aided America's enemies. They are just missing one essential element for the meme to take flight: evidence.
An op-ed by Representative Mike Pompeo (Republican, Kansas) proclaiming Snowden, who provided disclosed widespread surveillance on phone records and internet communications by the National Security Agency, "not a whistleblower" is indicative of the emerging narrative. Writing in the Wichita Eagle on 30 June Pompeo, a member of the House intelligence committee, wrote that Snowden "has provided intelligence to America's adversaries".
Pompeo correctly notes in his op-ed that "facts are important". Yet when asked for the evidence justifying the claim that Snowden gave intelligence to American adversaries, his spokesman, JP Freire, cited Snowden's leak of NSA documents. Those documents, however, were provided to the Guardian and the Washington Post, not al-Qaeda or North Korea.
It's true that information published in the press can be read by anyone, including people who mean America harm. But to conflate that with actively handing information to foreign adversaries is to foreclose on the crucial distinction between a whistleblower and a spy, and makes journalists the handmaidens of enemies of the state.
Yet powerful legislators are eager to make that conflation about Snowden.
The Twitter account of Representative Mike Rogers (Republican, Michigan), the chairman of the House intelligence committee, on 18 June placed Snowden and accused WikiLeaks source Bradley Manning in the same company as Aldrich Ames and Robert Hanssen, two infamous CIA and FBI double-agents. (The tweet appears to have been deleted.)
When I asked about the conflation, Rogers' Twitter account responded: "All 4 gave critical national security information to our enemies. Each did it in different ways but the result was the same."
Never to be outdone, Peter King, a New York Republican and former chair of the House homeland security committee, proclaimed Snowden a "defector" on 10 June. Days later, Snowden left Hong Kong to seek asylum in an undetermined country – a curious move for a defector to make.
Once elected and appointed leaders casually conflate leaking and espionage, it is a matter of time before journalists take the cue. For insight into the "fear and isolation that NSA leaker Edward Snowden is living through", CNN turned to Christopher Boyce – who sold US secrets to the USSR before becoming a bank robber.
There are understandable suspicions that Snowden may have aided foreign intelligence services in order to aid in his escape from American criminal justice. While some have speculated that the Russian or Chinese intelligence services might have snuck a look at the highly sensitive intelligence material Snowden is carrying, that material is heavily encrypted. For what it's worth, in a Guardian webchat I asked Snowden directly if he would trade access to his documents for asylum. He said he would not.
Perhaps Snowden lied. Perhaps he might change his mind. But all of that is far off in the realm of speculation. As things stand now, there is no evidence Snowden has aided any US adversary or intelligence service, wittingly or not.
Even the Obama administration has stopped short of terming Snowden a spy, even in the course of attacking his character. (Yes, he was indicted under the Espionage Act, but the actual charges against him are theft of government property, unauthorized communication of national defense information, and willful communication of classified intelligence information to an unauthorized person.) In an email meant to discredit Snowden in the press, an anonymous "senior administration official" told reporters on 24 June that Snowden's ostensible idealism "is belied by the protectors he has potentially chosen: China, Russia, Cuba, Venezuela and Ecuador". That's something to remember the next time Washington wants to talk about its commitment to human rights while cooperating with, say, China and Russia.
Edward Snowden. Photograph: Reuters/The GuardianWhen asked directly if there was any evidence that Snowden had cooperated with any intelligence service or American adversary, the administration and Congress declined to provide any. The office of the director of national intelligence, James Clapper, declined to comment for this story. The Justice Department and the House intelligence committee didn't even respond to inquiries.
By all means, consider Snowden a hero, a traitor or a complex individual with a mixture of motives and interests. Lots of opinions about Snowden are valid. He is a necessarily polarizing figure. The information he revealed speaks to some of the most basic questions about the boundaries between the citizen and the state, as well as persistent and real anxieties about terrorism.
What isn't valid is the blithe assertion, absent evidence, that the former NSA contractor actively collaborated with America's enemies. Snowden made classified information about widespread surveillance available to the American public. That's a curious definition of an enemy for US legislators to adopt.
Blowback from the White House's vindictive war
on whistleblowersEdward Snowden is explicit: seeing whistleblowers like me punitively treated only motivates citizens of conscience more
Shamai Leibowitz, guardian.co.uk, Friday 5 July 2013 08.30 EDT, Article Source
In 2009, I was working as a contract linguist for the FBI when I discovered that the FBI was committing what I believed to be illegal acts. After I revealed these to a blogger, the Department of Justice came after me with a vengeance.
When the FBI confronted me, I admitted what I had done. I tried to negotiate for a reasonable resolution of my case. The documents I disclosed were never explicitly published anywhere, but that didn't matter: the DOJ was adamant that I be charged under the Espionage Act and spend time in jail. Even though I leaked the material because I thought the FBI was doing something illegal, and the American people had a right to know, I faced the threat of dozens of years in prison. I did what was best for my family, and signed a plea agreeing to a 20-month sentence.
Considering Edward Snowden's revelations, what I witnessed pales in comparison. But reading about the secretive NSA programs collecting the private data of millions of Americans did not surprise me. As Snowden explained, he watched for years as the military-industrial-intelligence complex turned our country into a massive surveillance state, and observed a "continuing litany of lies" from senior officials to Congress. Eventually, he decided to speak out, because he could not in good conscience remain silent.
Although he chose a very different path than I did – he fled first to Honk Kong and then to Moscow while apparently seeking asylum in another country – the US authorities are faced with a similar dilemma in how to react to his revelations. Can the DOJ and national security establishment act in a reasonable manner? Or will they allow their fuming anger to consume them into making further irrational decisions?
This ongoing manhunt, accompanied by a smear campaign and threats to throw the book at Snowden, is a grave mistake. If the government really wanted to keep more secrets from coming out, they would do well to let this man of conscience go live his life in some other country. Meanwhile, it would only help them if they were to apologize to the American public for lying to us, and turning the country into what Pentagon Papers leaker Daniel Ellsberg calls the United Stasi of America.
In my case, my family and I pleaded with the DOJ lawyers to avoid a prison term, agree to a lesser punishment and put this case to rest without any media attention. But the FBI and DOJ were insistent on imprisoning me and splashing it all over the media. The ink was not even dry on my plea bargain before they ran to the media with a press release, announcing to the whole world how the 20-month prison sentence will teach me – and any future whistleblowers – a great lesson.
But this punitive strategy, this desire to demonize and imprison people at all costs, is wrong and misguided.
When Edward Snowden, hiding in Honk Kong, participated in an online chat to explain his motives, he was asked whether the treatment of other whistleblowers influenced him. He responded:
"[Previous whistleblowers] are all examples of how overly-harsh responses to public-interest whistleblowing only escalate the scale, scope, and skill involved in future disclosures. Citizens with a conscience are not going to ignore wrongdoing simply because they'll be destroyed for it: the conscience forbids it. Instead, these draconian responses simply build better whistleblowers."
So it seems that in their goal to imprison me, to imprison John Kiriakou, to detain Bradley Manning in what have been called cruel and inhumane conditions and seek monstrous punishment, to aggressively prosecute NSA whistleblower Thomas Drake and others – they actually encouraged Snowden to reveal this important information.
The Snowden saga is a great teaching moment for the Obama administration. It is now reaping the fruit of its vindictive behavior.
Even in a democracy certain information needs to remain secret, and those with access to that information must honor their obligation to safeguard it. But Snowden and other whistleblowers have not leaked secrets for their own benefit or enrichment; rather, they sacrificed the comfort of their lives to expose lies, fraud, human rights abuses, and unconstitutionality.
As Martin Luther King pointed out, we should never forget that everything Adolf Hitler did in Germany was "legal" and everything the Hungarian freedom fighters did in Hungary was "illegal". Of course, the abuses revealed by Snowden are a far cry from the atrocities of the Nazis, but the principle, nevertheless, is the same: obedience to the law should not be absolute. Technically, we whistleblowers broke the law, but we felt, as many have felt before, that the obligation to our consciences and basic human rights is stronger than our obligation to obey the law.
NSA leaks: UK blocks crucial espionage talks
between US and EuropeFirst talks to soothe transatlantic tensions to be restricted to data privacy and Prism programme after Britain and Sweden's veto
Ian Traynor in Vilnius, guardian.co.uk, Friday 5 July 2013 09.36 EDT, Article Source
José Manuel Barroso, the European commission president, and Dalia Grybauskaitė,
Lithuania's president, have backed down from initial demands of two strands
of dialogue with the Americans. Photograph: Valda Kalnina/EPABritain has blocked the first crucial talks on intelligence and espionage between European officials and their American counterparts since the NSA surveillance scandal erupted.
The talks, due to begin in Washington on Monday, will now be restricted to issues of data privacy and the NSA's Prism programme following a tense 24 hours of negotiations in Brussels between national EU ambassadors. Britain, supported only by Sweden, vetoed plans to launch two "working groups" on the espionage debacle with the Americans.
Instead, the talks will consist of one working group focused on the NSA's Prism programme, which has been capturing and storing vast amounts of internet and mobile phone metadata in Europe.
The disclosures in the Guardian over the past month have triggered a transatlantic crisis of confidence and threatened to derail crucial free trade talks between the EU and the US, also due to be launched in Washington on Monday.
The talks on Prism and data privacy have been arranged to coincide with the trade talks in an attempt to defuse the transatlantic tension. EU diplomats and officials say the offer of talks by the Americans is designed to enable the leaders of Germany and France to save face following revelations about the scale of US espionage – particularly in Germany, but also of French and other European embassies and missions in the US.
Other aspects of the dispute, such as more traditional spying and intelligence matters, will be off limits for the Europeans after Britain insisted the EU had no authority to discuss issues of national security and intelligence.
"It was decided. It finished successfully," said Dalia Grybauskaitė, the president of Lithuania, which has just assumed the EU's six-month rotating presidency and which mediated the sensitive talks in Brussels over the past two days.
On Thursday, Grybauskaitė said the Europeans hoped to hold two separate strands of consultations with the Americans. By Friday she and José Manuel Barroso, the European commission president, conceded that the intelligence strand had been dropped. "Intelligence matters and those of national security are not the competence of the EU," he said, echoing the UK's objection.
Senior EU diplomats, officials, and government ministers confirmed that Britain opposed most of the rest of the EU on joint European talks with the Americans on intelligence and espionage, meaning that national governments will need to pursue the issues separately with Washington.
"The consultations in Washington will first of all address data protection matters. Addressing the intelligence topic is not expected," said a senior Lithuanian official.
The Lithuanian government phoned Carl Bildt, Sweden's foreign minister, on Thursday evening to try to remove the Swedish resistance, but failed, sources said. The talks in Brussels continued throughout the night as diplomats sought to come up with wording that would keep everyone happy.
Officials said the abortive attempt to come up with a common European position only served to highlight the divisions that have surfaced as a result of the espionage scandal, with the Europeans against the Americans, the French and the Germans against the British, and leading pro-EU figures arguing that the fiasco has underlined the case for Europe constructing its own cyber-defences.
"We need our own capacities, European cloud computing, EU strategic independence," said Michel Barnier, the French politician and European commissioner for the single market.
Such is the transatlantic and intra-European disarray over the espionage wars, that senior east and west European politicians and intelligence veterans privately suspect a Russian role in the intelligence row. They point to the presence of the NSA whistleblower, Edward Snowden – apparently still at Moscow's Sheremetyevo airport – and to the controversy surrounding the Bolivian presidential plane. President Evo Morales, travelling from Moscow, was forced to land in Vienna after being denied permission to enter the airspace of several EU countries.
The surveillance dispute led to calls, particularly from France, for the long-awaited negotiations on a transatlantic free trade pact to be delayed. The simultaneous opening of talks on the NSA, Prism and surveillance is designed to mute such calls and give European leaders an opportunity to climb down while claiming concessions from the Americans, EU diplomats said.
Since Nobody Seems to Care, I Have A Few Questions:
On the ongoing US surveillance row ~ Copyright © Steve Bell 2013
Barack Obama says the NSA will assess EU espionage allegations as Edward Snowden's asylum options narrow.by Balz, US Military Veteran with Honorable Discharge, not like chickenhawk cowards Bush and Cheney, July 3, 2013
Why isn't George W Bush and his Family on trial for Aiding & Abetting the Enemy like Bradley Manning?
Salem bin Laden invested heavily in Arbusto Energy, a company run by George W. Bush, through his friend James R. Bath. Several members of the Bush family are investors in the Carlyle Group, a defense contractor and investment fund with numerous interests in the Saudi Arabia and the Middle East and connections to the Saudi Binladen Group, run by former Reagan administration Secretary of Defense Frank Carlucci. On September 10, 2001, former President George H.W. Bush and several members of his cabinet had been present at a Carlyle Group business conference with Shafig bin Laden, a half-brother of Osama bin Laden, at the Ritz-Carlton hotel located several miles from the Pentagon. The conference was continuing with the remaining cabinet members and bin Laden's brother at the time of the Pentagon attack. George H.W. Bush remained an advisor to the Carlyle Group for two years after the attacks.
The New York Times reported that members of the bin Laden family were driven or flown under Federal Bureau of Investigation (FBI) supervision to a secret assembly point in Texas and then to Washington from where they left the country on a private charter plane when airports reopened three days after the attacks.
On June 20, 2007, the public interest group Judicial Watch released FBI documents that it says suggested that Osama bin Laden himself may have chartered one of the flights.
Why was this Obvious Lie Never Explained?
On Friday 14 December 2001 a videotape of Osama bin Laden "confessing" to the 9/11 attacks was released. The tape was supposedly found in a house in Qandahar, Afghanistan. The recording was of very poor audio and visual quality and the authenticity of the tape was questioned.
This annoyed War Criminal George W. Bush who said, [It is] preposterous to think this tape was doctored.
Okay, let's have a look.
Here's 5 Osama's - which is the odd one out?While thinking about the above, consider this: In 2002, Pakistani President Pervez Musharraf said bin Laden had kidney disease, and that he had required a dialysis machine when he lived in Afghanistan.
(BTW) Where is the dialysis machine that was not in the photos from Pakistan?
Why wasn't the 2.3 Trillion US Tax Dollars Donald Rumsfeld said was missing on September 10, 2001 thoroughly investigated?
Was it really coincidence records of this missing money were destroyed during the mass murders of September 11, 2001; remembering Rumsfeld was part of a Neocon group who were determined to get rid of Saddam Hussein, steal Iraqi oil, and first used the term "Weapons of Mass Destruction." It was Rumsfeld who attempted to shift blame from he and Halliburton's Dick Cheney by claiming, "Money wasted by the military poses a serious threat."
WHERE IS THAT HARD EARNED TAX PAYER MONEY?
Why Isn't Condoleezza Rice; initiator of Torture, in prison for having children sodomized?
Why wasn't Dianne 'War Profiteer' Feinstein investigated for making billions for her War Profiteer husband?
Why wasn't Halliburton's Dick Cheney investigated for secret energy meetings that alleged establishment of a foundation for the Mass Murders of 9/11?
How did John Ashcroft and Alberto Gonzales avoid being brought up on criminal charges? It is a known fact Gonzales and Ashcroft broke laws.
There are more questions, but explaining the above will determine if an Obama Administration supports Democrat & Republican traitors and criminals.
On Bolivia and Evo Morales ~ Copyright © Steve Bell 2013
US refuses to comment on Morales plane but admits contact with other nations over potential Snowden flights
Karl Cohen ~ Association International du Film d'Animation-SF Newsletter
ASIFA-SF NEWSLETTER
Association International du Film d'Animation
(International Animated Film Association)
July 2013This issue includes:
A critical look at the mindless animated features being offered this summer (including why Pixar is not making great films at the moment)
Why are CalArts and USC Exceptional Animation Schools
INSPIRING ANIMATION ARTISTS TO BE CREATIVE THINKERS
ADDITIONS TO RECENT ARTICLES ABOUT EMPLOYMENT
TWO FORMER INTERNS WIN THEIR LAWSUIT AGAINST FOX. THE JUDGE'S VERDICT ALLOWS FOR A CLASS ACTION SUIT AGAINST FOX TO PROCEED
A note from Marv Newland
Promote yourself as having "added value"
European firms 'could quit US internet
providers over NSA scandal'European commission vice-president says American cloud services providers could suffer loss of business
Ian Traynor in Vilnius, guardian.co.uk, Thursday 4 July 2013 11.53 EDT, Article Source
Neelie Kroes, European commissioner for digital matters, who said: 'If I were an American cloud
provider, I would be quite frustrated with my government right now.' Photograph: Yves Logghe/APEuropean businesses are likely to abandon the services of American internet providers because of the National Security Agency surveillance scandal, the European commission has warned.
Neelie Kroes, the commission vice-president who speaks on digital affairs, predicted that providers of cloud services, which allow users to store and access data on remote servers, could suffer significant loss of business if clients fear the security of their material is under threat.
The warning came as it appeared that the Americans and the Europeans were to start investigating alleged breaches of data privacy in the EU as well as US intelligence and espionage practices.
Despite threats from France to delay long-awaited EU-US negotiations on a new transatlantic free trade pact, scheduled to open in Washington on Monday, EU ambassadors in Brussels reached a consensus on Thursday to go ahead with the talks.
They could not yet agree, however, on how to respond to a US offer of parallel talks on the NSA scandal, the Prism and Tempora programmes and issues of more traditional espionage arising from reports of how US agencies bugged and tapped the offices and embassies of the EU and several member states.
Dalia Grybauskaitė, the president of Lithuania, said on Thursday that she was not seeking an apology from the Americans. Lithuania takes over the rotating six-month EU presidency this week.
While no decision had yet been taken, she said she hoped the EU-US talks on electronic surveillance would also be launched on Monday and run concurrently. Since much of the alleged US hoovering up of telephone and internet traffic in Europe is assumed to amount to commercial and industrial espionage, the two parallel sets of talks will affect one another.
Senior EU officials complain that there is no point engaging in sensitive trade talks when the other side has already eavesdropped on you and knows your negotiating position.
Grybauskaitė emphasised that the American side was keen to come clean on the dispute.
"They are open to co-operation. They are open to explain," she said. "I never seek an apology from anyone. I seek information … We don't want to jeopardise the strategic importance of free trade."
Pointing to the potential fallout from the disclosures about the scale of NSA operations in Europe, Kroes, the European commissioner for digital matters, predicted that US internet providers of cloud services could suffer major business losses.
"If businesses or governments think they might be spied on, they will have less reason to trust cloud, and it will be cloud providers who ultimately miss out. Why would you pay someone else to hold your commercial or other secrets if you suspect or know they are being shared against your wishes?" she said.
"It is often American providers that will miss out, because they are often the leaders in cloud services. If European cloud customers cannot trust the United States government, then maybe they won't trust US cloud providers either. If I am right, there are multibillion-euro consequences for American companies. If I were an American cloud provider, I would be quite frustrated with my government right now."
The German chancellor, Angela Merkel, the European commission and Grybauskaitė made clear they wanted the trade talks to go ahead as planned on Monday. France appeared to drop its objections despite previously insisting on guarantees that the espionage had been halted before the trade talks could start.
Grybauskaitė also voiced suspicions of a possible Russian role in the furore, pointing to Edward Snowden, the NSA whistleblower, being stuck in Moscow at the same time as weekend revelations about US spying on Europe emerged in the runup to the trade talks.
She insisted that the espionage dispute should not be allowed to derail the trade talks but conceded that "some countries are very sensitive on this question." The Lithuanian finance minister, Rimantas Šadžius, said: "The French have some problems."
EU diplomats said ambassadors from the 28 member states engaged in "urgent and tricky" discussions on Thursday on how to proceed. While the European commission would lead the EU side on issues of data privacy, the talks on intelligence and espionage practices would need to be done by national governments.
It was not clear where Britain fitted into the picture since it is one of the biggest EU countries but has not been targeted by the NSA, unlike Germany or France, according to the reports, and the UK's GCHQ has itself been collecting vast quantities of European internet and telephone data.
Kroes warned that US firms could be the biggest losers from the US government's voracious appetite for information.
"Concerns about cloud security can easily push European policy-makers into putting security guarantees ahead of open markets, with consequences for American companies. Cloud has a lot of potential. But potential doesn't count for much in an atmosphere of distrust."
NSA surveillance:
protesters stage Restore the Fourth rallies across USSan Francisco protest targets Senator Dianne Feinstein as part of demands for reform of Patriot Act across the US
Rebecca Bowe in San Francisco, guardian.co.uk, Friday 5 July 2013 03.40 EDT, Article Source
Protesters on Market Street in San Francisco. Photograph: Justin BenttinenProtests took place across the US on Thursday to demonstrate opposition to sweeping National Security Agency surveillance programs.
The events were organised by a newly hatched organisation called Restore the Fourth, named after the constitutionally guaranteed protection against illegal search and seizure under the Fourth Amendment. Rallies and marches took place in San Francisco, Los Angeles, Dallas, New York City, Washington DC and dozens of other US cities.
Ryan Brown, a regional leader for the San Francisco Bay protests who has been co-ordinating with national organisers, said his participation in Restore the Fourth stemmed from concern over excessive governmental power implied by the spying programs. "I see it as ethically disgusting that the government has both the opportunity and the ability … to collect the data on us individually, without a given reason other than quote-unquote 'protecting our freedoms'," he said.
Restore the Fourth describes itself as a "grassroots, non-partisan, non-violent movement", according to its website. Its central demands are to ask Congress to enact reform of the Patriot Act, which has been used as legal justification for the surveillance programs, to call for the formation of a special committee to investigate the extent of the spying programs, and to hold public officials accountable if they are found to be responsible for unconstitutional surveillance efforts.
Protesters rally in San Francisco. Photograph: Justin BenttinenMany of the individuals behind the San Francisco event had not met before collaborating with one another, said organiser Nick Desaulniers. After proposing a Bay Area protest on Reddit, "a couple people kind of found it, and a Facebook event popped up" Desaulniers explained. He works for Mozilla but emphasised that the company was not involved in organising efforts. "This has been just kind of running with it."
As it gained traction, Brown said, the effort drew support from the San Francisco-based Electronic Frontier Foundation, the American Civil Liberties Union and the National Lawyers Guild.
Brown said before the protest he expected a turnout of anywhere from 300 to 1,000 in San Francisco. Protesters planned to stop outside the office of Senator Dianne Feinstein, who chairs the Senate intelligence committee and had knowledge of the NSA spying activities before they were revealed to the general public. "She did nothing to stop it," said Brown. "We'll be making a point there of what elected officials can do to stop government wiretapping."
In the end, a few hundred protesters marched down Market Street. By the standards of San Francisco, a city with a rich history of activism, the protest was a tame affair. Police officers on bicycles pedalled alongside the crowd, but the mood stayed relaxed and the protest march never strayed from the sidewalk into the street.
While at least one person donned a Guy Fawkes mask, reminiscent of the Occupy movement, and another covered his face with a black bandana, the crowd consisted of a diverse mix of young and old from throughout the Bay Area, including a number of lawyers and tech workers sporting close-cropped hair, button-down shirts, and glasses. It was infused with an element of internet culture. One person held a sign featuring an Internet meme, and at one point, the crowd chanted in unison, "Get your mitts off my bits!"
The march passes the San Francisco Federal Building. Photograph: Justin Benttinen"I cannot believe we actually have to protest this in the United States," said Jonathan Nelson, who started an organisation called Hackers and Founders to assist Silicon Valley tech entrepreneurs, and said he'd heard about Restore the Fourth online.
Jack Breese, a San Francisco resident who also works in tech, displayed a sign that read "The NSA has TMI", or too much information. "I knew at the very least I had to come out," said Breese, who illustrated his passion for civil liberties by showing off a metal card he was carrying in his pocket inscribed with the text of the Bill of Rights.
Kristen Rudd, a San Francisco resident who attended the march with her husband and two children, said it was the first time she had been to a protest. "We want to see the Fourth Amendment followed by the government," she said, adding that she'd only learned about Restore the Fourth a day earlier, when she read about it online.
A media spokesperson for the national Restore the Fourth organisation, Douglas MacArthur, said Restore the Fourth got under way last month, in response to revelations about the NSA spying programs. That touched off a firestorm of response on social media networks, which in turn gave rise to a decentralised online community, a website, and finally a call to action. "Pretty much everyone met on the internet," MacArthur explained. "Reddit – that's how we all got involved."
National Restore the Fourth organisers generated widespread interest from online audiences when they conducted an Ask Me Anything forum on Reddit, where readers fired questions directly at discussion leaders.
"One criticism we've gotten about the date is that we'd be 'competing' with the celebrations," MacArthur noted in that thread. "But we aren't competing with them. We are integrated with them. The Fourth of July is already about what we're protesting. What better time to fight for your rights or inform others of the need to than when you're already celebrating the ones you have?"
Where Have All the Flowers Gone?
Reflections on the Spirit and Legacy of the Sixties
by Fritjof Capra ~ December 1, 2002 ~ Local SourceThe 1960s were the period of my life during which I experienced the most profound and most radical personal transformation. For those of us who identify with the cultural and political movements of the sixties, that period represents not so much a decade as a state of consciousness, characterized by "transpersonal" expansion, the questioning of authority, a sense of empowerment, and the experience of sensuous beauty and community.
This state of consciousness reached well into the seventies. In fact, one could say that the sixties came to an end only in December 1980, with the shot that killed John Lennon. The immense sense of loss felt by so many of us was, to a great extent, about the loss of an era. For a few days after the fatal shooting we relived the magic of the sixties. We did so in sadness and with tears, but the same feeling of enchantment and of community was once again alive. Wherever you went during those few days - in every neighborhood, every city, every country around the world - you heard John Lennon's music, and the intense idealism that had carried us through the sixties manifested itself once again:
In this essay, I shall try to evoke the spirit of that remarkable period, identify its defining characteristics, and provide an answer to some questions that are often asked nowadays: What happened to the cultural movements of the sixties? What did they achieve, and what, if any, is their legacy?
expansion of consciousness
The era of the sixties was dominated by an expansion of consciousness in two directions. One movement, in reaction to the increasing materialism and secularism of Western society, embraced a new kind of spirituality akin to the mystical traditions of the East. This involved an expansion of consciousness toward experiences involving nonordinary modes of awareness, which are traditionally achieved through meditation but may also occur in various other contexts, and which psychologists at the time began to call "transpersonal." Psychedelic drugs played a significant role in that movement, as did the human potential movement's promotion of expanded sensory awareness, expressed in its exhortation, "Get out of your head and into your senses!"
The first expansion of consciousness, then, was a movement beyond materialism and toward a new spirituality, beyond ordinary reality via meditative and psychedelic experiences, and beyond rationality through expanded sensory awareness. The combined effect was a continual sense of magic, awe, and wonder that for many of us will forever be associated with the sixties.
questioning of authority
The other movement was an expansion of social consciousness, triggered by a radical questioning of authority. This happened independently in several areas. While the American civil rights movement demanded that Black citizens be included in the political process, the free speech movement at Berkeley and student movements at other universities throughout the United States and Europe demanded the same for students.
In Europe, these movements culminated in the memorable revolt of French university students that is still known simply as "May '68." During that time, all research and teaching activities came to a complete halt at most French universities when the students, led by Daniel Cohn-Bendit, extended their critique to society as a whole and sought the solidarity of the French labor movement to change the entire social order. For three weeks, the administrations of Paris and other French cities, public transport, and businesses of every kind were paralyzed by a general strike. In Paris, people spent most of their time discussing politics in the streets, while the students held strategic discussions at the Sorbonne and other universities. In addition, they occupied the Odéon, the spacious theater of the Comédie Française, and transformed it into a twenty-four-hour "people's parliament," where they discussed their stimulating, albeit highly idealistic, visions of of a future social order.
1968 was also the year of the celebrated "Prague Spring," during which Czech citizens, led by Alexander Dubcek, questioned the authority of the Soviet regime, which alarmed the Soviet Communist party to such an extent that, a few months later, it crushed the democratization processes initiated in Prague in its brutal invasion of Czechoslovakia.
In the United States, opposition to the Vietnam war became a political rallying point for the student movement and the counterculture. It sparked a huge anti-war movement, which exerted a major influence on the American political scene and led to many memorable events, including the decision by President Johnson not to seek reelection, the turbulent 1968 Democratic Convention in Chicago, the Watergate scandal, and the resignation of President Nixon.
a new sense of community
While the civil rights movement questioned the authority of white society and the student movements questioned the authority of their universities on political issues, the women's movement began to question patriarchal authority; humanistic psychologists undermined the authority of doctors and therapists; and the sexual revolution, triggered by the availability of birth control pills, broke down the puritan attitudes toward sexuality that were typical of American culture.
The radical questioning of authority and the expansion of social and transpersonal consciousness gave rise to a whole new culture - a "counterculture" - that defined itself in opposition to the dominant "straight" culture by embracing a different set of values. The members of this alternative culture, who were called "hippies" by outsiders but rarely used that term themselves, were held together by a strong sense of community. To distinguish ourselves from the crew cuts and polyester suits of that era's business executives, we wore long hair, colorful and individualistic clothes, flowers, beads, and other jewelry. Many of us were vegetarians who often baked our own bread, practiced yoga or some other form of meditation, and learned to work with our hands in various crafts.
Our subculture was immediately identifiable and tightly bound together. It had its own rituals, music, poetry, and literature; a common fascination with spirituality and the occult; and the shared vision of a peaceful and beautiful society. Rock music and psychedelic drugs were powerful bonds that strongly influenced the art and lifestyle of the hippie culture. In addition, the closeness, peacefulness, and trust of the hippie communities were expressed in casual communal nudity and freely shared sexuality. In our homes we would frequently burn incense and keep little altars with eclectic collections of statues of Indian gods and goddesses, meditating Buddhas, yarrow stalks or coins for consulting "sacred" objects.
Although different branches of the sixties movement arose independently and often remained distinct movements with little overlap for several years, they eventually became aware of one another, expressed mutual solidarity, and, during the 1970s, merged more or less into a single subculture. By that time, psychedelic drugs, rock music, and the hippie fashion had transcended national boundaries and had forged strong ties among the international counterculture. Multinational hippie tribes gathered in several countercultural centers - London, Amsterdam, San Francisco, Greenwich Village - as well as in more remote and exotic cities like Marrakech and Katmandu. These frequent cross-cultural exchanges gave rise to an "alternative global awareness" long before the onset of economic globalization.
the sixties' music
The zeitgeist of the sixties found expression in many art forms that often involved radical innovations, absorbed various facets of the counterculture, and strengthened the multiple relationships among the international alternative community.
Rock music was the strongest among these artistic bonds. The Beatles broke down the authority of studios and songwriters by writing their own music and lyrics, creating new musical genres, and setting up their own production company. While doing so, they incorporated many facets of the period's characteristic expansion of consciousness into their songs and lifestyles.
Bob Dylan expressed the spirit of the political protests in powerful poetry and music that became anthems of the sixties. The Rolling Stones represented the counterculture's irreverence, exuberance, and sexual energy, while San Francisco's "acid rock" scene gave expression to its psychedelic experiences.
At the same time, the "free jazz" of John Coltrane, Ornette Coleman, Sun Ra, Archie Shepp, and others shattered conventional forms of jazz improvisation and gave expression to spirituality, radical political poetry, street theater, and other elements of the counterculture. Like the jazz musicians, classical composers, such as Karlheinz Stockhausen in Germany and John Cage in the United States, broke down conventional musical forms and incorporated much of the sixties' spontaneity and expanded awareness into their music.
The fascination of the hippies with Indian religious philosophies, art, and culture led to a great popularity of Indian music. Most record collections in those days contained albums of Ravi Shankar, Ali Akbar Khan, and other masters of classical Indian music along with rock and folk music, jazz and blues.
The rock and drug culture of the sixties found its visual expressions in the psychedelic posters of the era's legendary rock concerts, especially in San Francisco, and in album covers of ever increasing sophistication, which became lasting icons of the sixties' subculture. Many rock concerts also featured "light shows" - a novel form of psychedelic art in which images of multicolored, pulsating, and ever changing shapes were projected onto walls and ceilings. Together with the loud rock music, these visual images created highly effective simulations of psychedelic experiences.
new literary forms
The main expressions of sixties' poetry were in the lyrics of rock and folk music. In addition, the "beat poetry" of Allen Ginsberg, Lawrence Ferlinghetti, Gary Snyder, and others, which had originated a decade earlier and shared many characteristics with the sixties' art forms, remained popular in the counterculture.
One of the major new literary forms was the "magical realism" of Latin American literature. In their short stories and novels, writers like Jorges Luis Borges and Gabriel García Márquez blended descriptions of realistic scenes with fantastic and dreamlike elements, metaphysical allegories, and mythical images. This was a perfect genre for the counterculture's fascination with altered states of consciousness and pervasive sense of magic.
In addition to the Latin American magical realism, science fiction, especially the complex series of Dune novels by Frank Herbert, exerted great fascination on the sixties' youth, as did the fantasy writings of J. R. R. Tolkien and Kurt Vonnegut. Many of us also turned to literary works of the past, such as the romantic novels of Hermann Hesse, in which we saw reflections of our own experiences.
Of equal, if not greater, popularity were the semi-fictional shamanistic writings of Carlos Castaneda, which satisfied the hippies' yearning for spirituality and "separate realities" mediated by psychedelic drugs. In addition, the dramatic encounters between Carlos and the Yaqui sorcerer Don Juan symbolized in a powerful way the clashes between the rational approach of modern industrial societies and the wisdom of traditional cultures.
film and the performing arts
In the sixties, the performing arts experienced radical innovations that broke every imaginable tradition of theater and dance. In fact, in companies like the Living Theater, the Judson Dance Theater, and the San Francisco Mime Troupe, theater and dance were often fused and combined with other forms of art. The performances involved trained actors and dancers as well as visual artists, musicians, poets, filmmakers, and even members of the audience.
Men and women often enjoyed equal status; nudity was frequent. Performances, often with strong political content, took place not only in theaters but also in museums, churches, parks, and in the streets. All these elements combined to create the dramatic expansion of experience and strong sense of community that was typical of the counterculture.
Film, too, was an important medium for expressing the zeitgeist of the sixties. Like the performing artists, the sixties' filmmakers, beginning with the pioneers of the French New Wave cinema, broke with the traditional techniques of their art, introducing multi-media approaches, often abandoning narratives altogether, and using their films to give a powerful voice to social critique.
With their innovative styles, these filmmakers expressed many key characteristics of the counterculture. For example, we can find the sixties' irreverence and political protest in the films of Godard; the questioning of materialism and a pervasive sense of alienation in Antonioni; questioning of the social order and transcendence of ordinary reality in Fellini; the exposure of class hypocrisy in Buñuel; social critique and utopian visions in Kubrik; the breaking down of sexual and gender stereotypes in Warhol; and the portrayal of altered states of consciousness in the works of experimental filmmakers like Kenneth Anger and John Whitney. In addition, the films of these directors are characterized by a strong sense of magical realism.
the legacy of the sixties
Many of the cultural expressions that were radical and subversive in the sixties have been accepted by broad segments of mainstream culture during the subsequent three decades. Examples would be the long hair and sixties fashion, the practice of Eastern forms of meditation and spirituality, recreational use of marijuana, increased sexual freedom, rejection of sexual and gender stereotypes, and the use of rock (and more recently rap) music to express alternative cultural values. All of these were once expressions of the counterculture that were ridiculed, suppressed, and even persecuted by the dominant mainstream society.
Beyond these contemporary expressions of values and esthetics that were shared by the sixties' counterculture, the most important and enduring legacy of that era has been the creation and subsequent flourishing of a global alternative culture that shares a set of core values. Although many of these values - e.g. environmentalism, feminism, gay rights, global justice - were shaped by cultural movements in the seventies, eighties, and nineties, their essential core was first expressed by the sixties' counterculture. In addition, many of today's senior progressive political activists, writers, and community leaders trace the roots of their original inspiration back to the sixties.
Green politics
In the sixties we questioned the dominant society and lived according to different values, but we did not formulate our critique in a coherent, systematic way. We did have concrete criticisms on single issues, such as the Vietnam war, but we did not develop any comprehensive alternative system of values and ideas. Our critique was based on intuitive feeling; we lived and embodied our protest rather than verbalizing and systematizing it.
The seventies brought consolidation of our views. As the magic of the sixties gradually faded, the initial excitement gave way to a period of focusing, digesting, and integrating. Two new cultural movements, the ecology movement and the feminist movement, emerged during the seventies and together provided the much-needed broad framework for our critique and alternative ideas.
The European student movement, which was largely Marxist oriented, was not able to turn its idealistic visions into realities during the sixties. But it kept its social concerns alive during the subsequent decade, while many of its members went through profound personal transformations. Influenced by the two major political themes of the seventies, feminism and ecology, these members of the "new left" broadened their horizons without losing their social consciousness. At the end of the decade, many of them became the leaders of transformed socialist parties. In Germany, these "young socialists" formed coalitions with ecologists, feminists, and peace activists, out of which emerged the Green Party - a new political party whose members confidently "We are neither left nor right; we are in front."
During the 1980s and 1990s, the Green movement became a permanent feature of the European political landscape, and Greens now hold seats in numerous national and regional parliaments around the world. They are the political embodiment of the core values of the sixties.
the end of the Cold War
During the 1970s and 1980s, the American anti-war movement expanded into the anti-nuclear and peace movements, in solidarity with corresponding movements in Europe, especially those in the UK and West Germany. This, in turn, sparked a powerful peace movement in East Germany, led by the Protestant churches, which maintained regular contacts with the West German peace movement, and in particular with Petra Kelly, the charismatic leader of the German Greens.
When Mikhail Gorbachev came to power in the Soviet Union in 1985, he was well aware of the strength of the Western peace movement and accepted our argument that a nuclear war cannot be won and should never be fought. This realization played an important part in Gorbachev's "new thinking" and his restructuring (perestroika) of the Soviet regime, which would lead, eventually, to the fall of the Berlin Wall, the Velvet Revolution in Czechoslovakia, and the end of Soviet Communism.
All social and political systems are highly nonlinear and do not lend themselves to being analyzed in terms of linear chains of cause and effect. Nevertheless, careful study of our recent history shows that the key ingredient in creating the climate that led to the end of the Cold War was not the hard-line strategy of the Reagan administration, as the conservative mythology would have it, but the international peace movement. This movement clearly had its political and cultural roots in the student movements and counterculture of the sixties.
the information technology revolution
The last decade of the twentieth century brought a global phenomenon that took most cultural observers by surprise. A new world emerged, shaped by new technologies, new social structures, a new economy, and a new culture. "Globalization" became the term used to summarize the extraordinary changes and the seemingly irresistible momentum that were now felt by millions of people.
A common characteristic of the multiple aspects of globalization is a global information and communications network based on revolutionary new technologies. The information technology revolution is the result of a complex dynamic of technological and human interactions, which produced synergistic effects in three major areas of electronics - computers, microelectronics, and telecommunications. The key innovations that created the radically new electronic environment of the 1990s all took place 20 years earlier, during the 1970s.
It may be surprising to many that, like so many other recent cultural movements, the information technology revolution has important roots in the sixties' counterculture. It was triggered by a dramatic technological development - a shift from data storage and processing in large, isolated machines to the interactive use of microcomputers and the sharing of computer power in electronic networks. This shift was spearheaded by young technology enthusiasts who embraced many aspects of the counterculture, which was still very much alive at that time.
The first commercially successful microcomputer was built in 1976 by two college dropouts, Steve Wosniak and Steve Jobs, in their now legendary garage in Silicon Valley. These young innovators and others like them brought the irreverent attitudes, freewheeling lifestyles, and strong sense of community they had adopted in the counterculture to their working environments. In doing so, they created the relatively informal, open, decentralized, and cooperative working styles that became characteristic of the new information technologies.
global capitalism
However, the ideals of the young technology pioneers of the seventies were not reflected in the new global economy that emerged from the information technology revolution 20 years later. On the contrary, what emerged was a new materialism, excessive corporate greed, and a dramatic rise of unethical behavior among our corporate and political leaders. These harmful and destructive attitudes are direct consequences of a new form of global capitalism, structured largely around electronic networks of financial and informational flows. The so-called "global market" is a network of machines programmed according to the fundamental principle that money-making should take precedence over human rights, democracy,
Since the new economy is organized according to this quintessential capitalist principle, it is not surprising that it has produced a multitude of interconnected harmful consequences that are in sharp contradiction to the ideals of the global Green movement: rising social inequality and social exclusion, a breakdown of democracy, more rapid and extensive deterioration of the natural environment, and increasing poverty and alienation. The new global capitalism has threatened and destroyed local communities around the world; and with the pursuit of an ill-conceived biotechnology, it has invaded the sanctity of life by attempting to turn diversity into monoculture, ecology into engineering, and life itself into a commodity.
It has become increasingly clear that global capitalism in its present form is unsustainable and needs to be fundamentally redesigned. Indeed, scholars, community leaders, and grassroots activists around the world are now raising their voices, demanding that we must "change "and suggesting concrete ways of doing so.
the global civil society
At the turn of this century, an impressive global coalition of nongovernmental organizations (NGOs), many of them led by men and women with deep personal roots in the sixties, formed around the core values of human dignity and ecological sustainability. In 1999, hundreds of these grassroots organizations interlinked electronically for several months to prepare for joint protest actions at the meeting of the World Trade Organization (WTO) in Seattle. The "Seattle Coalition," as it is now called, was extremely successful in derailing the WTO meeting and in making its views known to the world. Its concerted actions have permanently changed the political climate around the issue of economic globalization.
Since that time, the Seattle Coalition, or "global justice movement," has not only organized further protests but has also held several World Social Forum meetings in Porto Alegre, Brazil. At the second of these meetings, the NGOs proposed a whole set of alternative trade policies, including concrete and radical proposals for restructuring global financial institutions, which would profoundly change the nature of globalization.
The global justice movement exemplifies a new kind of political movement that is typical of our Information Age. Because of their skillful use of the Internet, the NGOs in the coalition are able to network with each other, share information, and mobilize their members with unprecedented speed. As a result, the new global NGOs have emerged as effective political actors who are independent of traditional national or international institutions. They constitute a new kind of global civil society.
This new form of alternative global community, sharing core values and making extensive use of electronic networks in addition to frequent human contacts, is one of the most important legacies of the sixties. If it succeeds in reshaping economic globalization so as to make it compatible with the values of human dignity and ecological sustainability, "sixties revolution" will have been realized:
Closing Argument
Boston Legal Speech on America and more
Please Click to View Video ~ http://vimeo.com/47165357
One Can Lead A Horse To Water, But...
Until there is a solution for this, where one solution has been provided, Nobody will bring Peace to Our Times, feed the hungry, care for the sick, and bake apple pie better than Mom. (otoh) If None of the Above was a choice on voter ballots, it would be a huge step towards recovering U.S. political control, and Nobody gets it.
None of the Above
should be a choice on Voter Ballots
George Carlin, The American Dream ~ http://vimeo.com/37487342
Give Peace a Chance
Wars happen when intolerance reaches epic proportions, when the reasons for war become greater than the sanctity of peace. Wars happen when we fail to realize the value of being alive. World leaders try to bring peace, but it is not an issue of institutions. It is human beings who start wars. Before a war begins outside, it starts inside.
The war on the inside is more dangerous because it is a fire that may never be put out. Wars are being fought because peace is not being found within, because it is not being allowed to unfold. We are all searching for something, we may call it success, peace, love, or tranquility. It is the same thing. What we are looking for has many names because we do not know what we need. To find what we need, we look around us. To know where to find what we are looking for, we first need to ask ourselves where we can find it. Have we considered looking within?
Living is not an easy task, especially if we want the best of it. We have to mine for it. Mining is not easy. We have to take out what we need and leave the rest. If we want to mine for peace, then we have to seek what is precious and discard what is not. The thing that we are searching for is not outside of us. It is within us. It always has been and always will be. Contentment feels good, and it is not an accident. It is not an accident that peace feels good. Peace is already here, and it resides in the hearts of all human beings.
Peace is something that has to be felt. One of the most incredible powers we have is that we can feel. When we place peace in front of that power to feel, we feel peace. We are here to be filled with gratitude, love and understanding. We carry a lamp within so bright that even in the darkest night, it can fill our world with light. This light is waiting to be found. Peace makes no distinctions. It does not care if we are rich, if we are poor, or what religion we belong to. It does not care which country we live in.
Peace is waiting to be found. Waiting to once again feel whole, not separated by all the issues that divide our lives. Peace is when the heart is no longer in duality, when the struggle within has been resolved. When peace comes to the heart, serenity follows. Love comes flooding in, uncontrolled. Joy cannot be held back. It bursts through because it is right. That is peace. Peace needs to be felt, love needs to be felt, truth needs to be felt. As long as we are alive, the yearning to feel good, to feel joy, will always be there, and as long as it is there, there will be a need for it to be discovered.
Life is a journey. We are passengers in a train called life, and we are alive in the moment called now. The journey of life is so beautiful that it needs no destination. On this journey, we have been given a compass. The compass is the thirst to be fulfilled. The true journey of life begins the day we begin to seek to quench our thirst. This quest is the most noble one. For many centuries, a voice has been calling out: "What you are looking for is within you. Your truth is within you, your peace is within you, your joy is within you." In our hearts, peace is like a seed waiting in the desert to grow, to blossom. When we allow this seed to blossom inside, then peace is possible outside. We have to give peace a chance.
Will we give peace a chance? ~ Prem Rawat, India Times 2/25/2000, Local Source
Oh, I hope that I see you again I never even caught your name As you looked through my window pane ~~ So I'm writing this message today I'm thinking that you'll have a way Of hearing the notes in my tune ~~ Where are you going? Where have you been? I can imagine other worlds you have seen ~~ Beautiful faces and music so serene ~~ So I do hope I see you again My universal citizen You went as quickly as you came ~~ You know the power Your love is right You have good reason To stay out of sight ~~ But break our illusions and help us Be the light ~ Message by Michael Pinder
Without love in the dream, it will never come true. ~ Jerry Garcia/Robert Hunter
The man whispered, "God, speak to me" and a meadowlark sang. But the man did not hear.
So the man yelled "God, speak to me" and the thunder rolled across the sky. But the man did not listen.
The man looked around and said, "God let me see you" and a star shined brightly. But the man did not notice.
And the man shouted, "God show me a miracle" and a life was born. But the man did not know.
So the man cried out in despair, "Touch me God, and let me know you are there"
Whereupon God reached down and touched the man. But the man brushed the butterfly away and walked on.
Don't miss out on a blessing because it isn't packaged the way you expect.